As cloud adoption accelerates, so too will the complexity of managing it. Being able to monitor your misconfigurations and map current configuration statuses to security control frameworks or regulatory standards is key to anyone who takes their cloud security strategy seriously. Trying to do this with only the cloud provider tools is challenging at best.
This challenge increases tenfold if you have a multi-cloud strategy. You should consider employing a dedicated cloud security tool that can focus on behavior-based threat detection so that you can focus more on your core business rather than have cloud security become your core business.
Compliance ≠ Security In The Cloud As Well
Cloud Security Posture Management solutions approach cloud security in a very binary way —“this is misconfigured in your account”; “your configuration has drifted from framework xyz”; “your data store is open to the world.” But this only tells part of the story by looking at it through the lens of what a company or framework has deemed to be “appropriately configured” within an environment. By following this, at best your company will meet compliance/regulatory requirements but still be susceptible to a threat actor escalating privileges, exfiltrating data, targeting you for ransomware.
Case in point: the Capital One breach of 2019. Financial institutions have some of the strictest compliance/regulatory requirements in the world. We can only assume they were “appropriately configured” across all their compliance/regulatory responsibilities, but yet they were victims of data exfiltration. Threat actors today have become cloud experts. Their TTPs are evolving quicker than most want to believe. Therefore it's time we start thinking like them and mimicking detection on their attack behavior.
Identifying Opportunities For Behavioral Detection In The Cloud
When (not if) a threat actor steals credentials to your cloud environment, time is of the essence to be able to achieve their goal (escalate privileges; exfiltrate data; destroy resources; deploy ransomware). But before they can execute on their goal they need to determine whose credentials they have, what the permissions associated with the credentials are, and what all they have access to. We can analogize this by imaging a large house (your cloud account) which is pitch black on the outside and the inside.
The threat actor gains access to your house but needs to understand which rooms they have access to by testing all the doors (reviewing permissions); finding the room that has the stairs so they can navigate to the second floor (escalating permissions). In other words, they’re “feeling out the account” to understand what all they have access to which then determines what all they need to do to be able to continue on their objective. Let’s call this performing reconnaissance on the account.
The reconnaissance phase of a threat actor is where we should be prioritizing our detection efforts because it’s our opportunity to detect and take action before the attack progresses further with privilege escalation, data exfiltration, resource termination, or deploying ransomware. At Uptycs, we’re collecting a wealth of telemetry from the cloud environment and analyzing those signals to identify reconnaissance actions that threat actors will typically perform as they determine their next moves.
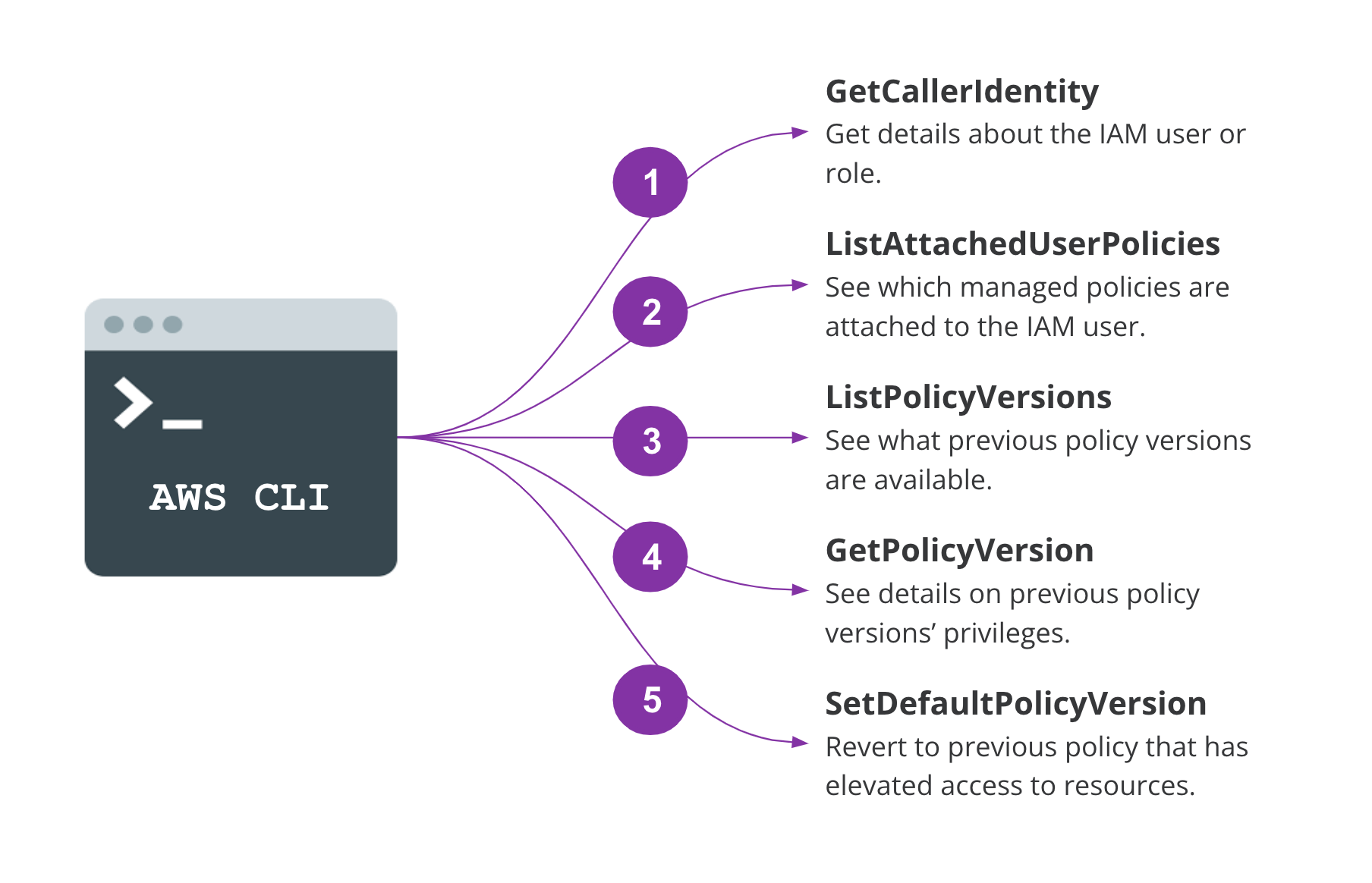
What does this look like in practical terms? Let’s assume a threat actor has discovered an access key (from GitHub, Bitbucket, GitLab, etc.) for an IAM principal. The threat actor needs to know who the IAM principal their stolen access key access key is associated with. To accomplish this, they will use the CLI command aws sts get-caller-identity to return the user ID, account ID, and IAM ARN/name from the GetCallerIdentity AWS API. It’s very rare that a legitimate customer will make this call in their own account and it presents just one opportunity for detection of reconnaissance activity.
There are many other similar actions that present an opportunity for detection. In the video below, I show what we mean by reconnaissance and privilege escalation within an AWS account:
To Learn More About Going Beyond CSPM, Click Here To Request A Demo
Go Beyond Compliance To Cloud Detection And Response
At Uptycs, our aim is to provide Security teams with greater confidence about their cloud security posture. Cloud security posture has both proactive and reactive elements. We believe that proactive checks against frameworks such as the CIS Benchmarks and PCI-DSS are necessary, but Security teams also need the ability to reactively respond to attack behavior before serious damage is done.
To date, most CSPM tools deliver alerts telling you about misconfigurations and risky policies, but do not have robust cloud detection and response capabilities for active attacks. Both are needed for a mature cloud security posture.
We understand that many Security teams are building out their cloud expertise to keep up with attacks against their cloud environments. We can help. If you would like to learn more about how to deploy cloud detection and response capabilities in your environment with Uptycs, please schedule a consultation.

-1.png?width=200&name=image%20(4)-1.png)