The Apache Struts vulnerability CVE-2023-50164, with a critical CVSS score of 9.8, poses a significant threat to a wide range of industries. This newly reported vulnerability enables remote code execution, and its exploitation is already evident in the wild.
Apache Struts is an open-source web application framework for developing Java EE web applications. It leverages the Model View Controller (MVC) architecture, which is a widely used design pattern for separating an application's business logic from its user interface.
Considering its widespread usage and adoption in critical industries, any vulnerability in Apache Struts is looked upon with high priority by enterprises. In the past, attackers have exploited the struts' vulnerabilities to target large enterprise organizations as well. The Equifax breach in 2017 happened because of exploitation of Apache Struts CVE-2017-5638 vulnerability.
In this blog, we reveal the details about the vulnerability and the nature of CVE-2023-50164, its potential impacts, and the immediate actions required to mitigate this critical threat, offering insights and solutions to help secure your digital infrastructure against this alarming security lapse.
Anatomy of the vulnerability
CVE-2023-50164 is a path traversal vulnerability caused because of flaws in file upload logic. As per Apache's security advisory, "An attacker can manipulate file upload params to enable paths traversal and under some circumstances this can lead to uploading a malicious file which can be used to perform remote code execution."
The bug resides in the handling of HTTP request parameters within the ‘core/src/main/java/org/apache/struts2/dispatcher/HttpParameters.java’ file in the Struts source code. Originally, the code performed case-sensitive comparisons when processing parameter names in the ‘remove,’ ‘contains,’ and ‘get’ methods of the ‘HttpParameters’ class. The updated version has been altered to make these comparisons case-insensitive. This change implies that parameter overriding could occur through modifications in the capitalization of the first letter. For instance, the vulnerability distinguishes between ‘param1="value1"’ and ‘Param1="Value1"’ treating them as separate entities due to the original case-sensitive nature of HTTP parameters.
Detailed exploitation mechanism
Exploitation of this vulnerability is achieved by modifying the upload form name to begin with an uppercase letter and sending file uploads to the ‘upload.action’ endpoint. This process is illustrated in the figure below.
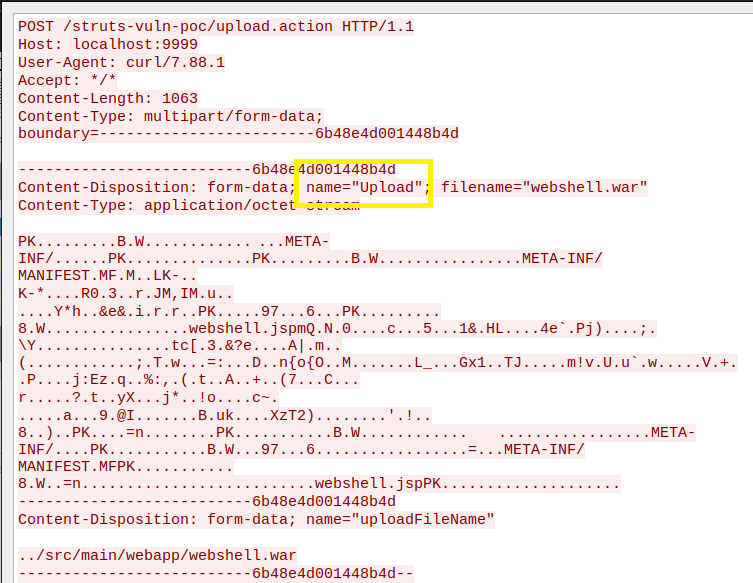 Figure 1 - HTTP request to trigger parameter overriding
Figure 1 - HTTP request to trigger parameter overriding
The exploit requires the attacker to know the URI path of the file upload page of the web application. The URI path and HTTP headers required will differ in every application.
Following are the three variables required for the exploit to work:
- URI Path. In the above case, it's "/struts-vuln-poc/upload.action"
- Upload variable name. In the above case, it’s "upload" (which is then capitalized for exploiting)
- Upload file variable name. In the above case, it's "uploadFileName"
Comparative analysis of CVE-2017-5638 and CVE-2023-50164
CVE-2017-5638 was a significant vulnerability found in the Jakarta Multipart parser plugin, which is utilized by Apache Struts for parsing multipart/form-data. This vulnerability was activated through a crafted OGNL (Object-Graph Navigation Language) expression within the content type header. In contrast, CVE-2023-50164, a more recent vulnerability, presents different exploitation dynamics. Unlike CVE-2017-5638, which consistently used a fixed URI path and HTTP headers regardless of the target, CVE-2023-50164 requires a tailored approach for each specific target. This means that exploiting CVE-2023-50164 necessitates preliminary reconnaissance to effectively understand the nuances of the target web application, particularly in identifying the correct file upload URL path.
Mitigations and actions
The vulnerability can be patched by upgrading to Struts versions 2.5.33, 6.3.0.2 or greater. Since there are no workarounds mentioned by Apache advisory, upgrading is the only recommended action.
Detection with Uptycs XDR
To inventory vulnerable versions of Apache Struts, Uptycs unified CNAPP and XDR platform offers robust vulnerability scanning features for timely detection.
Uptycs XDR solution stores vulnerability scan results in a dedicated table, accessible via SQL queries, as shown below:
select * from vulnerabilities where cve_list = 'CVE-2023-50164'
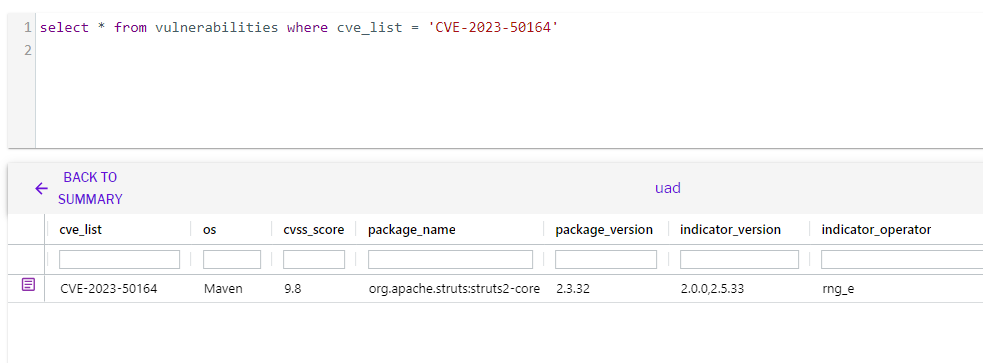 Figure 2 - Detection of CVE-2023-50164 using vulnerability scan
Figure 2 - Detection of CVE-2023-50164 using vulnerability scan
The vulnerability is exploited to upload webshell and perform remote code execution. Uptycs XDR detects these post exploitation activities and displays the commands executed in the detection graph.
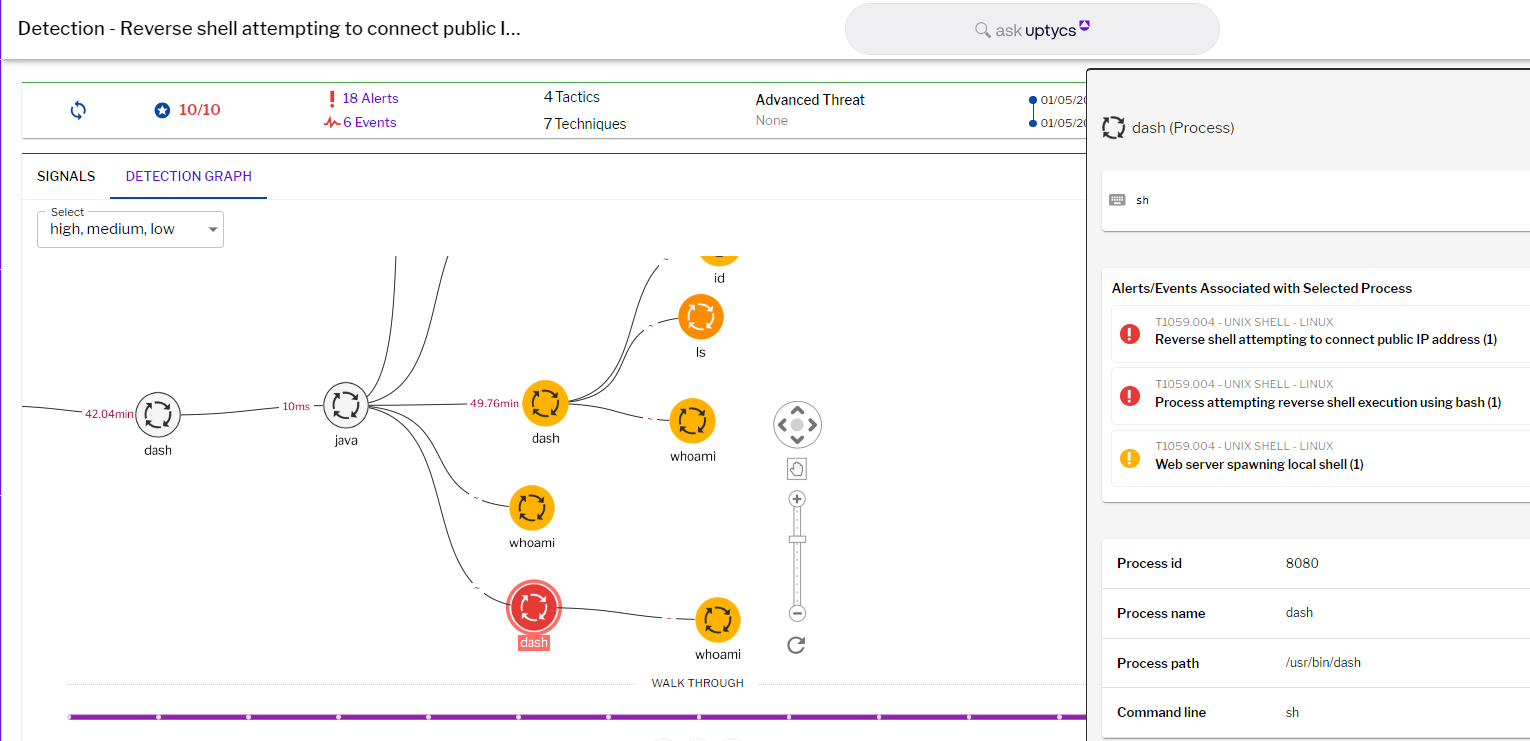
Figure 3 - Post exploitation commands detection
Identifying post-exploitation activities is just one part of the puzzle. Uptycs’ Threat Hunting capabilities also focus on spotting and analyzing anomalous activities, a crucial aspect of early threat detection and response.
Conclusion
Apache Struts is a widely used enterprise application that is used to host public facing web applications and services in an organization. Web-based remote code execution techniques are some of the most dangerous types of exploits because of their low complexity. They can also easily bypass firewall and intrusion detection systems. With the past history of Apache Struts vulnerabilities being used in attacks on many Fortune 500 companies, defending against CVE-2023-50164 attacks is very necessary.







