Recently, while monitoring dark web forums and Telegram channels, the Uptycs Threat Research team made a compelling discovery: a formidable menace dubbed The Meduza Stealer.
Crafted by an enigmatic actor known as 'Meduza', this malware has been specifically designed to target Windows users and organizations, currently sparing only ten specific countries from its reach.
The Meduza Stealer malware has a singular objective: comprehensive data theft. It pilfers users' browsing activities, extracting a wide array of browser-related data. From critical login credentials to the valuable record of browsing history and meticulously curated bookmarks, no digital artifact is safe. Even crypto wallet extensions, password managers, and 2FA extensions are vulnerable.
Left unchecked, the consequences for those affected could be severe, including financial losses and the potential for large-scale data breaches that can have far-reaching implications for organizations.
While Meduza may be a recent addition to the realm of cybercrime and no specific attacks have been attributed to date, the risks it poses shouldn't be underestimated.
To proactively address this emerging threat, Uptycs has taken action by incorporating a YARA rule into our product. This integration empowers us to conduct thorough memory scanning, enabling swift detection and effective mitigation of the Meduza threat.
What sets Meduza apart is its evolving nature. Our conversations with the malware's administrator highlight that it is not simply another run-of-the-mill ransomware, but an actively developed tool, poised for the potential addition of new features. The malware admin did explicitly state that their operations do not involve any ransom activities and that their sole focus is on functioning as a stealer. Currently, Meduza can avoid detection in certain countries and prevent execution if the attacker's server is unreachable, making it an extremely stealth cybersecurity threat.
The Uptycs threat research team’s analysis of the Meduza stealer reveals its distribution methods, capabilities, potential impact, and highlights their concerted efforts to counter this threat.
Marketing & Distribution Tactics of Meduza Stealer
The administrator of the Meduza stealer has been employing sophisticated marketing strategies to promote this malicious offering. In a calculated move to gain trust and confidence, they have initiated static and dynamic scans of the Meduza stealer file using some of the industry's most reputable antivirus software. Screenshots were then shared demonstrating that this potent malware could evade detection by these top-tier antivirus solutions.
What makes Meduza stealer particularly crafty is its operational design. This binary does not employ obfuscation techniques, a common practice among similar threats, making it harder to identify and trace. Additionally, it seeks to establish a connection with the attacker's server before it commences the theft of data from victim machines. If this connection fails, it terminates promptly, further complicating attempts to trace its activities.
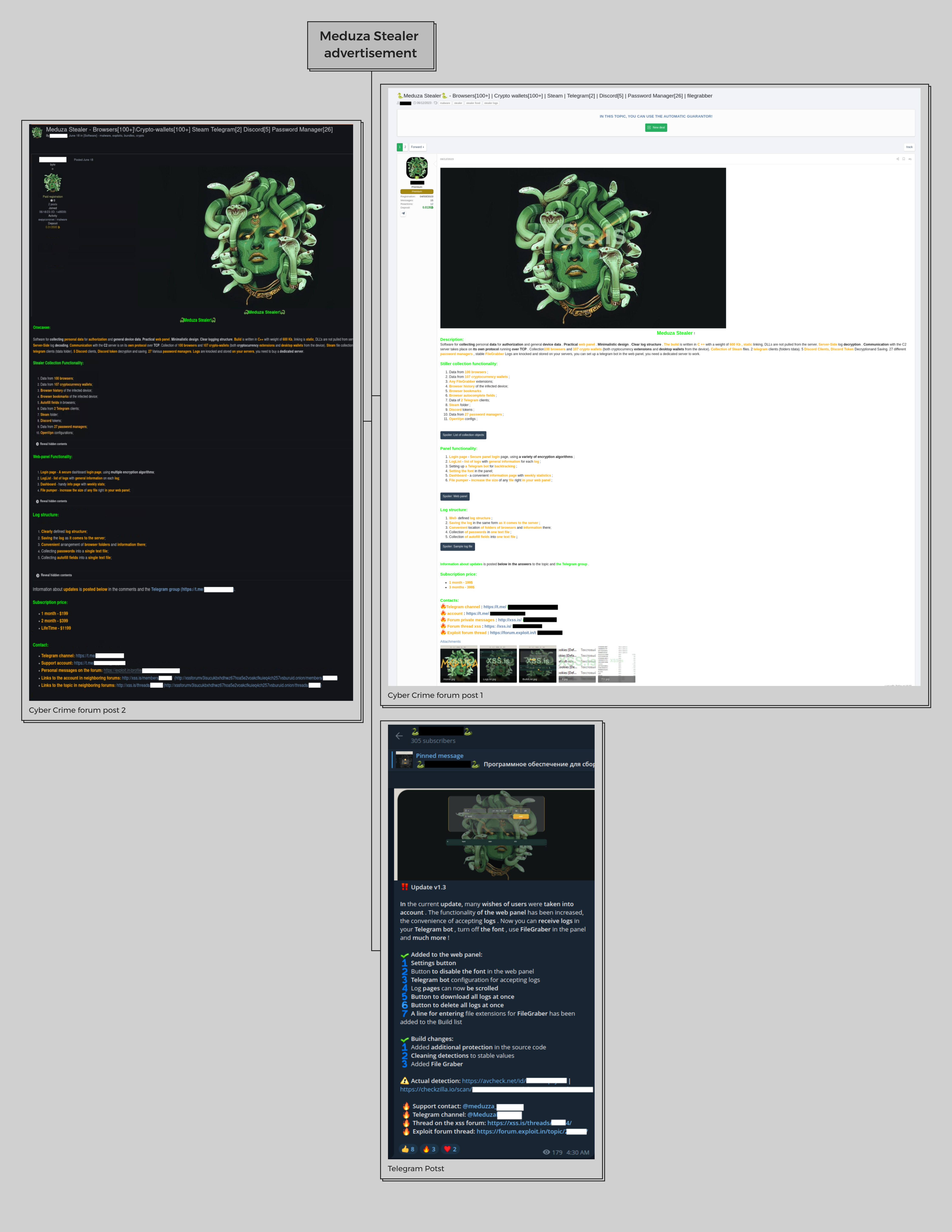
The marketing efforts didn't stop at proving the malware's efficacy. As shown in Figure 1, the administrator has been advertising the Meduza stealer aggressively via cybercrime forums and Telegram channels.
Fig.1 – Advertising via cyber-crime forum and Telegram
What's more concerning is that a large portion of antivirus software has proven ineffective against the Meduza stealer binary, either failing to detect it statically or dynamically. (Fig. 2, Fig. 3).
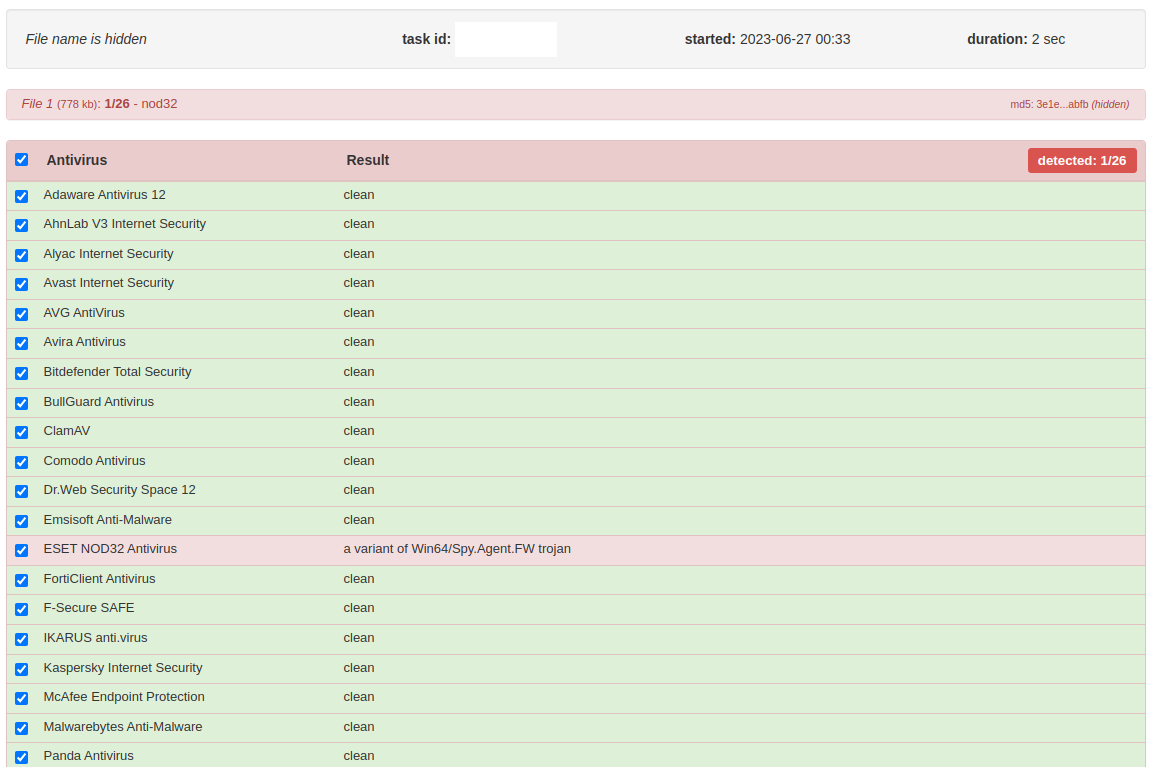
Fig.2 – Static AV scan report
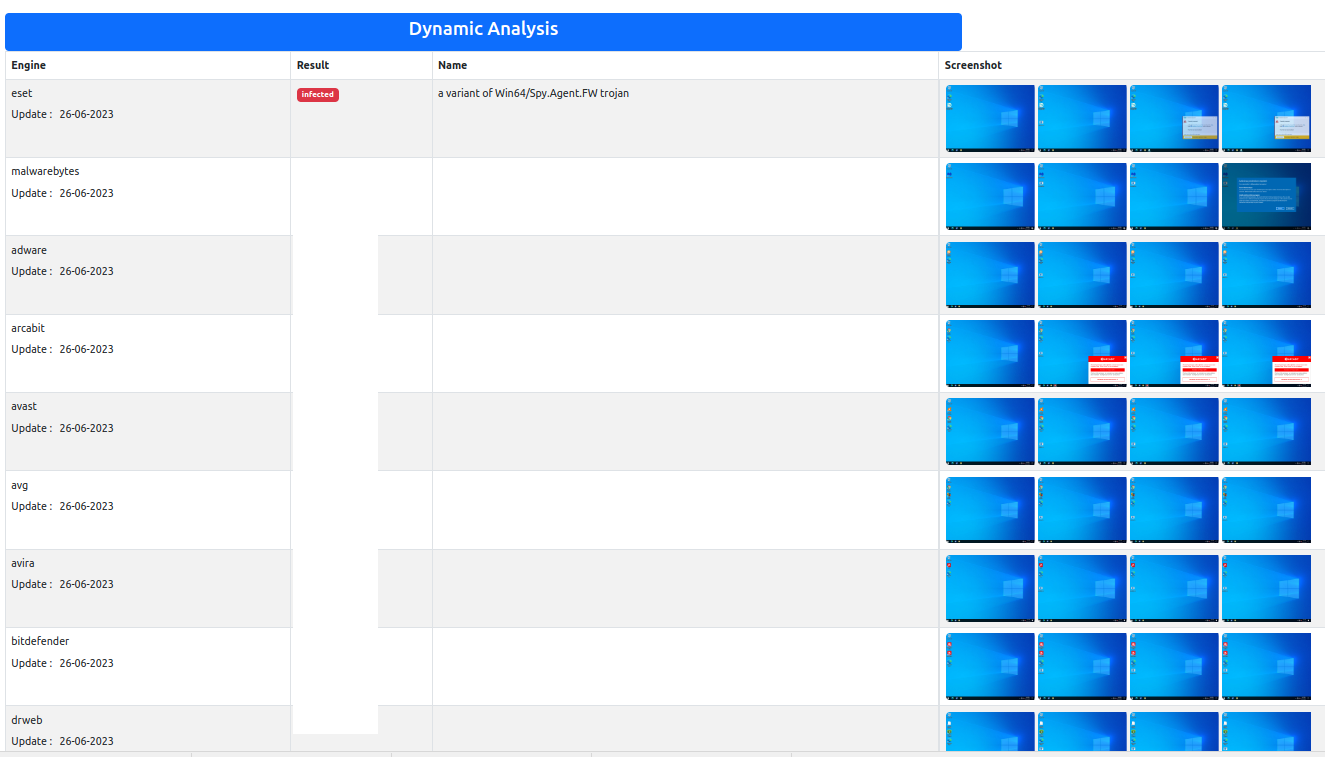
Fig.3 – Dynamic AV scan report
But the real game-changer in their marketing strategy has been the pricing model and the added control provided to subscribers. To attract potential customers, the administrator offers access to the stolen data through a user-friendly web panel (Fig.4). They present different subscription options, including a one-month, three-month, and lifetime access plan, each with its own price point.
Inside this web panel, subscribers can craft their customized binary options. The panel offers a wealth of information, including IP addresses, geographical data, OS build names, and even the count of stored passwords, wallets, and cookies. This feature allows subscribers to download or delete the stolen data directly from the web page, granting them an unprecedented level of control over their ill-gotten information. This in-depth feature set showcases the sophisticated nature of the Meduza stealer and the lengths its creators are willing to go to ensure its success.
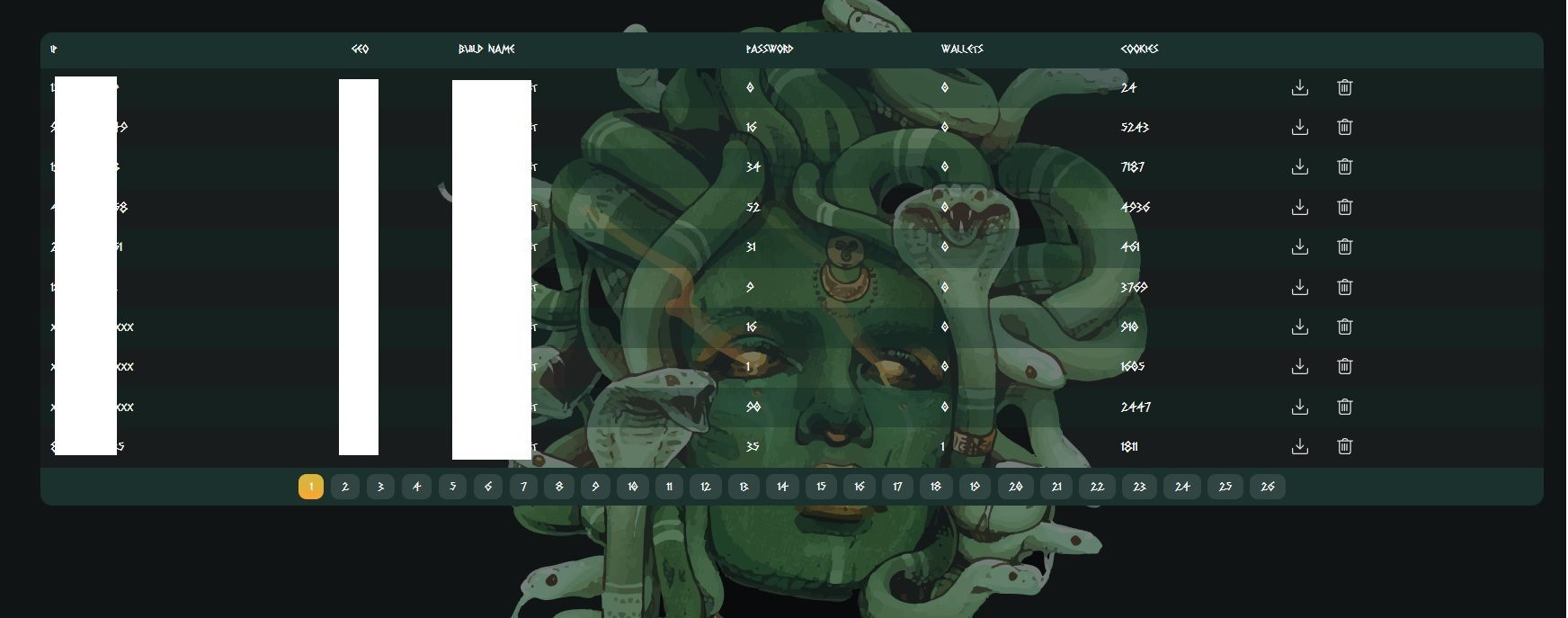
Fig.4 – Web panel
Meduza Stealer's Workflow
The Meduza Stealer initiates its operations once it successfully infiltrates a machine. The first step it performs is a geolocation check. If the victim's location is in the stealer's predefined list of excluded countries, the malware operation is immediately aborted.
However, if the location isn't on the list, Meduza Stealer checks if the attacker's server is active. In case the server isn't accessible, the stealer also promptly terminates its activity. If both conditions—location check and server accessibility—are favorable, the stealer proceeds to gather extensive information. This includes collecting system information, browser data, password manager details, mining-related registry information, and details about installed games.
Once this comprehensive set of data is gathered, it is packaged and uploaded, ready to be dispatched to the attacker's server, thereby completing the stealer's operation within the infected machine. See Figure 5.
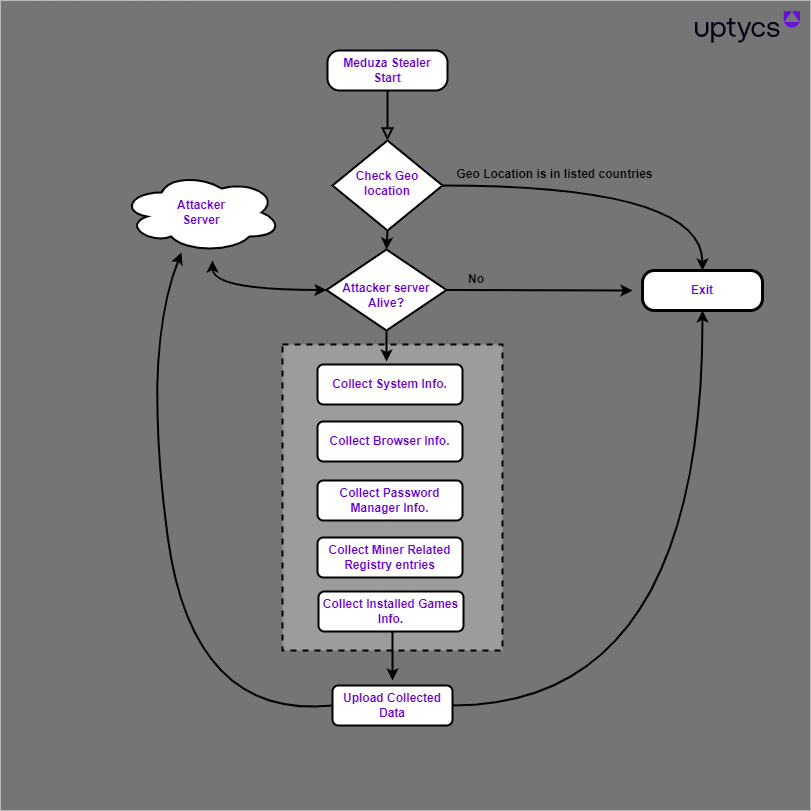
Fig.5 – Work flow
Additionally, it's important to highlight the variety of data that the malware collects - system info, browser info, password manager info, miner related registry info, and installed games info. This demonstrates the broad potential impact of an infection, as it targets not only personal and financial data, but also system-specific and potentially proprietary information. Lastly, the swift uploading and transferring of the collected data to the attacker's server accentuates the speed at which a breach can occur and the urgent need for effective detection and protection measures.
Utilizing APIs and country exclusions: How Meduza stealer operates
This section delves into the operational mechanisms of Meduza Stealer, highlighting its utilization of Application Programming Interfaces (APIs) and the implementation of a country exclusion feature. The unraveling of these technical aspects provides a clearer understanding of how this malware functions, assisting users and cybersecurity professionals in anticipating its tactics and developing more effective countermeasures. The exploration covers everything from the initial infection phase to how Meduza communicates with its Command and Control server, demonstrating the malware's sophistication and wide-reaching capabilities.
First, the stealer leverages the GetUserGeoID and GetGeoInfoA APIs on the victim's machine to obtain country details, which are subsequently compared to a predefined list. See Figure 6.
 Fig.6 – Listed countries
Fig.6 – Listed countries
Exclusion List
The table below outlines the country codes and corresponding names from the exclusion list.
|
Country name |
Country code |
|
Russia |
RU |
|
Kazakhstan |
KZ |
|
Belarus |
BY |
|
Georgia |
GE |
|
Turkmenistan |
TM |
|
Uzbekistan |
UZ |
|
Armenia |
AM |
|
Kyrgyzstan |
KG |
|
Moldova |
MD |
|
Tajikistan |
TJ |
If the victim's country isn't part of this list, the malware tries to establish a connection with the attacker's server (Fig.7). If the connection fails, the process comes to a halt. A likely reason for this particular list of excluded countries is that countries often avoid launching cyberattacks against their own or friendly nations, although the specific rationale behind this restraint may not be explicitly stated.
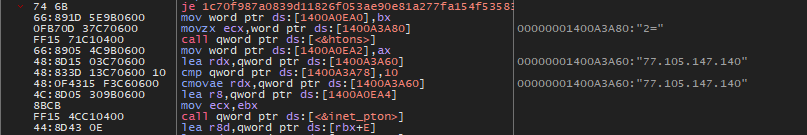
Fig.7 – Connect threat actor server
Upon activation, the malware begins to collect system information from the victim's machine, using a variety of Windows APIs such as GetUserName, GetComputerName, GetCurrentHWProfile, and EnumDisplayDevices. It also retrieves the public IP address using the HTTPS-based API found at https[:]//api.ipify[.]org. A screenshot of the current Windows screen is taken and converted into base64 format.
System details collected
- System build details
- Computer name
- CPU details
- Execute path
- Geo
- GPU
- Hardware ID details
- Public Ip
- OS details
- RAM details
- Screen Resolution details
- Screenshot
- Time
- TimeZone
- Username

Fig.8 – Victim details
The stealer possesses a predefined list of browsers and proceeds to enumerate the "User Data" folder, where it reads various browser-related data such as Browser History, Cookies, Login Data, Web Data, Login Data for Account, and Local State.
Listed browsers
|
Google\Chrome |
Maxthon5\Users\guest\MagicFill |
Opera Software\Opera Stable Opera Software\Opera Neon Opera Software\Opera Crypto Developer Opera Software\Opera GX Stable Elements Browser CatalinaGroup\Citrio Fenrir Inc\Sleipnir5\setting\modules\ChromiumViewer QIP Surf Liebao Coowon\Coowon MapleStudio\ChromePlus Rafotech\Mustang Suhba TorBro\Profile RockMelt Bromium Twinkstar CCleaner Browser AcWebBrowserr CoolNovo SRWare Iron Mozilla\Firefox AVG\Browser Thunderbird Blisk 8pecxstudios\Cyberfonx SwingBrowser Mozilla\IceCat SalamWeb FlashPeak\SlimBrowser Kinza |
- HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{53F49750-6209-4FBF-9CA8-7A333C87D1ED}_is1
- HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{C4A4AE8F-B9F7-4CC7-8A6C-BF7EEE87ACA5}_is1
The registry paths mentioned above contain crucial details such as display names, versions, UninstallString, and other pertinent data.
Additional Clients Targeted
- Steam client
- Discord
- Password manager applications
- Two-factor authentication (2FA)
- Cryptocurrency wallet extensions
The stealer extracts ID details of password manager applications, 2FA, and cryptocurrency wallet extensions. These are of particular interest as they can contain valuable information and may have vulnerabilities that the attacker can exploit to gain unauthorized access to user accounts.
Steam client
The stealer retrieves Steam client data by reading the registry key "HKCU\SOFTWARE\Valve\Steam.” Steam is a digital distribution platform created by Valve Corporation, primarily used for video games. This registry key stores user-specific settings, game information, login data, session information, and other configuration data associated with the Steam client.
Discord
The stealer accesses the Discord folder and retrieves the configuration and other relevant details, such as:
- Discord
- DiscordCanary
- DiscordPTB
- Lightcord
- DiscordDevelopment
Extension ID
The malware attempts to extract the ID details of password manager applications, two-factor authentication (2FA) and cryptocurrency wallet extensions from web browsers.
Furthermore, the malware specifically focuses on extracting data from extensions related to 2FA and password managers. These extensions can store crucial information and may have vulnerabilities. By obtaining access to 2FA codes or exploiting weaknesses in password manager extensions, attackers can bypass security measures and gain unauthorized entry to user accounts.
Extension IDs of password managers and 2FA:
| Password Managers and Authentication Name | Extension ID |
| Authenticator 2FA Authenticator 2FA Trezor Password Manager GAuth Authenticator EOS Authenticator 1Password 1Password KeePassXC KeePassXC Dashlane Password Manager Dashlane Password Manager Bitwarden Password Manager Bitwarden Password Manager NordPass Keeper Password Manager RoboForm RoboForm LastPass LastPass BrowserPass MYKI MYKI Splikity CommonKey SSO Authenticator Zoho Vault Authy |
bhghoamapcdpbohphigoooaddinpkbai ocglkepbibnalbgmbachknglpdipeoio imloifkgjagghnncjkhggdhalmcnfklk ilgcnhelpchnceeipipijaljkblbcobl oeljdldpnmdbchonielidgobddffflal aeblfdkhhhdcdjpifhhbdiojplfjncoa dppgmdbiimibapkepcbdbmkaabgiofem oboonakemofpalcgghocfoadofidjkkk pdffhmdngciaglkoonimfcmckehcpafo fdjamakpfbbddfjaooikfcpapjohcfmg gehmmocbbkpblljhkekmfhjpfbkclbph nngceckbapebfimnlniiiahkandclblb jbkfoedolllekgbhcbcoahefnbanhhlh fooolghllnmhmmndgjiamiiodkpenpbb bfogiafebfohielmmehodmfbbebbbpei pnlccmojcmeohlpggmfnbbiapkmbliob ljfpcifpgbbchoddpjefaipoiigpdmag hdokiejnpimakedhajhdlcegeplioahd bbcinlkgjjkejfdpemiealijmmooekmp naepdomgkenhinolocfifgehidddafch bmikpgodpkclnkgmnpphehdgcimmided nofkfblpeailgignhkbnapbephdnmbmn jhfjfclepacoldmjmkmdlmganfaalklb chgfefjpcobfbnpmiokfjjaglahmnded nhhldecdfagpbfggphklkaeiocfnaafm igkpcodhieompeloncfnbekccinhapdb gaedmjdfmmahhbjefcbgaolhhanlaolb |
Crypto wallet extensions
The malware attempts to extract cryptocurrency wallet extensions from web browsers via software plugins or add-ons that enable users to conveniently manage their cryptocurrency assets directly within web browsers like Chrome or Firefox. These extensions provide functionality for tasks such as monitoring account balances, conducting cryptocurrency transactions details.
The following table shows Extension IDs of crypto wallets:
| Cryptocurrency wallet Name | Extension ID |
| MetaMask MetaMask MetaMask Binance Wallet BitApp Wallet Coin98 Wallet SafePal Wallet SafePal Wallet DAppPlay Guarda EQUA Wallet GuildWallet Casper Wallet Unknown wallet ICONex Math Wallet Math Wallet MOBOX WALLET Phantom TronLink XDCPay Ton Sollet Slope DuinoCoin Wallet Starcoin Hiro Wallet MetaWallet Swash Finnie Keplr Crocobit Wallet Oxygen Nifty Wallet Liquality Ronin Wallet Ronin Wallet Oasis Temple Pontem Aptos Wallet Solflare Wallet Yoroi iWallet Wombat – Gaming Wallet for Ethereum & EOS Coinbase Wallet MEW CX Jaxx Liberty OneKey Hycon Lite Client SubWallet or Polkadot Goby TezBox ONTO Wallet Hashpack Cyano Martian Wallet for Sui & Aptos Sender Wallet Zecrey Auro Terra Station KardiaChain Rabby Wallet NeoLine Nabox XDEFI KHC OneKey CLW Polymesh ZilPay Byone Eternl Unknown wallet Nami Maiar DeFi Wallet LeafWallet Brave Wallet Opera Wallet CWallet Flint Wallet Exodus Web3 Wallet Trust Wallet Crypto Airdrops & Bounties |
nkbihfbeogaeaoehlefnkodbefgpgknn ejbalbakoplchlghecdalmeeeajnimhm djclckkglechooblngghdinmeemkbgci fhbohimaelbohpjbbldcngcnapndodjp fihkakfobkmkjojpchpfgcmhfjnmnfpi aeachknmefphepccionboohckonoeemg lgmpcpglpngdoalbgeoldeajfclnhafa apenkfbbpmhihehmihndmmcdanacolnh lodccjjbdhfakaekdiahmedfbieldgik hpglfhgfnhbgpjdenjgmdgoeiappafln blnieiiffboillknjnepogjhkgnoapac nanjmdknhkinifnkgdcggcfnhdaammmj abkahkcbhngaebpcgfmhkoioedceoigp dfmbcapkkeejcpmfhpnglndfkgmalhik flpiciilemghbmfalicajoolhkkenfel afbcbjpbpfadlkmhmclhkeeodmamcflc dfeccadlilpndjjohbjdblepmjeahlmm fcckkdbjnoikooededlapcalpionmalo bfnaelmomeimhlpmgjnjophhpkkoljpa ibnejdfjmmkpcnlpebklmnkoeoihofec bocpokimicclpaiekenaeelehdjllofo nphplpgoakhhjchkkhmiggakijnkhfnd fhmfendgdocmcbmfikdcogofphimnkno pocmplpaccanhmnllbbkpgfliimjljgo ippiokklhjjdlmmonmjimgbgnnllcleg mfhbebgoclkghebffdldpobeajmbecfk ldinpeekobnhjjdofggfgjlcehhmanlj bkklifkecemccedpkhcebagjpehhabfb cmndjbecilbocjfkibfbifhngkdmjgog cjmkndjhnagcfbpiemnkdpomccnjblmj dmkamcknogkgcdfhhbddcghachkejeap pnlfjmlcjdjgkddecgincndfgegkecke fhilaheimglignddkjgofkcbgekhenbh jbdaocneiiinmjbjlgalhcelgbejmnid kpfopkelmapcoipemfendmdcghnegimn fnjhmkhhmkbjkkabndcnnogagogbneec kjmoohlgokccodicjjfebfomlbljgfhk ppdadbejkmjnefldpcdjhnkpbjkikoip ookjlbkiijinhpmnjffcofjonbfbgaoc phkbamefinggmakgklpkljjmgibohnba bhhhlbepdkbapadjdnnojkbgioiodbic ffnbelfdoeiohenkjibnmadjiehjhajb kncchdigobghenbbaddojjnnaogfppfj amkmjjmmflddogmhpjloimipbofnfjih hnfanknocfeofbddgcijnmhnfnkdnaad nlbmnnijcnlegkjjpcfjclmcfggfefdm cjelfplplebdjjenllpjcblmjkfcffne jnmbobjmhlngoefaiojfljckilhhlhcj bcopgchhojmggmffilplmbdicgaihlkp onhogfjeacnfoofkfgppdlbmlmnplgbn jnkelfanjkeadonecabehalmbgpfodjm mnfifefkajgofkcjkemidiaecocnkjeh ifckdpamphokdglkkdomedpdegcjhjdp gjagmgiddbbciopjhllkdnddhcglnemk dkdedlpgdmmkkfjabffeganieamfklkm efbglgofoippbgcjepnhiblaibcnclgk epapihdplajcdnnkdeiahlgigofloibg ojbpcbinjmochkhelkflddfnmcceomdi cnmamaachppnkjgnildpdmkaakejnhae aiifbnbfobpmeekipheeijimdpnlpgpp pdadjkfkgcafgbceimcpbkalnfnepbnk acmacodkjbdgmoleebolmdjonilkdbch cphhlgmgameodnhkjdmkpanlelnlohao nknhiehlklippafakaeklbeglecifhad hmeobnfnfcmdkdcmlblgagmfpfboieaf hcflpincpppdclinealmandijcmnkbgn jnmbobjmhlngoefaiojfljckilhhlhcj nhnkbkgjikgcigadomkphalanndcapjk jojhfeoedkpkglbfimdfabpdfjaoolaf klnaejjgbibmhlephnhpmaofohgkpgkd nlgbhdfgdhgbiamfdfmbikcdghidoadd kmhcihpebfmpgmihbkipmjlmmioameka acdamagkdfmpkclpoglgnbddngblgibo lpfcbjknijpeeillifnkikgncikgfhdo dngmlblcodfobpdpecaadgfbcggfjfnm cihmoadaighcejopammfbmddcmdekcje odbfpeeihdkbihmopkbjmoonfanlbfcl gojhcdgcpbpfigcaejpfhfegekdgiblk apnehcjmnengpnmccpaibjmhhoadaico hnhobjmcibchnmglfbldbfabcgaknlkj aholpfdialjgjfhomihkjbmgjidlcdno egjidjbpglichdcondbcbdnbeeppgdph dhgnlgphgchebgoemcjekedjjbifijid |
- HKCU\SOFTWARE\Etherdyne\Etherwall\geth
- HKCU\SOFTWARE\monero-project\monero-core
- HKCU\SOFTWARE\DogecoinCore\DogecoinCore-Qt
- HKCU\SOFTWARE\BitcoinCore\BitcoinCore-Qt
- HKCU\SOFTWARE\LitecoinCore\LitecoinCore-Qt
- HKCU\SOFTWARE\DashCore\DashCore-Qt
After gathering stolen data, it attempts to establish a connection with a socket and utilizes a send handle to transmit the data to the attacker's server.
Prevention and detection
The importance of timely detection and proactive prevention of threats such as the Meduza Stealer is crucial. Here at Uptycs, our aim is to equip you with the knowledge and resources needed to keep your systems secure and resilient against evolving cyber threats.
Defensive measures
To defend against malware attacks like the Meduza Stealer, it is recommended to:
- Regularly install updates for your operating system, browsers, and installed applications to patch vulnerabilities that malware can exploit.
- Be cautious when downloading files or opening email attachments, especially from unknown sources. Scan files using security software before opening them.
- Employ strong and unique passwords for all your accounts, including browsers, email, and cryptocurrency wallets. Consider using a password manager to securely store and manage your passwords.
- Enable 2FA wherever possible to add an extra layer of security to your accounts. This helps protect against unauthorized access, even if passwords are compromised.
- Only install browser extensions from trusted sources. Regularly review and remove unnecessary or suspicious extensions to minimize the risk of malware interference.
- Keep a close eye on your financial accounts, including cryptocurrency wallets, and regularly review transaction history for any suspicious activities. Report any unauthorized transactions or security breaches immediately.
Uptycs XDR Detection
Uptycs extended detection and response (XDR) customers can easily scan for Meduza Stealer since Uptycs XDR is armed with YARA process scanning and advanced detections. Additionally, Uptycs XDR contextual detection provides important details about the identified malware.Users can navigate to the toolkit data section in a detection alert, then click the name of a detected item to reveal its profile. (Fig. 9).
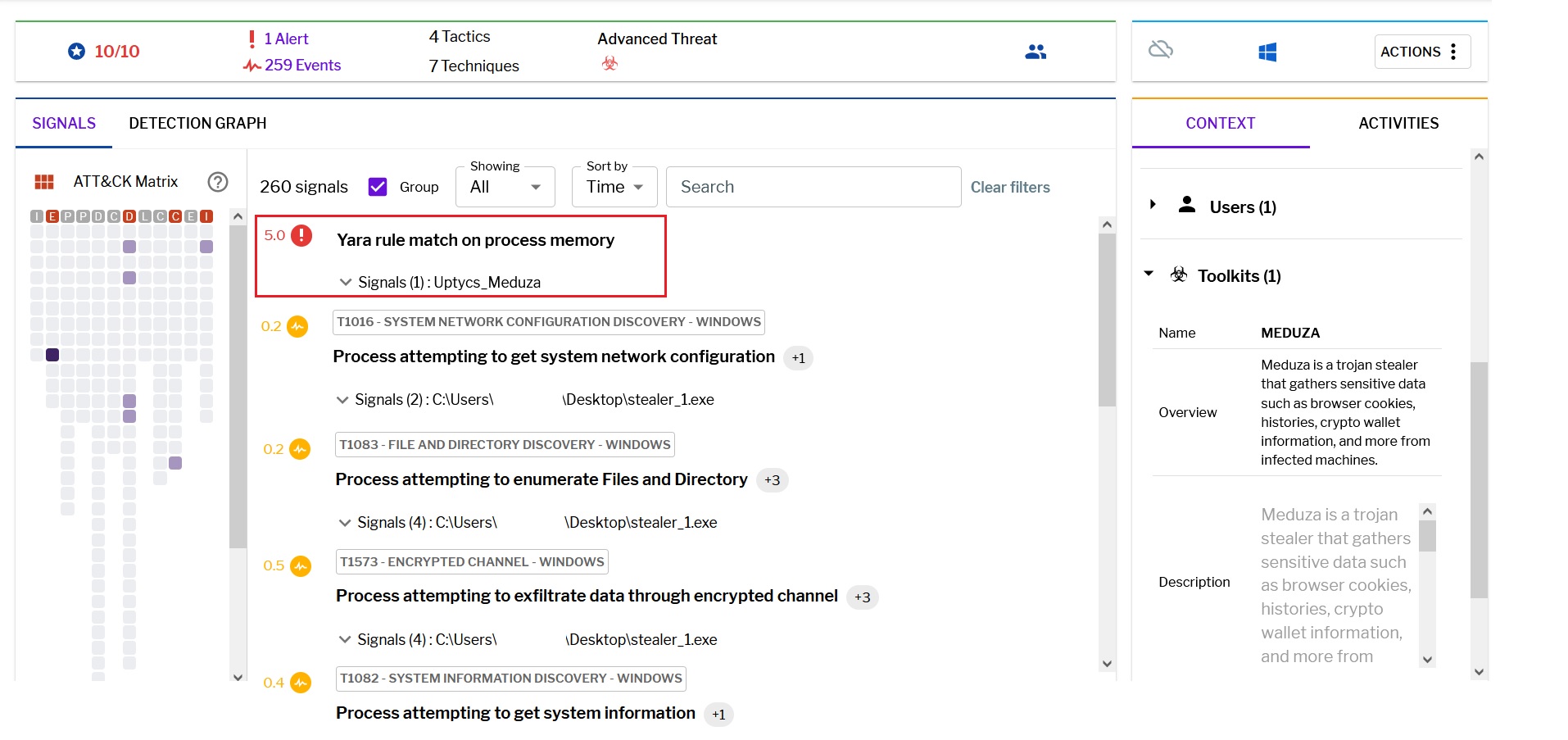
Fig.9 – Uptycs XDR detection
Meduza YARA detection rule
Uptycs XDR scans the memory of newly launched processes and detects any presence of suspicious strings by utilizing YARA rules. The YARA rule for detecting this malware has already been made available to our customers.
rule Uptycs_Meduza
{
meta:
malware_name = "Meduza"
description = "Meduza is a trojan stealer that gathers sensitive data such as browser cookies, histories, crypto wallet information, and more from infected machines."
author = "Uptycs Inc"
version = "1"
strings:
$string_1 = "autofill-profiles.json" ascii wide
$string_2 = "formhistory.sqlite" ascii wide
$string_3 = "logins.json" ascii wide
$string_4 = "cookies.sqlite" ascii wide
$string_5 = "key4.db" ascii wide
$string_6 = "Electrum\\config" ascii wide
$string_7 = "Sparrow\\wallets" ascii wide
$string_8 = "Coinomi\\wallets" ascii wide
$string_9 = "Electrum-LTC\\wallets" ascii wide
$string_10 = "Mozilla\\SeaMonkey" ascii wide
$string_11 = "Yandex\\YandexBrowser" ascii wide
$string_12 = "BrowserPass" ascii wide
condition:
all of them
}
IOC
| File name | MD5 |
| Stealer Stealer |
45f0b444f8de5bf28ffc312212935284 8058b771b506f0ac785b55e6e16e012e |
URL
By analyzing the VirusTotal graph, we were able to identify Meduza stealer samples spreading in recent days. According to a VirusTotal analysis report, the Meduza Stealer malware components are seen to be communicating with a server located in Germany (Fig. 10).

Fig.10 – Virustotal graph






.png?width=352&name=%23iamroot%20(1).png)
