The need to centralize and analyze security data from various sources has never been more critical. Uptycs, an AWS partner with deep expertise in cloud security solutions, has joined forces with Amazon Security Lake to offer a powerful integration that empowers organizations to enhance their security posture across AWS services. Let’s explore the seamless integration between Uptycs and Amazon Security Lake, highlighting the value it brings to organizations seeking comprehensive cloud security.
Uptycs and AWS: Better Together
Uptycs and AWS share a common goal: To help organizations secure their cloud environments effectively. Combining Uptycs' expertise in cloud security and AWS's industry-leading cloud platform, the integration between Uptycs and Amazon Security Lake provides comprehensive security visibility, actionable insights, and robust protection for AWS environments.
Together, we can strengthen cloud security and empower organizations to thrive in the cloud-first era.
Overview of Amazon Security Lake
Amazon Security Lake is a fully-managed security data lake service provided by AWS. It offers organizations a centralized solution for aggregating and analyzing security logs and events from various sources, including AWS environments, on-premises systems, and third-party services. By automatically collecting and normalizing security data using the Open Cybersecurity Schema Framework (OCSF), Security Lake enables organizations to understand their security posture comprehensively. With Security Lake, organizations can improve their security operations, enhance threat detection capabilities, and effectively protect their workloads, applications, and data.
Introducing Uptycs Unified CNAPP and XDR Security Platform
Uptycs’ unified Cloud-Native Application Protection Platform (CNAPP) with Extended Detection and Response (XDR) helps organizations protect cloud-native applications and infrastructure from threats across endpoints, cloud environments, and containers. By eliminating silos and providing comprehensive visibility, detection, and response capabilities, Uptycs empowers organizations to strengthen their security posture and proactively defend against evolving threats. With advanced analytics and machine learning, Uptycs identifies known and unknown threats, enabling organizations to stay ahead of attackers.
Integration Overview
The integration between Uptycs and Amazon Security Lake combines powerful capabilities for enhanced security data management and analysis. Uptycs seamlessly sends a wealth of security data in the OCSF format to Security Lake. This includes behavioral threat detections from endpoints and cloud workloads, policy violations, risky policies, misconfigurations, vulnerabilities, and more.
By leveraging the OCSF schema, Uptycs ensures that the security data it sends to Security Lake is standardized and easily consumed. This enables organizations to correlate and analyze data from multiple sources within the Security Lake environment, including Uptycs' comprehensive security platform. With this integration, organizations can gain a holistic view of their security posture and effectively detect and respond to potential threats.
Prerequisites
Before setting up the integration between Uptycs and Amazon Security Lake, there are a few prerequisites that need to be in place:
- AWS Account with Security Lake: You will need an AWS account that has Amazon Security Lake configured. This involves setting up the necessary resources and permissions to aggregate and manage security-related log and event data within Security Lake. You can refer to the AWS documentation for guidance if you haven't set up Security Lake yet.
- Specific Requirements and Permissions: Certain requirements and permissions must be met to ensure a smooth integration. These may include having the AWS CLI version greater than 2.11.24, being a customer of Uptycs CSPM, and having the necessary IAM roles and policies configured for data ingestion and management.
It's important to review and fulfill these prerequisites before proceeding with the integration setup. This will help ensure that the integration process goes smoothly and that you can fully leverage the capabilities of Uptycs and Amazon Security Lake for comprehensive security monitoring and analysis.
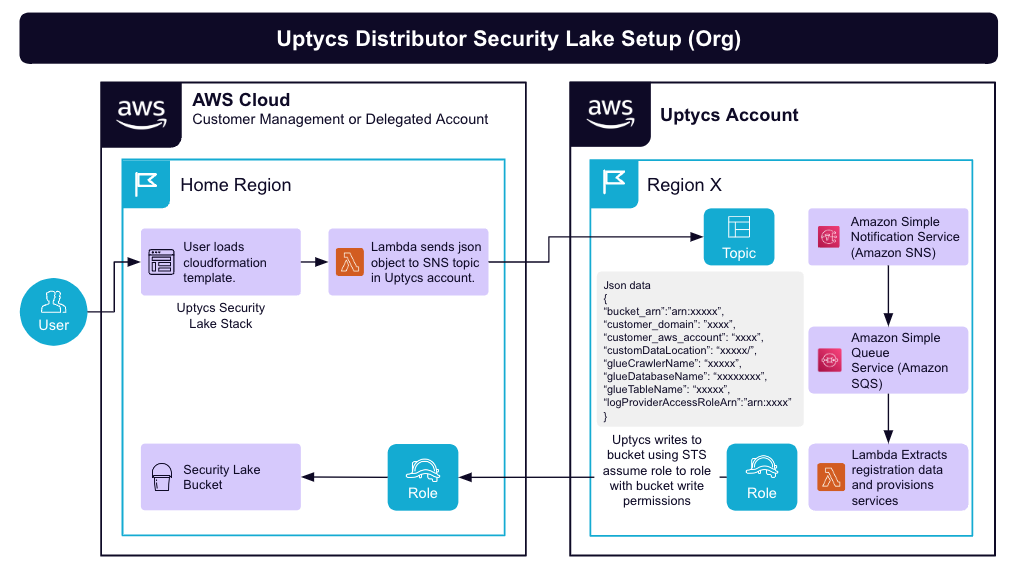
Integration Guide
The integration process begins with the replication and transformation of data. Uptycs replicates and enriches endpoint, cloud workload, and identity data, ensuring that a wealth of valuable information is captured for analysis. This data is then transformed into the Open Cybersecurity Schema Framework (OCSF) schema, a standardized format that enables efficient processing and analysis. Uptycs ensures optimized storage and retrieval for subsequent analysis by converting the data into Parquet files.
Once the data is transformed, it must be uploaded to the customer-owned Amazon S3 bucket for ingestion by Security Lake. This step ensures that the enriched and standardized data is readily available for analysis, threat detection, and incident response within the Security Lake environment. The integration process is designed to be straightforward and streamlined, enabling organizations to quickly and efficiently set up the necessary data replication and transformation pipelines.
Benefits of the Integration
The integration between Uptycs and Amazon Security Lake offers numerous benefits to organizations seeking to enhance their security operations and gain comprehensive visibility of their environment. By combining the capabilities of Uptycs' advanced security solutions with the power of Amazon Security Lake, organizations can unlock the following advantages:
- Improved Security Operations: The integration provides organizations with enhanced threat detection and incident response capabilities. By centralizing and analyzing security data in Security Lake, organizations can identify and respond to security incidents more effectively, minimizing the impact of potential threats.
- Enhanced Visibility and Analysis: With the integration, organizations can achieve a holistic view of their security-related log and event data. This comprehensive visibility enables better analysis and identification of patterns, anomalies, and potential security risks. By leveraging the power of Security Lake, organizations can gain actionable insights to strengthen their security posture.
- Streamlined Compliance Monitoring: The integration with Amazon Security Lake facilitates compliance monitoring by providing a centralized repository for security-related data. This simplifies auditing and demonstrates adherence to regulatory standards and industry best practices, saving time and resources.
Use Cases and Examples
The integration between Uptycs and Amazon Security Lake opens up a wide variety of use cases for organizations across various industries. Here are a few examples:
- Security Analytics: Organizations can leverage the integrated solution to perform in-depth security analytics, leveraging the enriched and standardized data in Security Lake. This enables them to identify and investigate security incidents, detect emerging threats, and proactively address vulnerabilities.
- Compliance Monitoring: The integration streamlines compliance monitoring by providing a centralized platform to collect, store, and analyze security-related data. This facilitates monitoring regulatory compliance requirements, such as those specified by NIST, HIPAA, or PCI-DSS, allowing organizations to demonstrate adherence to these standards.
- Threat Intelligence: The integration enables organizations to leverage the rich data in Security Lake for threat intelligence purposes. By analyzing the data, organizations can uncover valuable insights and indicators of compromise, enhancing their threat intelligence capabilities and enabling proactive threat hunting.
Conclusion
The integration between Uptycs and Amazon Security Lake is a strong solution for organizations seeking to strengthen their security operations, gain comprehensive visibility, and streamline compliance monitoring. By leveraging the advanced capabilities of Uptycs' unified CNAPP and XDR platform with the centralized data management of Security Lake, organizations can enhance their security posture and effectively respond to emerging threats. As a committed partner, Uptycs continues to support and enhance the integration, ensuring that customers can derive maximum value from this powerful combination of technologies.







