Research by Ashwin Vamshi and Abhijit Mohanta
The Uptycs threat research team is monitoring ongoing targeted attacks and trends. We’ve recently seen threat actors and APT groups frequently using two document-based techniques: template injection and the Equation Editor exploit. In this piece, we’ll cover these oft-used techniques and provide details on the APT groups applying them.
Template Injection Technique
Microsoft’s Office specification permits embedding external or remote resources in documents. This feature allows a user to create a document with a template hosted on a local or remote machine. Adversaries apply this feature by injecting a malicious URL in the document to implement a template injection. Upon execution, the document attempts to open, download, and execute the malicious template.
This technique gives an added advantage to the attacker over anti-malware solutions and static analysis tools that rely on static detection. This technique of bypassing security controls by “living off the land” is described in the MITRE ATT&CK ID T1221. Using this technique, an attacker can easily launch next-stage payloads or even harvest credentials with toolkits like Phishery.
Equation Editor Exploit
Equation Editor (eqnedt32.exe) is an out-of-process COM server Microsoft module that allows for writing a mathematical equation into a document. As this is an out-of-process COM server, protections specific to any Microsoft Office application may not provide protection for commonly used vulnerabilities like CVE-2018-0798, CVE-2017-1182, and CVE-2018-0802 that date back to 2017-2018. Threat actors generally deploy an exploitable RTF document to execute the malicious payload. This technique belongs to the exploitation for client execution described in the MITRE ATT&CK ID T1203.
Next we’ll cover details of recent targeted attacks and the threat actors using these techniques.
Threat Group: TinyScouts
Technique: Template injection via a DOCX file that downloads a DOTM template.
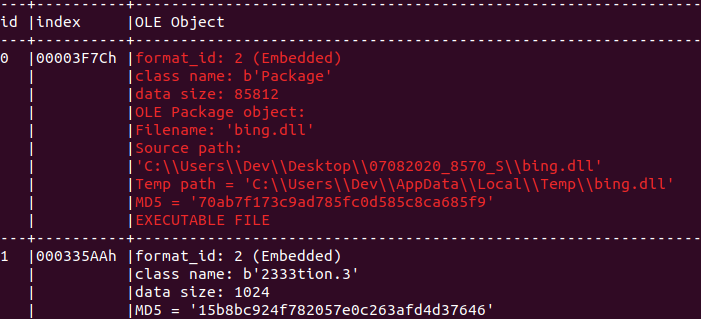
Our threat intelligence systems detected a document titled “Счет на оплату АКИТ - 53557.docx.” This translates to “Account for payment AKIT - 53557.docx.” (Hash: 36d335d96db7cccf84a732afa8b264fa72443aa8ba31445d20879882b783513b.) This document is related to the TinyScouts group that targets members of the Russian Union of Industrialists and Entrepreneurs with ransomware and password stealers.
The same document was delivered via three different bit.ly links that redirect to Cloudflare worker URLs (workers.dev) hosting the document:
https://bit[.]ly/36Dtpcl → https://shiny-meadow-ce6e.xena[.]workers[.]dev/6754345654
https://bit[.]ly/3oI5nmY → https://restless-shadow-3c21[.]xena.workers[.]dev/543
https://bit[.]ly/2O2G1n7 → https://curly-wind-45ba.xena[.]workers[.]dev/345678765
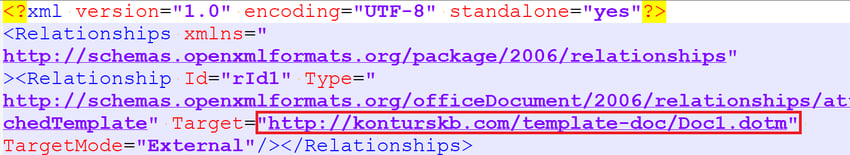
This document is in Microsoft’s Office Open XML (OOXML) format. It contains the malicious DOTM template URL present in word\_rels\settings.xml.rels (see Figure 1, below).
Figure 1: DOTM malicious template. (Click to see larger version.)
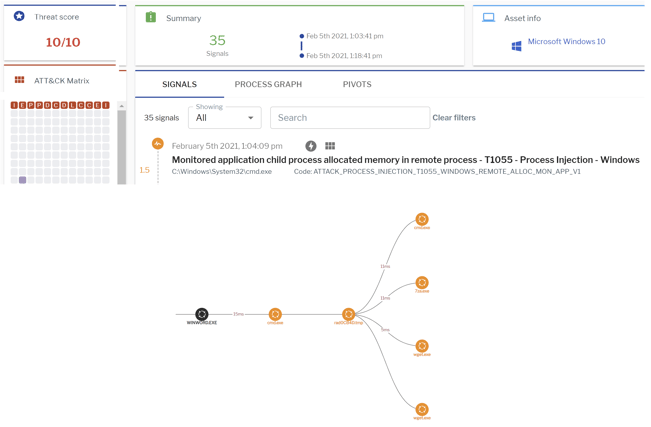
Upon execution, the document opens the malicious DOTM file downloaded from konturskb[.]com, as shown in Figure 2, below.
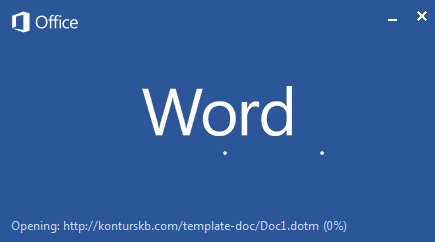
Figure 2: Document opening the downloaded malicious DOTM template.
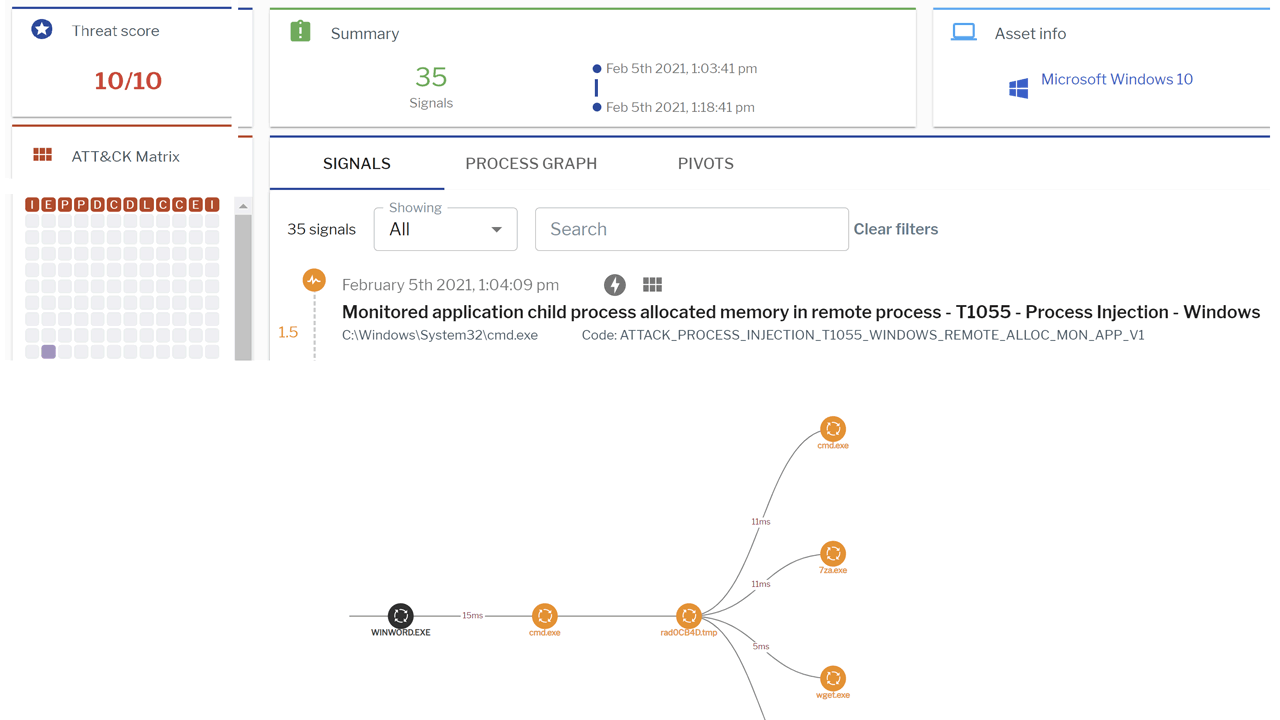
Uptycs’ EDR capabilities detected this attack with a threat score of 10/10 (Figure 3).
Figure 3: Uptycs EDR detection of the TinyScouts group kill chain. (Click to see larger version.)
Threat Group: Gamaredon
Technique: Template injection via a DOC file downloading a DOT template.
Another template injection document is titled “План служби по РзГТОТ на 2021 рік (з внес. правками Т.Р.).doc” (this translates to “Service plan for RzGTOT for 2021 (as amended by TR).doc.” (Hash: 156d440b1b6c8ea39d961b4ad6c942d0b4d33dacbd2702c3711d5f1ca0831833.) This document is related to the Gamaredon group, also known as Primitive Bear or Operation Armageddon, that uses multiple implants to carry out surveillance on people in the Ukrainian government.
Unlike the previous example, the Gamaredon document contains the malicious DOT template URL present in the 1Table element, as shown Figure 4, below.
Figure 4: DOT malicious template. (Click to see larger version.)
The document also contains four pages. This would have skipped the eye of static heuristic engines because these engines generally scan suspicious files based on the number of pages (malicious documents are usually one page).
Upon execution, the document opens the malicious DOT file downloaded from asilidae[.]online (see Figure 5, below).
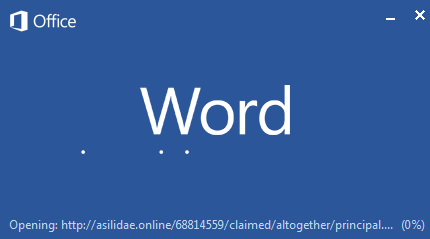
Figure 5: Document opening the downloaded DOT template.
At the time of analysis, the malicious DOT template was down and was not serving any content.
Threat Profile: GuLoader
Technique: Template injection via a DOCX file using a shortened link that downloads an RTF file with a DOC extension.
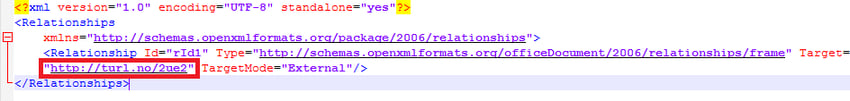
This template injection document is titled “SPPG-contract PO12403_PF01-0560-21_Korea Marine Service Power_Contract No 0560-19-01-2021.docx.” (Hash: 8465a0869d5b2998b2099ce04c72ccb2126aac34b4ed192b47caf36c55cdbda5.) The document is in Microsoft’s Office Open XML (OOXML) format. It contains a turl.no shortened link present in word/_rels/webSettings.xml.rels (see Figure 6).
Figure 6: URL shortener link. (Click to see larger version.)
This URL downloads an RTF file named “document.doc,” which downloads a Visual-Basic-based payload named GuLoader.
Threat Group: Confucius
Technique: Equation Editor exploit.
As noted in our previous post, Confucius (also known as Mo Luoxiu) is a threat actor/group primarily targeting government sectors in South Asia. It uses Warzone RAT as its stage payload. This threat group has used several decoys with template injection and an RTF-based Equation Editor exploit.
We have recently identified an RTF-based Equation Editor exploit used by this group (Figure 7).
Figure 7: Confucius Equation Editor document. (Click to see larger version.)
Here are the file details:
RTF hash: 8ecf1c276e10e3f3e9f7bc9e728fde9abea23348a2af6ce70269008d632a412d
C2: mlservices[.]online
DLL: 8b535452727edf06280c495b190c10eb0a90522fad1c61cae8bfeef9b84a4879
PDB path: C:\Users\admin\Documents\dll\linknew\Release\linknew.pdb
Other Attacks
Alongside this, we have observed the Lazarus threat actor group and several toolkits like Formbook, LokiBot, Agent Tesla, NanoCore RAT, Warzone RAT, and Remcos RAT frequently using these techniques in malicious documents.
We are continuing to see threat actors using malicious documents with the template injection attack and the Equation Editor exploit to download next-stage payloads. We expect these attacks to continue because they're successful in bypassing security controls and static scanners for a successful attack kill chain.
Enterprise users must be cautious opening documents from unknown or untrusted sources. Enterprise administrators and incident response teams must regularly monitor the suspicious processes, events, and network traffic spawned after executing these documents. Toward that end, the advanced analytics, threat intelligence, and granular visibility in Uptycs’ EDR capabilities can help organizations identify the artifacts, events, and toolkits in the attack kill chain of targeted attacks.
IOCs
Hashes
36d335d96db7cccf84a732afa8b264fa72443aa8ba31445d20879882b783513b
25ea03020243554dbfab6d5b4b3f70013e2f12734667975a203ce7a3108a480d
156d440b1b6c8ea39d961b4ad6c942d0b4d33dacbd2702c3711d5f1ca0831833
8465a0869d5b2998b2099ce04c72ccb2126aac34b4ed192b47caf36c55cdbda5
6398b747183908950d7d683b9731df7e11f81795111638d2b3918bd5000ddb04
8ecf1c276e10e3f3e9f7bc9e728fde9abea23348a2af6ce70269008d632a412d
8b535452727edf06280c495b190c10eb0a90522fad1c61cae8bfeef9b84a4879
URLs
https://shiny-meadow-ce6e.xena[.]workers[.]dev/6754345654
https://restless-shadow-3c21[.]xena.workers[.]dev/543
https://curly-wind-45ba.xena[.]workers[.]dev/345678765
http://konturskb[.]com/template-doc/Doc1.dotm
http://asilidae[.]online/68814559/claimed/altogether/principal.dot
turl[.]no/2ue2
mlservices[.]online