Research by: Shilpesh Trivedi and Tejaswini Sandapolla
The Uptycs Threat Research Team has discovered a new infostealer. Spread by multiple bundlers and new on cybercrime forums, HookSpoofer has keylogging and clipper abilities. (A bundler combines two or more files in a single package.) It sends its stolen data to a Telegram bot.
Uptycs threat research has determined that while it includes enhanced features, HookSpoofer is coded in C# and is inspired by StormKitty, an open source program found on GitHub.
Infection Vector
HookSpoofer is spread by bundlers (MD5: de90466d983da595e863339c34ee4b6b) named “Spotify proxyless checker 2022.rar.” It contains 17 files, with the main executable (the HookSpoofer stealer) being circulated as Spotify checker.exe.
HookSpoofer Infection Flow
.png?width=3307&height=1873&name=Figure1%20(1).png)
Figure 1 - Hookspoofer infection flow
Technical Analysis
The analyzed program has an md5 hash: 7FCE055A581C0B116A9679291BF89B7D. It’s .NET compiled and packed by Confuser, a .NET obfuscator.
.png?width=1258&height=498&name=Figure2%20(1).png)
Figure 2 - Array initialization
Looking at the file contents, a large chunk of data is stored in the variable array that is later decrypted and stored in array2.
.png?width=1015&height=822&name=Figure3%20(1).png)
Figure 3 - Decryption loop
The decrypt function then decrypts the long array2 object (fig. 3). The result is a GCHandle object; its content creates a “koi” module, after which one of its methods is invoked.
.png?width=1506&height=475&name=Figure4%20(1).png)
Figure 4 - Code for Memory Loading of decrypted .Net Module
The figure 4 decryption logic is also related to Confuser. After decryption another .NET-compiled PE file is packed by Confuserex v1.0.0. Figure 4 shows how the “koi” module is loaded internally to the main stub.exe file inside memory.
After the module is loaded into the memory, there is a call to invoke a fake error message, (fig. 5) stored as a string in the “koi” module. This is done to divert the victim as the “koi” module performs its activity in the background.
.png?width=512&height=220&name=Figure5%20(1).png)
Figure 5 - Fake error message
Figure 6 shows how the error message is invoked:
.png?width=1905&height=558&name=Figure6%20(1).png)
Figure 6 - Code showing the error message
Here’s an in-depth look into the “koi” module (md5: BD4345C3A7CC6F6E261986E1F5F1E8BC). As it’s packed by Confuserex, to ease our analysis we’ve removed the obfuscation to obtain an unpacked file (md5: 474E0CD6BC1F0FB71BBFFA1AE7DD8E66).
After the error message appears, the code creates a mutex, then checks if the file is in the Startup subfolder (it sets file attributes to Hidden if not there). The malware then checks for a hardcoded, obfuscated Telegram API and Telegram ID (as follows). If they’re not found it deletes itself, after which dependent DLLs (DotNetZip.dll and AnonFileApi.dll) are downloaded from the following locations:
hxxps://raw.githubusercontent.com/LimerBoy/StormKitty/master/StormKitty/stub/packages/DotNetZip.1.13.8/lib/net40/DotNetZip.dlhxxps://raw.githubusercontent.com/LimerBoy/StormKitty/master/StormKitty/stub/packages/AnonFileApi.1.14.6/lib/net40/AnonFileApi.dll
respectively..png?width=1121&height=746&name=Figure7%20(1).png)
Figure 7 - Self deletion code
Figure 8 shows string_2 and string_3 that are hardcoded, obfuscated Telegram API and Telegram ID.
.png?width=1232&height=93&name=Figure8%20(1).png)
Figure 8 - Obfuscated Telegram API and ID
To deobfuscate the Telegram API and Telegram ID, the CRYPTED keyword is removed, base64 decoded, then the base 64 decoded hex bytes form an array that undergoes AES 256 decryption. It uses the same key and salt.
Key: {104,116,116,112,115,58,47,47,103,105,116,104,117,98,46,99,111,109,47,76,105,109,101,114,66,111,121,47,83,116,111,114,109,75,105,116,116,121}
After decryption; it forms:
hxxps://api[.]telegram.org/bot6122846074:AAF6rJZMCIphpMPrSWQdU2PZSf14u6p4zeA/
.png?width=1592&height=291&name=Figure9%20(1).png)
Figure 9 - Deobfuscated Telegram API and ID
Anti-Analysis Techniques
Various anti-analysis techniques are used to detect VirtualBox, SandBox, Debugger, VirusTotal, and Any.Run.
Debugger Checks
It checks if the sample is running inside a debugger via CheckRemoteDebuggerPresent.
Process Checks
It checks if processes (used by reverse engineers) such as process hacker, netstat, tcpview, and regmon are present. If detected, the program stops its execution.

Figure 10 - Checks if the processes are running inside victims machine
Sandbox Checks
It checks for sandbox-related DLL files (e.g., SbieDll) are running.

Figure 11 - Checks if the sandbox dll’s are present
Virtualization Checks
It uses the wmi query, "Select * from Win32_ComputerSystem" to check for vmware/VIRTUALBOX/Virtual, et al.
root\\CIMV2", "SELECT * FROM Win32_VideoController" to check vmware/vbox

Figure 12 - Virtualization check
Hosting Checks
Checks the system IP address and compares with IP addresses associated with sandbox environments such as VirusTotal, anyRun etc.
If any of the above are detected then it creates a log of below strings in %temp% and sends a fake error message with exit code showing runtime error.

Figure 13 - Anti Analysis detected
Figure 14 shows this error message:

Figure 14 - Fake error message check
Stealing Capabilities
It tries to steal the following data:
- ProtonVPN, OpenVPN, NordVPN
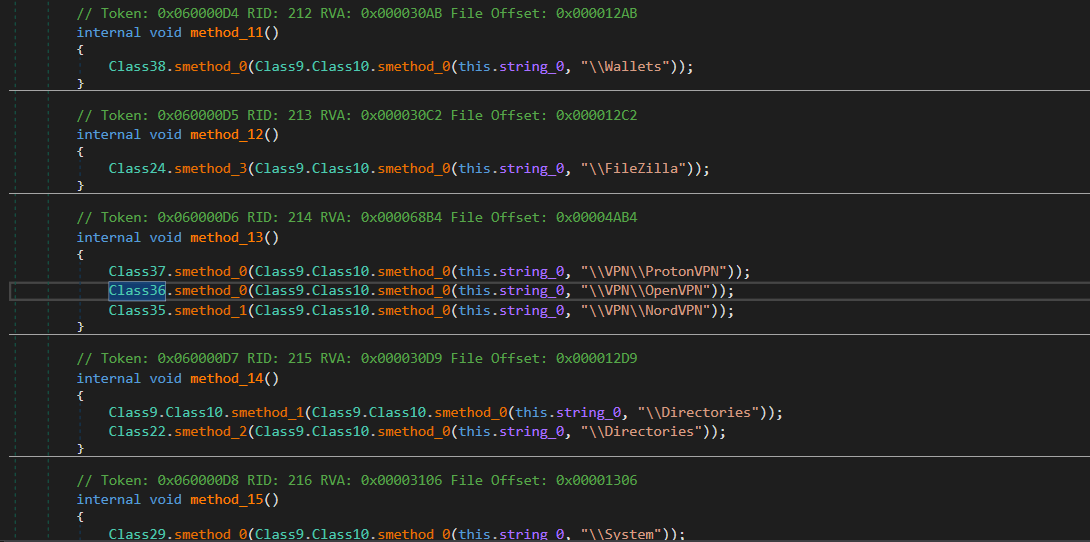
Figure 15 - VPN Stealer
- Filezilla steals data from “recentservers.xml” and “sitemanager.xml”

Figure 16 - Filezilla Hosts
- Information about processes running on the system, including process name, PID, path

Figure 17 - Info of the running processes
- Captures desktop screenshots

Figure 18 - Desktop screenshot
- Uses the netsh wlan show profile command via cmd.exe to obtain info related to saved Wi-Fi modules and passwords along with scan networks around device (SSID, BSSID)

Figure 19 - Wifi Passwords
- File Grabber
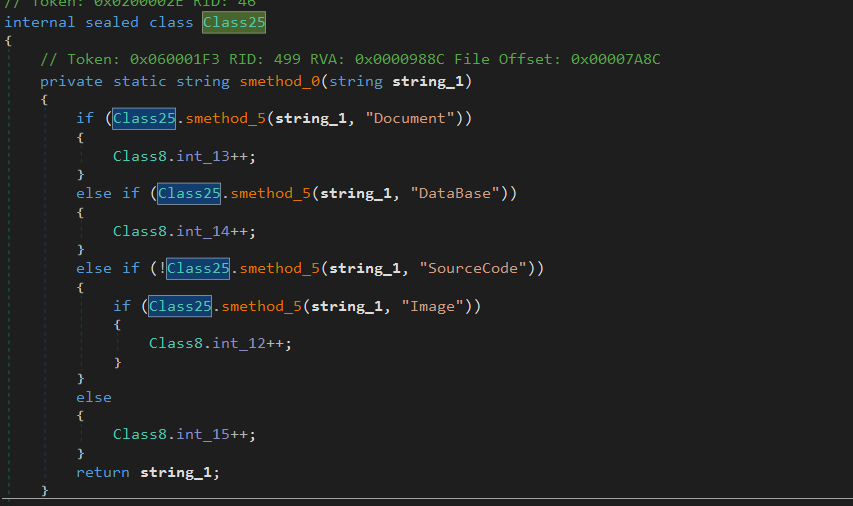
Figure 20 - File grabber
- Firefox.IE, Opera, and Edge browser history, cookies, login data, credit cards, et al.

Figure 21 - Edge web data, cookies, history, etc.
- Messengers (Telegram, Discord, Pidgin, Outlook and Skype)

Figure 22 - Telegram and Skype stealer
- Steam, Uplay, Battle.Net, Minecraft session gaming
- Cryptocurrency wallets
- Directories structure using filesystem info
- Webcam screenshot

Figure 23 - Webcam screenshot
- Product key
- Card info
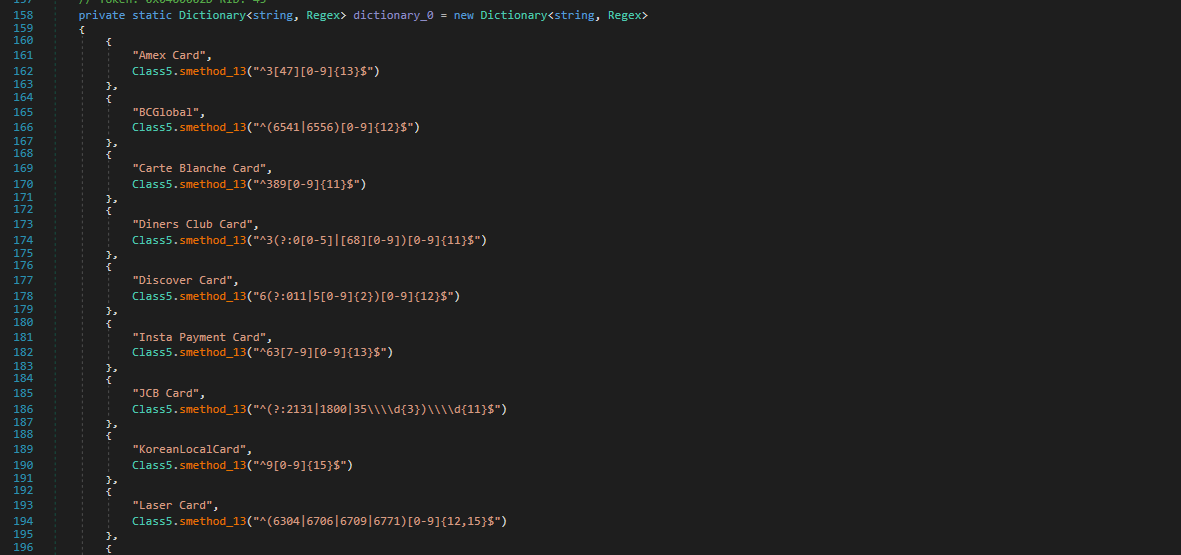
Figure 24 - Card info
- Keylogger

Figure 25 - Keylogger
- System info

Figure 26 - Systeminfo
- Clipper
Stores all %AppData% folder info with the name <md5 of string concat current timedatestamp, username, comp name, culture name, CPU name, GPU name>.
All collected data is again archived in a password protected Zip file having the password <md5 of string concat current timedate, username, comp name, culture name, CPU name, GPU name>.
Zip File
The Zip file is uploaded on anonfile.com/<message_id>, where the message ID is processed by the Telegram bot. This link is sent to the Telegram bot shown above.

Figure 27 - Anon file link

Figure 28 - Info if the report has been sent to telegram or not
Figure 29 shows the complete report being sent with the title “HookSpoofer.”

Figure 29 - Report contents
StormKitty Similarities
Uptycs has discovered that the “HookSpoofer” code is inspired from open source StormKitty with a few enhanced features (e.g., error code popup, memory loading). Misuse of open source stealers has become common, with StormKitty code being observed earlier in Typhon, WorldWind stealer, and Prynt Stealer malware. Figure 30 shows their common generated report format.

Figure 30 - Similarity
Conclusion
Stealer bundlers can spread through various channels, including email attachments, fake software downloads, and social engineering techniques. To defend against malware attacks like Hookspoofer, Uptycs recommends:
- Users should keep their operating system and security software up to date and avoid downloading files or clicking links from unknown sources.
- Businesses should ensure that all staff receive cybersecurity training, and implement measures such as two-factor authentication and data encryption to protect against data theft.
Uptycs EDR Detection
In addition to having YARA built-in, Uptycs EDR customers can easily scan for HookSpoofer since our tool is armed with other advanced detection capabilities. EDR contextual detection provides important details about identified malware. Users can navigate to the toolkit data section in the detection alert, then click on the name of a detected item to reveal its profile (fig. 31).

Figure 31 - Uptycs EDR detection
IOC
|
File name |
SHA1 hash |
|
Bundler |
de90466d983da595e863339c34ee4b6b |
|
Packed Hookspoofer |
7fce055a581c0b116a9679291bf89b7d |
|
Unpacked Hookspoofer |
474e0cd6bc1f0fb71bbffa1ae7dd8e66 |







