I’ve written before about how I feel open-source technology will prove disruptive in the security industry. Having recently returned from a week in San Francisco for B-Sides SF & RSA, which is known as the annual pilgrimage for "Infosec Sales," I feel that way now more than ever. The growth in adoption of open-source technologies may indicate that people are starting to get more comfortable with the concept or ability of their still being enough room for innovation that companies can charge for what they develop on top of “free” open-source projects. Coming back from the premier sales conference for the information security industry is a great showcase for why I’ve come away with that thought. Let's explore...
The big differentiator in open-source is the open part. That in and of itself is not any specific technical piece... but what does that lead to? Having an "open" project or tool leads to visibility, collaboration, and community. 
With the freedom that "open" allows taken to an additional level, you can get interoperability, and an entire different tier of community as projects interact and try to work together. Much as I have a bit of dread for RSA proper, the week in San Francisco let me see where a bunch of those things are taking us, and confirmed some of my "good" suspicions about what’s going on in the security industry.
At B-Sides, open-source software and open-ness were both still in full effect. Some that stood out: I saw a presentation by Jason Craig & Michael George at Dropbox about using open-source tools to secure their macOS environment (video | blogpost), citing my current favorite open-source security project, osquery, and other open tools and processes that are helping them greatly enhance the protection of their users. There were several presentations and numerous solutions involving containerization and automation of containers at both B-Sides and RSA, which were mainly inspired by the open-source roots of docker & kubernetes. I saw a great presentation by Maya Kaczorowski & Evan Johnson ( video | slides ) on managing secrets in the cloud, featuring both open-source solutions and sharing of information on problems we all face securing secrets in the cloud.
But at RSA, You're There to Sell, Right?
I mean, sure, I expected to see lots of open-source use cases at B-Sides, but RSA? You're there to sell, right? How do you make money off of "free" software? More and more, despite what you might get sold at some booths, the people building the next generations of solutions want to start with technologies that do not have proprietary lock-in when possible. Then, they're building on that software to deliver a value-add that people will happily pay for. Look at the growth of Docker, Aqua (and far too many others to list) that are building on the container ecosystem. Look at the push for interoperability in the SOAR space (more on that later). See that there are now about five companies building on top of osquery.
If the underlying fundamental core technology is open-source, it can be shaped by the community around it, and the rare organization with the wealth of resources and crack teams of engineers can build a fully "free" solution. However, those open-source building blocks are usually only the beginning to most security solutions -- requiring a wide variety of additional engineering work to scale and customize the solutions for a given customers needs. Even if all underlying software was open-source, the amount of work that needs to be done to make a universal technology work as part of a solution for all the different companies out there in the connected world is a never-ending font of work for businesses that can charge money. Thus open-source projects like osquery, kubernetes, docker, Zeek, and others are allowing for business opportunities and solution creation that would never have been possible in an all proprietary space.
Where should open-source be applied next?
A space that many vendors are touting that begs for “open” software is the Security Orchestration, Automation, and Response (SOAR) -- this has been a solid buzzword for the past year or two, with darlings in the space and news-making acquisitions each year. It's really just productizing what security folks have been doing for ages -- the need is just finally far out-stripping the demand. Don't have the staffing? Then replace the lower level slots with orchestration, and have your staff do the work after all the automated triage has been done. Sounds great, but even the quarter before RSA, Gartner was pointing out that many security products have limited APIs. Open projects where you can dig in and figure out what they are doing are going to beat an undocumented API in a black box for interoperability any day.
Another emerging idea that greatly benefits from "open" (both tools and techniques) is Zero Trust Networks. Though the concept has been around for a while, it has just recently been brought to life by Google's Beyond Corp project and is really only possible through the way that Google has been sharing information about their system over the years. This is not a trivial thing to implement. It is a foolish statement to glibly say "you can just do it with open source tools, Google did." Like with the other opportunities above, the "follow-on work" that has to be done to make the solution really work for a given customer is turning instead to provide a fertile market for both established companies like Duo and emerging companies like ScaleFT.
Moving beyond tool technology, open-source projects for security collaboration shone as well this year at RSA. Almost every third booth is now baselining their product coverage off of MITRE’s ATT&CK framework (which is an amazing piece of work -- if you haven’t checked it out yet, you owe it to yourself to do so), which is completely open-source & community driven. ATT&CK allows for a common reference of adversary life cycle that is far more useful and in depth than trying to backtrack from a “kill chain” or other defensive strategies. And in its (relatively) new home under the OASIS CTI TC, the STIX & TAXII standards are about to re-launch in revised, accessible versions. The evolution of STIX from what it originally was shows the power of the community to take a decent idea with really poor execution and turn it into something that can be used and actually implemented by developers with cool new features to help in sharing Cyber Threat Intelligence at machine speed.
So, is open-source disruptive?
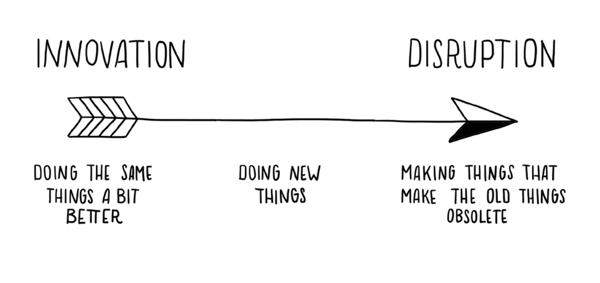 (this image is property of Leyla Acaroglu’s “Disruptive Design”)
(this image is property of Leyla Acaroglu’s “Disruptive Design”)
Looking back, is all this “disruptive?” In the sense that it is trashing the industry because someone has come up with something so radically different, no, not disruptive in that sense -- but that’s a good thing. Instead, open-source and openness seem to be disrupting in that they break an established status quo of iterations of the same thing every year and allow for forward progress. I’ll take that over the next “buzzword of the month” any day. I’d be willing to bet that out of the next round of startups “coming out of stealth” around Black Hat / DEFCON time frame, at least one of them will be building on top of an open-source project.






.png?width=352&name=451%20Report%20Blog_%20Featured%20Image%20(1).png)