The scalability and flexibility offered by cloud computing come with significant security considerations. In the AWS ecosystem, Auto Scaling Groups (ASGs) facilitate application scaling, but this feature also introduces security vulnerabilities. For example, a misconfiguration in a single EC2 instance within an ASG can precipitate security issues, potentially impacting the entire group of instances.
Understanding the risk
Auto Scaling Groups (ASGs) in AWS utilize launch configurations or templates to specify the setup for EC2 instances, which includes setting the instance type, Amazon Machine Image (AMI), key pairs, security groups, and IAM roles. Vulnerabilities can arise not only from the misconfiguration of these elements but also from the exploitation of such misconfigurations. For example, an outdated AMI may harbor unpatched security vulnerabilities that could be exploited to gain unauthorized access to the system. Similarly, IAM roles with overly broad permissions might inadvertently grant access to sensitive resources, increasing the risk of data breaches.
We explore the mechanisms through which attackers exploit these vulnerabilities, highlighting the potential threats they pose. Exploiting an outdated AMI, for instance, could allow attackers to execute code remotely on the EC2 instance, providing them a foothold in the cloud environment. From there, they could leverage overly permissive IAM roles to access and exfiltrate sensitive data, leading to significant security incidents. Understanding these exploitation mechanisms and potential threats is crucial for extending the risk analysis beyond the initial ASG setup to encompass the broader implications of these vulnerabilities on cloud security.
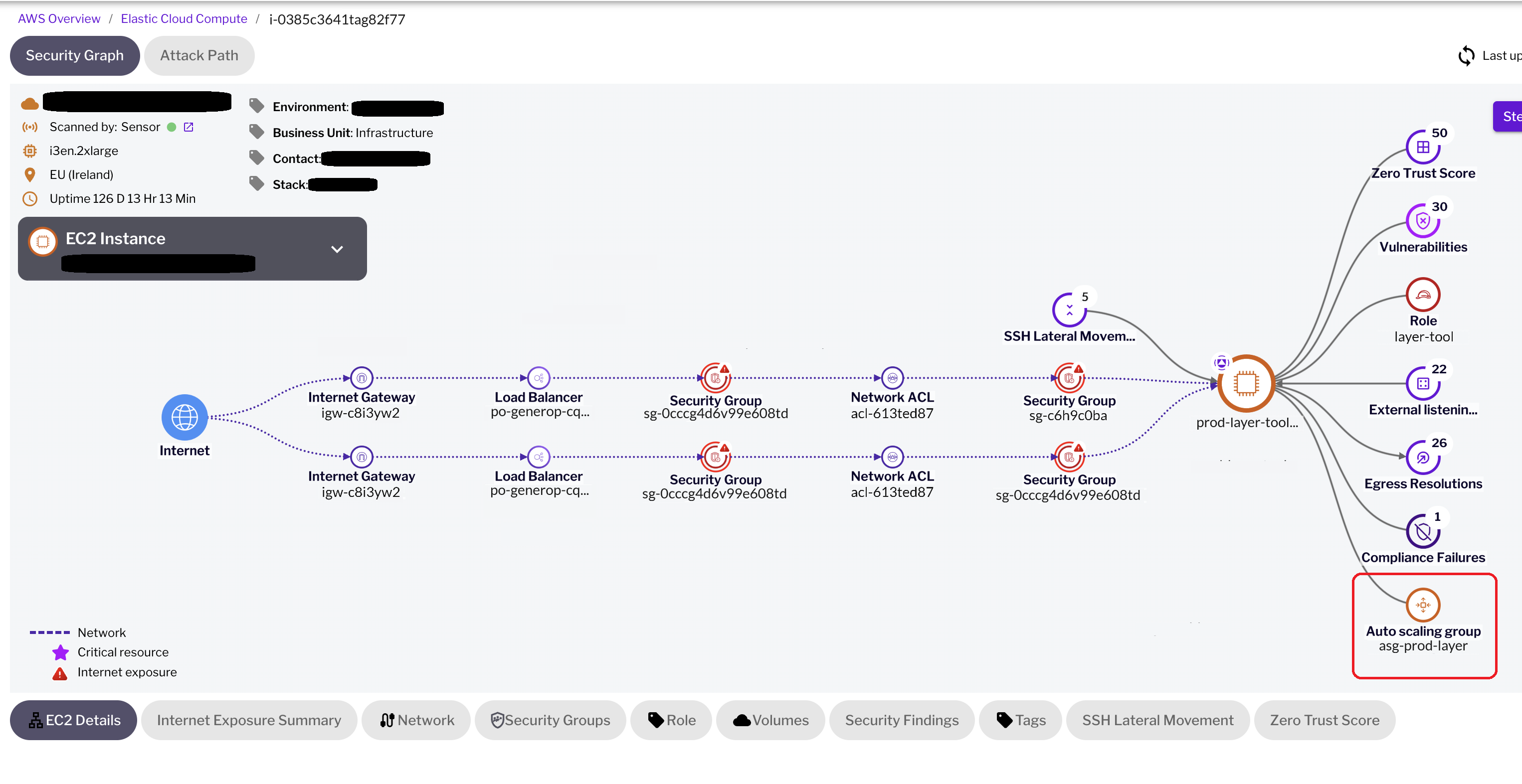
Figure 1 - Here we see a vulnerable EC2 instance and the ASG it belongs to.
Launch configurations and threat actors
Following the identification of vulnerabilities, threat actors often turn their attention to the launch configurations or templates used by ASGs. They look for outdated AMIs specified within these templates, which may contain unpatched vulnerabilities in operating systems or applications. Exploiting these vulnerabilities allows attackers to compromise EC2 instances from the moment they are launched. A subtler tactic employed by attackers is to modify an existing launch template, updating it to include the vulnerable AMI and then setting this compromised version as the default. This action ensures that all new instances launched by the ASG are predisposed to the same vulnerabilities, significantly expanding the potential attack surface without immediate detection.
Security group configurations within these launch templates are also critical. Improperly configured security groups that leave essential ports open to the internet, such as SSH (port 22) or RDP (port 3389), serve as direct avenues for attackers to gain initial access. Once inside, attackers can leverage these entry points to perform lateral movements within the cloud infrastructure, escalating the impact of the breach.
IAM Role Misconfigurations
The IAM roles assigned to EC2 instances within ASGs also present potential security risks. When these roles are configured with overly broad permissions, they inadvertently empower the instances—and any attacker who gains control over them—with the capability to access and potentially manipulate sensitive resources. This could lead to unauthorized actions, such as accessing S3 buckets containing sensitive data or modifying DNS records in Route 53, thereby compromising the security and integrity of an organization's data and systems. Proper management and configuration of IAM roles are essential to mitigate such risks and protect against unauthorized access and data breaches.
Real-world implications
FinCorp, a financial services entity, relies on AWS for hosting its customer-oriented applications, utilizing ASGs to manage scalability. The ASGs are configured with launch templates detailing specific AMIs, security group settings, and IAM roles, the latter of which provides crucial access to S3 buckets holding confidential client data.
Compromising the account
The breach initiates when an attacker, through stolen credentials, gains unauthorized entry into FinCorp's AWS account. These credentials could be obtained from phishing attacks, leaked databases, or other means. Once inside, the attacker focuses on the ASGs, specifically targeting launch templates associated with outdated and vulnerable AMIs identified from vulnerability databases.
Manipulating the launch template
Having accessed the account, the attacker leverages their privileges to modify an existing launch template. They replace the AMI with one containing known vulnerabilities, adjust the security group configurations to open ports to the internet, and attach an overly permissive IAM role, vastly increasing the attack surface. This altered launch template version is then set as the default, ensuring all new instances launched by the ASG inherit these vulnerabilities.
Lateral movement and data breach
With the compromised instances now running, the attacker uses them as a springboard for further malicious activities. Due to the overly permissive IAM role associated with these instances, the attacker can easily list, access, and exfiltrate data from the S3 buckets containing sensitive client information, leading to a significant data breach.
Challenges in detection and response
The dynamic nature of ASGs, which constantly adjust the number of instances based on load, complicates the detection of compromised instances. This fluid environment can obscure anomalies, especially if the attacker minimizes their footprint to avoid detection. Conventional security solutions might not keep up with this rapid scalability, delaying the identification of security breaches.
This scenario highlights the critical need for dynamic and robust security monitoring and response mechanisms capable of adapting to the ever-changing cloud infrastructure, ensuring the protection of resources against sophisticated attack vectors.
Introducing Uptycs Security Graph
Uptycs Security Graph is designed to address the complex challenges inherent in cloud environments, offering a comprehensive overview of cloud assets. This tool is pivotal in enabling organizations to identify and rectify vulnerabilities and misconfigurations within their AWS infrastructure, including the detailed intricacies associated with ASGs.
It provides an in-depth view of the relationships and dependencies between cloud assets, crucial for understanding how a single misconfiguration in an EC2 instance can affect the overall security of connected assets, including other instances within the ASG. This capability allows security teams to quickly determine if a vulnerable EC2 instance is a component of an ASG and to fully grasp the makeup of all EC2 instances within that ASG.
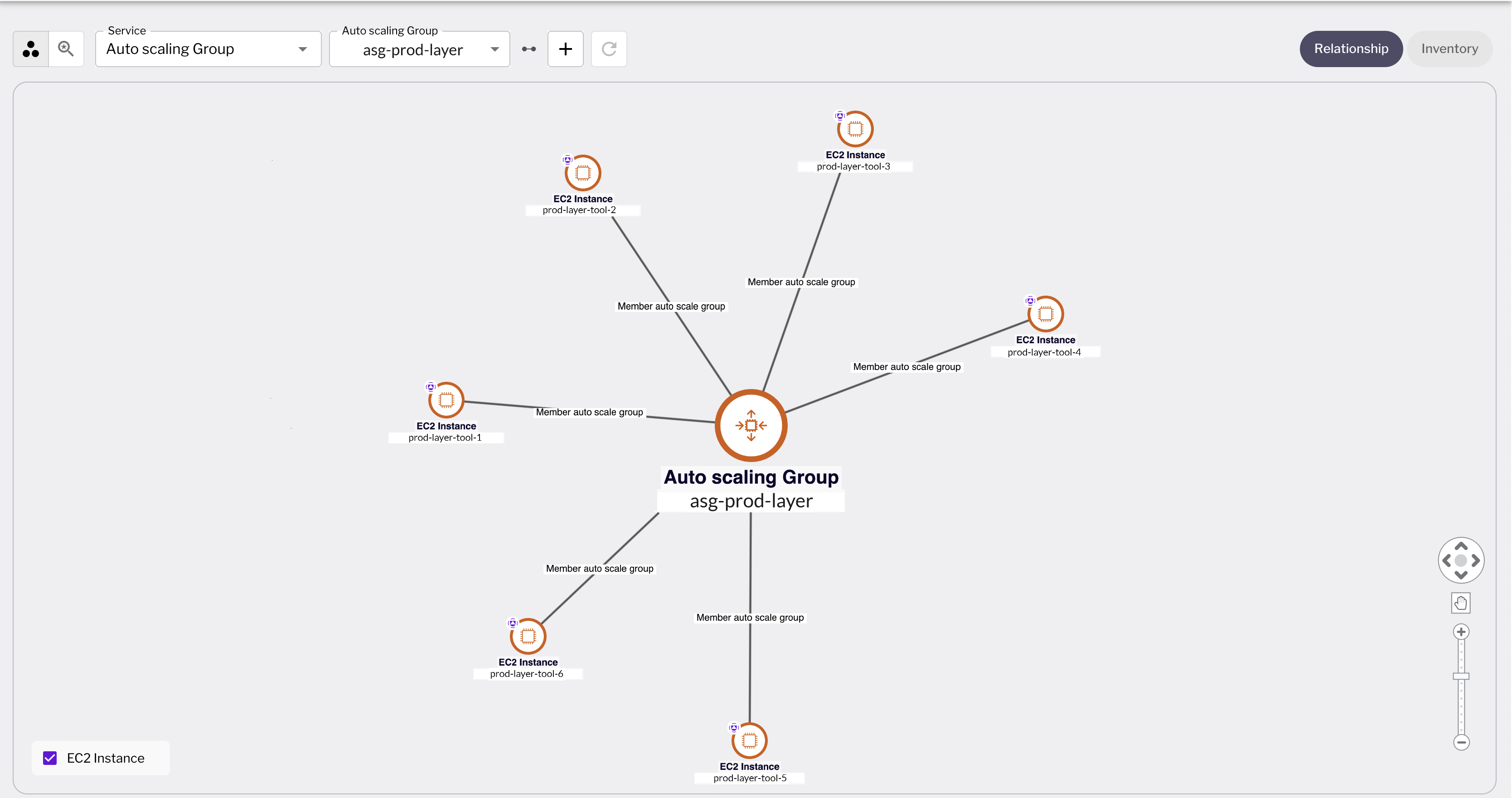
Figure 2 - Here will see a drill-down view of the ASG and all EC2 instances associated with it.
The Uptycs advantage
What sets Uptycs Security Graph apart is its proficiency in not just identifying vulnerabilities but also contextualizing them within the broader cloud ecosystem. This contextual understanding is crucial for security professionals and CISOs, assisting in the prioritization and swift mitigation of security issues. For instance, Security Graph's ability to detect an EC2 instance within an ASG with an open SSH port highlights a significant risk due to potential lateral movement. Uptycs enhances this capability by outlining the complete dependency chain of the EC2 instance, including the ASG name, Launch Template ID, and detailed launch template specifications such as versions, ownership, AMI ID, instance type, and more. This comprehensive information streamlines the remediation process, allowing for quick adjustments without the need for exhaustive searches.
Moreover, Uptycs Security Graph simplifies the complex task of cloud security management. Its intuitive interface and actionable insights empower security teams to effectively navigate the cloud environment, proactively identifying and mitigating potential threats. This proactive approach ensures that organizations can uphold a strong security posture amidst the dynamic and intricate landscape of cloud computing.
Key takeaways
The scalability of cloud environments, particularly autoscaling groups in AWS, brings both advantages and inherent security risks. These vulnerabilities, if not properly addressed, pose significant threats to organizations.
As cloud infrastructure becomes increasingly complex, the need for sophisticated security solutions becomes indispensable. Uptcys Security Graph delivers crucial visibility and insights into hidden threats within cloud infrastructures.
Grasping the nuances of ASGs and their associated vulnerabilities is just the beginning. Uptycs Security Graph enables organizations to transcend conventional security measures, uncovering concealed threats and fortifying cloud defenses to ensure a more secure and resilient cloud environment.

-1.png?width=200&name=image%20(4)-1.png)





