Late last week cybersecurity company Red Canary published an article revealing a new strain of macOS malware they discovered. Looking at data provided by Malwarebytes they determined that this new malware, which they dubbed “Silver Sparrow,” had already infected nearly 30,000 macOS endpoints around the world.
There are a few important and unusual characteristics of this malware to highlight. First, it’s believed to be only the second piece of malware that’s been released into the wild with compatibility for Apple’s new ARM-based M1 chip.
This malware also is unique in its use of the macOS Installer JavaScript API to run its commands. It was delivered using normal Apple installer packages (.pkg files). Upon launching the package file the user is prompted to approve a dialog box stating that the package will run a program to determine software compatibility. This is not unusual as some software developers use this mechanism to legitimately check for compatibility prior to actual installation of their software. In this case, though, clicking on the “Continue” button within that dialog box will execute the JavaScript payload and install the malware onto the host system, regardless if the user cancels the installation immediately afterward.
The last unusual characteristic of this malware is it’s actual malicious payload; it seems to be missing. That’s right, this malware has spread to a large number of macOS endpoints, it has a novel installation vector, and broad compatibility on even the latest M1-based Macs. Yet the final malicious payload doesn’t seem to exist. The mechanism for downloading that payload is there though--it’s a script that checks in periodically to a remote host.
With all of these factors taken into account it’s no surprise that owners of macOS endpoints are looking for ways to detect this malware’s presence on their systems and remove it. Through our implementation of MITRE’s ATT&CK framework, Uptycs can detect the actions this malware takes as it installs itself onto a host. Specifically, the following alerts would trigger on an endpoint infected with Silver Sparrow.
- Suspicious use of sqlite3 to get the history of downloaded files from internet - T1082 Discovery for macOS
- Process created plist file LaunchAgents - T1543.001 Persistence for macOS
- Process created hidden mach-O file - T1543.001 Persistence for macOS
- Process using cp utility to create plist file in LaunchAgents - T1543.001 Persistence for macOS
- Detected use of curl utility to download file - T1105 Command and Control for macOS
- Suspicious use of curl utility to download plist file from internet - T1547.011 Persistence for macOS
These alerts will trigger on your macOS endpoints as long as they have the proper osquery flag file configuration in place. Here are the flags you need to make sure you have enabled for the above alerts:
disable_audit: falseaudit_allow_process_events: trueprocess_ancestor_list: trueancestor_list_max_entries: 20audit_allow_fim_events: trueoverride_audit_allow_fim_events: trueenable_fs_events_based_file_events: truefim_capture_magic_number_bytes: 10
If you don’t currently have the MITRE ATT&CK feature on your Uptycs account, reach out to your sales representative for further information.
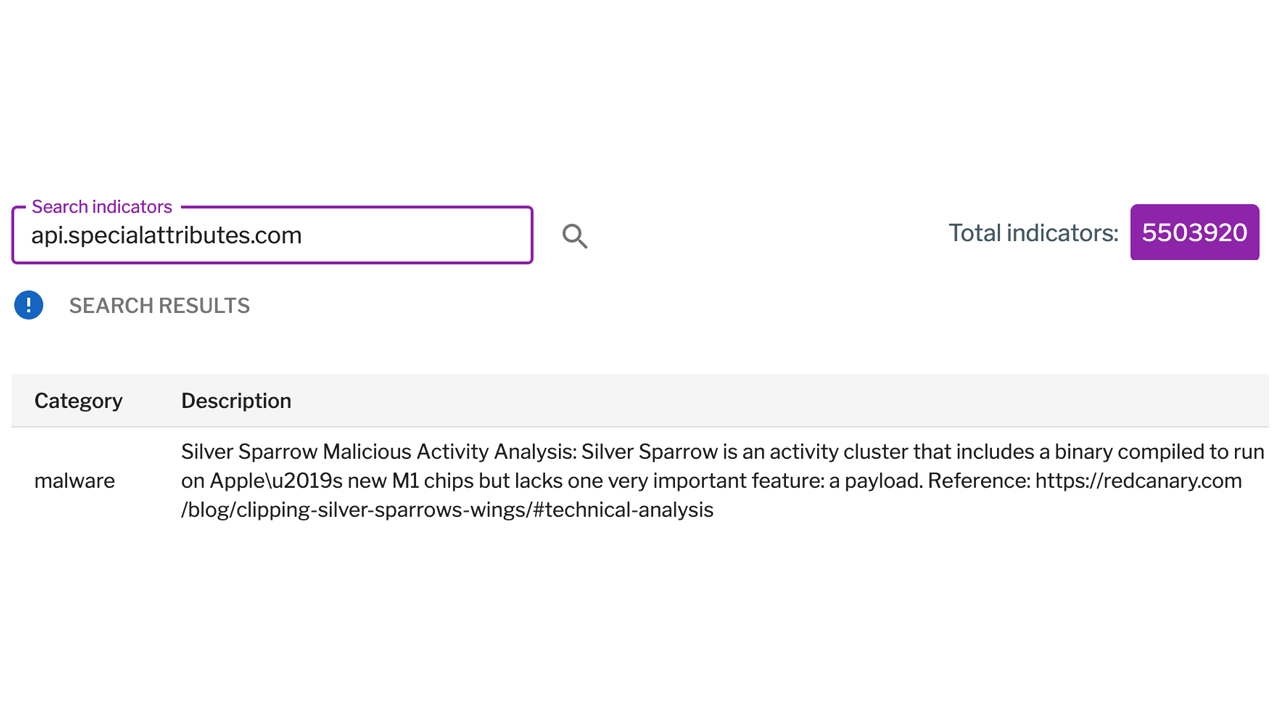
The Uptycs threat intelligence team has already added the Silver Sparrow IOCs within the Uptycs threat intelligence system. These will alert you when these IOCs are triggered.
Figure 1. Uptycs threat intelligence IOC for Silver Sparrow API server URL. (Click to see larger version.)
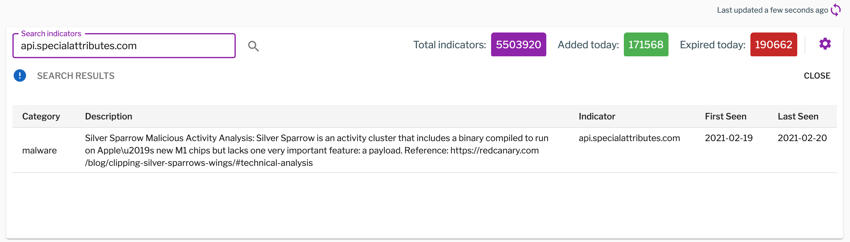
You’ll want to use an Uptycs Threat Book for historical searching across your endpoints. You can upload the following CSV Threat Book to your account and use it to scan your hosts for the IOCs of an existing Silver Sparrow infection (the CSV file can also be downloaded here). Thank you to Red Canary and Malwarebytes for the IOCs.
Figure 2. Uptycs Threat Books menu item. (Click to see larger version.)
| indicator | description | type |
| 30c9bc7d40454e501c358f77449071aa | v1 updater.pkg md5 | hash |
| c7dd06b20b64b64d3b155b6b77c2778a08ef6a6c0396d7537af411258e57af1e | v1 updater.pkg sha256 | hash |
| c668003c9c5b1689ba47a431512b03cc | v1 mach-o intel binary md5 | hash |
| c668003c9c5b1689ba47a431512b03cc | v1 mach-o intel binary md5 | hash |
| api.mobiletraits.com | v1 api c2 domain | dns |
| mobiletraits.s3.amazonaws.com | v1 s3 bucket for version.json | dns |
| fdd6fb2b1dfe07b0e57d4cbfef9c8149 | v2 update.pkg md5 | hash |
| 1decb4070db4dfe5d68ba502cf3a67de96a69ea6f3acfa4454795f96472ccc0d | v2 update.pkg sha256 | hash |
| b370191228fef82635e39a137be470af | v2 mach-o intel/m1 binary md5 | hash |
| api.specialattributes.com | v2 api c2 domain | dns |
| specialattributes.s3.amazonaws.com | v2 s3 bucket for version.json | dns |
Schedule a demo to learn more about the detection and investigation functionality in Uptycs.