A new Linux kernel vulnerability (CVE 2022-0847) has been discovered affecting Linux kernel versions since 5.8. This vulnerability allows the attacker to escalate privileges which can be further leveraged to perform elevated command/code execution. The vulnerability has been fixed in newer versions of the Linux kernel viz. 5.16.11, 5.15.25 and 5.10.102.
In this blog, we will cover the working of the exploit and also share the queries which security team members can use to identify vulnerable systems in their environment.
DirtyPipe Exploit Operation
A flow graph representation of the steps used by an attacker to trigger this vulnerability is shown below (See Figure 1).
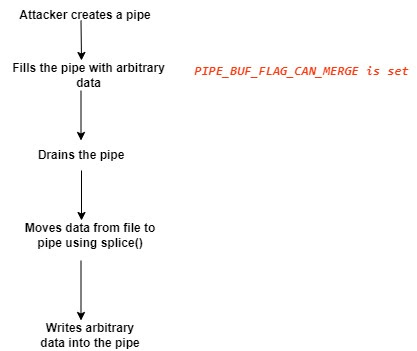
Figure 1: Exploitation steps
The exploitation starts with the creation of a pipe filled with arbitrary data. Upon draining the pipe, the flag PIPE_BUF_FLAG_CAN_MERGE remains set in all struct pipe_buffer instances. Then, using splice() system call, the page cache reference is added during which PIPE_BUF_FLAG_CAN_MERGE already remains set. At last, the arbitrary data gets written to the page cache. This way, the vulnerability allows the overwriting of the page cache even in the absence of writers at (almost) arbitrary positions with arbitrary data.
Notably, this exploit allows an attacker to overwrite any file's data in the page cache, even if the file is not permitted to be written, immutable or on a read-only mount.
We used a POC for demonstrating and triggering the vulnerability as shown below (See Figure 2)
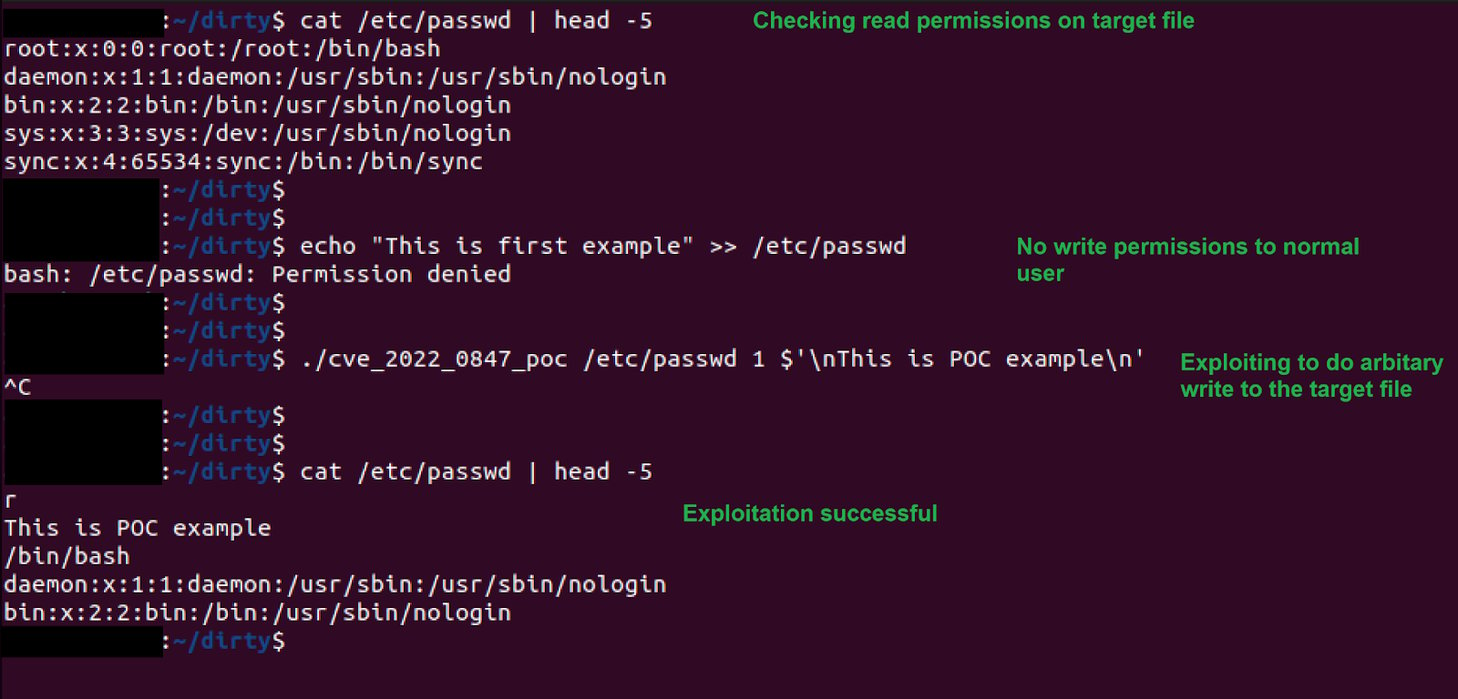
Figure 2: POC tested on /etc/passwd
We tested the POC on the /etc/passwd file present in Linux. The /etc/passwd file as shown above cannot be modified by a normal user. With the exploit we were successfully able to modify the passwd file.
Then, using the same POC, we tried to write arbitrary data in the read-only file present in the filesystem (/snap/firefox/1075/). After achieving this, we tried to write the same file with the exploit POC. The file was successfully modified (see Figure 3).
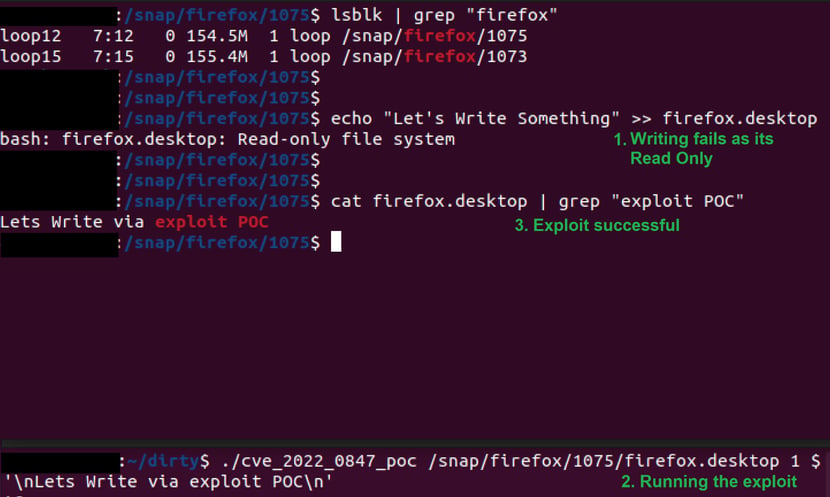
Figure 3: POC tested on Read-only filesystem
Uptycs Queries to Inventory Vulnerable Systems
The security analysts can use the following queries in Uptycs EDR to identify the systems vulnerable to CVE-2022-0847. For the open-source osquery, you can replace distinct(upt_hostname) with * if run manually on a single host machine. If anything but the empty set is returned then the machine is vulnerable.
Query for Linux systems using deb packages (Ubuntu, Debian, Linux Mint, and other derivatives)
select distinct(upt_hostname) from deb_packages where (name like '%linux-image%' and (version not like '%5.10.102%' and version not like '%5.15.25%' and version not like '%5.16.11%'));
Query for Linux systems using rpm packages (RHEL, CentOS, Fedora and other derivatives)
select distinct(upt_hostname) from rpm_packages where (name = 'kernel' and (version not like '%5.10.102%' and version not like '%5.15.25%' and version not like '%5.16.11%')) limit 1000;
At the time of this writing, we have not observed any malware family leveraging this bug. But this exploit could be used in many malware for privilege escalation. To mitigate the risk, the Uptycs threat research team recommends users to upgrade their Linux kernel versions to patched versions.







