The Uptycs quarterly threat intel bulletin provides insights into the current cybersecurity threat landscape. This intel comes from our threat intelligence systems, sources, and a world-class cyber threat research team. Building and proactively monitoring the latest hybrid cloud security TTPs (Tactics, Techniques, and Procedures) continues to be their priority.
We've designed this bulletin to help organizations develop and evaluate their detection and protection posture. The goal is to strengthen your posture against the latest Linux and container-based threats.
Index
Insights: In-depth threat analysis and cybersecurity trends
Techniques used in malware samples
Commonly abused commands and utilities
Linux utilities abused by malware
Top prevalent malware families in the wild
Key vulnerabilities and exploits
Insights: In-depth threat analysis and cybersecurity trends
Critical alerts & emerging threats
CVE-2024-27198 and CVE-2024-27199 - Remote code execution vulnerabilities in JetBrains TeamCity
JetBrains revealed two severe security flaws within its TeamCity On-Premises platform, identified as CVE-2024-27198 and CVE-2024-27199. These vulnerabilities compromise the platform's security by allowing unauthorized users to bypass authentication mechanisms and gain administrative access.
The critical nature of CVE-2024-27198 lies in its ability to enable remote code execution. This is done via an authentication bypass in the web component, classified with a CVSS score of 9.8. It does this by manipulating HTTP requests to trigger a 404 error and exploiting specific URL patterns.
CVE-2024-27199, on the other hand, presents a directory traversal issue with a CVSS score of 7.3. This permits malicious actors to leak information and alter TeamCity settings by exploiting vulnerable paths in the server.
Rapid7's analysis demonstrates the active exploitation of these vulnerabilities. Additionally, numerous proofs of concept have circulated on platforms like GitHub and social media. Attackers have leveraged these flaws to deploy malicious software to execute domain discovery and persistence operations. That public proofs of concept and observed active exploitations exist shows how urgently organizations need to apply updates and secure their systems.
Ransomware attacks include:
- Jasmin ransomware
- XMRig cryptocurrency miner
- Cobalt Strike beacons
- SparkRAT backdoor
The exploitation processes include downloading and executing malicious payloads through sophisticated command sequences. Known malware and custom scripts for ransomware encryption, cryptocurrency mining, backdoor access, and system reconnaissance have both been leveraged. Notably, the Jasmin ransomware renames files with a ".lsoc" extension and leaves a ransom note. The XMRig miner meanwhile deploys through multiple stages, using native tools to evade detection and mine cryptocurrency.
The SparkRAT backdoor and other payloads aim to establish long-term access. This allows malicious actors to control affected systems remotely and perform further malicious activities. The observed use of Cobalt Strike beacons indicates an intention to maintain stealthy and persistent access to compromised networks.
Recently, the BianLian extortion group has been observed leveraging security flaws in the TeamCity continuous integration server to gain initial entry into networks. In their latest series of attacks, they also introduced a new, previously undetected backdoor crafted in PowerShell. This new malicious tool appears to be a rewritten version of their older backdoor, originally developed in Golang.
This widespread exploitation of TeamCity vulnerabilities represents a significant threat to data security and system integrity. Potential financial and operational impacts for affected organizations exist as well. The United States Cybersecurity and Infrastructure Security Agency (CISA) has included CVE-2024-27198 in its Known Exploited Vulnerabilities (KEV) catalog. This clearly underscores the severity of CVE-2024-27198.
Techniques used in malware samples
Utilizing Uptycs EDR, equipped with YARA process scanning, we have identified the most prevalent malware families across Linux and Docker-based targeting platforms.
The top techniques/tactics triggered by malware samples, aligned with the MITRE ATT&CK framework, are Hide Artifacts (T1564), Unix Shell (T1059.004), Cron (T1053.003), Remote Services (T1021), and Malicious Files (T1204.002).
Figure 1 shows how prevalent these observed ATT&CK technique IDs.
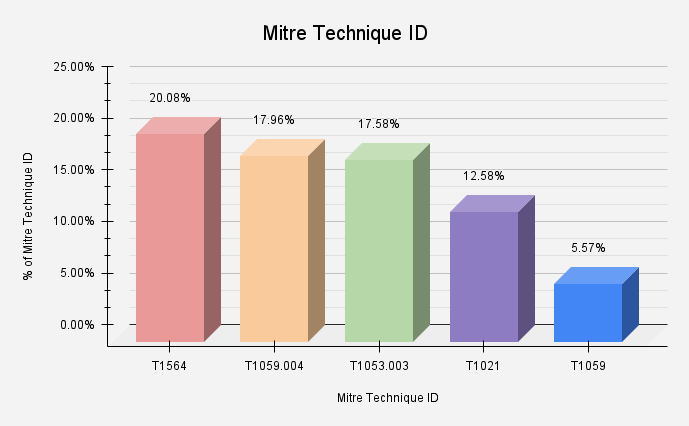
Figure 1 – Observed ATT&CK technique IDs
Commonly abused commands and utilities
"Living off the Land" is a detection evasion technique. Malicious samples often utilize built-in target operating systems utilities in their attack sequences. Across Linux and Docker based platforms, these utilities correspond to our replication systems' tactics.
Linux utilities abused by malware
This quarter, we focused more on Linux Utilities also known as GTFOBins. Chattr, frequently observed in Mirai malware attacks, is the most abused Linux utility.
Figure 2 displays the five Linux utilities most often misused by malware and their prevalence.
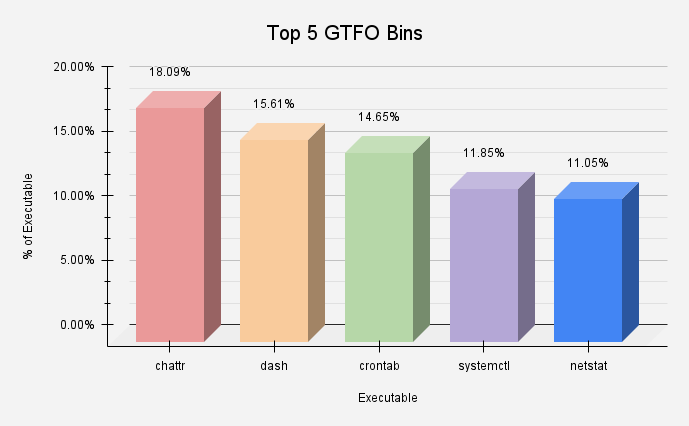
Figure 2 – Top five Linux utilities abused by malware
- Chattr (Tactics: Defense Evasion and Persistence): Used for file attributes/permissions modification. In the recent campaign targeting misconfigured Docker, YARN services, the Chattr utility has been used for file modification for its persistence of an attack.
- Dash (Tactics: Execution): Dash stands for Debian Almquist Shell. It replaces the /bin/sh in default scripts and provides better execution speed while consuming fewer resources. Generally, the miner malware will often use this utility for their campaign activity.
- Crontab (Tactics: Persistence): Crontab is abused for scheduling tasks. NoaBot malware has been installed in the form of a persistence method after rebooting the system by Crontab utility.
- Systemctl (Tactic: Defense Evasion): Systemctl is used to stop EDR services. GobRAT and botnet malware generally abuse this utility for Defense Evasion method.
- Netstat (Tactics: Discovery): Netstat is often used to discover system network connections. XMRig miner malware has used this utility to check the required connection port to establish a network.
"XZ Utility" library compromised to deliver backdoor malware
At the end of March 2024, cybersecurity experts disclosed a new vulnerability in a Linux utility called XZ Utils (CVE-2024-3094). The existence of this backdoor vulnerability has sent ripples across the tech world. XZ Utils is widely used for lossless data compression in Linux and macOS systems.
Summary
In the first stage, the user named "JiaT75 (Jia Tan)" in 2021 created a GitHub account.
In 2022, Jia Tan submitted a patch via a mailing list. Later in 2023, it started pushing updates of vulnerable XZ utility versions 5.6.0 and 5.6.1 on a Debian-Linux system. This was done to mask its malicious changes.
In 2024, the project URL was modified. This modified URL, included in the XZ subdomain, executed the backdoor named "XZ Backdoor." This was done by exploiting the vulnerability [CVE-2024-3094] in a supply chain attack.
Top prevalent malware families in the wild
Utilizing Uptycs EDR, equipped with YARA process scanning, we identified the most prevalent malware families across Linux and Docker-based targeting platforms.
Our team of cyber threat researchers has improved our platform by adding extensive tactics, techniques, and procedures (TTPs). We have also added YARA rules to detect these malicious activities. Uptycs users can now view in-depth profiles of the malware upon detection.
Here are the top malware identified across Linux and Docker-based targeting platforms:
Linux malware
Mirai
Mirai is a type of botnet malware that exploits vulnerabilities in IoT (Internet of Things) devices to infect them with malicious code. Mirai, which had its source code leaked in 2016, has been the progenitor of a number of botnets.
Recently NoiBat, a new Mirai-based malware, has also emerged. With the capabilities of a wormable self-spreader and an SSH key backdoor, it downloads and executes additional binaries. Spreading itself to new victims in this way is another key attribute.
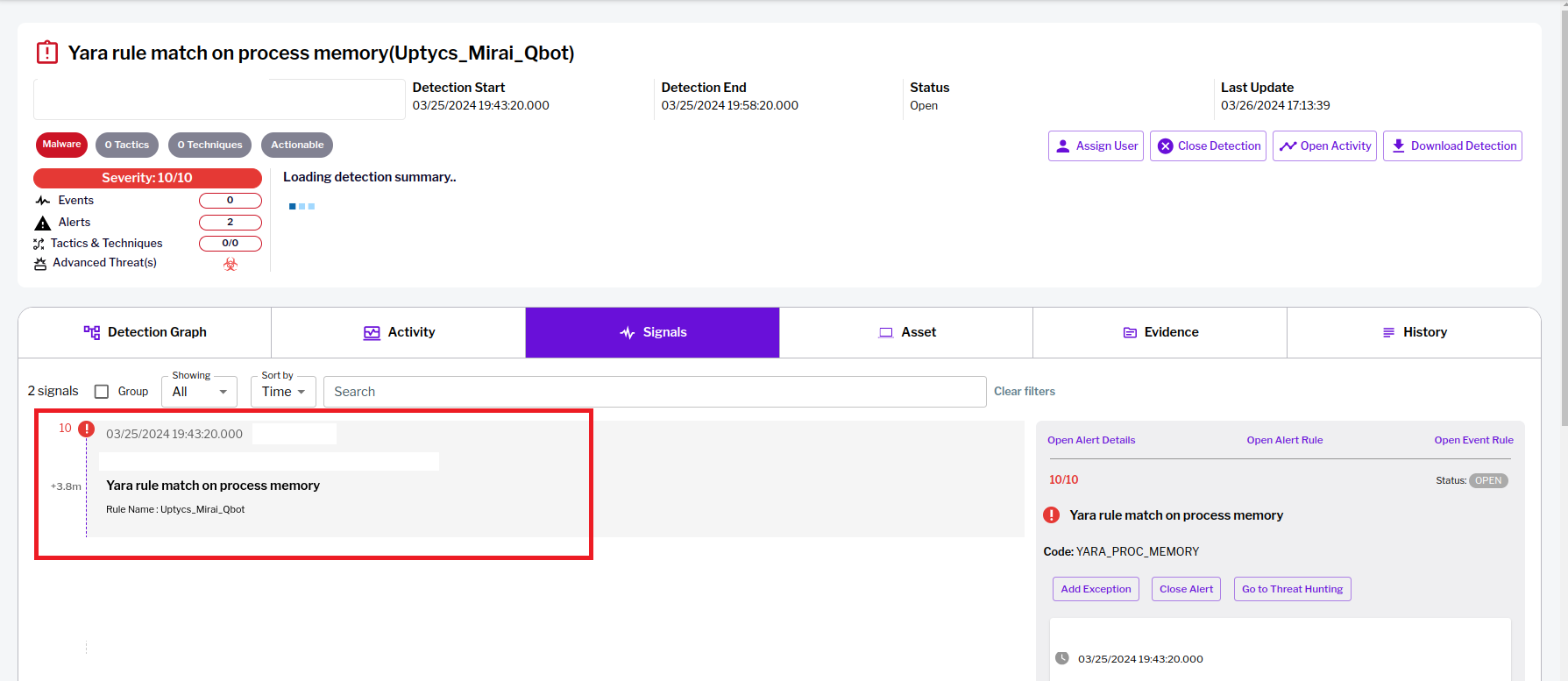
Figure 3 – Uptycs XDR detection of Mirai malware
Gafgyt
Gafgyt malware, also known as Bashlite, has been targeting millions of vulnerable IoT devices like Mirai botnet. In recent variants, targeting commands have changed significantly, performing many kinds of DoS attacks:
- HTTP DoS attacks
- TCP DoS attacks
- UDP DoS attacks
- Various other types
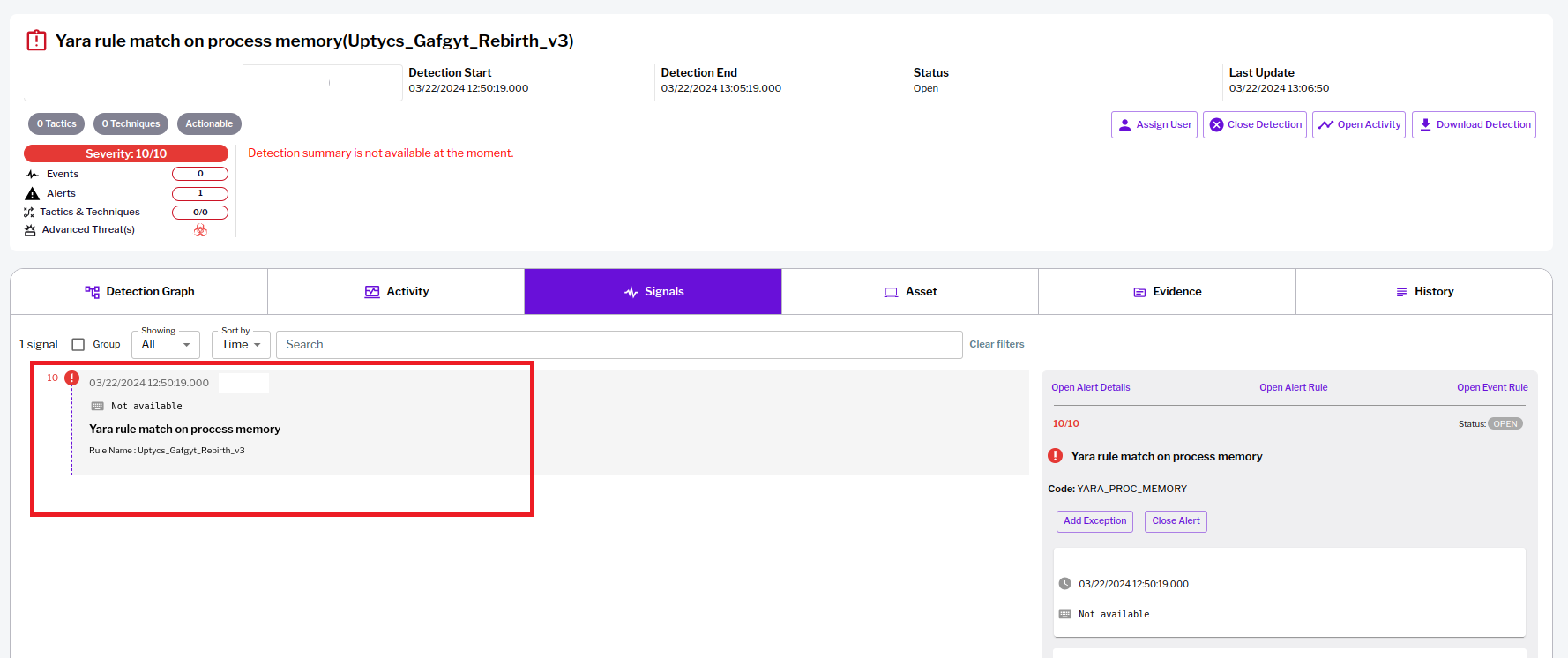
Figure 4 – Uptycs XDR detection of Gafgyt malware
Trending Linux ransomware
Linux systems run many of the most critical operations behind organization servers. Consequently, ransomware operators have intensified their focus on targeting Linux systems.
In this quarterly threat landscape report, we have included several new and emerging ransomware trends.
ALPHA SPIDER is the adversary behind the development and operation of the ALPHV ransomware as a service (RaaS). In the latest version, researchers observed the usage of NTFS Alternate Data Streams to hide a reverse SSH tool. Likewise, multiple vulnerabilities associated with a GNU/Linux-based appliance for initial access and privilege escalation were exploited. Also, bypassing DNS-based filtering and multifactor authentication (MFA) by tampering with network configuration files was in evidence.
"Abyss Locker" ransomware, which previously was discovered targeting Windows systems in early January 2024, has now also started targeting Linux systems. The Abyss Locker threat actor steals victims' sensitive data before deploying and running its ransomware malware for file encryption.
The ALPHV Blackcat update has the capability to encrypt both Windows and Linux devices, and VMWare instances. ALPHV Blackcat affiliates have extensive experience with ransomware and data extortion operations.
Q1 threat research articles
Ukraine targeted by UAC-0050 using Remcos RAT pipe method for evasion
Uptycs researchers discovered a resurgence of the UAC-0050 threat group campaign activity targeting Linux and Windows systems. In their latest operational technique, the UAC-0050 group has integrated a pipe method for interprocess communication, showcasing their advanced adaptability.
The group’s weapon of choice is RemcosRAT, a notorious malware for remote surveillance and control, which has been at the forefront of its espionage arsenal.
Read more about UAC-0050 Using Remcos RAT
Cybersecurity advisory: Apache Struts vulnerability CVE-2023-50164
Uptycs researchers identified a vulnerability, CVE-2023-50164, in Apache Struts that poses a significant threat to a wide range of industries. This newly reported vulnerability enables remote code execution, and its exploitation is already evident in the wild.
In the report, researchers reveal the details about the vulnerability and the nature of CVE-2023-50164, its potential impact, and the immediate actions required to mitigate this critical threat.
Read more about Apache Struts vulnerability
Preventing BuildKit & runC Leaky Vessels container escape vulnerability
The Uptycs research team shared an awareness report on the emergence of four new container vulnerabilities collectively dubbed Leaky Vessels by Snyk researchers. These vulnerabilities exploit the runC and BuiltKit components of Docker container environments. In the blog, researchers said that Uptycs' enhanced detection and response capabilities allow users to catch privilege escapes and use remediation actions to kill any container process that is running with these vulnerabilities.
Details about Leaky Vessels vulnerability
CVE-2024-23897: Possible Jenkins exploit, CI/CD pipeline vulnerability
The Uptycs Threat Research Team thoroughly investigated CVE-2024-23897, a significant vulnerability discovered in Jenkins, the open-source automation server integral to CI/CD pipelines worldwide. The vulnerability has been identified in Jenkins' built-in command line interface (CLI) and its interaction with the args4j library.
The team analysis sheds light on the technical details and potential impacts of this vulnerability.
Analysis report on CVE-2024-23897
8220 Gang cryptomining campaign targets Linux & Windows platforms
The Uptycs Threat Research Team spotted the resurgence of 8220 Gang, a notorious Chinese-based threat actor group. They have moved into the spotlight again with a renewed assault on cloud-based infrastructure. Unfolding from May 2023 through February 2024, this latest campaign showcases the gang's strategic pivot towards more sophisticated tactics and techniques, targeting both Linux and Windows platforms.
Through a meticulously orchestrated operation, the group has been exploiting well-known vulnerabilities, including CVE-2021-44228 and CVE-2022-26134. This underscores a persistent threat to cloud environments worldwide.
8220 Gang group latest campaign
Social marketing news
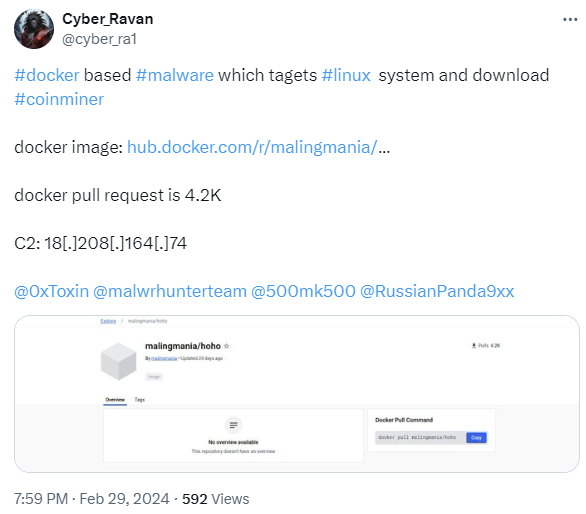
Docker-based malware targets Linux system
The Uptycs Threat Research Team identified a new Docker-based malware while performing threat hunting activity. This malware was targeting Linux systems connected to its Command-and-control [C2] server and downloaded Coinminer malware.
Figure 5 – Please click the image to see the original post.
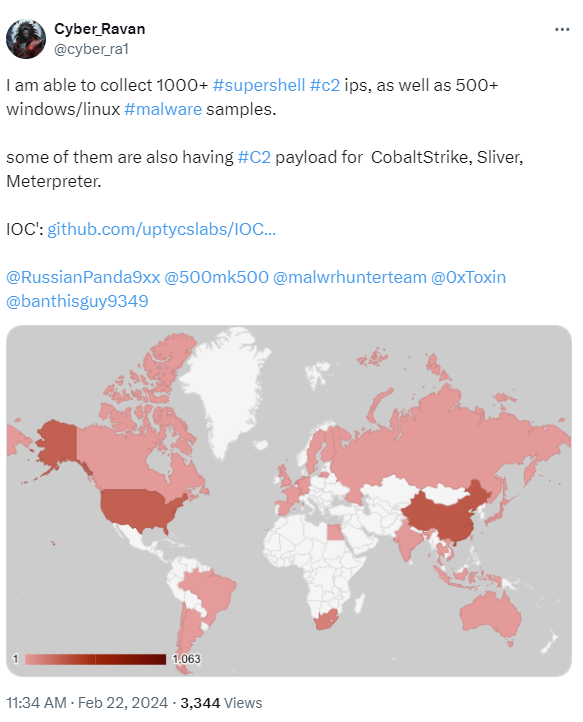
High increase surge in SuperShell C2 IPs
From January 2024, Uptycs researchers tracked more than 1k active SuperShell C2 IPs. These targeted both Windows and Linux systems.
Supershell is a C2 remote control platform. Successful payload execution allows attackers to establish a reverse SSH tunnel. This is a fully interactive shell to execute arbitrary code within the context of the application.
On Linux systems, malware like Mirai, Gafgyt, SSH based Reverse Shell, and GoRAT deliver SuperShell C2 payloads.
See more information on SuperShell IOCs here.
Figure 6 – Please click the image to see the original post.
Q1 focus on top threat actors
APT-C-36, also known as Blind Eagle, is a financially motivated threat actor. APT-C-36 has a history of orchestrating cyber attacks against entities in Colombia and Ecuador. These have delivered an assortment of Remote Access Trojan [RATs]:
- AsyncRAT
- BitRAT
- Lime RAT
- NjRAT
- Remcos RAT
- Quasar RAT
In its latest campaign, this threat actor delivered RATs malware with loader malware called Ande Loader. APT-C-36 now focuses on targeting Spanish-speaking users in the manufacturing industry in North America.
Lazarus is a North Korean-based APT group mainly targeting South Korean companies, institutions, think tanks, and others. Recently, Lazarus exploited a Microsoft vulnerability associated with Windows Kernel Privilege Escalation to establish a kernel-level read/write primitive. Lazarus group also uses a DLL side-loading attack technique. Using legitimate web applications in the initial access stage, they have achieved the next stage of their attack process.
The cyber threat actor NoName057 has been observed changing tactics amid the escalating conflict in Ukraine. The group has gained notoriety for their involvement in Project DDoSia, an initiative aimed at executing large-scale distributed denial-of-service (DDoS) attacks against entities supporting Ukraine. That have predominantly been NATO member states.
A Chinese-based threat actor group named 8220 Gang, has surfaced with a renewed assault on cloud-based infrastructure. Their most recent campaign showcases their strategic pivot towards more sophisticated tactics and techniques targeting both Linux and Windows platforms.
Additionally, the utilization of Windows PowerShell for fileless execution is noted, leading to the deployment of a cryptominer.
Turla has targeted entities in the USA, European Union, Ukraine, and Asia with a huge set of offensive tools. Threat actors have previously used malware families such as CAPIBAR and KAZUAR to target Ukrainian defense forces.
After Crutch and TinyTurla, Turla has expanded its arsenal to include the TinyTurla-NG and TurlaPower-NG malware families. It has also widened its net of targets to Non-Governmental Organizations (NGO). This activity signals Turla’s intention to expand their suite of malware. Please also note, these targets do not align with Russia’s strategic and political goals.
Key vulnerabilities and exploits
The key vulnerabilities/exploits seen across Linux and container-based platforms are as follows.
- CVE-2024-3094 - Supply Chain Compromise Affecting XZ Utils Data Compression Library
- CVE-2024-23897 - Remote Code Execution in Jenkins CLI
- CVE-2024-21626, CVE-2024-23651, CVE-2024-23652, CVE-2024-23653 - runC and BuildKit Container Escape Vulnerabilities (also referred to as Leaky Vessels)
- CVE-2024-27198, CVE-2024-27199 - Remote Code Execution in JetBrains TeamCity
- CVE-2024-23334 - Directory Traversal Vulnerability in Aiohttp Python Package
- CVE-2024-1597 - SQL Injection org.postgresql:postgresql Dependency in Bamboo Data Center and Server
- CVE-2023-51467 - Apache OfBiz Authentication Bypass Vulnerability
Recommendations
Incident response teams should investigate the parent processes responsible for triggering key utility execution rigorously across different operating systems:
- Linux: Monitor the use of chattr, dash, crontab, systemctl, and netstat utilities
- XZ utility has been exploited in versions 5.6.0 and 5.6.1. It has also been used to deploy backdoors. We recommend checking to ensure you have stopped using these two versions.
To enhance security against malware attacks, organizations should follow these cyber hygiene best practices:
- Update software: Regularly update all software to patch vulnerabilities.
- Implement robust password policies: Deploy and diligently enforce password policies.
- Use multi-Factor authentication: Add another layer of security with multi-factor authentication.
- Be cautious with suspicious links: Do not click links or open attachments from unknown or untrustworthy sources.
- Backup data: Prevent the potential loss of a cyber attack by backing up data.
Implementing these practices is likely to strengthen your organization’s defenses against a variety of cyber threats significantly.
Conclusion
As we wrap up the Uptycs Q1, 2024 Quarterly Threat Bulletin, it's clear cyber threat sophistication has continued to increase. This highlights a critical need for advanced cybersecurity strategies and tools. During Q1, 2024 we saw the emergence of new vulnerabilities and the continued evolution of dangerous of malware. It also demonstrates the innovation threat actors relentlessly employ with new tactics.
The analysis Uptycs provides in this bulletin underscores the vital role of sophisticated solutions in today’s cybersecurity landscape. To more effectively counter these threats, organizations must be familiar with the latest adversarial trends. Understanding and equipping themselves with the most advanced defenses is key.
At Uptycs, we remain unwavering in our commitment to empowerment via cutting-edge security insights and solutions. Our goal remains to thoroughly prepare our clients to be resilient in the face of today's multifaceted cyber threats.
Uptycs remains at the leading edge of threat intelligence by offering actionable insights and robust tools to help secure the digital frontier. We encourage our readers to stay informed and proactive, making cybersecurity an integral part of their operational ethos.
Uptycs thanks you for placing your trust in us. Together, we are building a more secure and resilient digital future.






-1.png?width=352&name=Untitled%20design%20(2)-1.png)
