Imagine you’re a security analyst working remotely and you see something is amiss with a machine in your fleet. SSH isn’t an option because it expands the attack surface. Plus, there’s no guarantee the machine you need to investigate is even accessible through SSH. What do you do?
I ran into this situation myself. I wanted to improve Stripe’s remote investigation capabilities because the company’s workforce is distributed around the world. “Remote” is a very common scenario for us, and I needed a fast and secure way to investigate problems. I also wanted to make this improvement using technology we already have.
I found a solution when I brought two things together: Uptycs APIs and goquery.
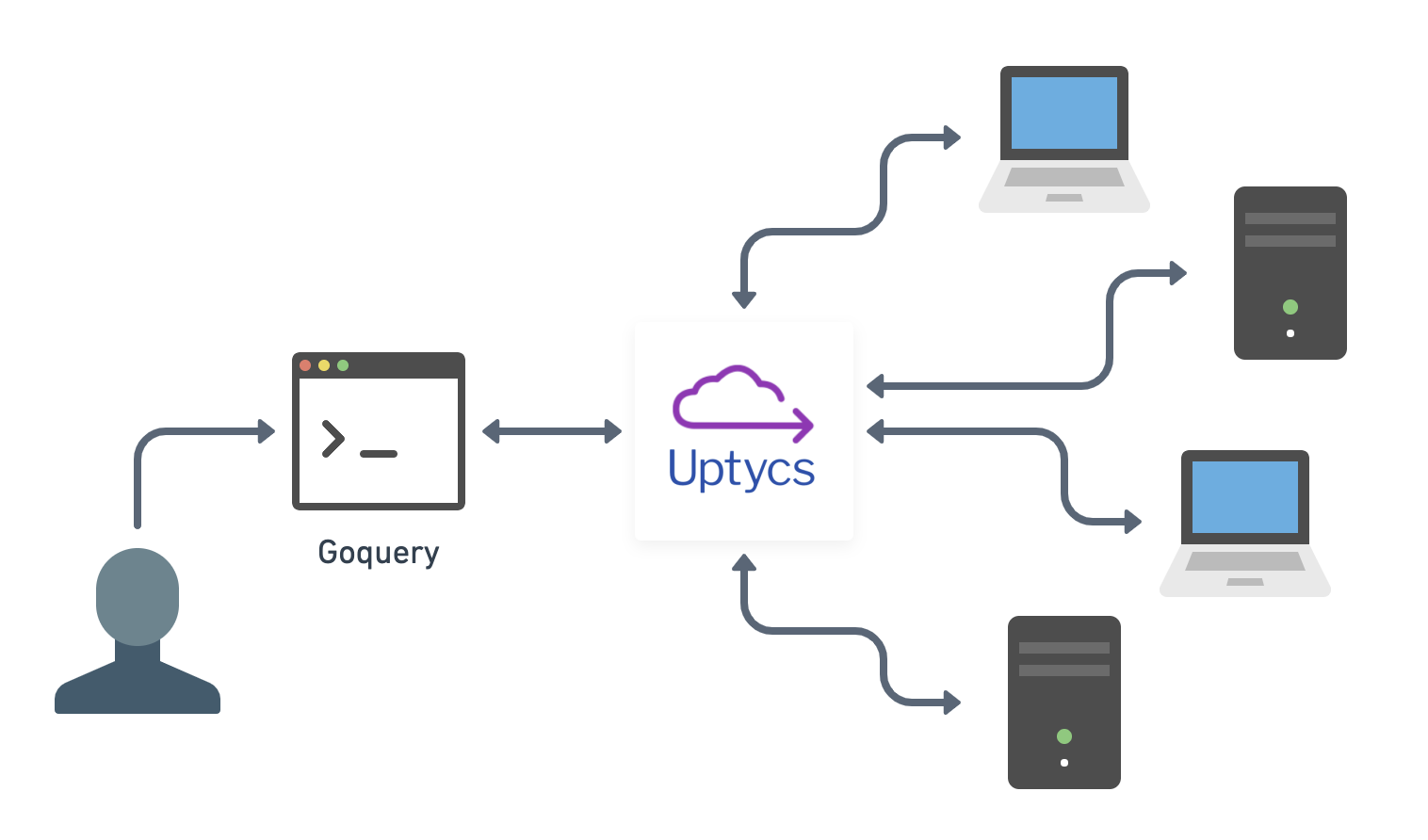
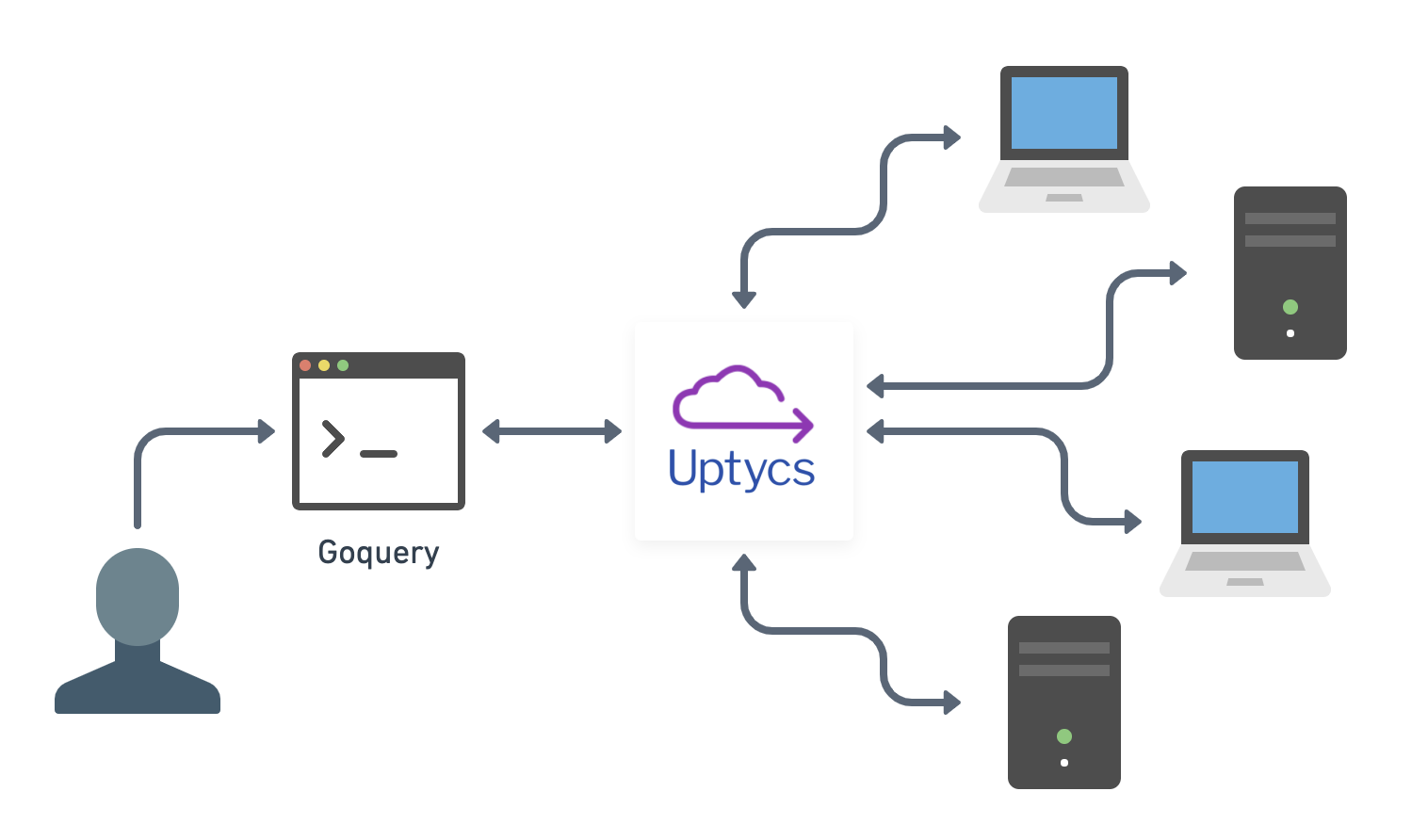
A remote investigation workflow using goquery and Uptycs. (Image via Carl Vincent.)
Goquery, co-created by Andrew Guthrie and Mitchell Grenier, is an open source remote investigation client that simulates a terminal by using osquery. It provides SSH-like access without the risk. Analysts who aren’t well versed in SQL can also use goquery to navigate systems with simulated Unix commands in a terminal environment. Goquery translates these commands into SQL.
Goquery offers SSH-like access to machines in your fleet without the security risk. This short video shows me connecting to a machine on Uptycs and issuing a series of commands. (Video via Carl Vincent.)
This combination of Uptycs and goquery helps me investigate issues in real time without expanding the attack surface. I can ls around a machine. I can sit on one terminal in a coffee shop and access 4,000 endpoints.
There’s another benefit, too, and it’s timely. As the COVID-19 pandemic forces work into home offices and other remote locations, combinations like Uptycs and goquery—connected because of Uptycs’ commitment to open APIs—help analysts maintain observability and access during these unexpected times. That’s important because security teams can’t be held back by their tools. They need to be empowered to swiftly adapt no matter where they, their fleets, and their colleagues are located.
Discover how to use osquery for threat hunting in this on-demand webinar.
Learn more
- “An introduction to goquery” - Presentation by Mitchell Grenier and Andrew Guthrie at osquery@scale 2020.