Today, Uptycs is announcing the addition of new cloud detection and response capabilities to our cloud security offering. This feature continuously analyzes AWS CloudTrail logs to detect patterns that match malicious behavior.
I can hear the reader ask, “Wait, do we need another acronym? Don’t we have enough detection and response?” Let’s explore why CDR is an important and necessary next step in cloud security.
Think back to when endpoint detection and response (EDR) became a market. At the time, security teams relied on antivirus software to protect their endpoint fleet. All good, but as we’ve learned, we should assume an attacker has compromised the environment and deploy defense in depth. EDR filled the gap of detecting attackers inside the environment as they went about trying to achieve their objectives, whereas antivirus solutions focused on the initial compromise.
Cloud detection and response offers the same type of defense in depth for cloud environments. While attackers’ high-level tactics remain the same as on endpoints (discovery, privilege escalation, lateral movement, etc.), the specific techniques that they use are unique to cloud environments. Consider the following example:
- An attacker finds long-term credentials to an AWS environment left in application code
- Using the stolen credentials, the attacker uses the CLI to retrieve details about the user whose credentials they've stolen
- Again using the CLI, the attacker lists the policies attached to that user, along with the number of versions of those policies
- The attacker gets details about previous policy versions to find one that has elevated privileges
- The attacker elevates their privileges by reverting to the previous policy version with elevated privileges
All the activities listed above will be recorded in CloudTrail logs, but it would require someone with cloud security expertise to recognize that an attacker was escalating their privileges. A good CDR solution will continuously analyze CloudTrail logs and other telemetry to automatically detect this type of malicious behavior.
Automating Cloud Security Expertise
The Uptycs CDR solution gives your security team superpowers—eyes continuously watching your CloudTrail logs for evidence of attackers who are finding their way around and looking for ways to gain further access.
Unlike other CDR offerings brought to market so far, Uptycs puts far less burden on your staff. Other CDR solutions alert on discrete events that are unusual, but put the burden on your analysts to determine what the alert might mean and whether it is legitimate. The Uptycs solution is different, and only fires a detection when discrete events are correlated and fit a recognizable cloud-focused attack technique.
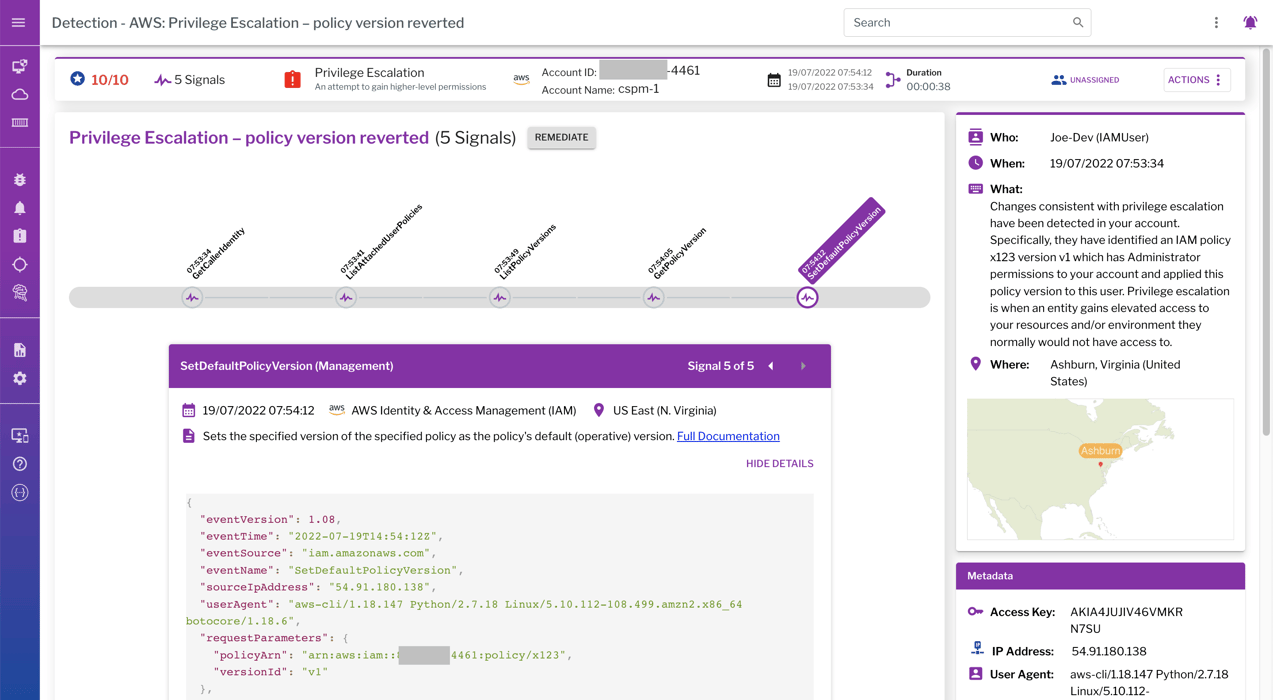 Instead of firing alerts on discrete events, Uptycs only fires a detection when activity matches recognized cloud attack techniques. This screenshot shows the five signals that comprise a privilege escalation behavior by reverting the user’s policy version.
Instead of firing alerts on discrete events, Uptycs only fires a detection when activity matches recognized cloud attack techniques. This screenshot shows the five signals that comprise a privilege escalation behavior by reverting the user’s policy version.
The Uptycs approach to behavioral cloud detections will result in fewer alerts for security teams to triage, more context to help analysts understand the severity of the incident, and also give them a running start on remediation with tailored instructions for each detection. Uptycs CDR capabilities are available as part of our cloud security solution and currently support AWS.
CDR Is a Perfect Complement to CSPM
Cloud security posture management (CSPM) is an essential building block for cloud security, helping you to ensure that your cloud services and assets are configured correctly. It’s analogous to installing good locks on your doors and windows. However, good locks are no use if the thief has a key. Attackers that have stolen credentials are like a thief that has a key to your house. In this case, you need to deploy defense in depth to detect attacker activity inside your environment, and that’s where CDR plays a critical role.
See a Demo of Uptycs CDR
We’d love to show you a demo of our new CDR capabilities. Request a personalized demo to learn how Uptycs can help to reduce risk in your cloud environments.







