Kubernetes and Container Security
Remediate Kubernetes risk inside the cluster and across your container supply chain – from developer to cloud.
Automate security across the software development lifecycle (SDLC), protect your container runtime environments, and simplify how developers and SecOps align on risk prioritization and remediation guidelines.
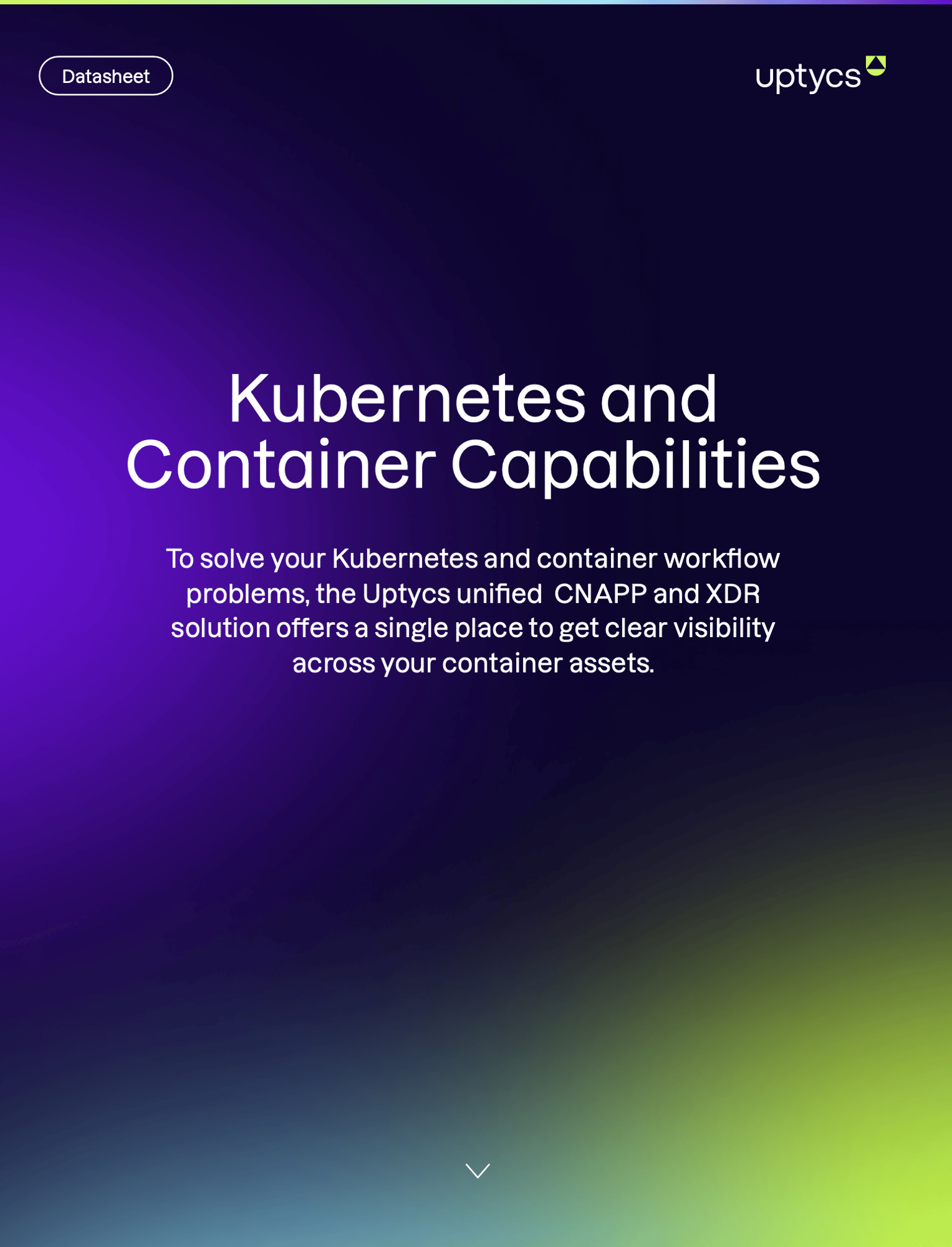
Real-time container security visibility across your fleet
Prioritize risk across Kubernetes clusters residing in private and public clouds and self-managed containers running on VMs.
- See a graphical overview of your Kubernetes environment, pick a cluster, then drill down to the most vulnerable containers
- Surface up the most risky namespaces, pods, and images based on real-time vulnerability, compliance, and threat data
- Leverage CIS and NSA Compliance Standards to determine Kubernetes control plane and data plane misconfigurations
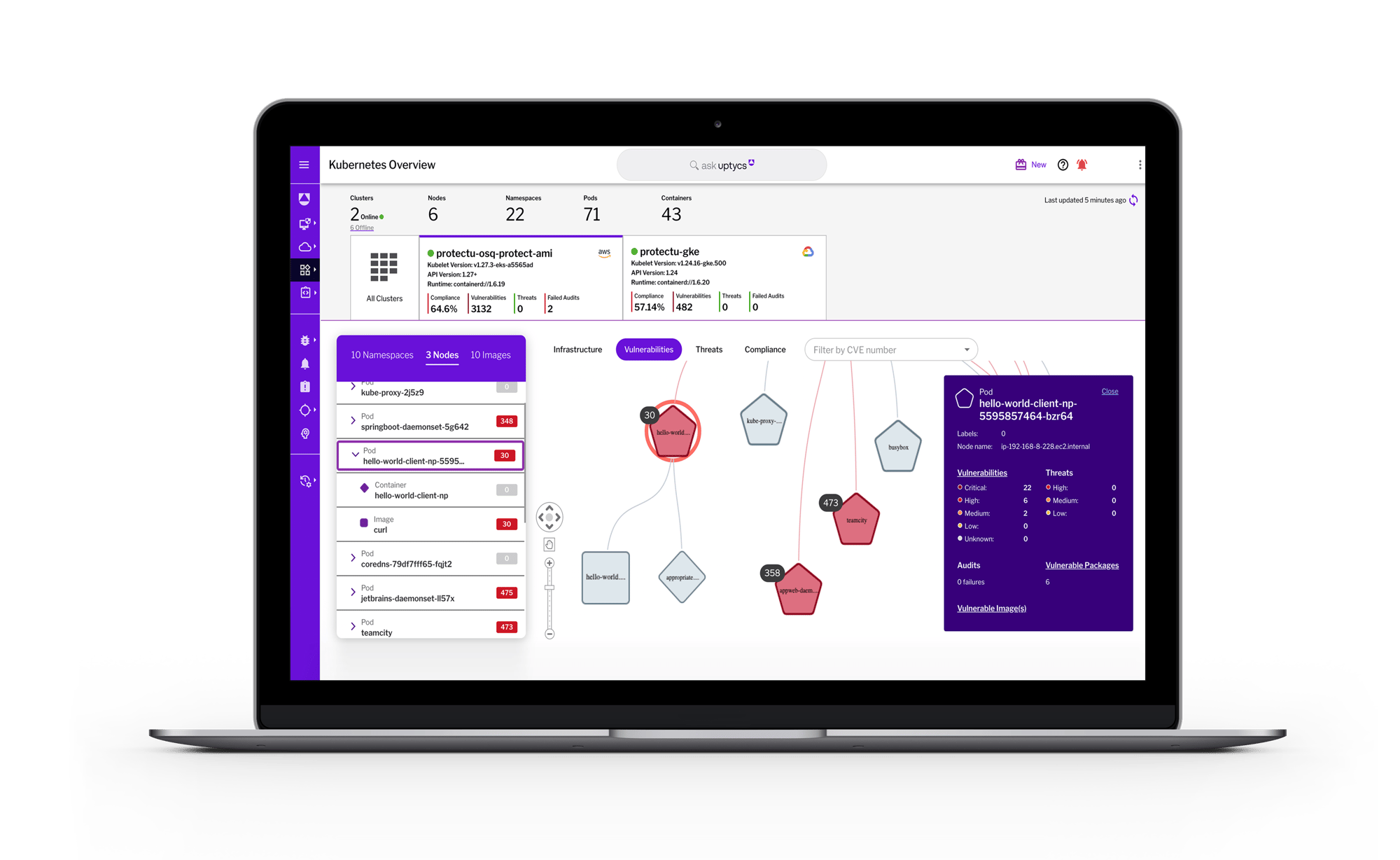
Shift left with preventative measures
Ensure issues are addressed before they reach production with shift left security controls.
- Automate security early in the software development lifecycle (SDLC) by scanning for vulnerabilities, malware, and secrets across developer workspaces, CI/CD pipelines, container registries, and runtime
- Create custom policies and incorporate CIS Software Supply Chain benchmarks to enforce source, build, and deployment integrity across your Kubernetes infrastructure
- Conduct IaC scans across your code repositories to find insecure Kubernetes configuration files and Helm charts
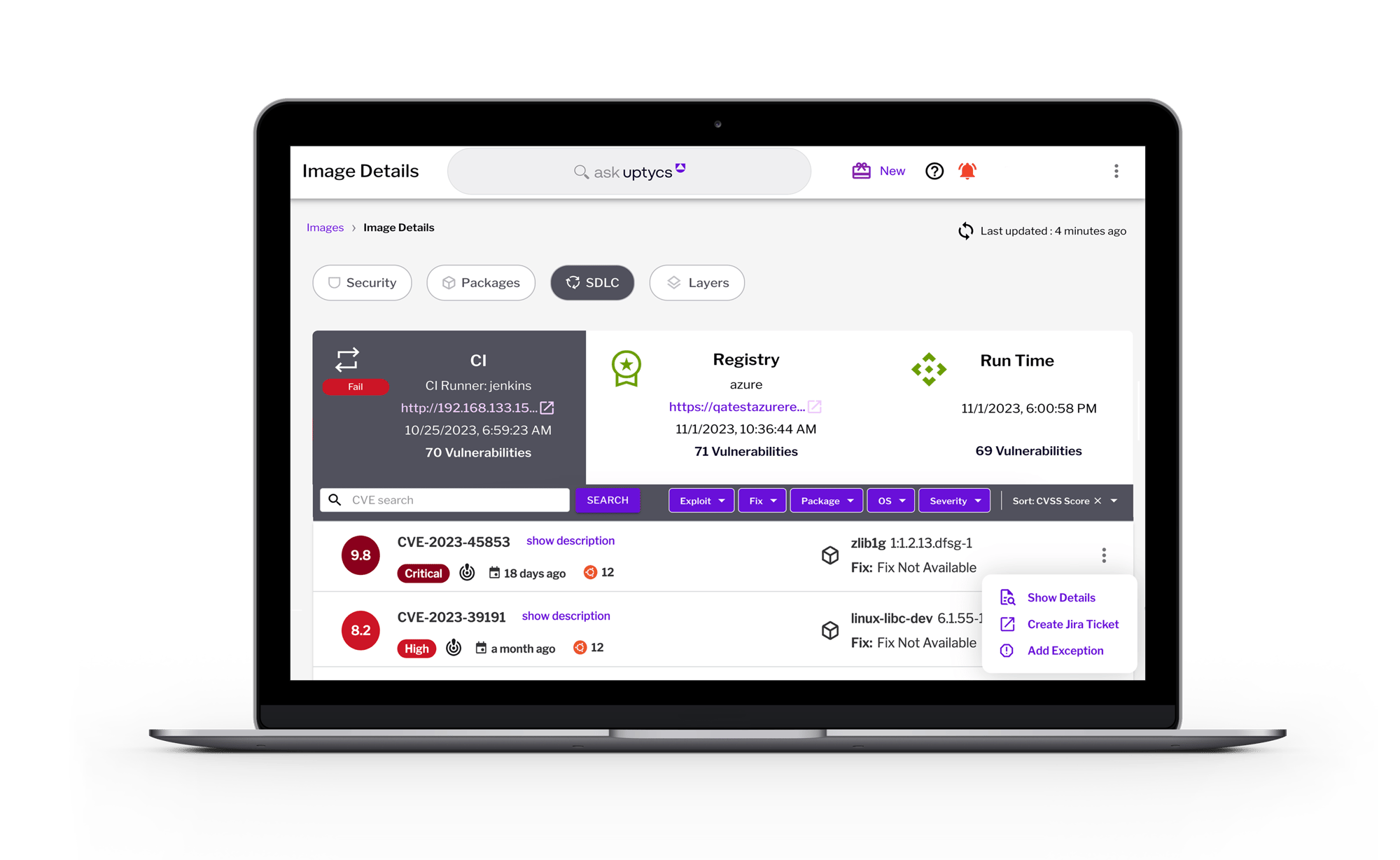
Defend against attacks in real time
Prevent malicious container threats and insecure infrastructure from spreading across your runtime environment.
- Remediate in real time by correlating threat detections, such as container breakouts and privilege escapes, to control plane misconfigurations including Kubernetes RBAC and access to secrets
- Align on remediation guidelines through OPA Gatekeeper policy controls to prevent insecure container images and infrastructure from making its way to container runtime based on Indicators of Compromise.
- Leverage YARA rule scanning to hunt and kill malicious container processes in real-time.
Resources for
the modern defender
Ebook
Mastering Kubernetes Security

Webinar
Can't Be Contained:Top Security Takeaways from KubeCon
Datasheet
Container and Kubernetes Security