The results for the 2020 ATT&CK Evaluations for Enterprise, performed by MITRE Engenuity, are out, and we’re excited about our participation and our journey as we were evaluated against the best solutions in the world. Based on the feedback during the evaluation process alongside measurable outcomes, we are delighted with our performance during our initial evaluation [read our press release here].
Notably, in addition to surfacing key indicators of behavior, attacks, and compromise, Uptycs linked the lateral movement of the attackers as they moved from host to host throughout the entire attack campaign.
Description of the 2020 ATT&CK Evaluations for Enterprise
MITRE Engenuity’s most recent ATT&CK Evaluation round is the first to look at the behavior of financially motivated criminal groups, in this case Carbanak and FIN7, both of which target retail and banking companies. Previous evaluation rounds simulated the behavior of APT3 (2018), attributed to China's Ministry of State Security, and APT29 (2019), attributed to the offensive cybersecurity arm of the Russian government.
View the 2020 enterprise evaluation results.
During the simulation for Carbanak and FIN7, a few details stood out about the attackers’ behavior:
- They used a malicious .rtf file to compromise the initial system, bypassing Windows User Account Control (UAC).
- For the most part, they used a “living off the land” strategy to avoid detection. For example, they used native Windows tools to move laterally (RDP, psexec, etc.) By using the binaries already on the system, the attackers avoid having to create any additional code or binaries that can trigger alarms.
- Largely, they target Windows environments but they can pivot off of Linux machines as well, emphasizing the need for EDR solutions to offer robust multi-OS coverage.
In this video, Amit Malik, head of threat research at Uptycs, describes the Day 1 activity observed for Carbanak+FIN7.
Why MITRE Engenuity’s ATT&CK evals matter: quantitative demonstration
At Uptycs, we believe that too much in the EDR world is black-box analytics obfuscated by marketing messaging, making it difficult for buyers to measure the capabilities of a product. The MITRE Engenuity’s ATT&CK Evaluations offer an even playing field for vendors to transparently and quantitatively demonstrate their capabilities.
The ATT&CK knowledge base itself is sourced from the community based on real-world observations. Anyone can go to the ATT&CK website and read the details of a particular sub-technique, along with documented examples, and then determine their coverage (and gaps). Uptycs advocates for this type of transparency in the industry, and our users can similarly view the configurations for the hundreds of event and alert rules in the Uptycs platform describing these techniques in the ATT&CK knowledge base. Similarly, for each detection, users can see what signals contributed to that detection, how they are correlated, and what tactics and techniques they map to on the MITRE ATT&CK matrix.
From the Uptycs homepage, users can see the amount of host and cloud resource telemetry streaming into the backend. In some of our large customers’ environments, this can be billions of points of telemetry per day, such as process or socket events. Much of this activity is benign, but Uptycs ingests and correlates it all.
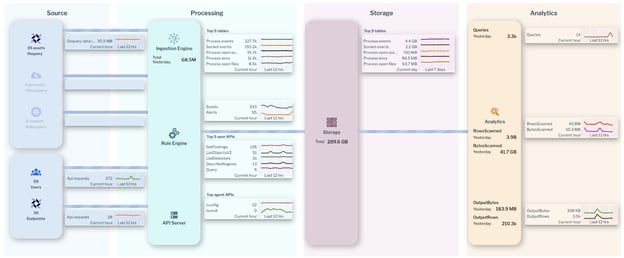
Figure 1. The Uptycs platform is capable of ingesting billions of points of telemetry and applying real-time streaming analytics to narrow that data down to hundreds of detections. (Click to see larger version.)
Of these events, Uptycs will generate thousands of signals (events and alerts) that are correlated and narrowed down to perhaps a hundred detections that potentially represent malicious behavior. All of this is transparent and measurable in the Uptycs platform, providing our customers with confidence in the capabilities of our platform: We’re happy to show you in a proof-of-concept engagement!
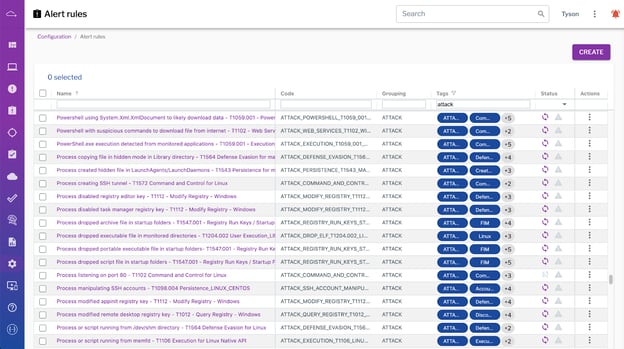
Figure 2. Users can examine event and alert rules in Uptycs to understand how they work, including hundreds of rules describing MITRE ATT&CK techniques. (Click to see larger version.)
Detection is necessary, but it’s not enough
MITRE Engenuity’s ATT&CK Evaluations measure the number and classification of detections during the simulation, but equally important in our view is the presentation of these signals to the analyst and the ease with which they can pursue investigations.
Uptycs not only offers 500+ indicators of behavior describing MITRE ATT&CK techniques, but also maps them in our UI. We offer an overview of threats detected across the endpoint fleet mapped to the ATT&CK matrix, providing a high-level visualization of possible threats to be validated. For individual detections, we also offer a visual indicator of where signals in the detection fall on the ATT&CK matrix. These types of visualizations give analysts context about the possible scope and severity of threats, and help them to prioritize their time (an analyst’s most precious resource).
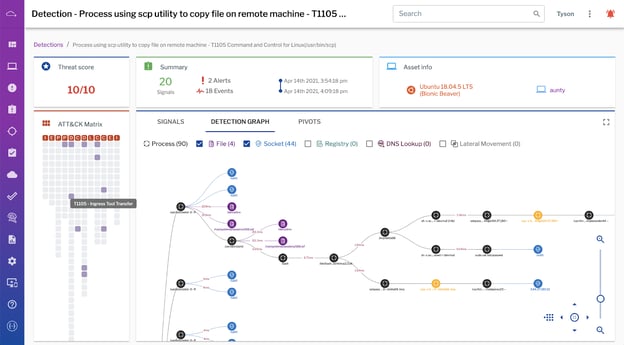
Figure 2. Detections in Uptycs offer a visual indicator of where signals that comprise that detection fall on the MITRE ATT&CK matrix. (Click to see larger version.)
The “R” in EDR comes into play after an analyst validates a detection and logs it as a security incident. Sure, some threats will be automatically blocked on the spot, but EDR products ought to be supporting the full incident response lifecycle. This is where Uptycs shines, as it not only stores and correlates telemetry associated with a detection, but all system activity—even for machines that are no longer running, such as ephemeral container workloads.
With telemetry available for real-time and historical querying, incident response teams can:
- Quickly track lateral movement to understand what systems and data were affected
- Hunt for indicators of malicious behavior and outliers in the environment—both currently and in the past
- Obtain forensic evidence by carving portions of files and memory from running processes
Much of this investigation work is automated in Uptycs so that incident responders have a head start in their work. For example, each detection in Uptycs has pivot points that analysts can use to search for associated hashes, domains, and users elsewhere in the environment. Our threat detection graphs show jumping off points for lateral movement, allowing analysts to follow attackers’ virtual footprints from one host to another.
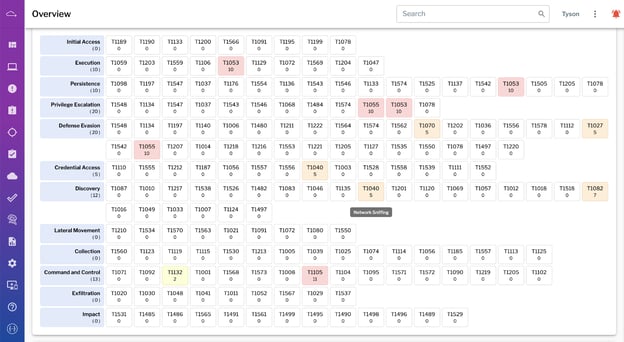
Uptycs maps detections to the MITRE ATT&CK knowledge base. This overview visualization is one example, providing a high-level summary of possible threat activity across the endpoint fleet. (Click to see larger version.)
Conclusion
We are happy to support transparency efforts in the industry such as the ATT&CK Evaluations performed by MITRE Engenuity, and are proud of our performance in the 2020 evaluation for Carbanak and FIN7. EDR is an important use case for our customers because even as new attack surfaces emerge, organizations still need visibility into traditional laptop and server endpoints. EDR is one of the key solution areas for the Uptycs security analytics platform along with cloud workload protection, cloud security posture management, audit and compliance, vulnerability management, and more.




-Dec-01-2022-08-10-42-5576-PM.png?width=352&name=Untitled%20design%20(4)-Dec-01-2022-08-10-42-5576-PM.png)

