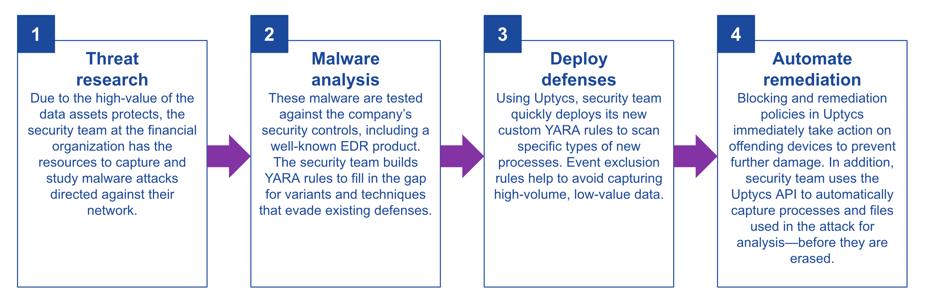
When the stakes are high, you need tools that will go the extra mile to protect your environment—beyond what’s available out-of-the-box from security vendors. That’s why a large financial services firm deployed Uptycs alongside their big-budget EDR vendor. This new Uptycs customer runs its own threat research operation to analyze malware targeting the company. They observed advanced attack techniques evading detection by their EDR solution and determined their risk profile demanded a more robust threat detection strategy.
Specifically, the security engineering team at the financial services firm wanted to write and deploy YARA rules based on their own research to catch malware behavior that their EDR missed. Since its creation by Victor Alvarez (@plusvic) in 2013, YARA has become the industry-standard format for matching text and binary patterns in malware families. As its GitHub description aptly states, YARA is a “pattern-matching swiss army knife.”
With their own custom YARA rules, the security team at the financial services organization felt that they could fill the gap in their detection capabilities much faster than waiting on their EDR vendor to do so. Since their EDR vendor did not support YARA, the team needed a way to deploy their new YARA detection rules out to their fleet of primarily Windows endpoints, numbering more than 10,000 devices.
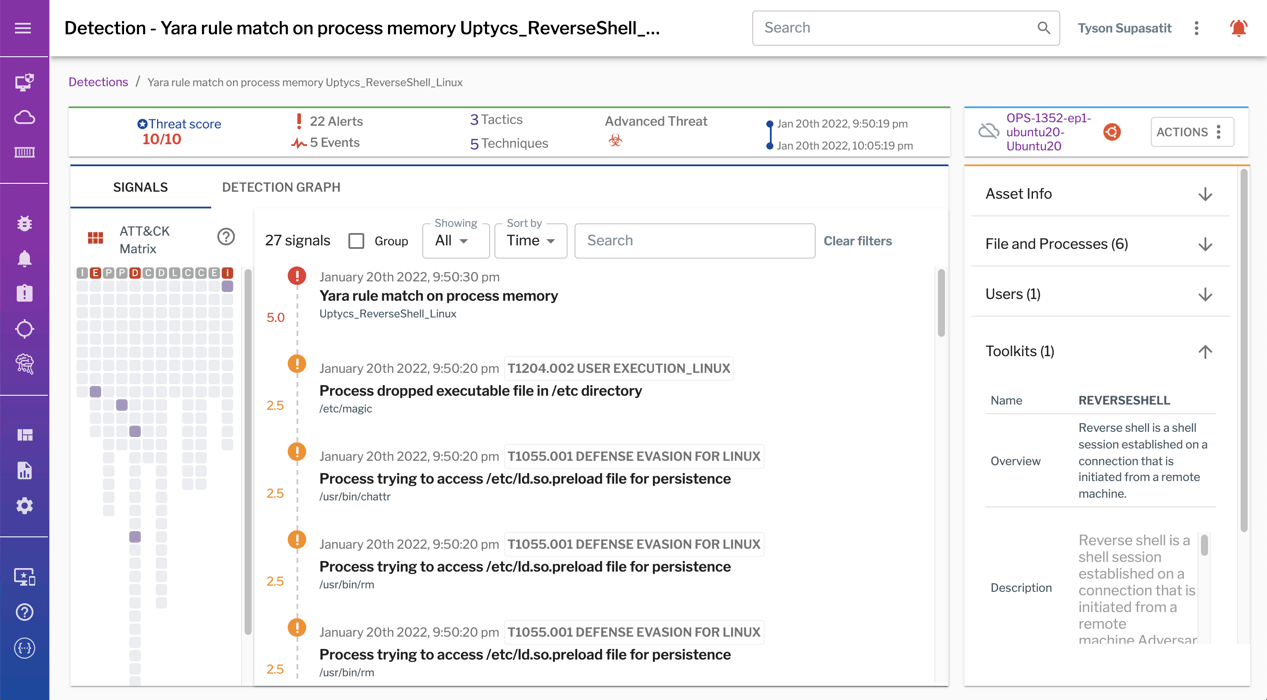
Enter Uptycs: The security team at the financial services firm loved that Uptycs was able to intelligently run YARA memory scans against specific types of files and new processes, and that deploying new rules to the fleet was safe and easy. This approach will be effective against fileless malware that often evades traditional antivirus. In addition, the Uptycs threat research team has compiled more than 200 YARA-based detections (and counting) profiling various APT toolkits, providing a strong baseline from which the security team can build its own custom definitions. The team also appreciated the level of customization available in Uptycs event-based rules that leverage streaming analytics of incoming telemetry to correlate signals in real time.
Going even further, the team purchased the Uptycs Protect add-on that enables remediation actions and blocking, including the ability to run custom scripts on machines to capture evidence of offending processes and files for forensic analysis before the malware erases them.
This powerful set of tooling, with Uptycs deployed alongside the XDR product, provides the financial services firm greater confidence that it is mitigating the risks it observed in its threat research. Certainly, not every organization is going to be as well-resourced to do their own threat research, but for those teams that are looking for a sophisticated and automated approach to YARA scanning at scale, Uptycs provides a robust solution. And for those organizations running lean security operations, the growing corpus of YARA-based detections already in Uptycs provides advanced malware protection out-of-the-box.
Read more about Uptycs XDR capabilities:
- Solution Brief: Uptycs XDR Overview, Detection and Response
- Webinar: Threat Detection and Malware Hunting with Uptycs
- Video: Lightning fast detection with Uptycs and MITRE ATT&CK
Uptycs includes more than 200 YARA-based detections, providing analysts with greater context into the types of toolkits that attackers are using against them






.png?width=352&name=YARA%20Webinar%20(2).png)
