Cloud Security Posture Management (CSPM)
Prioritize and remediate risks and misconfigurations across AWS, GCP, and Azure cloud environments with rich context across runtime, identity, network, data and business insights. Start with agentless scanning for quick ROI and optionally extend to deep runtime visibility through eBPF sensor based approach for efficient risk prioritization.
Revealed: The Biggest Threats to Your Cloud Workloads
Establish Pathways For Continuous Monitoring
and Hardening Of Your Cloud Environment
To Lower Risk and Increase Compliance
Our Customer Experience team is always on-hand to help fine-tune and optimize your strategy to improve efficiency and maximize your investment.
Uptycs enables security teams to prioritize the most critical risks and compliance issues in your hybrid cloud environment by correlating business context with insights from runtime vulnerabilities, identity, network exposure, malware threats and development pipeline. Map potential attack paths to your critical assets across your cloud environment.
Answer key questions to assess the threat boundaries, networking & IAM relationships, and security findings across your entire multi-cloud estate with the ability to customize such findings based on organizational context.
Out of the box behavioral detection rules and alerts using Cloud logs for key services with the ability to auto-remediate. Consistently apply policies in your development pipeline using IaC Scanning on your Terraform, CloudFormation, Azure Templates and more such tools.
Continuous Posture Management: Proactive Layered Defense
Hybrid cloud sprawl demands constant vigilance. Uptycs CSPM empowers a proactive layered defense, continuously monitoring and optimizing your cloud security posture management as your environment scales and evolves. Gain control and stay ahead of threats with Uptycs.
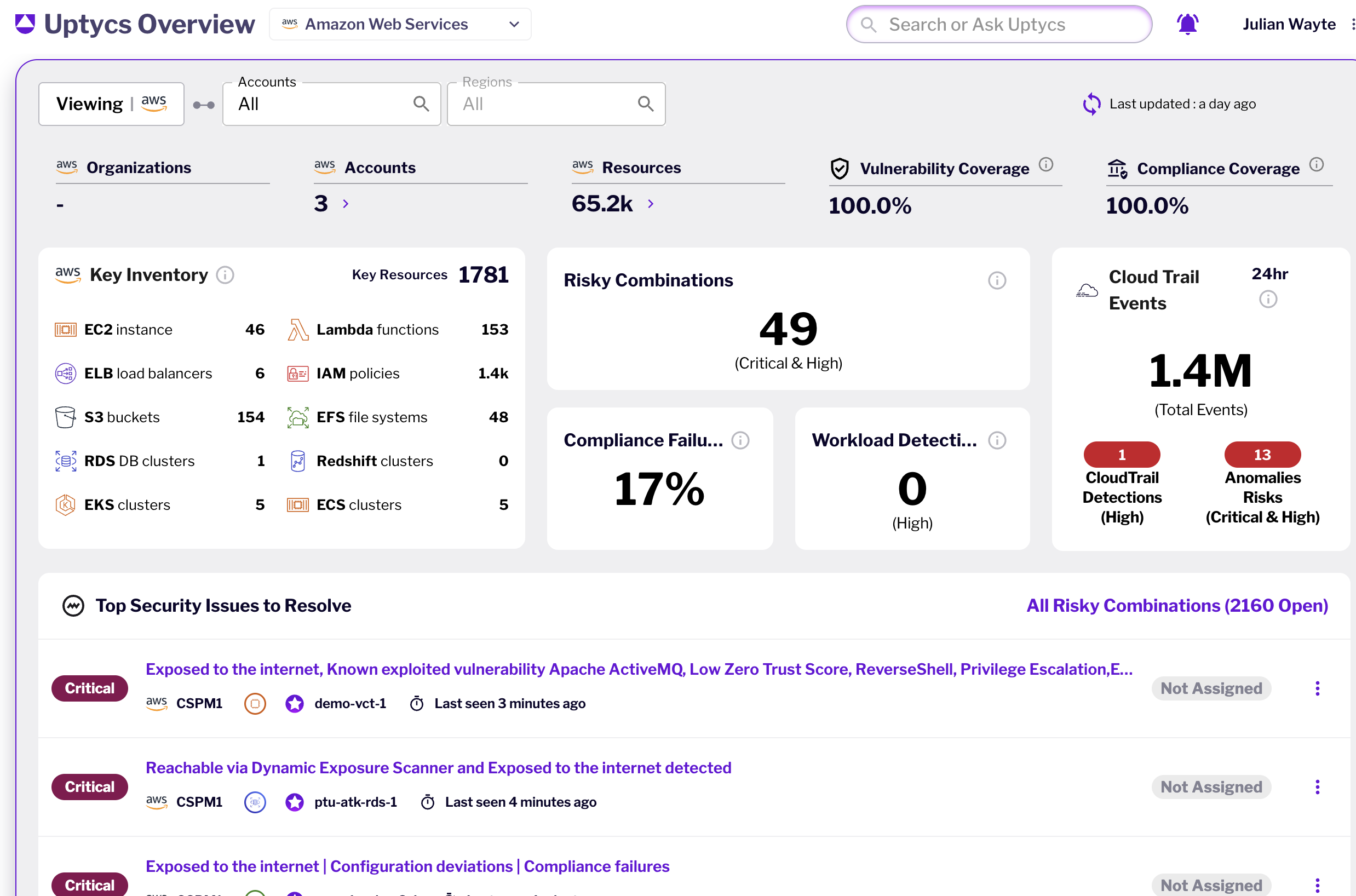
Powerful scanning, detection, and
remediation tools for the hybrid cloud
Real-time Posture Management and Remediation
-
Unified posture management: Optimize your security posture across all cloud environments, workloads, and software pipelines
-
Real-time cloud inventory & monitoring: Ensures you always have current information & detects modifications via contextual analysis using Cloud Audit Logs and optional eBPF based telemetry
-
Dynamic Cloud Discovery: Gain visibility into your cloud network topology, unwanted shadow communication, visualize who can access what
-
Streamlined misconfiguration alerting and remediation: Leverage contextually rich and extensible misconfiguration rules across AWS, Azure and GCP control plane, and runtime workloads, complemented with IaC scanning in build-time
Mitigate Cloud Risks through Unified Context
-
Contextual risk prioritization: Focus on the most critical issues with contextualized vulnerabilities, misconfigurations, runtime behavior, sensitive data and software pipeline to the cloud
-
Attack path analysis: Protect your high-value assets by uncovering potential hidden connections, attack paths and risky combinations overlayed with real-time threat and exploit information
-
Identity & Network Exposure: Detect internet exposure and potential lateral movements with correlated insights from Uptycs dynamic exposure scanner and identity risk engine.
Tailor Compliance To Your Organizational Needs
-
Continuous Monitoring: Support for key standards such as SOC2, HIPAA, CIS, PCI and more with continuous monitoring across any workload, cloud, Kubernetes, and software pipeline
-
Customizable Reporting: Combine and modify different out of the box standards with the ability to add different rules custom tailored to meet your organizational needs
-
Remediation In Runtime and Buildtime: Remediate key compliance issues automatically in real-time
Detect and Respond To Cloud Threats With Context
-
Real-Time Threat Correlation and Hunting: Uncover hidden threats correlating runtime signals, cloud activity, and audit logs complemented with identity analytics
-
Anomaly Detections: Spot outliers/anomalies in your cloud environment, investigate the behaviors across logical boundaries through cloud threat investigation
-
Cloud-Native Response: Leverage forensics and threat hunting to understand the blast radius of an attack across cloud environments and running workloads.
Works with What You Have
You rely on an existing suite of tools, and adding a CNAPP shouldn't complicate your
team's work. That's why Uptycs works seamlessly with your existing tech stack.


Success Stories
“Uptycs was deployed on a large scale as a key component of our security posture.”
“Uptycs has been instrumental for our FedRamp authorization and ISO 27001 certification.”
“Uptycs helps me sleep better at night.”
“A unified view from which we can quickly ask and answer security questions across our environment.”
“Uptycs simplifies investigations and saves time—about 30% per investigation.”
“I would not want to do security anywhere without this level of visibility.”
“Uptycs enables us to make risk-based decisions.”
“Uptycs contextualizes threat activity across K8s, cloud services, and laptops. We've dramatically shortened our threat investigation time.”






