Over the past year, Uptycs has been focused on adding new capabilities to our security analytics platform that meet cloud-native application protection platform (CNAPP) use cases. The time and effort it took us to add these features is arguably less than what other vendors spend acquiring technology and adding it into their portfolios. For more on that, read below in this post where we talk about the advantage of telemetry-powered security analytics.
Uptycs is on a mission to equip organizations with security observability. We’ve extended the concept started with osquery—structured telemetry across platforms—to new attack surfaces with our cloudquery and kubequery projects. The goal is to equip Security teams and their DevOps partners with the ability to ask questions and get answers quickly about their entire IT estate—including their cloud-native applications.
At RSA Conference 2022, we showcased Uptycs solutions that comprise what Gartner has termed CNAPP, including:
Cloud Workload Protection Platform (CWPP)
The Uptycs solution for cloud workload protection includes scanning container images for vulnerabilities and malicious components in the CI/CD pipeline (during the build and deploy stages) and—critically—also at the runtime stage. Uptycs uses the eBPF for deep introspection into what every container and program running on a Linux server is doing without ever leaving the kernel.
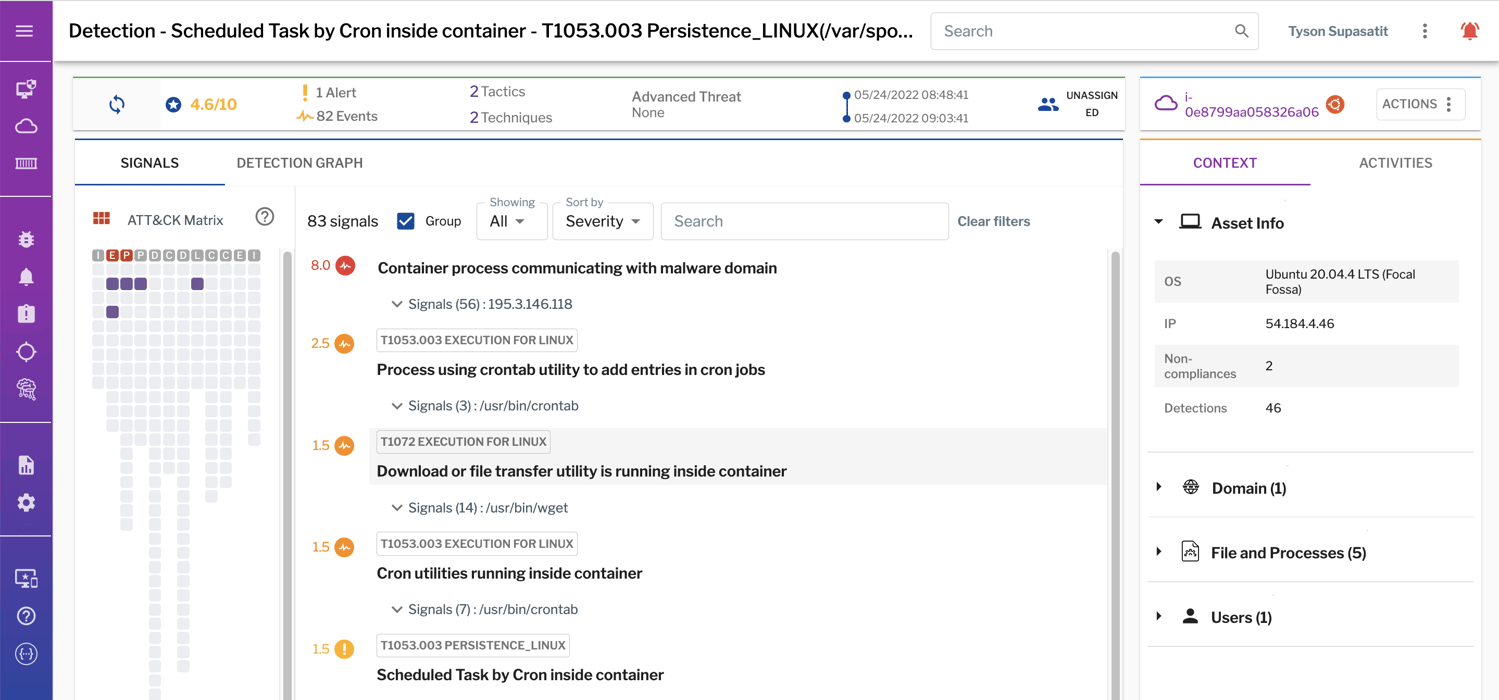 Uptycs secures containers at the build, deploy, and runtime stages of the CI/CD pipeline.
Uptycs secures containers at the build, deploy, and runtime stages of the CI/CD pipeline.
Kubernetes Security Posture Management (KSPM)
The orchestration layer expands the attack surface that Security teams must protect, and Uptycs now offers Kubernetes policy auditing and enforcement through integration with the Gatekeeper policy controller. Uptycs goes further to provide Security and DevOps teams with an overall inventory of all their K8s clusters across private and public clouds, as well as the vulnerability, threat, and compliance posture for each cluster.
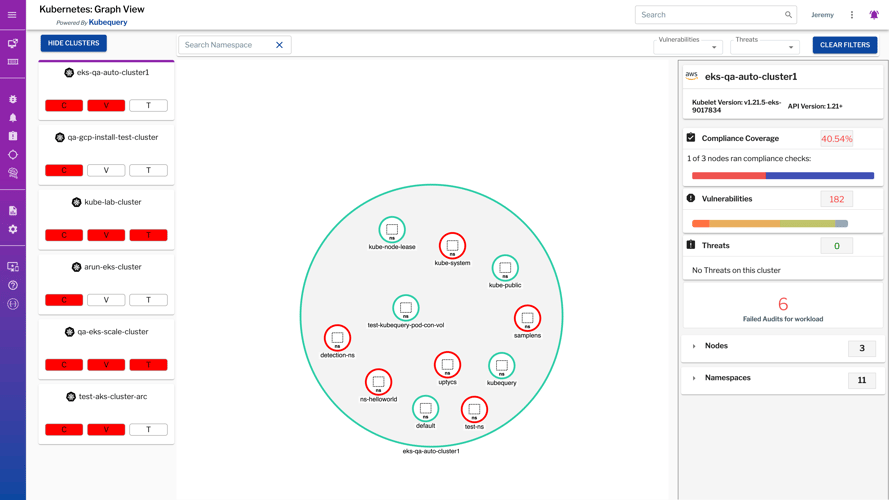
Uptycs enables Security teams to audit and enforce Kubernetes security policies.
Cloud Security Posture Management (CSPM)
Through 2025, 99% of cloud breaches will be the customer’s fault, not that of the cloud service provider, according to Gartner. Uptycs ingests and analyzes telemetry from AWS, Azure, and GCP to identify misconfigurations and detect threats. This offering equips Security teams and their IT partners to measure and reduce their cloud risk.
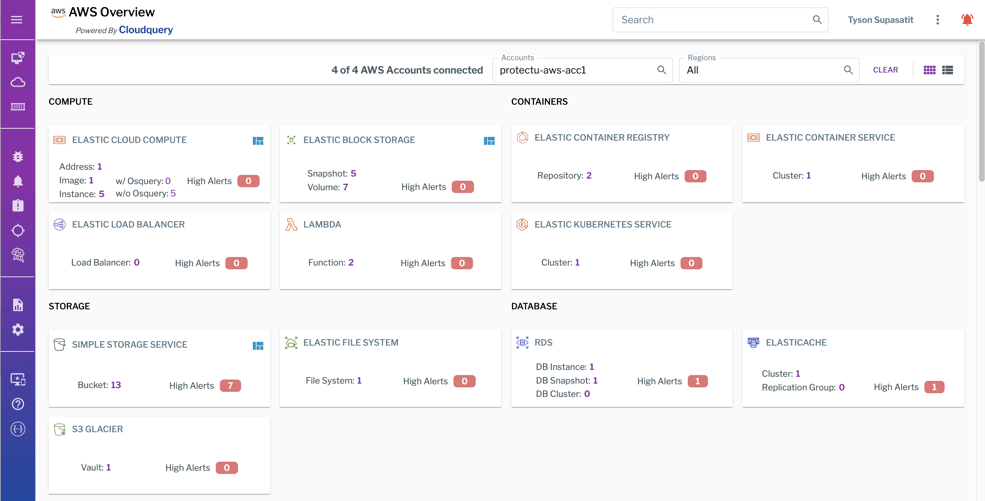
Uptycs provides cloud asset insight and inventory across public cloud providers.
Cloud Infrastructure Entitlement Management (CIEM)
It’s no secret that identity and entitlements are more important than ever, both in the prevention and detection of cloud-based attacks. Uptycs’ solution for CIEM measures the risk of organizations’ cloud IAM policies and enables teams to visualize access paths, prioritize remediation of risky policies, trim unnecessary privileges, and investigate access.
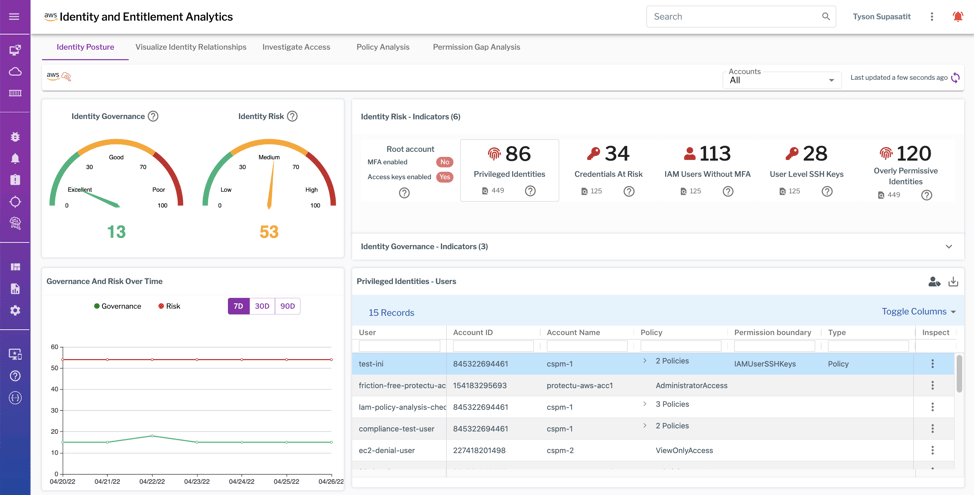
Uptycs measures risk based on analysis of cloud identity and access policies.
Cloud Security Is Maturing Beyond Niche Tools
Public cloud adoption continues to grow at a healthy pace—just look at cloud provider revenues for evidence. It’s not surprising to see the market for cloud security tools mature as well chasing demand for more holistic offerings. By 2025, Gartner predicts that 70% of organizations will consolidate the number of vendors securing the life cycle of cloud-native applications to a maximum of three vendors.
As they enter a new phase of cloud security maturity, organizations need to think architecturally about their cloud security tooling. Rather than purchase products piecemeal, Gartner recommends that organizations take a look at platforms that consolidate various CNAPP capabilities: “Evaluate security platforms where they share data and control planes; leverage this consolidation to define common policies and reduce gaps and vulnerabilities between legacy silos.”
As the Gartner report notes, operational efficiency is an important driver for tool consolidation. When cloud security talent is scarce, you want to make sure your skilled workers don’t need to learn and operate too many niche tools. Of note: this dynamic was—and is—also a major reason why organizations choose third-party tooling over the disparate services provided by the cloud service providers. It makes sense to have a single place where you can audit cloud assets and detect and investigate threats.
Telemetry-Powered Security Observability
This is where Uptycs’ telemetry-powered approach sets our solution apart. Rather than cobble together different products with a dashboard to display their respective alerts, Uptycs features a common data schema (SQL tables) and cloud data lake for all the telemetry required for security observability that includes but goes beyond cloud-native application protection.
By normalizing telemetry at the point of collection in SQL tables, Uptycs is able to analyze and correlate data in real time as it streams into the cloud. This also eliminates a lot of the “extract-transform-load” burden associated with correlating diverse data sources, and allows for fast query times across petabytes of data.
This also helps with operationalization because your teams only need to use one query language (SQL) for different domains (CWPP, CSPM, etc). If they need to see what network addresses are associated with a particular process, they can answer that question using SQL. The same is true for queries for cloud resources: If you need to see what cloud VMs across providers are publicly accessible from the internet, that’s also a SQL query.
Yes, Developer Laptops Are Essential to CNAPP
Even organizations born in the cloud still have on-premises assets - (mostly MacBook Pro laptops used by developers working from home). The security of developer machines is a top concern for many Uptycs customers whose business revolves around applications run in the cloud, such as Flexport.
Observing developer laptops adds another layer of detection when it comes to spotting supply chain attacks, because attackers can taint code early on if they’ve compromised the developer’s machine. With Uptycs, you can not only accomplish traditional EDR goals but also check to see if there are malicious Chrome extensions installed on your laptop fleet designed to steal sensitive data.
During investigations, it’s extremely helpful to be able to add context, as Taylor Merry, Director of Security Operations at Flexport, describes below:
“With Uptycs, we can gather security telemetry from attack surfaces across our entire ecosystem and have it normalized and accessible through SQL tables,” says Merry. “This enables our analysts and application owners to quickly answer questions that span different domains without having to find the right person to ask or collecting more entitlements to find those answers themselves. Access to this data in one place unlocks context that enables better alerting and incident response. For example, if a security group on an EC2 instance is listening on port 22 for 0.0.0.0., that’s not a concern if it’s not exposed to the Internet. But with visibility inside the host, we can also check to see if the SSH is also running on the endpoint. That ability to quickly get context is key.”
|
Download the case study to learn how Flexport, a global leader in logistics, leveraged Uptycs to improve their cloud security posture, deliver security observability for multiple teams, and provide risk assurance for clients. |







