The United States Cybersecurity and Infrastructure Security Agency (CISA) has ordered U.S. federal agencies to patch systems by June 23 against a security flaw in the Progress MOVEit Transfer managed file transfer (MFT) solution currently being exploited.
The advisory comes on the heels of a third critical vulnerability identified by Progress Software in less than a month. The latest CVE-2023-35708 vulnerability is a SQL injection breach that might permit an unauthenticated user to escalate privileges and access the database. All the MOVEit Transfer versions released before 2020.1.6 (special patch also need to be applied), 2021.0.8 (13.0.8), 2021.1.6 (13.1.6), 2022.0.6 (14.0.6), 2022.1.7 (14.1.7), and 2023.0.3 (15.0.3) and versions 2020.0.x (12.0) or older are vulnerable.
A SQL injection vulnerability is a security flaw that allows unauthorized individuals to manipulate a website or application's database. This vulnerability occurs when user input is not properly validated or sanitized, allowing an attacker to insert malicious SQL code into input fields.
MOVEit Active Exploits
A ransomware group known as Cl0P (or CLOP) recently used the vulnerabilities in the software to attack hundreds of organizations, including universities, banks, and major multinational corporations.
Multiple federal agencies, including two Department of Energy entities, reported last week they had been victimized by the attack, along with state government agencies.
CL0P claimed on its dark website to have “information on hundreds of companies” as part of its attack. The group also said that if the victim organization was “a government, city or police service do not worry, we erased all your data. You do not need to contact us. We have no interest to expose such information.”
Uptycs Analysis of MOVEit Vulnerability CVE-2023-34362
MOVEit Transfer is a file transfer software that allows organizations to securely exchange files with external parties. On Jun 1, 2023 Progress released a security advisory on the critical SQL Injection Vulnerability in MOVEit Transfer software. The vulnerability is tracked as CVE-2023-34362 and carries a severity level of Critical.
This vulnerability is being actively exploited by Cl0P ransomware group. The attack involves deploying a web shell human2.aspx which establishes a database connection using credentials provided in the SystemSettings.DatabaseSettings() method. It checks for a specific header value (X-siLock-Comment) and compares it with a hardcoded value. If the values don't match, it returns a 404 response, indicating access is denied. If the header value matches, it continues executing and sets additional headers. Depending on the value of instid (a request header), it performs different operations:
- If instid equals -1, it executes several database queries to retrieve data related to files, folders, and institutions. The resulting data is then formatted and written to the response, which is compressed using gzip before being sent.
- If instid equals -2, it executes a database query to delete a user from the users' table based on a specific condition.
- For any other value of instid, it handles file retrieval and download. It decrypts a file specified by file id from a specified folder, compresses it using gzip, and sends it as a downloadable response.
It's important to note that this web shell code snippet is likely part of a larger attack or exploitation scenario. The presence of such a web shell on a server indicates a significant security breach and should be addressed immediately to prevent further unauthorized access and potential harm.
Note: It’s not necessary for the name to be “human2.aspx”
OS: Windows
Vulnerable Versions: MOVEit Transfer versions prior to 2020.1.6(special patch also need to be applied), 2021.0.6 (13.0.6), 2021.1.4 (13.1.4), 2022.0.4 (14.0.4), 2022.1.5 (14.1.5), and 2023.0.1 (15.0.1) and versions 2020.0.x or older are vulnerable.
Uptycs Query to Retrieve Vulnerable Hosts/Images:
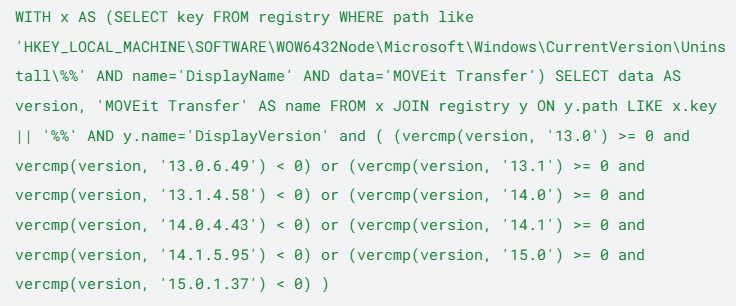
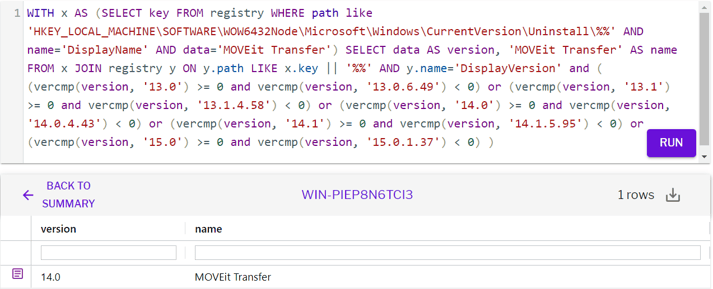
Query to determine the vulnerable software
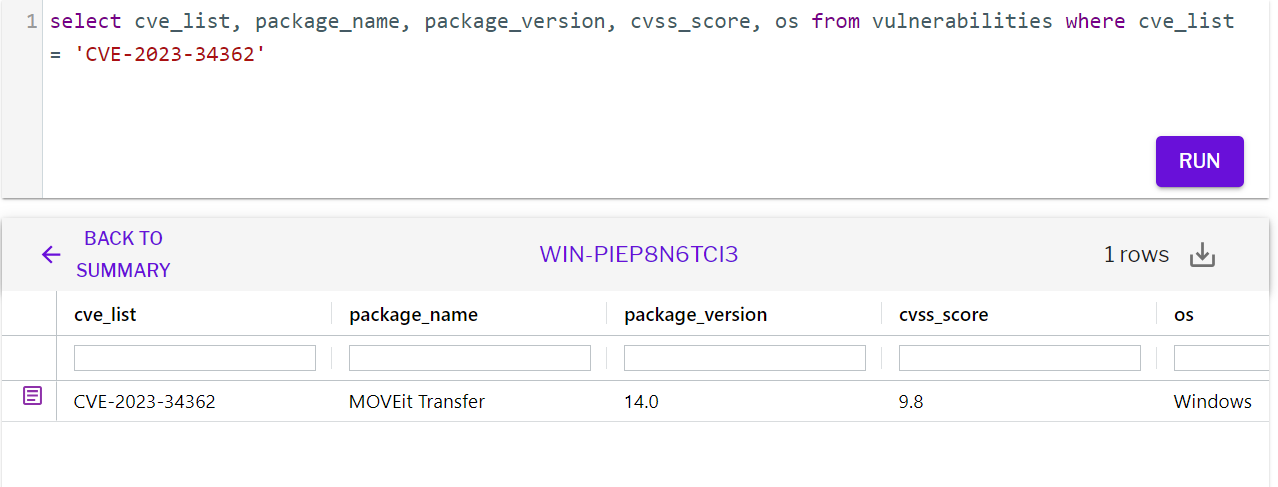
Detection through vulnerability scan
Uptycs Analysis of CVE-2023-35036
A security issue known as SQL Injection is currently ongoing in older versions of MOVEit Transfer. The vulnerability is tracked as CVE-2023-35036. The affected versions are released before 2020.1.6(special patch also need to be applied), 2021.0.7 (13.0.7), 2021.1.5 (13.1.5), 2022.0.5 (14.0.5), 2022.1.6 (14.1.6), and 2023.0.2 (15.0.2) and versions 2020.0.x or older. This vulnerability allows an unauthorized attacker who doesn't have proper authentication to gain access to the MOVEit Transfer database without permission.
By sending a specially crafted malicious payload to certain parts of the MOVEit Transfer web application, the attacker can manipulate and access the content stored in the MOVEit database. To address this issue, patches have been developed and are available for the supported versions.
There are two options to fix this vulnerability:
- DLL Drop-In: Download the patch from the advisory page and replace existing files with the files present in the patch.
- Upgrade to the latest version: Progress has also released the new version of MOVEit Transfer which addresses this vulnerability.
OS: Windows
MOVEit Transfer versions released before 2020.1.6(special patch also need to be applied), 2021.0.7 (13.0.7), 2021.1.5 (13.1.5), 2022.0.5 (14.0.5), 2022.1.6 (14.1.6), and 2023.0.2 (15.0.2) and versions 2020.0.x or older.
CVSSv3 Score: 9.1
Advisory link: MOVEit Transfer Advisory
Uptycs Query to Retrieve Vulnerable Hosts/Images:
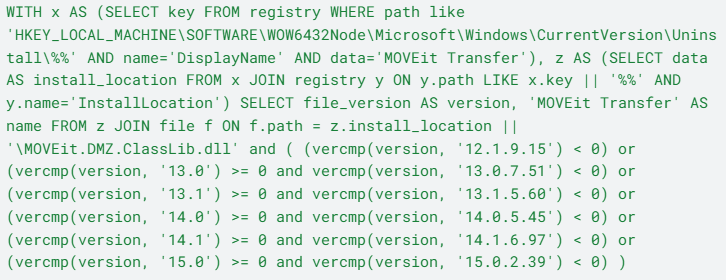
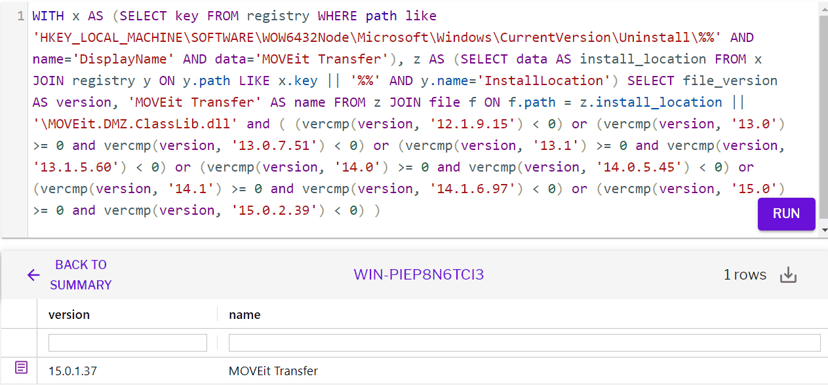
Query to determine the vulnerable software
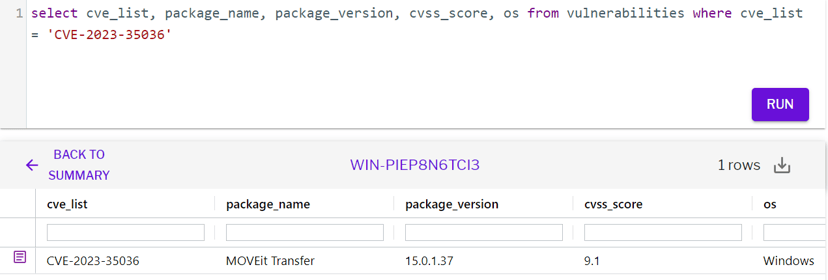
Detection through vulnerability scan
Uptycs Analysis of CVE-2023-35708
On June 15, Progress Software disclosed a new SQL injection vulnerability in its MOVEit Transfer application, which could potentially result in unauthorized access and escalated privileges.
The vulnerability is tracked as CVE-2023-35708. Progress Software advises customers to disable all HTTP and HTTPS traffic on ports 80 and 443 for MOVEit Transfer as mitigation. The affected versions are released before 2020.1.6(special patch also need to be applied), 2021.0.8 (13.0.8), 2021.1.6 (13.1.6), 2022.0.6 (14.0.6), 2022.1.7 (14.1.7), and 2023.0.3 (15.0.3) and versions 2020.0.x (12.0) or older.
There are two options to fix this vulnerability:
- DLL Drop-In: Download the patch from the advisory page and replace existing files with the files present in patch.
- Upgrade to latest version: Progress has also released the new version of MOVEit Transfer which addresses this vulnerability.
OS: Windows
Vulnerable Versions: MOVEit Transfer versions released before 2020.1.6(special patch also need to be applied), 2021.0.8 (13.0.8), 2021.1.6 (13.1.6), 2022.0.6 (14.0.6), 2022.1.7 (14.1.7), and 2023.0.3 (15.0.3) and versions 2020.0.x (12.0) or older.
CVSSv3 Score: 9.8
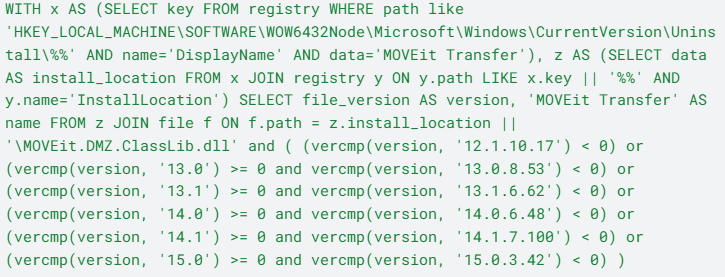
Query to determine the vulnerable software
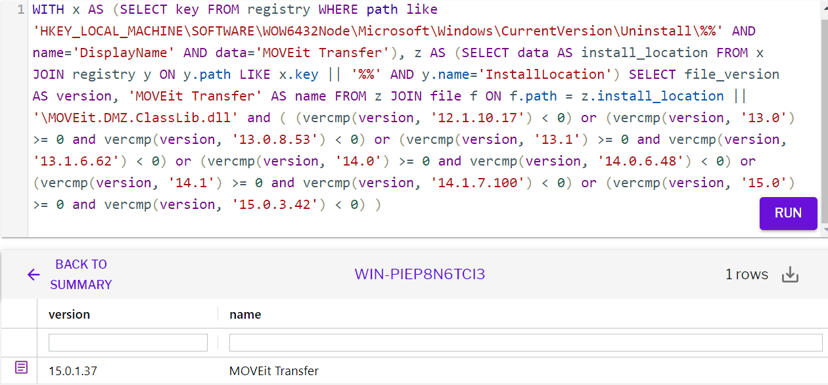
Query to determine the vulnerability software
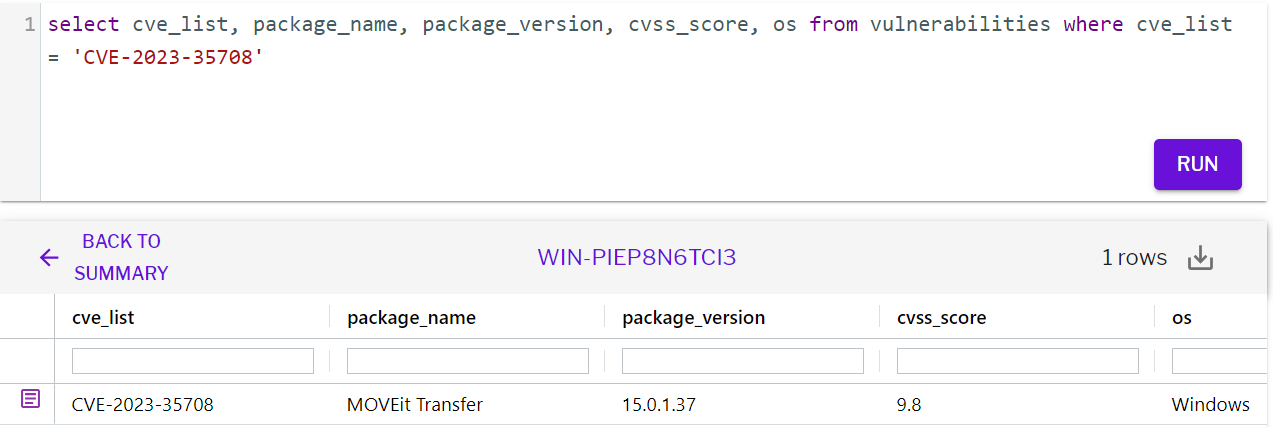 Detection through vulnerability scan
Detection through vulnerability scan







