Research by: Siddharth Sharma and Nischay Hegde
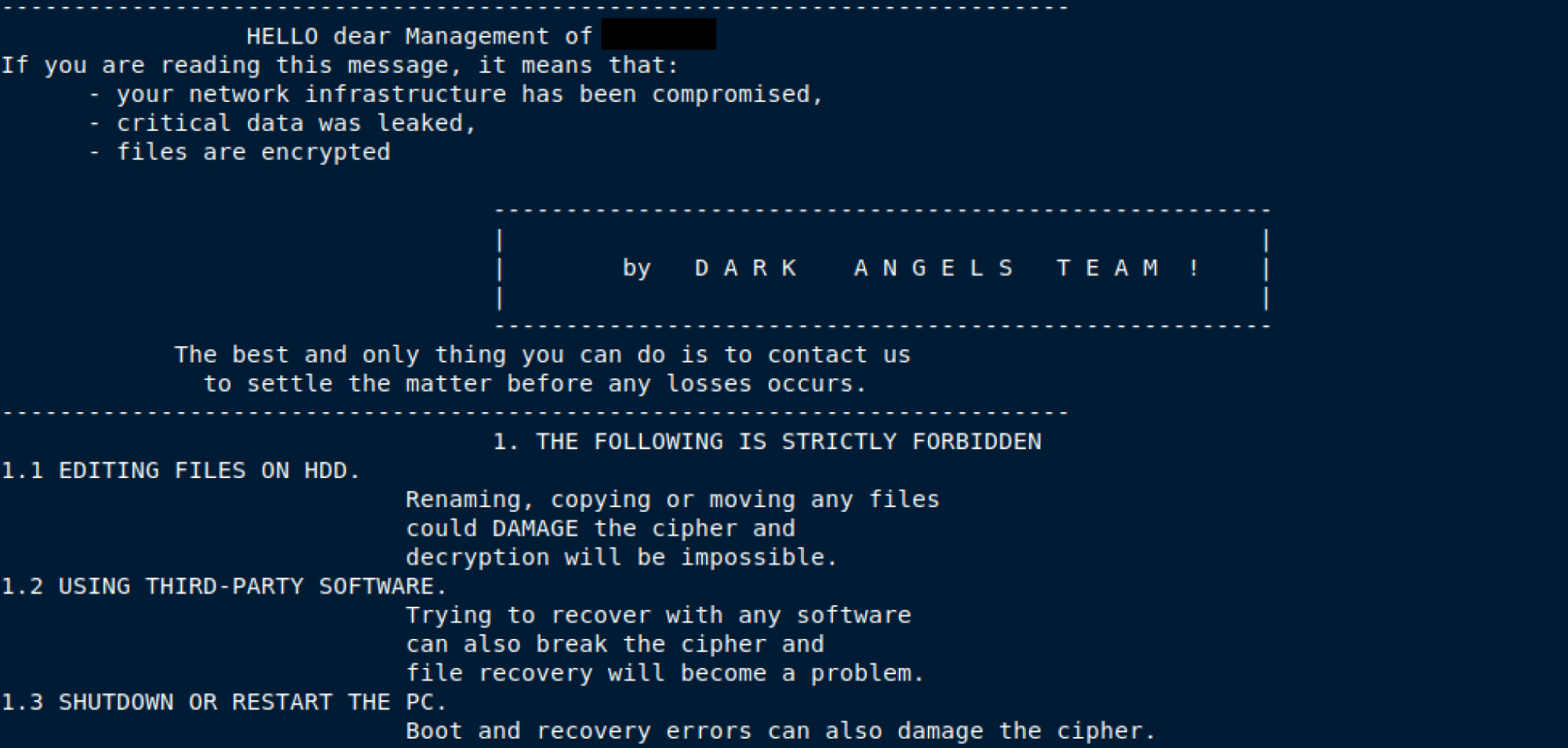
The Uptycs Threat Research team recently observed an Executable and Linkable Format (ELF) ransomware which encrypts the files inside Linux systems based on the given folder path. We observed that the dropped README note matches exactly with the DarkAngels ransomware README note (see Figure 1).
The DarkAngels ransomware was first seen this year during the month of May, in which its variants targeted Windows systems. The ELF file we found itself is new, but the Onion link found in the ransomware binary appears to be down, indicating that this new Linux-targeted ransomware might still be under development.
Figure 1: DarkAngels ransomware README
Technical Overview
The ransomware binary for the ELF version observed (hash: 3b56cea72e8140a7044336933cf382d98dd95c732e5937a0a61e0e7296762c7b) requires a folder as an argument for the encryption in the victim system. Once the folder path is given, it starts encrypting files present inside the folder. The extension used by the threat actor is .crypted (see Figure 2).
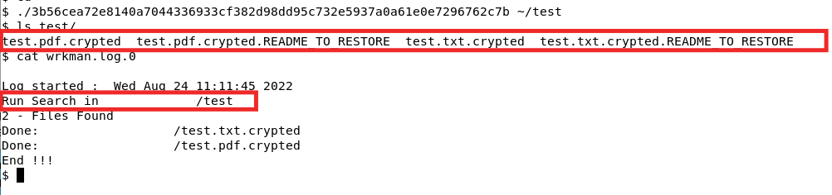
Figure 2: DarkAngels ransomware in action
The binary uses the pthread_create function for creating a new thread. The pthread_create() function starts a new thread in the calling process. The new thread starts execution by invoking start_routine()(FUN_0041cf55) (see Figure 3).
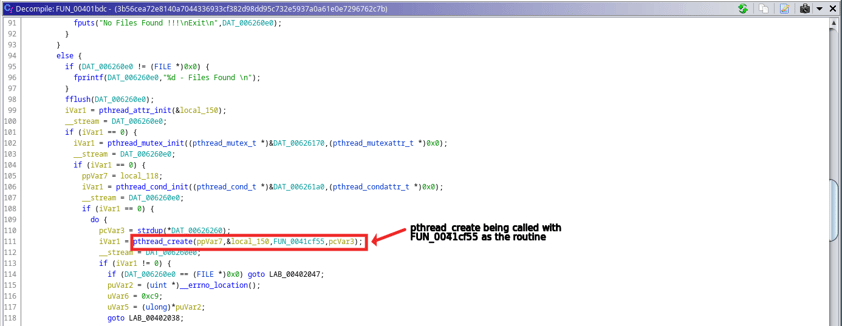
Figure 3: pthread usage inside the ransomware binary
The start_routine()(FUN_0041cf55) (see Figure 4) function performs the following steps to encrypt target files:
- Opens the target file and sets the write lock on it using fcntl().
- Closes the target file and then renames it to <target_file>.crypted.
- Opens another file by the name <target_file>.crypted.README_TO_RESTORE ,writes the README content into that and closes it.
- Opens <target_file>.crypted and writes the encrypted content to it using combination of lseek and write call.
- Also, a list of all the encrypted files gets stored in a file named wrkman.log.0.
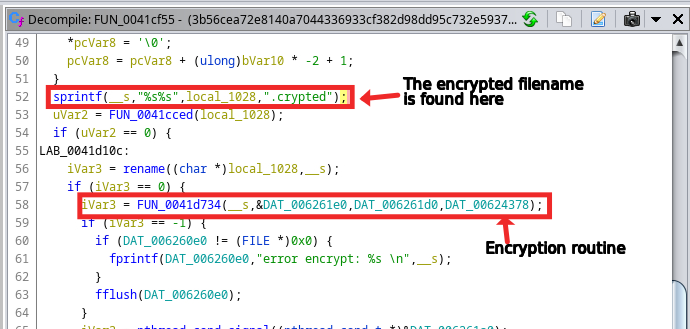
Figure 4: Inside the start_routine
Uptycs EDR Detections
The Uptycs endpoints detection and response (EDR), armed with YARA process scanning, detects the Dark Angels ransomware with a threat score of 10/10 (see Figure 5).
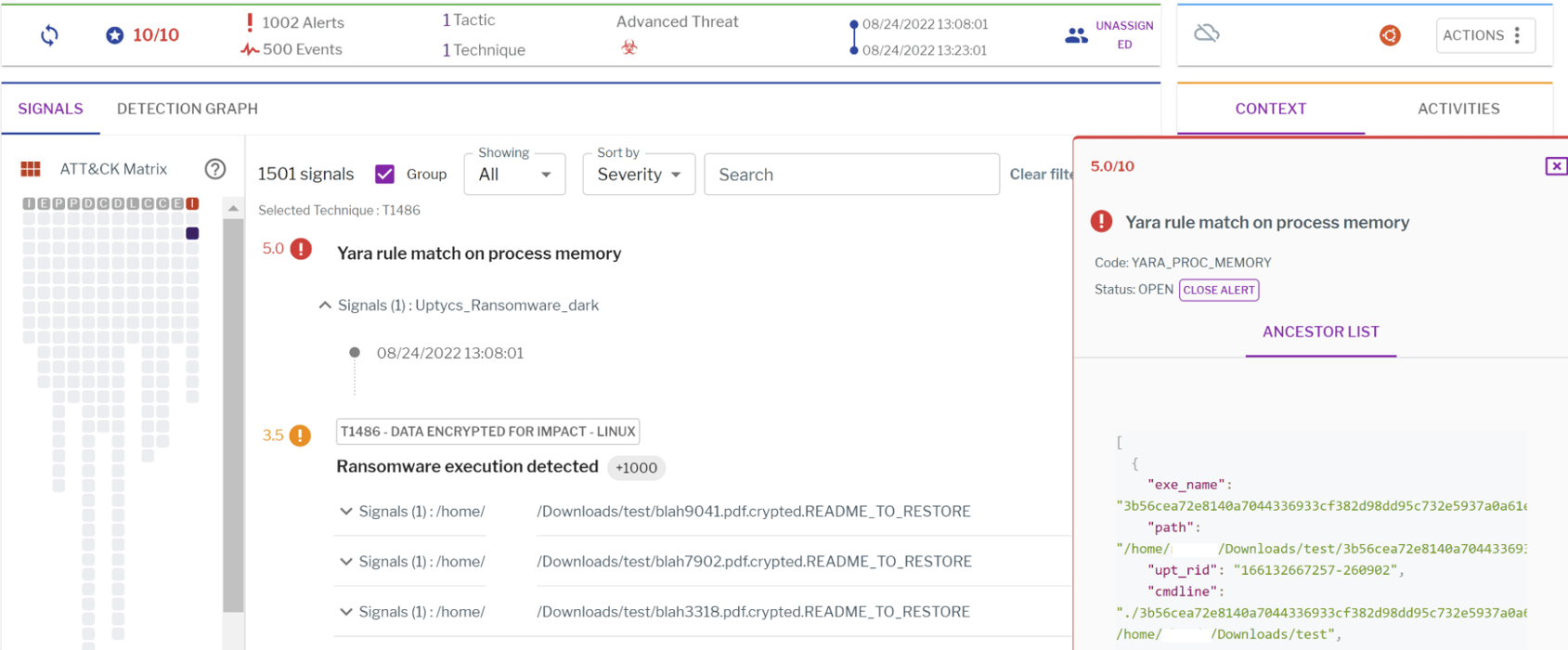
Figure 5: Uptycs EDR detection for DarkAngels ransomware
Conclusion
Ransomware families targeting Linux systems or going cross-platform to target multiple OSes is not new. In the past, the threat actors have expanded their ransomware campaigns across OS flavors in order to target more victims. The DarkAngels ransomware appears to still be in a development phase, with a clear goal to target Linux systems.
We may see some new features or advancements in this family of ransomware in the future. The Uptycs Threat Research team is continuously monitoring related malware campaigns to safeguard customers and inform the broader security community.
IOCS
3b56cea72e8140a7044336933cf382d98dd95c732e5937a0a61e0e7296762c7b
http[:]//qspjx67hi3heumrubqotn26cwimb6vjegiwgvrnpa6zefae2nqs6xqad[.]onion/page/6297aa368ec25
To learn more about the latest threat research conducted by the Uptycs Team, check out our most recent threat bulletin.