Written by: Tyson Supasatit and Jeremy Colvin
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) recently released Shields Up guidance outlining best practices in response to heightened cyber risk. The Shields Up guidance helps teams to begin assessing and prioritizing improvements in their cybersecurity posture. In this post, we break down the four phases described by Shields Up—summarized here as Hardening, Detection, Response, and Resilience—and explain how the Uptycs solution can help. If you are interested in a specific section, please navigate down below.
Furthermore, if there are any technical solutions described here that you want to gain a deeper understanding in or get a hands-on view of immediately, please reach out (jcolvin[at]uptycs.com) as we are happy to discuss a deeper layer of technicality.
Shields Up Section 1: Hardening Your Attack Surface
One of the first steps to create a comprehensive security framework is understanding what you have to protect. Over time, assets naturally require updates or fall out of proper configuration. You can harden your attack surface by updating software and installing patches. This requires a software inventory matched to a list of vulnerabilities. Happily, CISA maintains a list of known exploited vulnerabilities that you should reference—prioritize these patches. You can use Uptycs to find all instances of vulnerable software mentioned in CISA’s list across your laptop and server fleets, as well as your cloud workloads.
CISA recommends protecting cloud services by implementing controls focused on identity and entitlement policies, as they have observed attackers looking to steal credentials to cloud service accounts. Uptycs has developed capabilities in the area of entitlements management and identity analysis that will soon be generally available.
CISA’s hardening guidance mentions requiring multi-factor authentication for privileged and administrative access. These types of secure configurations are codified in the Centers for Internet Security (CIS) benchmarks for operating systems, cloud provider resources, and even systems such as Kubernetes. Uptycs enables you to quickly assess your compliance with checks for CIS Benchmarks for Linux, macOS, Windows, and more. These checks uncover configuration issues that can give attackers an entry point into your network.
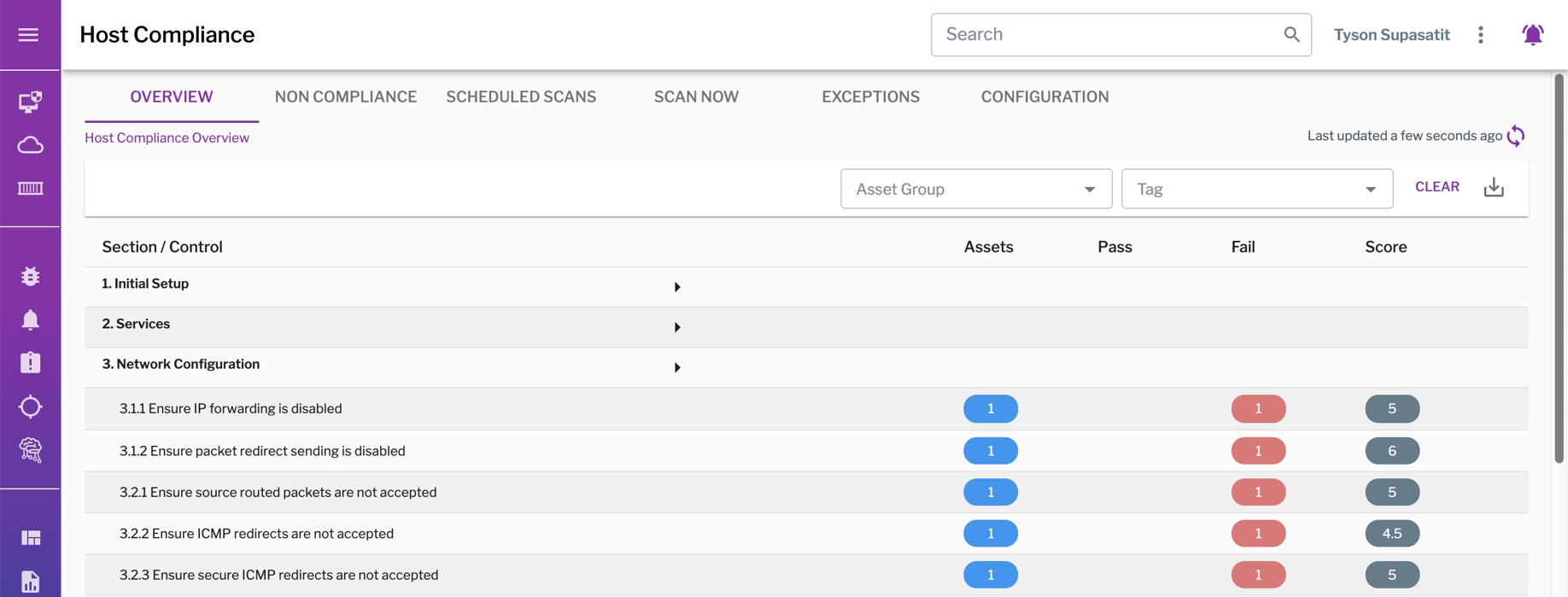 Uptycs performs compliance checks against CIS Benchmarks to ensure secure configurations, such as this one for CentOS Linux 7.
Uptycs performs compliance checks against CIS Benchmarks to ensure secure configurations, such as this one for CentOS Linux 7.
Finally, CISA offers free cyber hygiene services to U.S. government entities and companies providing critical infrastructure, focusing on vulnerability scanning. For ongoing vulnerability scanning, Uptycs can perform periodic scans for vulnerabilities in container images, file systems, and Git repositories using publicly available vulnerability databases.
Shields Up Section 2: Detecting Potential Intrusions
CISA places an emphasis on your organization's ability to quickly and accurately detect potential intrusions as part of a layered security strategy. Uptycs leverages multiple technologies to fine tune your detection capabilities and accurately detect attack behavior across the environment.
Telemetry collection: This starts with collecting rich telemetry from your cloud workloads and traditional endpoints to ensure that you have the right data to analyze, identify, and investigate cyber threats. Uptycs’ osquery-based agent captures telemetry across Linux, Windows, macOS, and container workloads. Data is normalized at collection so it can be easily analyzed and correlated while in flight, and available for real-time and historical queries by security teams.
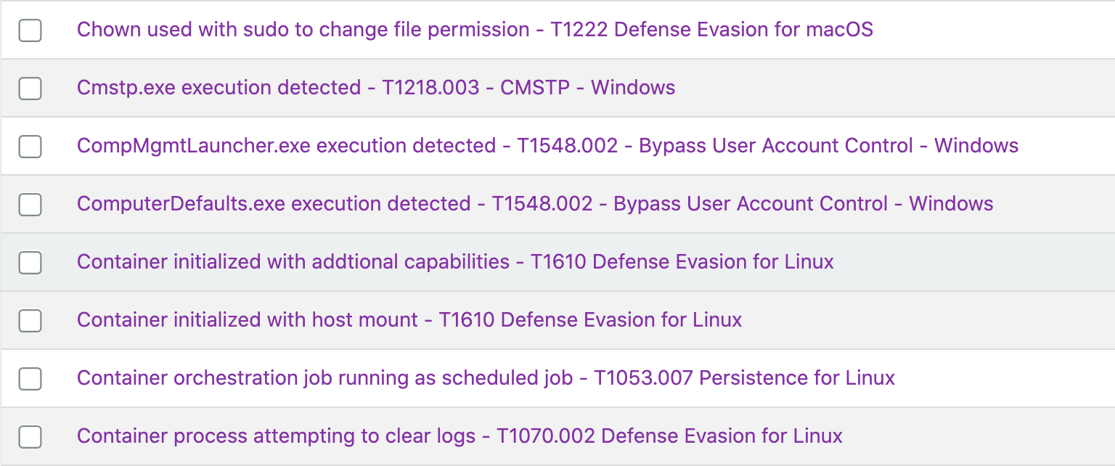
Behavioral detections: Behavioral detections use complex event rules to detect attacker behavior. Uptycs’ behavioral detections run against real-time streaming data as well as data stored for up to 90 days in a historical flight recorder. Uptycs has mapped over 1,000 MITRE ATT&CK techniques for endpoints and cloud infrastructure out of the box for you, allowing you to move quicker to identify and respond to an attacker that is in your system or trying to get into your system. These detections identify living-off-the-land techniques used by advanced adversaries.
Uptycs covers MITRE ATT&CK tactics and techniques, such as these detections for defense evasion.
YARA Detections: YARA signature detections are powerful, expressive, and easy using YARA rules to detect the latest malware and threats. YARA is embraced by security teams across the globe, now a primary method for detecting malware using a unique approach identifying textual or binary patterns. Uptycs has many out-of-the box YARA rules provided and helps you build query packs using YARA rules that can be run in memory against new files and process events.
Shields Up Section 3: Responding to Intrusions
The third part of CISA guidance has to do with preparing your organization for a security incident. When an attacker is inside your environment, speed is of the essence. Uptycs knows the power of 24/7 defense, and Uptycs remediation and blocking capabilities fortify your organization to respond in real-time to attacks and block dangerous processes from proliferating. You can create automated responses for quarantining suspicious activities, pausing processes, deleting files, and ensuring that malicious threats are unable to proliferate across your assets unchecked.
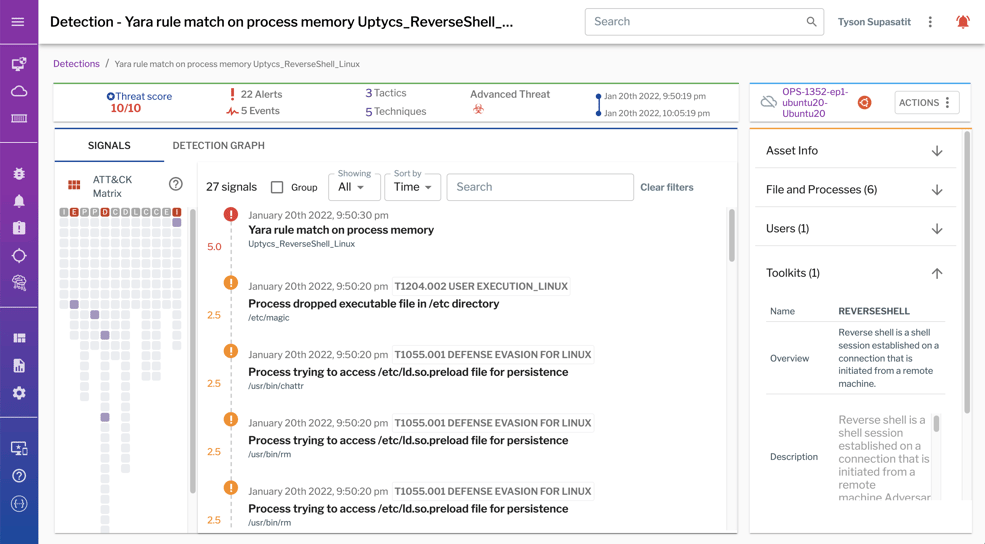
A first step of any intrusion response is to assess the scope of scale and risk to your organization. Defense-in-depth and proper tooling for your security team will amplify the ability to detect, respond, and resolve attacks. Uptycs’ rich telemetry gathers and correlates IOCs so that analysts can quickly analyze the depth of the issue. Because detections are mapped to the MITRE ATT&CK framework, analysts have additional context to understand the potential impact of the incident.
Analysts need context when triaging and investigating alerts. This screenshot illustrates how Uptycs correlates signals, maps them to the ATT&CK framework, and provides details about toolkits, files, processes, and more.
Optimal EDR tooling for your organization allows your security team to quickly drill down into specific endpoints and cloud workloads to understand attacker behavior and the extent of an intrusion. It’s not enough to just see the high-level view, security teams need actionable insights in real-time so that they know which systems to target for clean-up. Here at Uptycs, we find the needle in the haystack (forensic evidence) for you and also keep the haystack for up to 90 days for further investigation. Reconstruct past events with the Uptycs Flight Recorder to investigate how attackers entered and proliferated across your environment.
Shields Up Section 4: Resilience and Recovery
The final recommendation from Shields Up is focused on resilience to restore and recover critical assets in the wake of a cyber incident. CISA recommends resiliency through backups, ideally isolated from your network, in the event of a ransomware attack. Establish a cadence of regular backups and prioritize critical assets for protection and recovery. This includes rigorous testing beforehand for redundancy and failsafe of any critical controls. Ensure that any backups you do have can be made readily available and recovered at-will.
You can also improve resilience through purple-teaming, where sanctioned penetration testers simulate an advanced attack. Uptycs customers use our platform to test the efficacy of detection and response controls during purple team exercises. Through this process, you can improve your organization’s resilience by uncovering and fixing gaps in detection coverage or workflows.
Purple team exercises can test the efficacy of your detection and response capabilities. The dashboard above maps penetration testers’ activity against the MITRE ATT&CK framework.
Taking Action, Together
During this time of heightened risk, organizations should assess and take steps to improve their security posture. Security analytics solutions such as Uptycs can help by providing insight into software inventory and vulnerabilities, system and cloud resource configurations, and detection and investigation capabilities.
Security leaders should be prepared to share what steps they are taking to improve the organization’s security posture with executives and board members. You should be prepared to share what proactive measures (Hardening, per CISA’s guidance), reactive measures (Detection and Response), and protective measures (Response) your team has in place to mitigate the increase in risk during this time. Summary dashboards like the one from Uptycs shown below can lower the effort required when reporting to leadership.
If you are interested in learning more, please reach out to discuss anything outlined above.
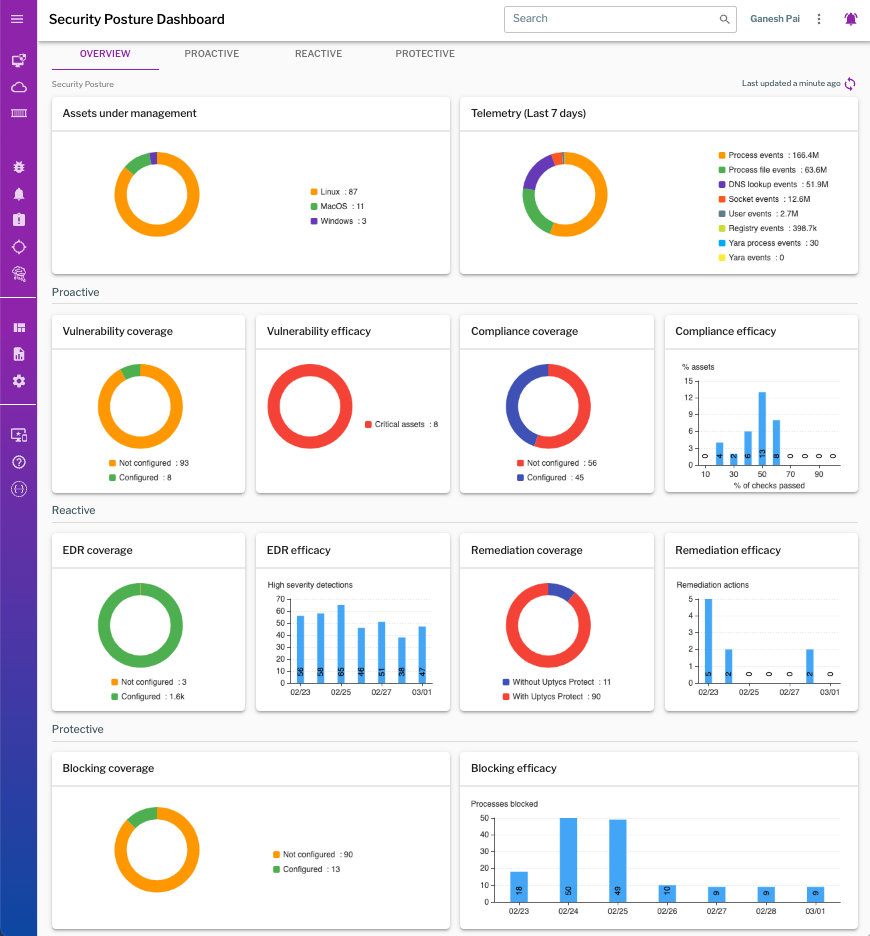 Dashboards can quickly convey high-level information. This Security Posture Dashboard contains information about proactive, reactive, and protective measures taken across the environment.
Dashboards can quickly convey high-level information. This Security Posture Dashboard contains information about proactive, reactive, and protective measures taken across the environment.




.png?width=992&height=540&name=85_MITRE%20ATT%26CK%20dashboard%20(1).png)




