We’re happy to announce the addition of blocking and remediation capabilities to our EDR offering. This has been a popular feature request from our customers, many of whom purchased Uptycs for its industry-leading threat detection and investigation capabilities but would now like to go further with enhanced response functionality.
Real-Time Remediation for CSIRT
One of the reasons security teams love Uptycs is the ability to observe real-time system activity. This is crucial during incident response when analysts suspect the presence of malware or an active adversarial operator.
Now, in addition to observing real-time system activity in detail (scanning or carving the memory of running processes) incident responders can take action to kill or pause malicious processes or delete malicious files. Users with sufficient permissions can also quarantine or shutdown a host, or disable a user account.
Traditional EDR vendors require incident responders to take action via terminal commands, but we’ve integrated these real-time actions into the Detection UI so that incident responders have MITRE ATT&CK-enhanced context for the real-time action they are taking.
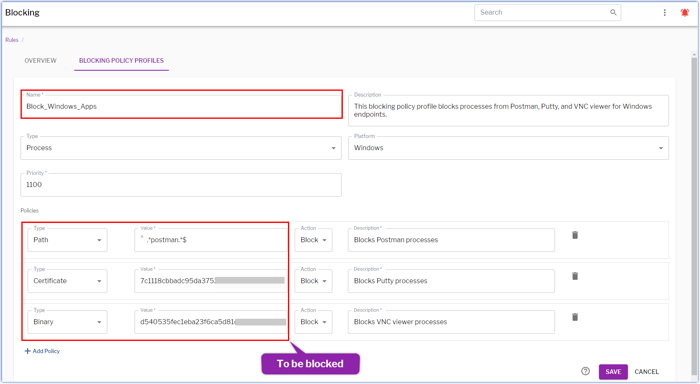
This example shows a blocking policy that would prevent Postman (a collaboration platform for API development), Putty (an open-source terminal emulator), and VNC viewer (a remote access application) from running.
Finally, because Uptycs is an API-first product, sophisticated Security Operations teams can easily create Security Orchestration, Automation, and Response (SOAR) workflows to trigger policy-driven responses.
Mitigate Threats in Real-Time, Without Waiting For IT
Security and compliance teams often rely on their counterparts in IT to remediate incidents and compliance policy violations. Uptycs now empowers these teams to rapidly contain and remediate immediate issues during an active threat, or simply remediate a compliance issue such as a Windows registry fix, while the IT team can focus on software or configuration updates.
Security teams can use the new blocking functionality to mitigate risk from urgent threats and prevent them from spreading (e.g. implementing policies to block malicious processes or domains).
“With Great Power Comes Great Responsibility”
We also understand that some people are hesitant about automated blocking on critical systems for fear of disrupting business. Those are valid concerns, and why the Uptycs Protect add-on is an optional software download—if you don’t want even the possibility of an agent interfering with critical systems, then you can install only the core Uptycs osquery-based agent that runs in read-only mode.
Uptycs has also included several features that help endpoint security teams to minimize risk when rolling out new blocking rules:
- Back-testing - You can back-test/pre-flight blocking rules against historical system telemetry to see what impact the rule might have had across your endpoint fleet. This is a unique capability that’s made possible because Uptycs stores and analyzes data in the cloud, and it’s not possible with EDR solutions that lack a cloud-based backend.
- Log-only mode - You can enable blocking rules in a log-only mode to evaluate the impact of the rules over a period of time. This enables you to iterate and reduce false positives using production data without risk of breaking anything.
- Sophisticated blocking profiles - You can minimize the scope of blocking rules by creating sophisticated profiles, keying in on domains, SHA file hash, file path, and signing certificates.
- Allow-list mode - If desired, you can lock-down what is possible on a host by only allowing certain processes (binaries, signing certificates, etc).
Yet Another Reason to Consolidate Tools With Uptycs
The Uptycs Security Analytics Platform offers one platform with multiple solutions for XDR, CWPP, CSPM, asset insights and inventory, and audit and compliance. Many organizations have a number of tools targeting their productivity endpoints, server endpoints, and cloud-native applications.
With new blocking and remediation functionality, Uptycs offers an even more robust option for supporting these heterogeneous environments, helping businesses save money and streamline their operations.
Read how Flexport, which is building a platform for global logistics, uses Uptycs to secure its laptop fleet, server workloads, and cloud infrastructure:
Flexport Empowers DevOps Teams with Security Observability