Cloud Infrastructure Entitlements Management (CIEM)
Make zero trust in the cloud a reality
Implement least privilege, visualize identity relationships, and rapidly respond to security incidents and threats from the same platform you use to secure your cloud infrastructure.
Cloud identity and
entitlement analytics
Implement least privilege
Enhance your cloud security using Uptycs' cloud infrastructure entitlement management (CIEM) solution, offering real-time detection of identity misconfigurations, access request tracking, and support for least privilege implementation.
- Obtain detailed insight into cloud permissions and access
- Monitor requests and pinpoint potential access risks
- Simplify access management with a user-friendly dashboard
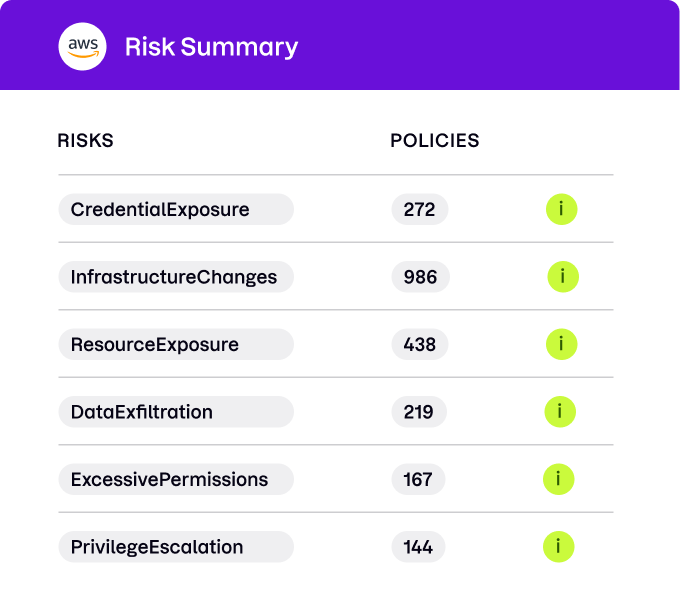
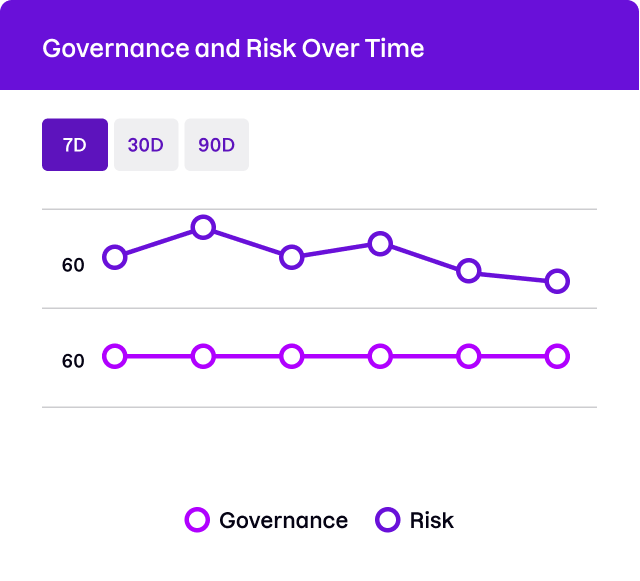
Measure identity risk posture
Uptycs evaluates the identity risk posture of your cloud accounts by analyzing cloud identity and access management (IAM) policies, considering factors such as credential rotation, potential privilege escalation, and credential exposure.
- Obtain actionable insights on identity risks and vulnerabilities
- Enhance cloud security and mitigate identity-related breaches
- Strengthen compliance posture and streamline auditing processes
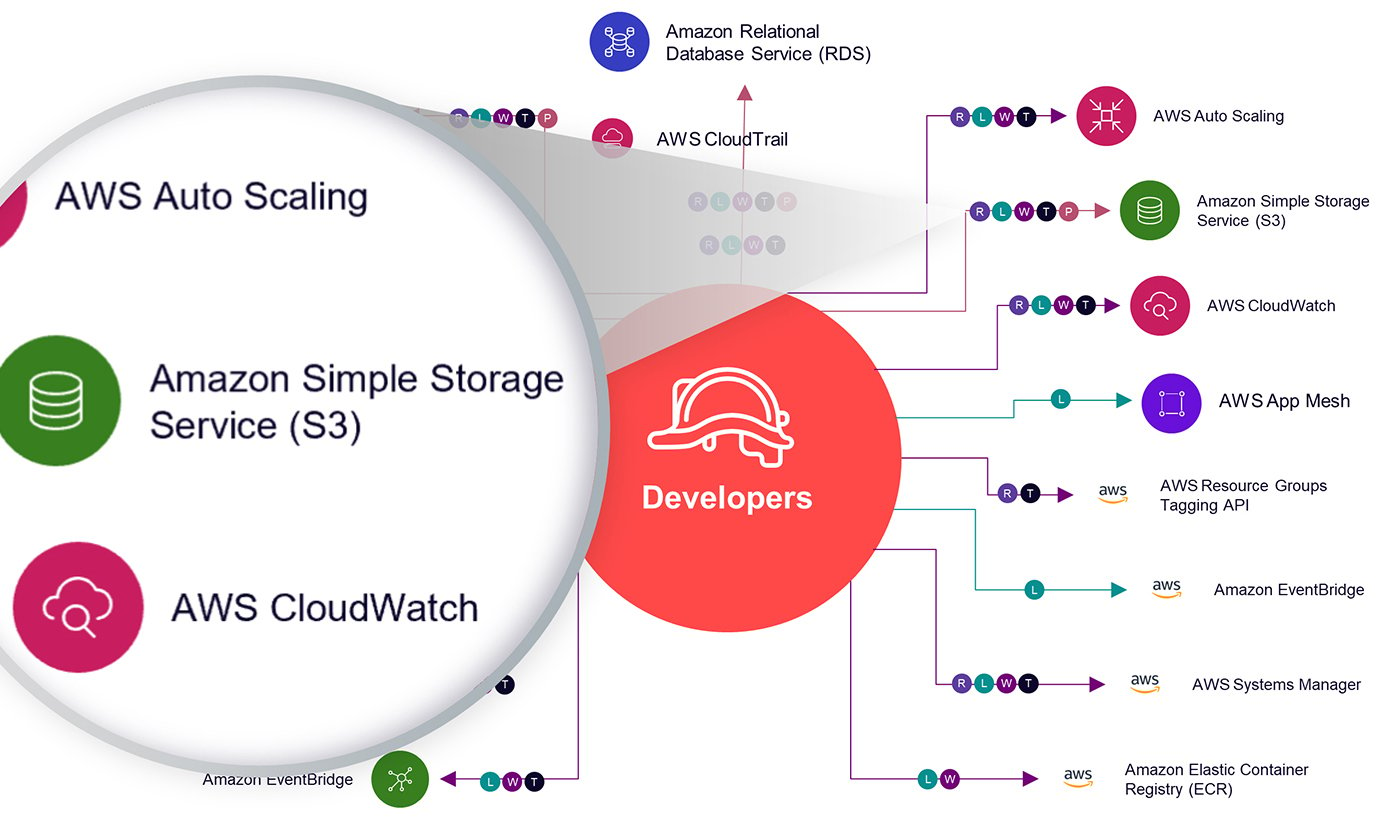
Map identities and relationships
Uptycs visually represents the relationships between resources, identities, and policies in an easily navigable graph, with filters that enable rapid querying and simplified answers.
- Quickly understand the implications of user or policy changes on your infrastructure
- Apply filters such as access level or resource type for more focused insights
- Expedite troubleshooting and incident response by rapidly identifying issue sources
Mitigate IAM-related cloud risks with Uptycs
According to Gartner®, “by 2023, 75% of security failures will result from inadequate management of identities, access, and privileges, up from 50% in 2020.”
Simplify cloud inventory
Amid increasing identity and access-related security failures, simplify your asset and resource inventory to prevent becoming a statistic.
Harden IAM policies
Uptycs continuously evaluates your IAM policies, generating risk profiles that enable you to focus on refining the highest-risk policies for enhanced security.
Lock down identities
Uptycs provides comprehensive analysis of your cloud identity activity, delivering insights into access decisions, unusual behavior, and more.
Why industry leaders
choose Uptycs
“Uptycs was deployed on a large scale as a key component of our security posture.”
Comcast
Vice President IT Security“We transitioned to Uptycs from an industry behemoth. We reduced costs, but more importantly, Uptycs' digs deeper for more impact.”
Computer & Network Security
Large Enterprise“Uptycs has been instrumental for our FedRamp authorization and ISO 27001 certification.”
Grant Kahn
Director, Security Engineering Lookout“Uptycs helps me sleep better at night.”
Sean Todd
CISO Pay Near Me“Uptycs contextualizes threat activity across K8s, cloud services, and laptops. We've dramatically shortened our threat investigation time.”
Anwar Reddick
Director of Information Security Greenlight Financial“Uptycs provides us with a comprehensive view of our environment without the need for log shipping or other data collection methods.”
Cloud Security Engineer
Top 10 Internet Site“I would not want to do security anywhere without this level of visibility.”
Steve Shedlock
Incident Response Team Lead SEI“Everything you want to know is as easy as querying a database. It’s fantastic.”
Security Engineer
E-learning Company“Product works great, is inexpensive, zero Dev complaints about slowing down systems (IYKYK), and they've added every feature I've asked for.”
Security Operations Manager
Business Services Company"Clean interface, very good visibility across assets, and their team is open to feedback."
Manager, Information Security
Finance Industry"A unified view from which we can quickly ask and answer security questions across our environment."
Chris Castaldo
CISO Crossbeam“A major game changer for heavily used hosts (40k requsts per second). Running safely within one of the largest cloud environments on the internet. ”
Uptycs Customer
"Uptycs simplifies investigations and saves time—about 30% per investigation.
Sean McElroy
CSO Lumin Digital“If threat actors try to evade detection Uptycs captures those events”
Security Engineer
Large Telecom Company“Blazingly fast. 0.7 seconds from execution to detection, and 1.6 seconds from execution to case management alert.”
Security Engineer
Global Payment ProcessorUptycs provides actionable runtime threat and vulnerability insights and a flexible threat hunting capability.
Uptycs Customer
Director, Information Security Financial“Monitoring containers for Exploit/Mining Activity can be easily traced compared to other apps”
Security Engineer
Telecom Company“For so many issues, our answer is ‘Go to Uptycs.’”
Director of Security Operations
Enterprise Logistics Company“Uptycs enables us to make risk-based decisions.”
Chris Castaldo
CISO, Crossbeam“We transitioned to Uptycs from an industry behemoth. We reduced costs, but more importantly, Uptycs' digs deeper for more impact.”
Computer & Network Security
Large Enterprise“Uptycs was deployed on a large scale as a key component of our security posture.”
Comcast
Vice President IT Security“We transitioned to Uptycs from an industry behemoth. We reduced costs, but more importantly, Uptycs' digs deeper for more impact.”
Computer & Network Security
Large Enterprise“Uptycs has been instrumental for our FedRamp authorization and ISO 27001 certification.”
Grant Kahn
Director, Security Engineering Lookout“Uptycs helps me sleep better at night.”
Sean Todd
CISO Pay Near Me“Uptycs contextualizes threat activity across K8s, cloud services, and laptops. We've dramatically shortened our threat investigation time.”
Anwar Reddick
Director of Information Security Greenlight Financial“Uptycs provides us with a comprehensive view of our environment without the need for log shipping or other data collection methods.”
Cloud Security Engineer
Top 10 Internet Site“I would not want to do security anywhere without this level of visibility.”
Steve Shedlock
Incident Response Team Lead SEI“Everything you want to know is as easy as querying a database. It’s fantastic.”
Security Engineer
E-learning Company“Product works great, is inexpensive, zero Dev complaints about slowing down systems (IYKYK), and they've added every feature I've asked for.”
Security Operations Manager
Business Services Company"Clean interface, very good visibility across assets, and their team is open to feedback."
Manager, Information Security
Finance Industry"A unified view from which we can quickly ask and answer security questions across our environment."
Chris Castaldo
CISO Crossbeam“A major game changer for heavily used hosts (40k requsts per second). Running safely within one of the largest cloud environments on the internet. ”
Uptycs Customer
"Uptycs simplifies investigations and saves time—about 30% per investigation.
Sean McElroy
CSO Lumin Digital“If threat actors try to evade detection Uptycs captures those events”
Security Engineer
Large Telecom Company“Blazingly fast. 0.7 seconds from execution to detection, and 1.6 seconds from execution to case management alert.”
Security Engineer
Global Payment ProcessorUptycs provides actionable runtime threat and vulnerability insights and a flexible threat hunting capability.
Uptycs Customer
Director, Information Security Financial“Monitoring containers for Exploit/Mining Activity can be easily traced compared to other apps”
Security Engineer
Telecom Company“For so many issues, our answer is ‘Go to Uptycs.’”
Director of Security Operations
Enterprise Logistics Company“Uptycs enables us to make risk-based decisions.”
Chris Castaldo
CISO, Crossbeam“We transitioned to Uptycs from an industry behemoth. We reduced costs, but more importantly, Uptycs' digs deeper for more impact.”
Computer & Network Security
Large EnterpriseResources for
the modern defender
Prepare for any challenges that lie ahead by choosing
the right tools today.
Gartner® CNAPP Market Guide
Cloud Identity Entitlement Analytics

ESG Report: Secure the Expanding Cloud-native Attack Surface

See Uptycs in action
Find and remove critical risks in your modern attack surface - cloud, containers, and endpoints - all from a single UI and data model. Let our team of experts show you how.
