Today, Uptycs is introducing enhanced detection capabilities, including a new detections UI that correlates signals (events and alerts), assigns a composite threat score, and maps the associated signals to the MITRE ATT&CK matrix.
This new experience equips analysts with the context they need to quickly triage their detections queue without feeling like they’re missing anything. Watch the demo video below to see the new functionality in action.
Schedule a demo to learn more about the new detection and investigation functionality in Uptycs.
Uptycs ♥ MITRE ATT&CK
More than 80% of organizations are using MITRE ATT&CK to understand whether they’re appropriately covering their bases given the likely threats they face. At Uptycs, we’ve embraced MITRE ATT&CK in our latest release, building out hundreds of detections to cover the techniques and sub-techniques described in the framework. Analysts can easily map the signals that comprise a detection to the associated techniques in MITRE ATT&CK. Organizations that have large Mac fleets will appreciate the robust macOS support in Uptycs, in addition to Linux and Windows coverage.
Uptycs is also participating in the MITRE ATT&CK enterprise evaluation targeting the Carbanak and FIN7 threat groups. This round of the evaluations is interesting as Carbanak and FIN7 are both known for their stealthy tactics, including obfuscation and using legitimate administration tools to hide their activity. The evaluations are underway, with the MITRE ATT&CK organization planning to make results publicly available in the spring.
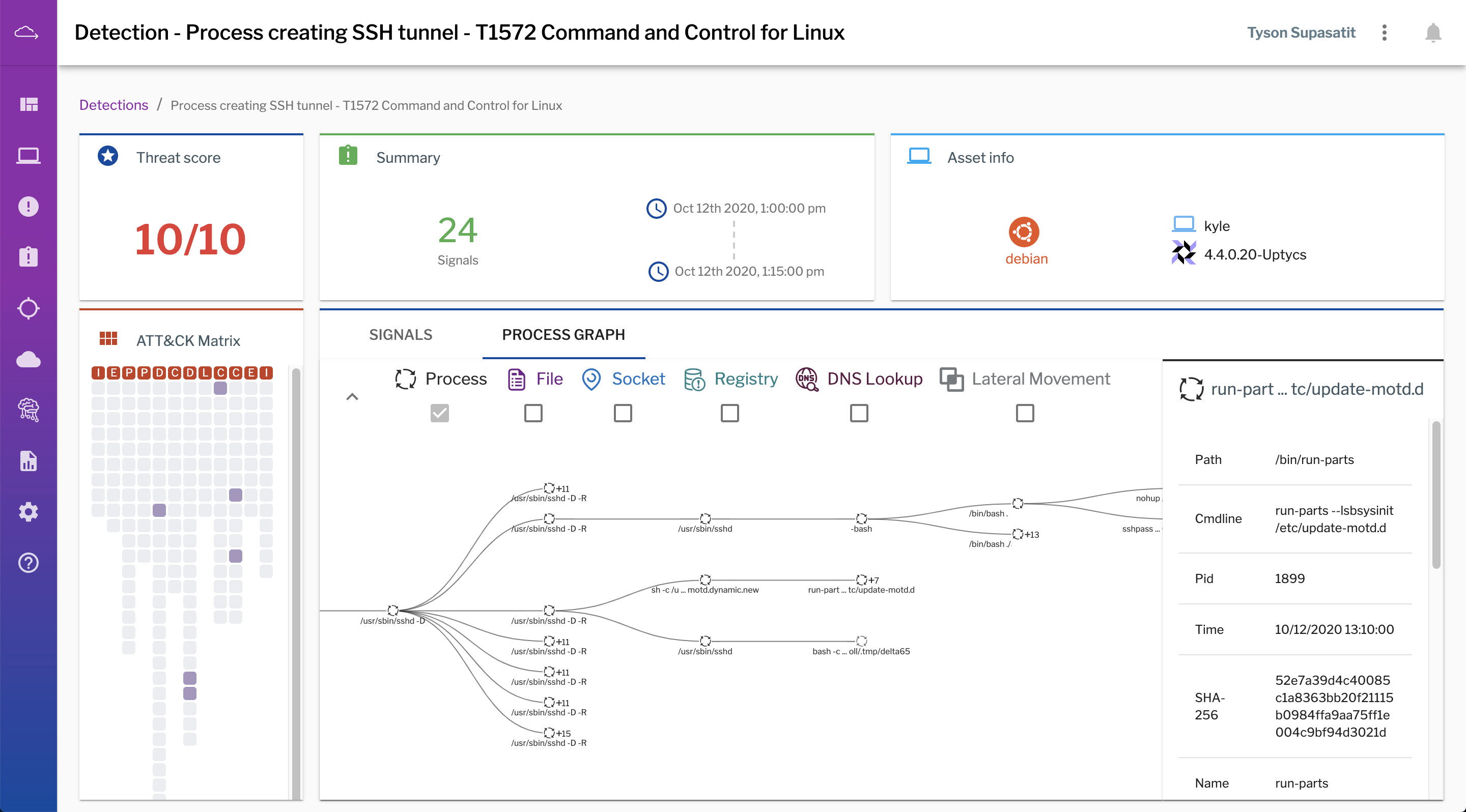
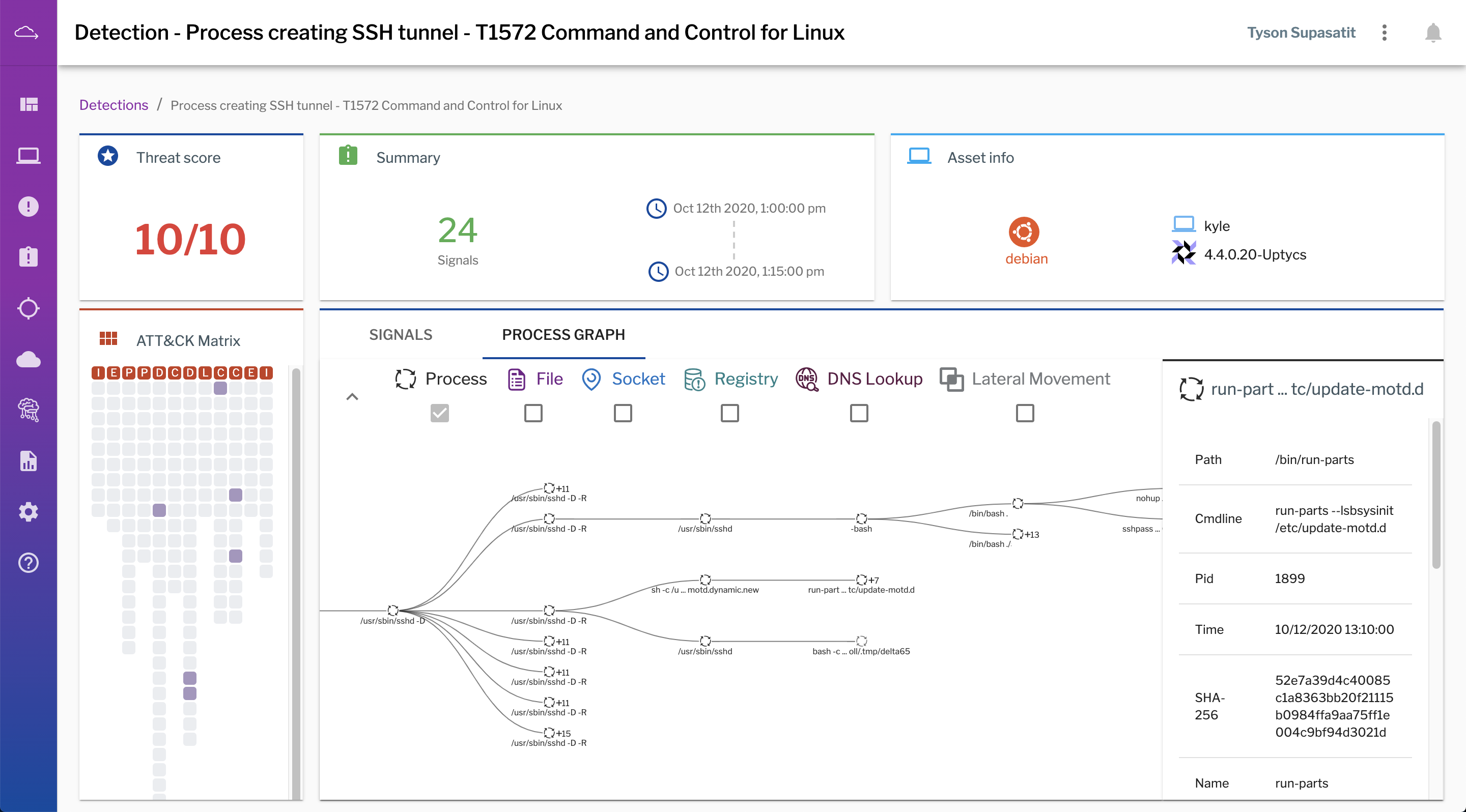
In this screenshot from the Uptycs interface, an easy-to-understand process graph helps analysts see the parent-child relationships of processes involved in a detection, as well as artifacts involved: files opened, created, and deleted; sockets connected; DNS lookups; user logins and privilege escalation; and registry entries manipulated.
Detection + Investigation = Analyst Sanity
Detection alone is not enough. Many security tools will tell you something is wrong, but few will tell you why and how. Our customers love the Uptycs platform because it gives them the ability to ask questions of their laptops and server fleets and easily get answers for fleet visibility, compliance, detection, and investigation.
The new release from Uptycs will do wonders for your SOC analysts. First, MITRE ATT&CK mapping, threat scores, and a process tree graph give analysts greater context to quickly determine if a detection is legitimate or not. If it’s a valid incident, they can continue their investigation in the Uptycs platform using pre-built and custom queries. Unlike traditional EDR solutions that are built to collect predetermined datasets, and therefore dictate the answers that can or cannot be retrieved, the Uptycs platform enables analysts to ask real-time and historical questions of their endpoints across hundreds of system attributes. The upshot is that analysts aren’t forced to hunt for needed answers elsewhere, such as in server logs, network packets, or other sources.
Uptycs offers another advantage for incident response teams: It is increasingly important for analysts to be able to reconstruct machine state for ephemeral cloud workloads that may run for hours or minutes. Uptycs makes this possible by storing machine state in a Flight Recorder so analysts can “go back in time” to perform forensic investigations on machines that are no longer running.
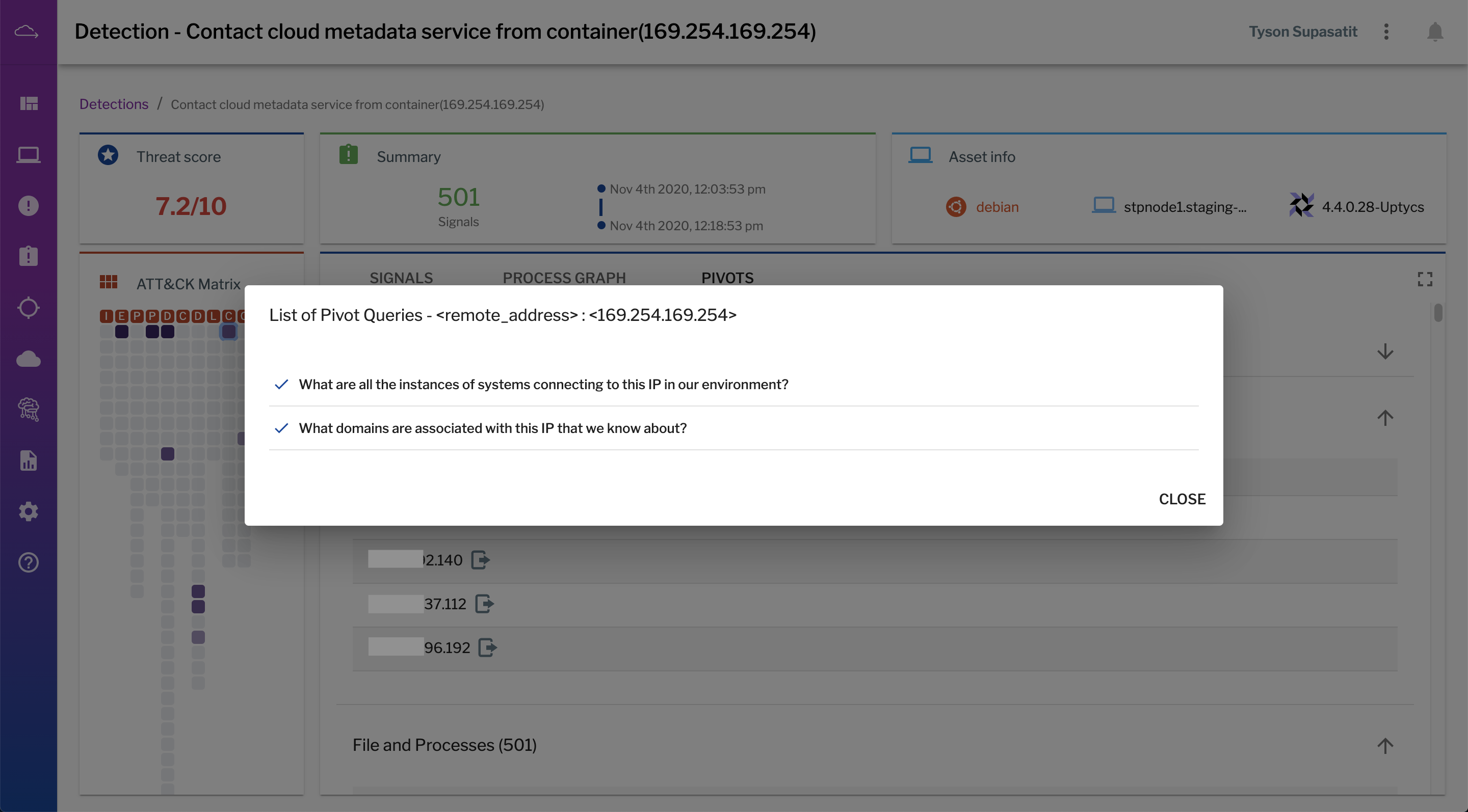
For artifacts associated with a detection—such as file hashes, users, IPs, and domains—Uptycs presents analysts with pre-built pivot queries to give them a head start on investigation.
The case for a unified endpoint data platform
SOC teams need to detect threats and operational risk across the entire IT estate—and they shouldn’t have to purchase one tool to cover their Mac and Windows endpoints, then another for their Windows and Linux servers, and yet another for their containers and cloud workloads.
Notice I added "operational risk" here. At Uptycs, we believe an endpoint platform should detect not only attack activity but also misconfigurations, vulnerabilities, and other operational issues that represent potential future risk, assigning them a threat score and providing host-based details needed for fast remediation—across laptops, servers, and containers.
The tool sprawl that can result from having to cover disparate environments not only increases cost and complexity for your organization, but it also introduces challenges to the incident response process. The pain is most acute during investigations when analysts need to correlate activity across their on-premises and cloud environments. Of course, attackers do not pay attention to these boundaries, but many security teams are forced to do so because of their tooling.
With Uptycs, security and IT teams have a single, unified platform that collects, aggregates, and analyzes telemetry from all types of computer hosts—whether they’re laptops, servers, containers, or ephemeral machine images in the cloud. To detect threats across all of these environments, Uptycs uses behavioral detections as well as real-time and historical correlations against 100+ threat intelligence feeds and IOC sources. Users can also build their own detections and add proprietary threat feeds. Structured data in Uptycs is accessible through SQL tables for real-time and historical queries, as well as through dashboards and visualizations.