Threat actors have become cloud security experts, and it’s time to start thinking like one! This is something you’ll see and hear me say a lot. Why? Because as an industry, this fact should be alarming. I want to reinforce to our customers that their bar for hiring cloud security leaders and engineers should be no less than “expert level” if they want to keep up with the speed at which threat actors are honing their cloud skills. If you’re unable to hire the necessary skills, then you should find a security vendor you can partner with who does have the skills.
In a previous blog, I explained why Cloud Detection & Response (CDR) is needed for a mature cloud security posture. In this blog, I go a little deeper to highlight the categories of detections within the CDR product our customers use today.
Before we dive deeper into these categories, I want to emphasize the problem CDR solves for. Threat actors know the many different ways to attack your cloud environment. They want to achieve a desired outcome—escalate privileges; exfiltrate data; terminate or spin up resources; deploy ransomware, evade detection mechanisms, etc. They are experts at knowing the sequence of API calls required to achieve this desired outcome, which includes performing reconnaissance on the account as soon as they access it.
Uptycs is thinking like a threat actor on your behalf and is able to detect these sequences whenever they show up in your log data so that you don’t have to know how threat actors think or keep a constant watch on your logs. We’re mapping out all the possible ways threat actors are able to do so and then creating detections to alert our customers when these behaviors take place in their environment. We include a simplified explanation of what just happened as well as actionable steps to take to remediate the issue.
Now, on to a subset of all the categories we detect for in your environment …
Privilege Escalation
There are many ways to escalate privileges in a cloud environment. Privilege escalation is an attempt to gain higher-level permissions in your account. But how exactly does a threat actor do this? It’s complicated and not something that’s well-known, even among cloud security-minded teams. For example, when an AWS managed policy has several versions, and one of those versions has “AdministratorAccess,” a threat actor will identify what the policy is, how many versions it has, and which version is most permissive. Then, they will set that version as the one they want to use.
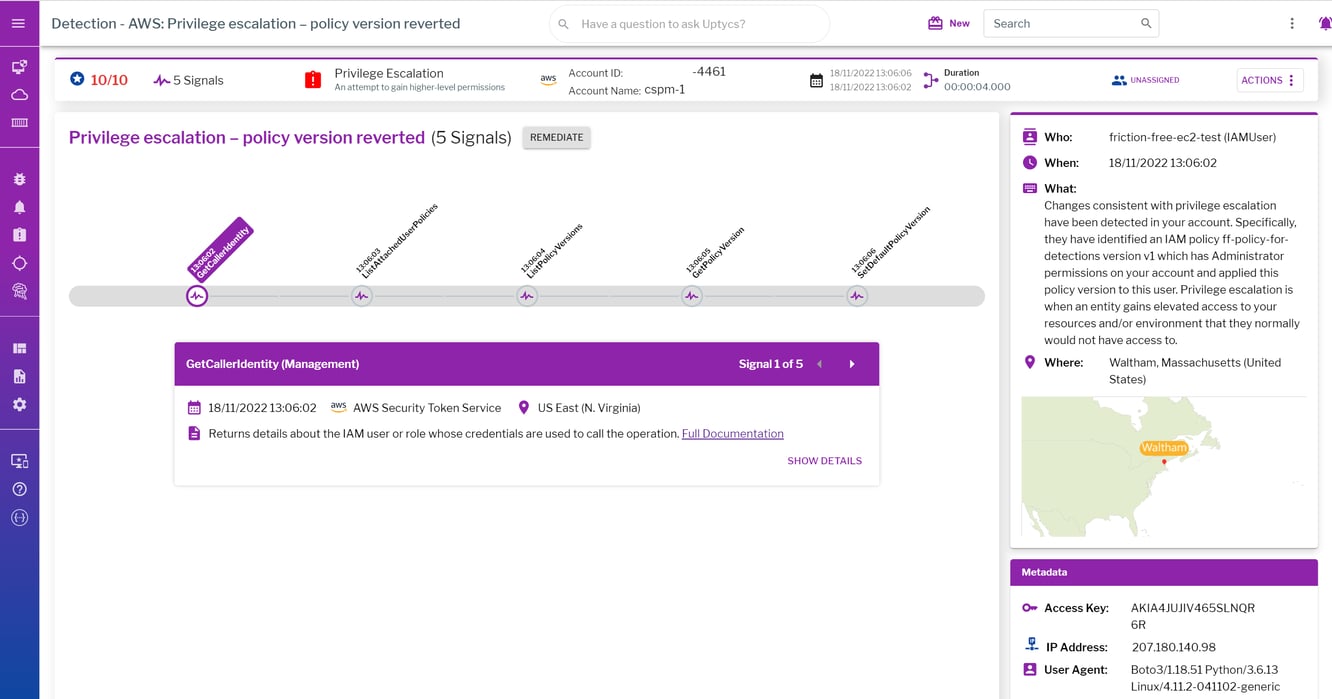
An example of a detection for privilege escalation in the cloud
Enumeration
What does enumeration in a cloud environment look like? Well, let’s start with the definition, which is the process of extracting usernames, machine names, network information and other services to discover potential attack vectors. An example of what this looks like in the cloud is when a threat actor is able to list all your Lambda functions, aliases, versions, execution roles, etc. With this information, they’re able to identify new attack vectors to further exploit your environment.
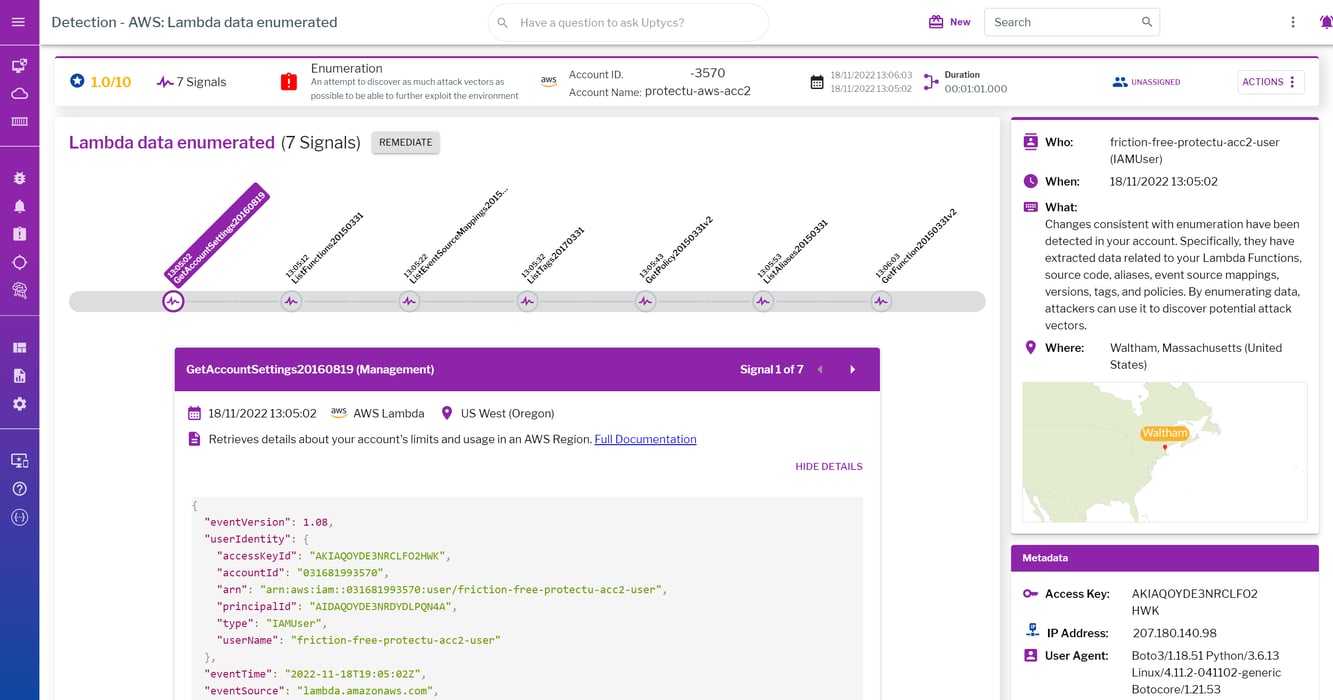
An example of a detection for enumeration in the cloud
Persistence
What does persistence in a cloud environment look like? Persistence can be defined as keeping access to an environment across restarts, changed credentials, and other interruptions that could otherwise cut off a threat actor’s access. Another term to describe this is creating a backdoor. An example of what this looks like in the cloud is when a threat actor modifies the trust policy of existing IAM roles to include a different user or account as the ‘trusted' principal who can assume that role.
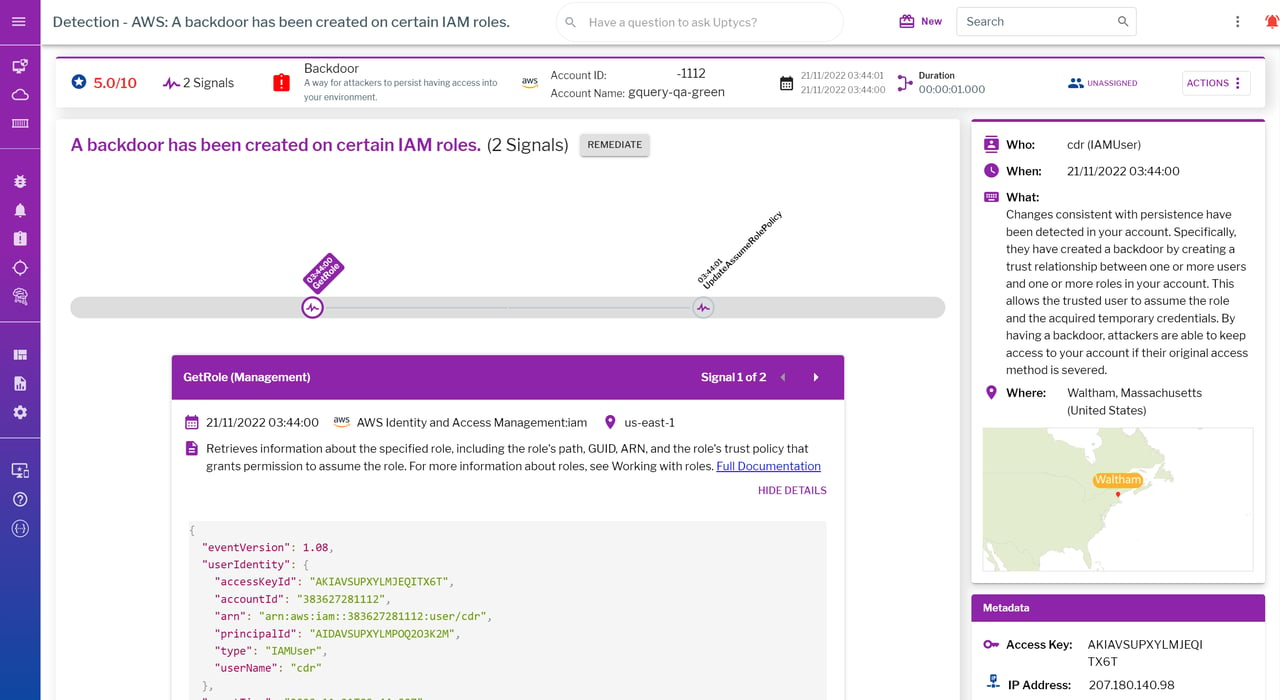
An example of a detection for persistence in the cloud
Exploitation
What does exploitation in a cloud environment look like? Exploitation can be defined as finding and taking advantage of a security flaw or vulnerability within your environment. In the cloud, sometimes this also means taking advantage of an overly permissive principal. With cloud environments nowadays, these types of overly permissive policies are plentiful for threat actors to exploit. An example of what this looks like in the cloud is when a threat actor uses AWS Systems Manager Run Command to perform remote code execution on one or more of your EC2 instances.
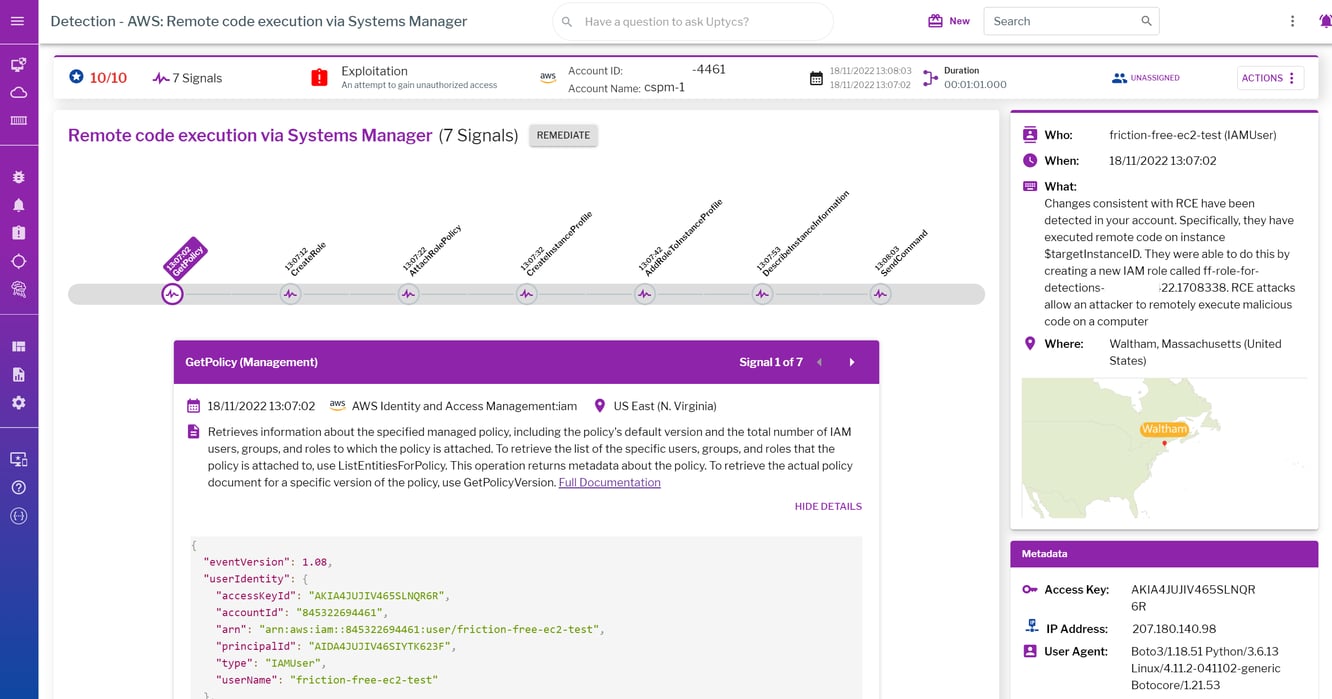
An example of detection for exploitation in the cloud
Data Exfiltration
What does data exfiltration in a cloud environment look like? Exfiltration can be defined as trying to steal your data. This is probably one of the most popular attacks threat actors target. By having access to your data, they have access to potential secrets (usernames, passwords), sensitive information (PII data or intellectual property), or now have a target to deploy ransomware on. An example of what exfiltration looks like in the cloud is performing reconnaissance of your EBS volumes, taking a snapshot of one or more target EBS volumes, modifying the attributes of these snapshots so that a different AWS account is able to use it to create a new EBS volume and attach it to their EC2 instance.
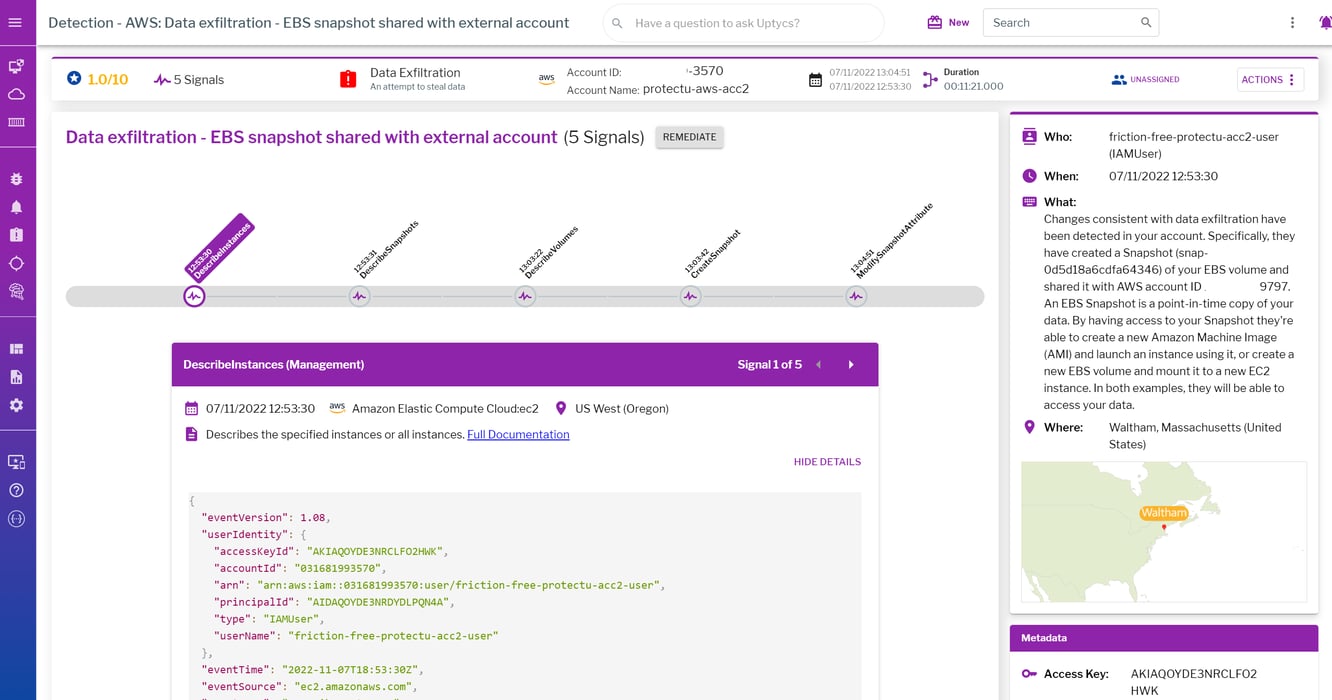
An example of a detection for data exfiltration in the cloud
Want to see what Uptycs CDR looks like for yourself? Try out our CDR interactive product tour.

-1.png?width=200&name=image%20(4)-1.png)