IBM Cloud Partnership: Secure the Cloud Together
Uptycs now extends our Continuous Threat Exposure Management (CTEM) framework to IBM Cloud, becoming the first and only provider to offer a truly comprehensive CTEM solution for IBM environments.
With this integration, IBM Cloud customers gain continuous visibility, contextual risk prioritization, and proactive remediation across workloads, identities, configurations, and Kubernetes resources — powered by the same unified telemetry that secures AWS, Azure, and Google Cloud.
Our cross-OS coverage supports AIX, LinuxOne, zLinux and Linux on Power, giving enterprises consistent protection for mission-critical workloads. Combined with deep Linux telemetry — validated by our #1 ranking in the Linux EDR Telemetry Project — organizations can continuously detect and mitigate threats across IBM’s infrastructure stack with confidence.
Elementum cras viverra placerat
Feature one here
Non massa sapien porta malesuada ex placerat nam eget luctus nibh elementum consectetur at. Donec sit efficitur laoreet.
Feature two here
Non massa sapien porta malesuada ex placerat nam eget luctus nibh elementum consectetur at. Donec sit efficitur laoreet.
Feature three here
Non massa sapien porta malesuada ex placerat nam eget luctus nibh elementum consectetur at. Donec sit efficitur laoreet.
Feature four here
Non massa sapien porta malesuada ex placerat nam eget luctus nibh elementum consectetur at. Donec sit efficitur laoreet.
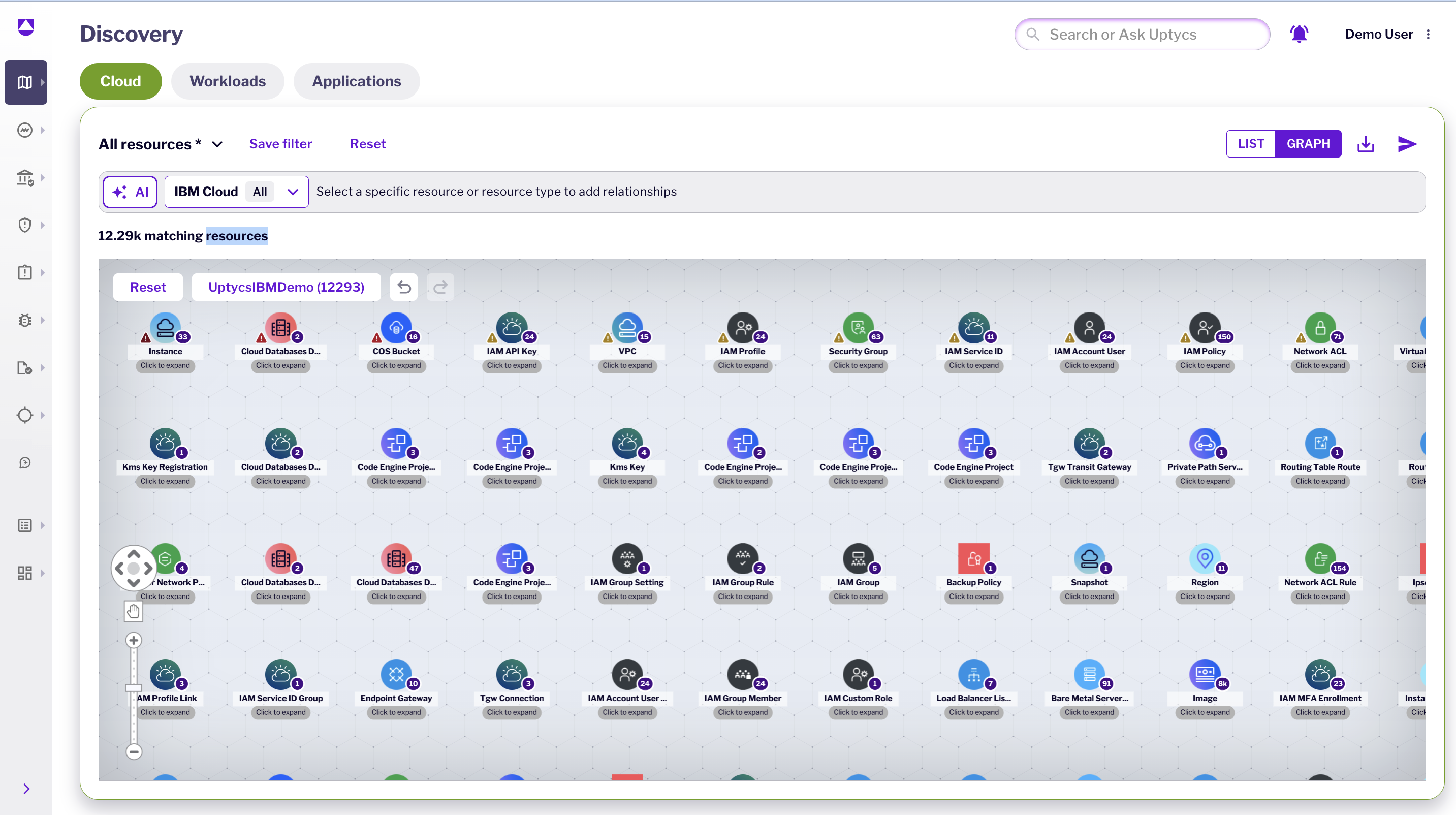
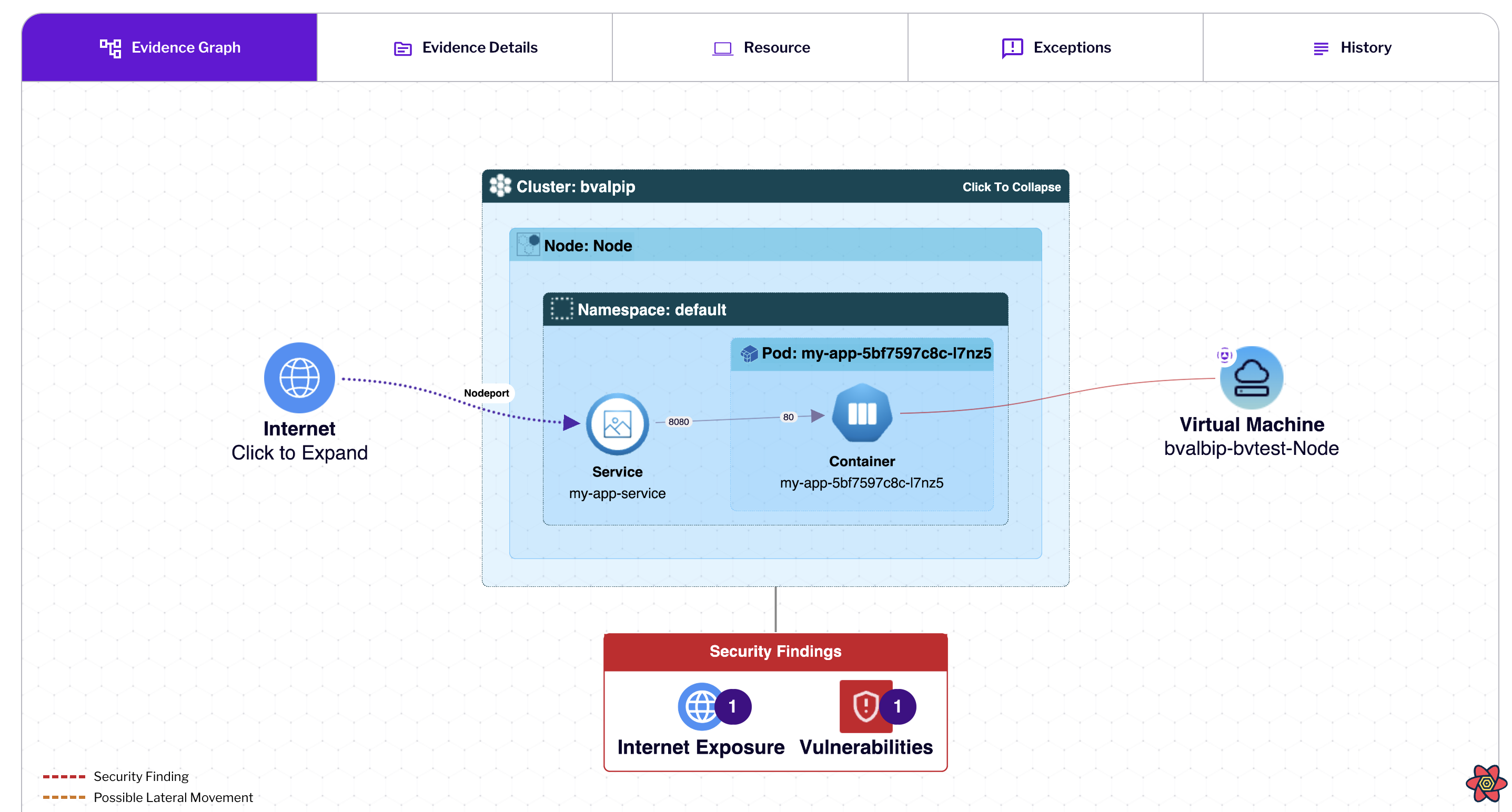
AWS Dashboard Overview
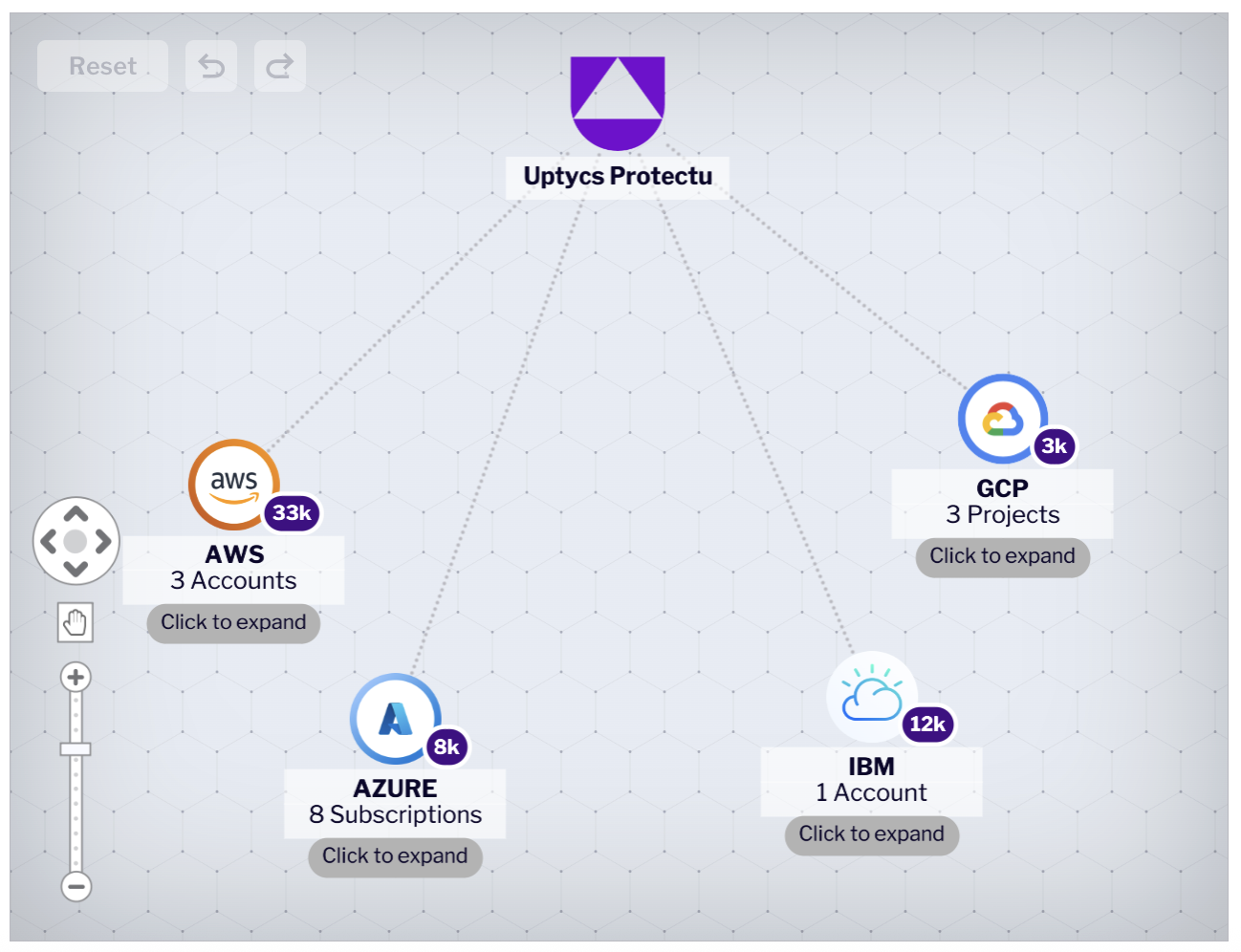
Uptycs Protects Your IBM Cloud Resources
Workload Protection (CWPP)
Workload protection in IBM environments presents unique challenges due to the diversity of operating systems. Our CWPP solves this by extending protection to:
-
AIX: Monitoring for misconfigurations, vulnerabilities, and runtime anomalies.
-
LinuxOne & zLinux: High-fidelity telemetry, behavioral analytics, and EDR coverage.
-
Linux on Power: Linux® applications taking advantage of POWER® hardware performance, availability, and reliability.
-
Containerized Environments: Runtime visibility and compliance in Kubernetes and OpenShift deployments.
Posture Management (CSPM)
-
Map configurations against compliance frameworks and security best practices.
-
Identify and prioritize posture gaps that increase exposure.
-
Automate fixes and verify continuous compliance without manual intervention.
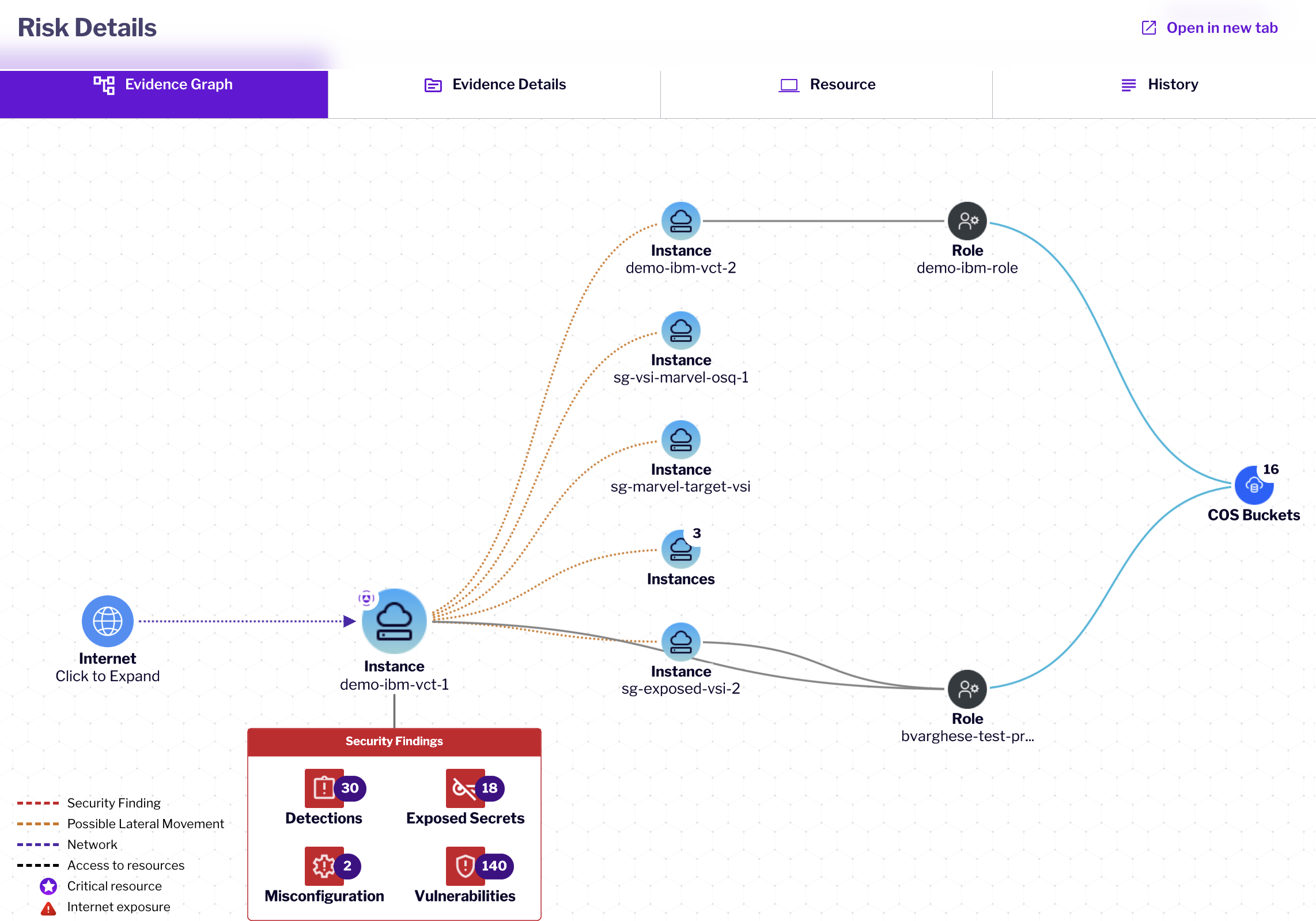
Identity and Entitlement Management (CIEM)
-
Discover over-privileged identities and risky access patterns across users, service IDs, and roles.
-
Visualize relationships between assets, identities, and permissions in a unified risk graph.
-
Apply least-privilege principles across hybrid and multicloud environments.
Kubernetes Security Posture Management (KSPM)
-
Analyze configurations across clusters, pods, and namespaces for misconfigurations or drift.
-
Detect runtime risks, privilege escalations, and identity misuses in containerized workloads.
-
Correlate cloud, container, and identity signals to uncover hidden attack paths.
Success Stories
“Uptycs was deployed on a large scale as a key component of our security posture.”
“Uptycs has been instrumental for our FedRamp authorization and ISO 27001 certification.”
“Uptycs helps me sleep better at night.”
“A unified view from which we can quickly ask and answer security questions across our environment.”
“Uptycs simplifies investigations and saves time—about 30% per investigation.”
“I would not want to do security anywhere without this level of visibility.”
“Uptycs enables us to make risk-based decisions.”
“Uptycs contextualizes threat activity across K8s, cloud services, and laptops. We've dramatically shortened our threat investigation time.”





