Revealed: The Biggest Threats to Your Cloud Workloads
Secure Hybrid Cloud Workloads At Scale
Our Customer Experience team is always on-hand to help fine-tune and optimize your strategy to improve efficiency and maximize your investment.
Starting with agentless discovery and scanning for every workload including vulnerabilities, malware, secrets, and software catalog for risk management with the ability to add Uptycs sensor for runtime detection & response
Stop malicious attacks in real-time leveraging the Uptycs sensor and establish hardened software pipelines for VM and Container Images to enable trusted deployments.
Discover hidden malware, secrets, and threats across your workload fleet leveraging best in class leveraging YARA toolkits, File Integrity Monitoring, Log Analysis, and eBPF event collection.
Adaptable Cloud Security: Uptycs Protects Every Workload
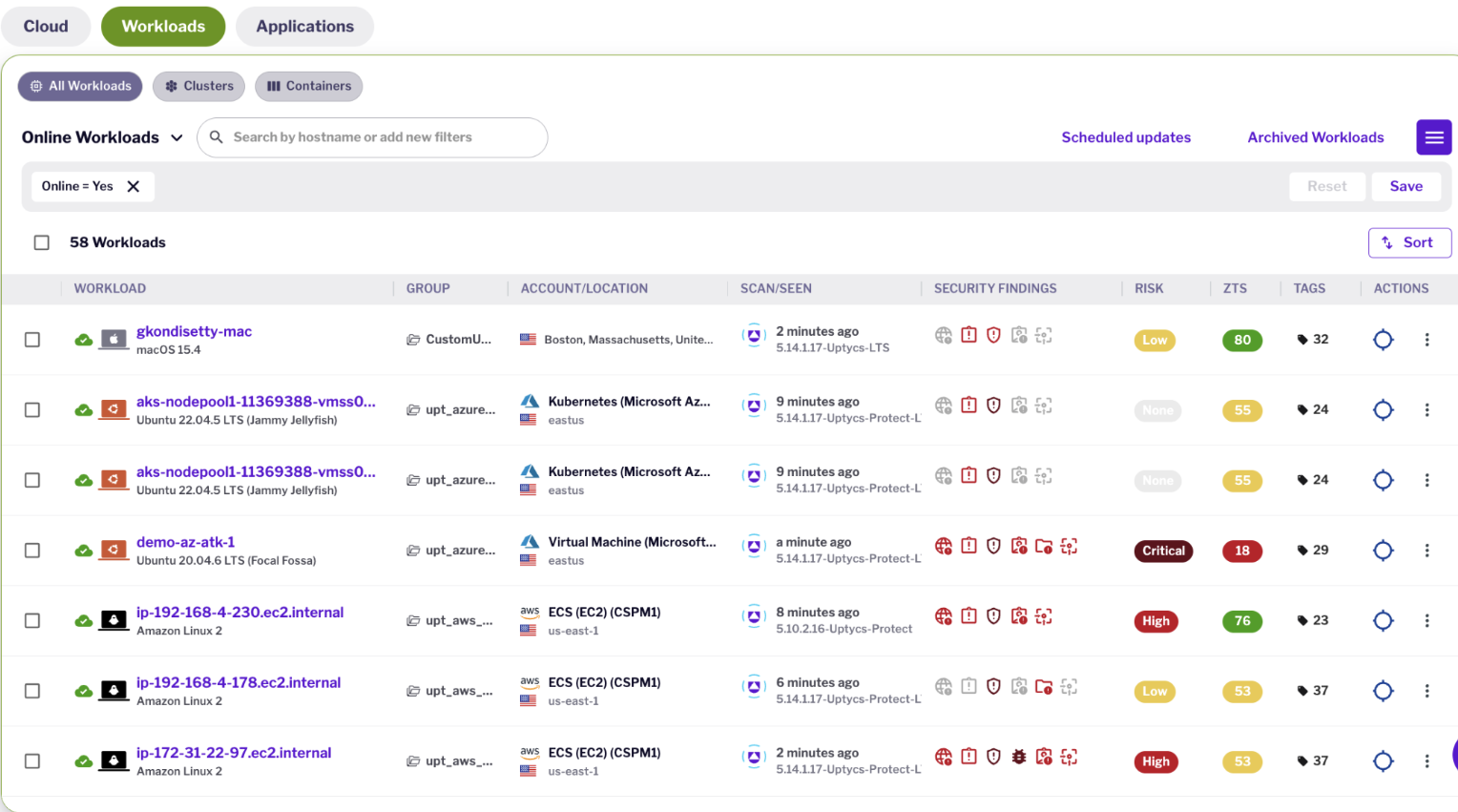
Uptycs gives you fleet-level visibility and deep insights into your workloads, from in-use packages and software inventory to processes, files, and network activity. Uptycs' eBPF sensor technology is designed to scale across millions of assets, enabling rich contextualization and prevention of vulnerabilities, risks, and threats in your hybrid cloud environment.
Powerful scanning, detection, and
remediation tools for the hybrid cloud
Fleet Level Discovery and Visibility
-
eBPF Asset Insights: Monitors every aspect of workloads from file and process execution to network level activity
-
SBOM and Software Catalog: Leverages GenAI intelligence to automatically label software inventory and packages in use by running assets for risk prioritization
-
Secrets & Certificates Scanning: Discovers unencrypted secrets, public keys and expired certificates
Runtime Risk and Threat Detection
-
Behavioral and Anomaly Based Detections: Detects malicious activity based on both YARA-based behavioral signatures and anomaly based detections
-
Contextualized Risk and Vulnerability Management: Prioritizes vulnerabilities that are actually in use by running processes in your environment to cut down noise
-
Attack Path and Software Build Provenance: Leverages detailed attack path analysis and application provenance for root cause analysis to hunt down misconfigurations, 3rd party dependencies, and malicious code in your software pipeline
Real-Time Response & Automated Prevention
-
Uptycs Rule Engine: Automatically detect and prevent malicious processes such as cryptominers and reverse shells in real-time
-
Bulk Remediation: Customizes remediation plans and admission policies for real-time and proactive remediation
-
Build To Runtime Policies: Apply customizable policies to enforce deployments from hardened container images
Threat Hunting & Forensics
-
File and Process Carving: Carve files and processes in real-time or for historical forensic analysis up to 13 months back
-
YARA Scanning: Leverage in-built as well as customized YARA toolkits for incident response
-
Threat Hunting: Discover malware and other key threats based on key signatures across your asset fleet
Works with What You Have
You rely on an existing suite of tools, and adding a CNAPP shouldn't complicate your
team's work. That's why Uptycs works seamlessly with your existing tech stack.


Success Stories
“Uptycs was deployed on a large scale as a key component of our security posture.”
“Uptycs has been instrumental for our FedRamp authorization and ISO 27001 certification.”
“Uptycs helps me sleep better at night.”
“A unified view from which we can quickly ask and answer security questions across our environment.”
“Uptycs simplifies investigations and saves time—about 30% per investigation.”
“I would not want to do security anywhere without this level of visibility.”
“Uptycs enables us to make risk-based decisions.”
“Uptycs contextualizes threat activity across K8s, cloud services, and laptops. We've dramatically shortened our threat investigation time.”










