Original research by Siddharth Sharma and Nischay Hegde
The Uptycs threat research team recently observed an advancement in the Black basta ransomware, where we saw that the ransomware binaries are now targeting ESXi servers. The Black Basta was first seen this year during the month of April, in which its variants targeted windows systems. This blog highlights the recent addition of the *nix component in the Black Basta ransomware by the ransomware authors.
Threat Attribution
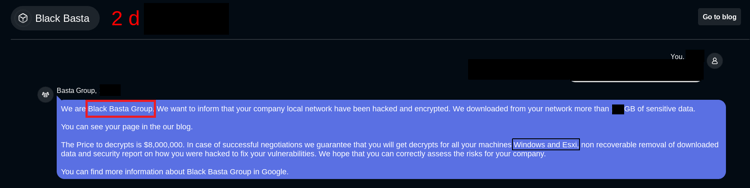
Based on the chat support link and encrypted file extension, we believe that the actors behind this campaign are the same who targeted windows systems earlier with the Black Basta ransomware.
Figure 1: Black basta chat support panel for negotiation
Technical Overview
The ransomware binary (hash: 0d6c3de5aebbbe85939d7588150edf7b7bdc712fceb6a83d79e65b6f79bfc2ef) looks for the /vmfs/volumes directory for encryption in the victim system. The /vmfs/volumes directory stores the virtual machines on the ESXi server. Once it finds the directory it starts encrypting files present inside the volumes folder.
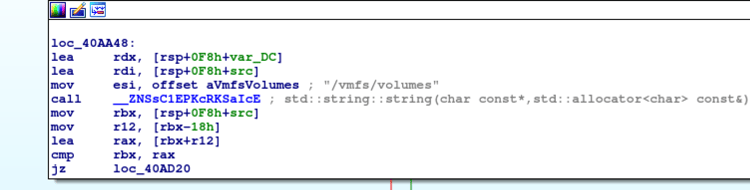
Figure 2: Ransomware binary looking for /vmfs/volumes folder
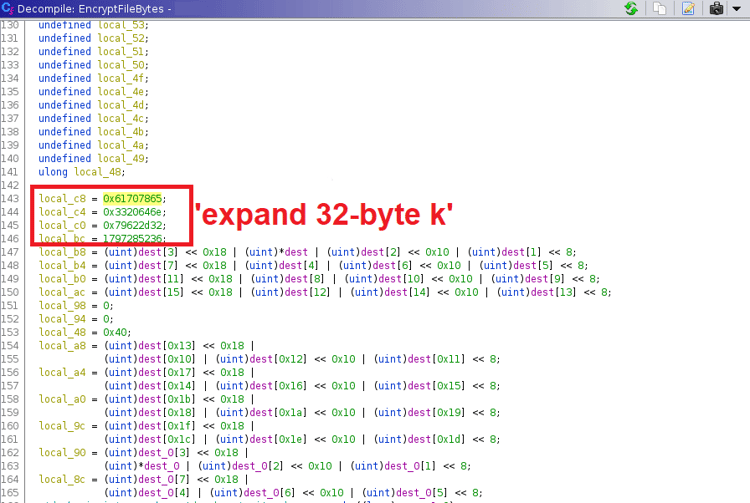
For encryption the ransomware author seems to be using the chacha20 algorithm as a part of the encryption mechanism, probably because chacha20 is fast.
Figure 3: chacha20 algorithm
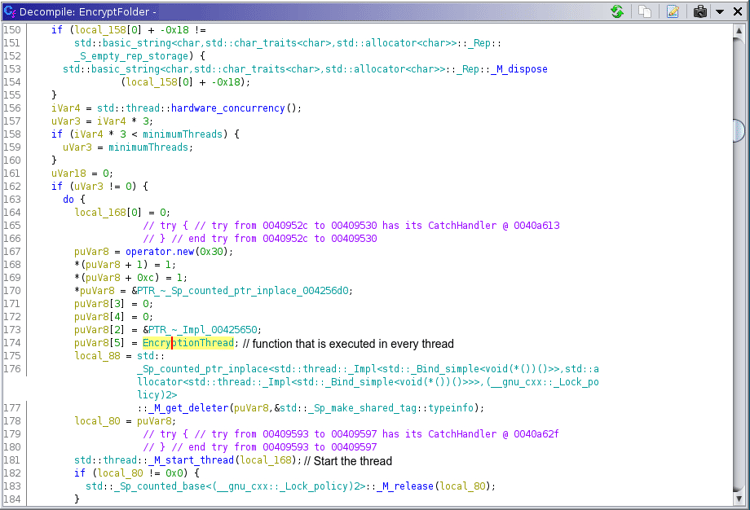
It also uses multithreading for encryption to utilize multiple processors and further make it faster and harder to detect. As shown in below figure(see figure: 4), the function `EncryptionThread` is run in parallel to increase throughput of the ransomware.
Figure 4: EncryptionThread usage
The ransomware binary also uses chmod utility for giving full permissions to the target files.(see figure 5)
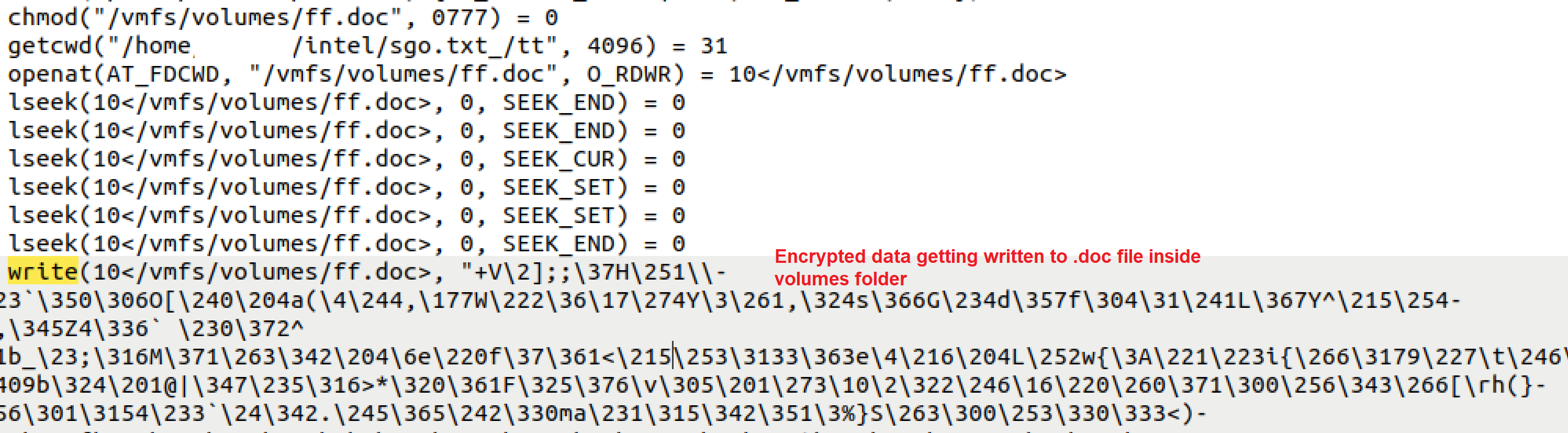
Figure 5: Malware binary writing encrypted content to files inside volumes folder
Below figure shows the encrypted files inside the volumes folder in the victim system. The extension used by the ransomware binary is .basta.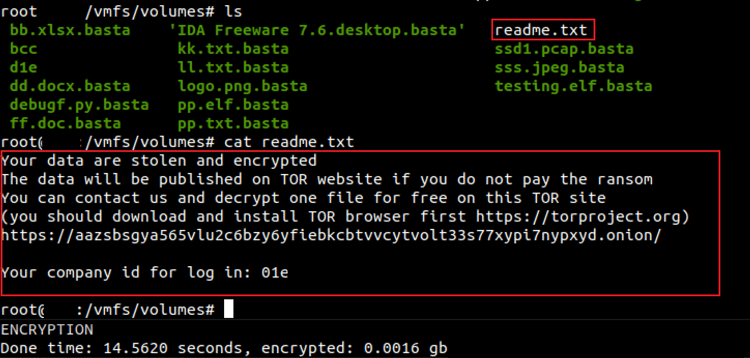
Figure 6: Encrypted files along with the readme file
Inside the readme.txt file, the author puts the link to the chat support panel where the victims can approach for file decryption.
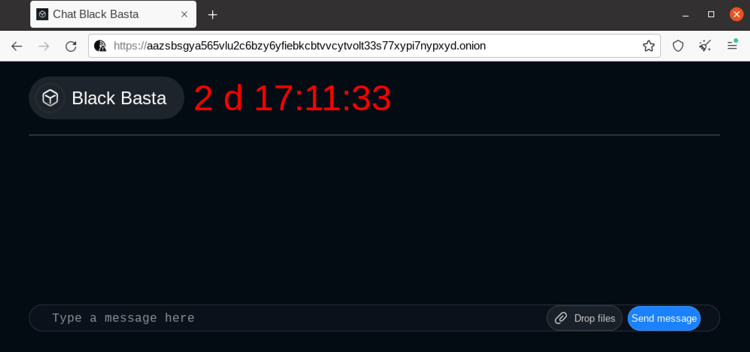
Figure 7: Black Basta panel for chat support
Uptycs EDR Detections
The Uptycs EDR armed with YARA process scanning detects the BlackBasta ransomware with a threat score of 10/10.(see figure 8)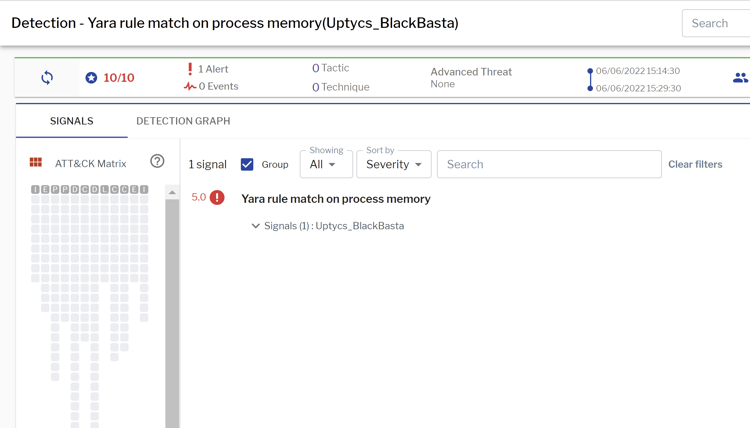
Figure 8: Uptycs EDR detection
IOCs
0d6c3de5aebbbe85939d7588150edf7b7bdc712fceb6a83d79e65b6f79bfc2ef
https[:]//aazsbsgya565vlu2c6bzy6yfiebkcbtvvcytvolt33s77xypi7nypxyd[.]onion