Juno AI Analyst
Our Juno AI Analyst is a fully integrated Security AI Analyst, built to help cybersecurity teams
interpret complex detection data, accelerate investigations, and verify every conclusion.
No black boxes.
Investigate faster. Trust the output. Rest easy.

Uptycs gets even better with Juno
Juno leverages the unified platform: single security console, policy frameworks
and data lake of Uptycs to create detailed analysis with actionable security findings.

Why Juno?
Security teams have to navigate constant noise: false positives, false alarms.
Traditional AI tools promise help, but they often deliver more confusion. Juno is different.
Our Customer Experience team is always on-hand to help fine-tune and optimize your strategy to improve efficiency and maximize your investment.
Every finding is backed by real queries, real evidence, and step-by-step logic - all without ever using your telemetry for training. Your data stays yours and every finding is fully verifiable.
Built on Anthropic's Claude via AWS Bedrock - delivering private, configurable deployments with no training on your data and full compliance alignment.
Built for how real teams investigate threats, triage alerts, and respond at scale - delivering clarity, consistency and faster decisions.
Secure Your Hybrid Cloud from Dev to Runtime
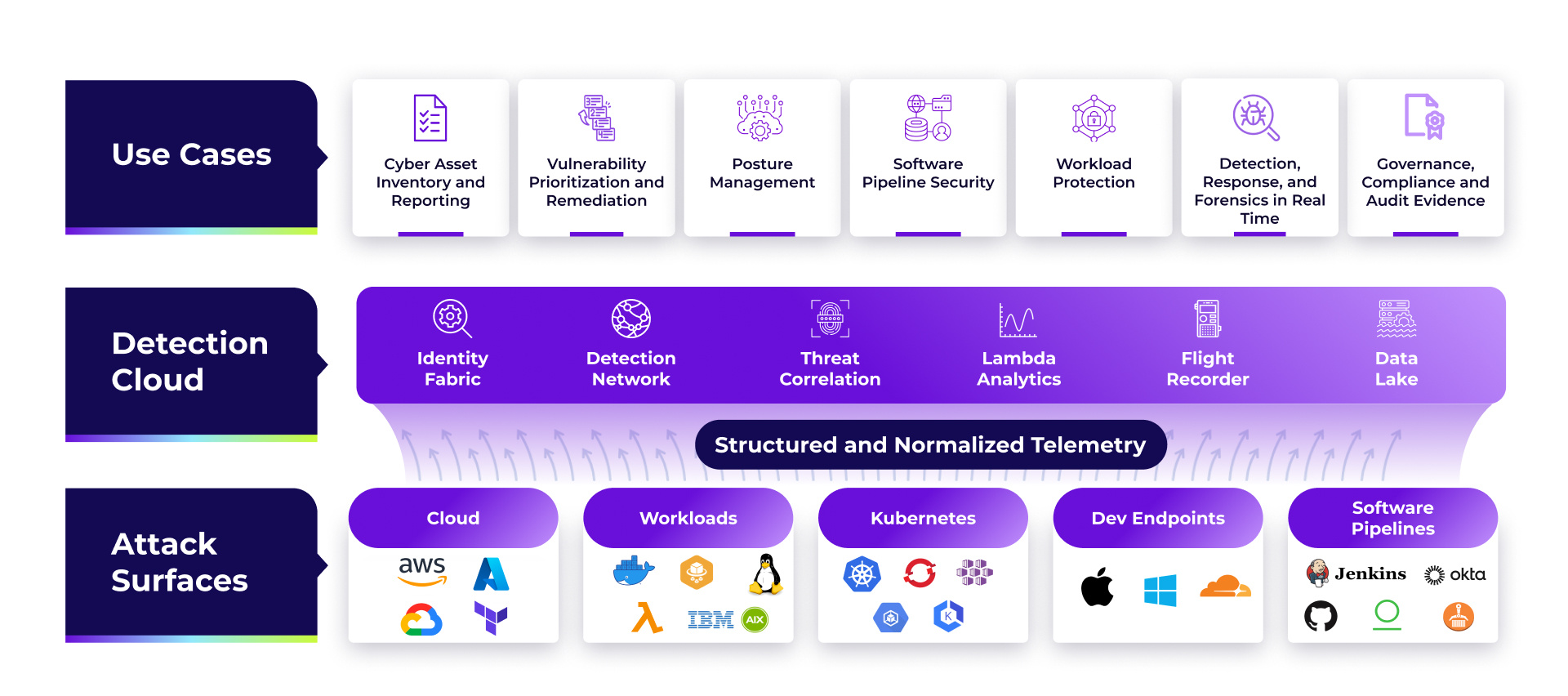
The Uptycs Approach to Cloud Security
1
Structured telemetry
Collect and normalize telemetry close to its source.
2
Cloud power
Deliver security analytics and alerts in real time.
3
Standards and APIs
Base data models and modes of interoperability on standards, using an API-first approach.
4
Unified data model
Simplify workflows and boost correlations with a single source of truth for all security data.
5
Effortless Scalability
Scale seamlessly from hundreds to millions of workloads.
Juno vs Traditional AI Tools
Feature
Juno AI
Traditional AI
Works with What You Have
You rely on an existing suite of tools, and adding a CNAPP shouldn't complicate your
team's work. That's why Uptycs works seamlessly with your existing tech stack.


What Users Are Saying
“Uptycs was deployed on a large scale as a key component of our security posture.”
“Uptycs has been instrumental for our FedRamp authorization and ISO 27001 certification.”
“Uptycs helps me sleep better at night.”
“A unified view from which we can quickly ask and answer security questions across our environment.”
“Uptycs simplifies investigations and saves time—about 30% per investigation.”
“I would not want to do security anywhere without this level of visibility.”
“Uptycs enables us to make risk-based decisions.”
“Uptycs contextualizes threat activity across K8s, cloud services, and laptops. We've dramatically shortened our threat investigation time.”
See Juno in action
Juno is the latest evolution of the Uptycs platform – trusted by enterprises for unified visibility across cloud, workloads, containers, and endpoints.
Ready to see how Juno works in your environment?
See Juno in Action








