The Uptycs threat research team has identified a new variant of credential stealing malware, dubbed Zaraza bot, that uses telegram as its command and control. Zaraza is the Russian word for infection.
Zaraza bot targets a large number of web browsers and is being actively distributed on a Russian Telegram hacker channel popular with threat actors. Once the malware infects a victim's computer, it retrieves sensitive data and sends it to a Telegram server where the attackers can access it immediately.
Zaraza bot steals login credentials from 38 web browsers including Google Chrome, Microsoft Edge, Opera, AVG Browser, Brave, and Yandex.
It then exfiltrates login credentials from online bank accounts, cryptocurrency wallets, email accounts, and other high value website targets. Attackers can then use the stolen data for malicious purposes such as identity theft, financial fraud, and unauthorized access to personal and business accounts.
This attack type can be particularly damaging, as it compromises a wide range of sensitive information that people and organizations rely on to protect their privacy and security.
Zaraza bot Malware FAQs
- What is the potential impact of Zaraza bot on individuals and organizations?
The impact of this malware on end-users includes potential identity theft, financial fraud, and unauthorized access to personal and business accounts. This could lead to significant financial losses and reputational damage for individuals and organizations. - How did Uptycs threat research first discover Zaraza bot and implement detection at scale?
During our malware hunting process, we received a binary specimen, which we subjected to testing within our sandbox environment. We noted that the malware attempted to gain access to the folder containing the credentials of the system's web browser. Subsequently, we conducted an analysis of the malware and implemented a YARA rule to enable detection alerts. We’ve included the YARA rule down below to help. - How does Zaraza bot steal credentials from web browsers?
The malware steals credentials from web browsers by scanning through a list of 38 different browsers and extracting any credential data present on the victim's machine. It targets specific files and databases within the browser to obtain stored login information. - What steps can I take to protect myself and my company?
To protect yourself against this malware, you should update your passwords regularly, follow online security best practices such as using strong passwords and multi-factor authentication, and ensure regular software and security system updates.
To protect your company, we are providing a copy of the YARA rule here down below which you can run across your environment with any EDR/XDR vendor with YARA rule detection capabilities, manually remove the malicious files, or seek professional help. - What is the significance of the malware using the Russian language?
According to network PCAP analysis, the Zaraza bot communicates back its findings, can be accessed through a Telegram channel and has been traced back to Russian hackers. The logs recorded by the bot are written in plain Russian language, without any use of colloquialism. The terminology used in the logs is basic and straightforward, such as "logs," "new logs," and "password." - Are there any indicators of compromise (IOCs) that can help detect Zaraza bot?
The article provides an IOC in the form of an MD5 file hash (41D5FDA21CF991734793DF190FF078BA) to help detect the malware. - The credentials collected are always/usually encrypted by the browser, correct? So the attacker would need to crack the passwords to use them?
Yes. The web browser on the system stores credentials in two encrypted formats as a default security measure. However, Zaraza bot is capable of decrypting both formats. - Is the Telegram channel that’s communicating the findings from Zaraza bot live?
Yes. The Telegram channel is live and attackers have grabbed all types of credentials from victims' browsers. After that, it is possible for threat actors to sell the credentials on the underground market or leverage them in follow-on attacks.
We’ve seen a recent increase in Telegram usage as C2 by threat actors. As a chat platform, Telegram provides attackers an advantage in bypassing detection technologies.
Infection Flow
The Zaraza bot has the ability to extract login credentials from a web browser and save them in a text file. Additionally, it can capture a screenshot of the victim's active window, which is then saved in a JPG file format. The stolen data is subsequently transmitted to the bot server where it can be accessed by the attacker.
Figure 1 depicts the Zaraza bot infection chain.
%20(1).png?width=1000&height=600&name=Zaraza%20bot%20Binary%20(4)%20(1).png)
Figure 1 – Zaraza bot infection flow
Technical Analysis
Zaraza bot is a 64-bit binary file compiled using C#. It’s associated with browser-related activities and contains the Russian language in the code. The threat actor has set the entry point of the program to null, making it difficult to halt the execution point while debugging.
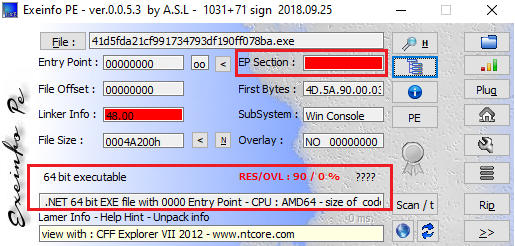
Figure 2 – Zaraza bot binary
Upon execution, an attacker obtains the username of a victim's machine, then creates a new subfolder in the Temp directory by that name.
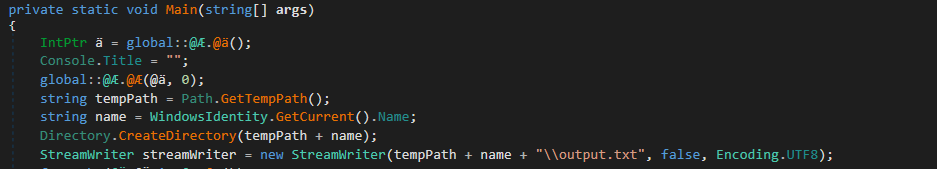
Figure 3 – Obfuscated and file creation code
Next, the attacker generates an "output.txt" file within the new subfolder.
C:\Users\<user name>\AppData\Local\Temp\<PC name>\<user name>\output.txt
Zaraza bot then systematically scans through each of 38 browsers, listed in the table below, to extract any credential data present on the victim's machine. Boldface type below indicates the most commonly used browsers worldwide.
| 360 Browser | Chromium | SRWare | Iridium Browser | Sleipnir 6 |
| 7Star | Iron Browser | Kinza | Slimjet |
| Amigo | Citrio | Kometa | Sputnik |
| AVAST Software | CocCoc | Liebao Browser | Torch Browser |
| AVG Browser | Comodo Dragon | Opera | uCozMedia |
| Brave Browser | CoolNovo | Opera GX | URBrowser |
| CCleaner | Coowon | Opera Neon | Vivaldi |
| CentBrowser | Edge Chromium (Microsoft Edge) |
Orbitum | Yandex |
| Chedot | Elements Browser | QIP Surf | |
| Chrome | Epic Privacy Browser | SalamWeb |
Figure 4 lists the User Data folder path configuration for various web browsers.
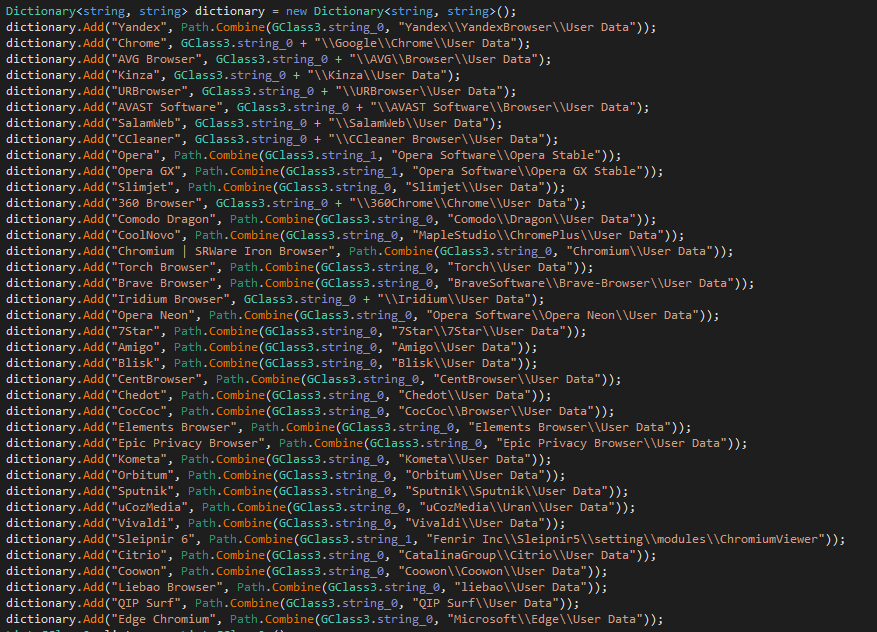
Figure 4 – Browser path list for User Data folder
The SQLite database format used by browsers contains a specific file named "Login Data"; it includes a "logins" database table. This table stores login details for various websites and contains fields such as the following:
"origin_url" (the main link of the site)
"action_url" (the login link of the site)
"username_element" (the username field on the site)
"username_value" (the username used for login)
"password_element" (the password field on the site)
"password_value" (the encrypted password used for login)
"date_created" (the date when the data was stored)
"times_used" (how many times the password has been used)
"blacklisted_by_user" (a flag set to 1 if the password should never be stored)
However, in our case the attacker managed to retrieve only three key database details: "origin_url", "username_value" and "password_value". Given that the password field is stored in an encrypted format, the attacker had to check two specific things to retrieve the passwords.
Two distinct encryption methods are used for storing passwords within a web browser database:
- Newer browser versions use a v80 password signature. Starting with v10 or v11, it uses master key-based encryption to securely store users' web login passwords. The encrypted password is further protected using the Windows DPAPI function ("CryptProtectData").
To identify the encrypted key, a signature DPAPI is inserted at the beginning of the string. Then the encrypted key is encoded using Base64 and saved in the Local State file located in the User Data folder (fig. 3).
- In older browser versions, website passwords were encrypted using the Windows DPAPI ("CryptProtectData") function; the resulting encrypted password was stored in the Login Data file.
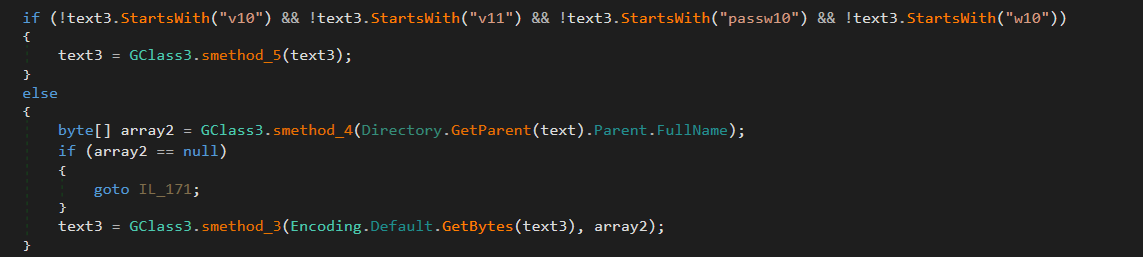
Figure 5 – Retrieve the password
After successfully extracting encrypted passwords from the browser, the attacker then saved this data to the output.txt file.
As anticipated, Uptycs successfully detected the stealer as it attempted stored browser credentials retrieval.
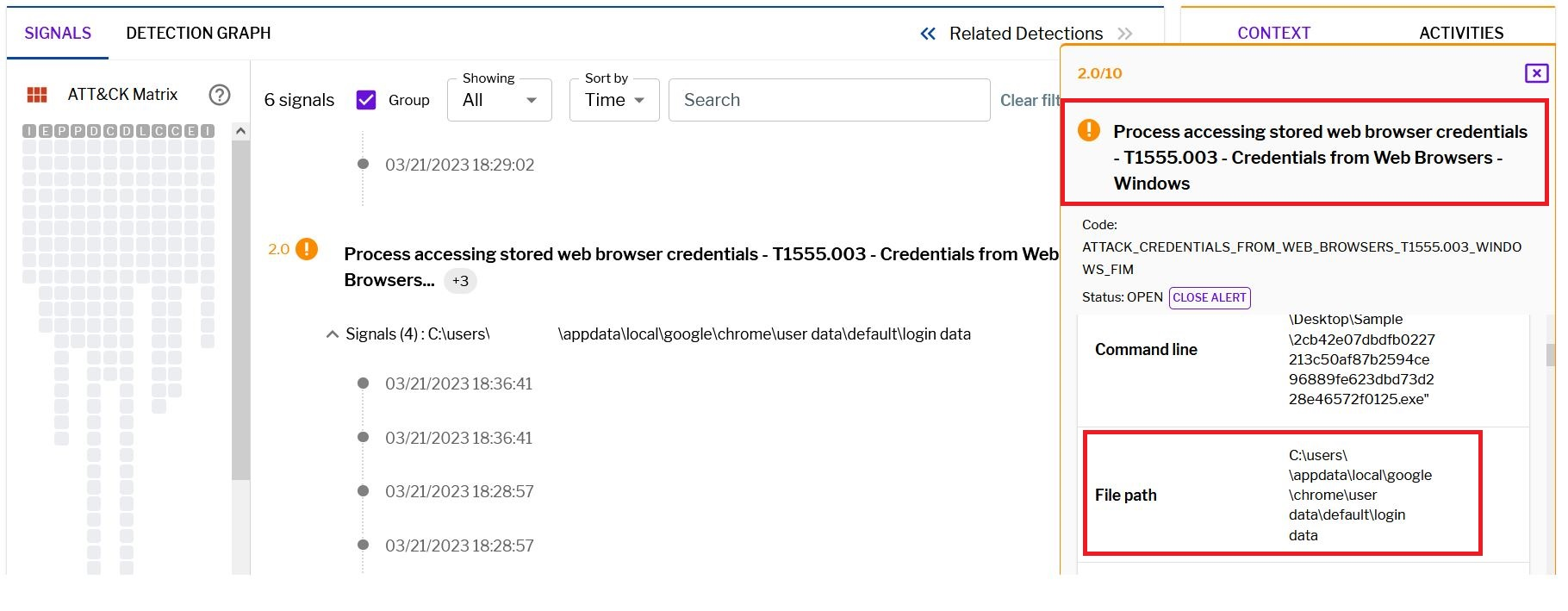
Figure 6 – Uptycs alert for credentials access
Using the CopyFromScreen() method, the attacker takes a screenshot of the victim's machine, saving that to Screen.jpg in the same output.txt file location.
C:\Users\<user name>\AppData\Local\Temp\<PC name>\<user name>\Screen.jpg
The attacker obtains the recorded information (output.txt, Screen.jpg) by accessing a Telegram bot channel where the data is shared.
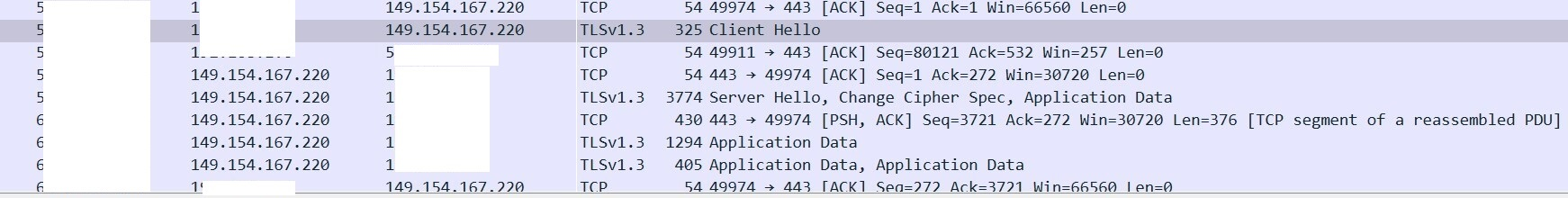
Figure 7 – Connecting telegram channel
Network Analysis
By analyzing the network capture, the Uptycs threat research team identified a private Telegram bot channel that originates from Russia. Through analysis of the Telegram bot channel link, the name of the bot was able to be determined, as clearly shown in the snapshot below (fig. 8).
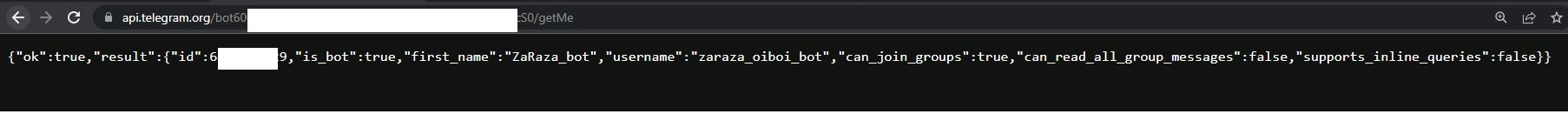
Figure 8 – bot channel details
The Zaraza bot
It appears that the Zaraza bot operates on a commercial basis, with threat actors able to purchase access to the bot. After analyzing the Telegram channel, we identified several options available through the bot.
- Restart (if keyboard is missing)
- Help and support
- Change a language/LANGUAGE
- Pay by Subscription
- Create a post
- Edit post
- Content plan
- Reports and statistics
- Settings
- Creatives
- Get a personalized sticker pack
Figure 9 shows the research team attempting to utilize some of the options available in the bot channel but were denied access.
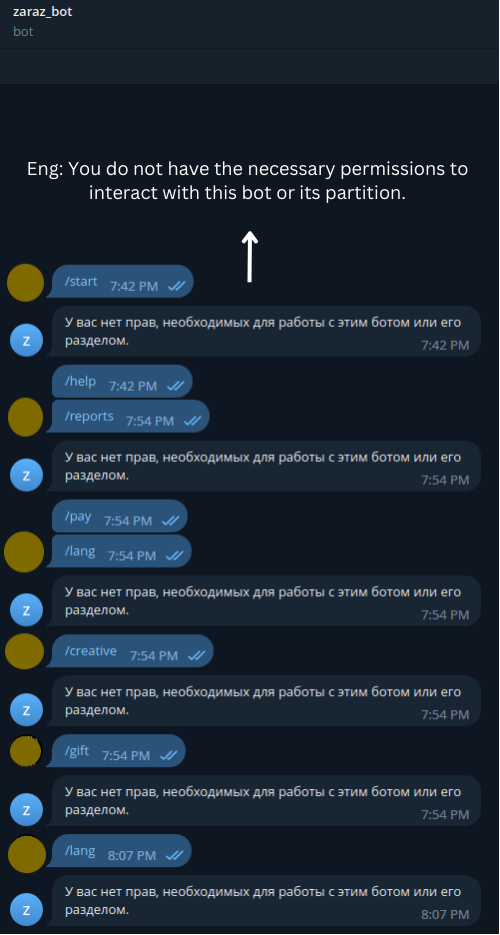
Figure 9 – Telegram bot
Through analysis of HTTPS packets, we discovered that the Zaraza bot had intercepted data containing the username and account information of a Russian user. This observation strongly suggests that the Russian user is connected to either the bot administrator or a threat actor associated with the bot as clearly shown in the snapshot below (fig. 10).
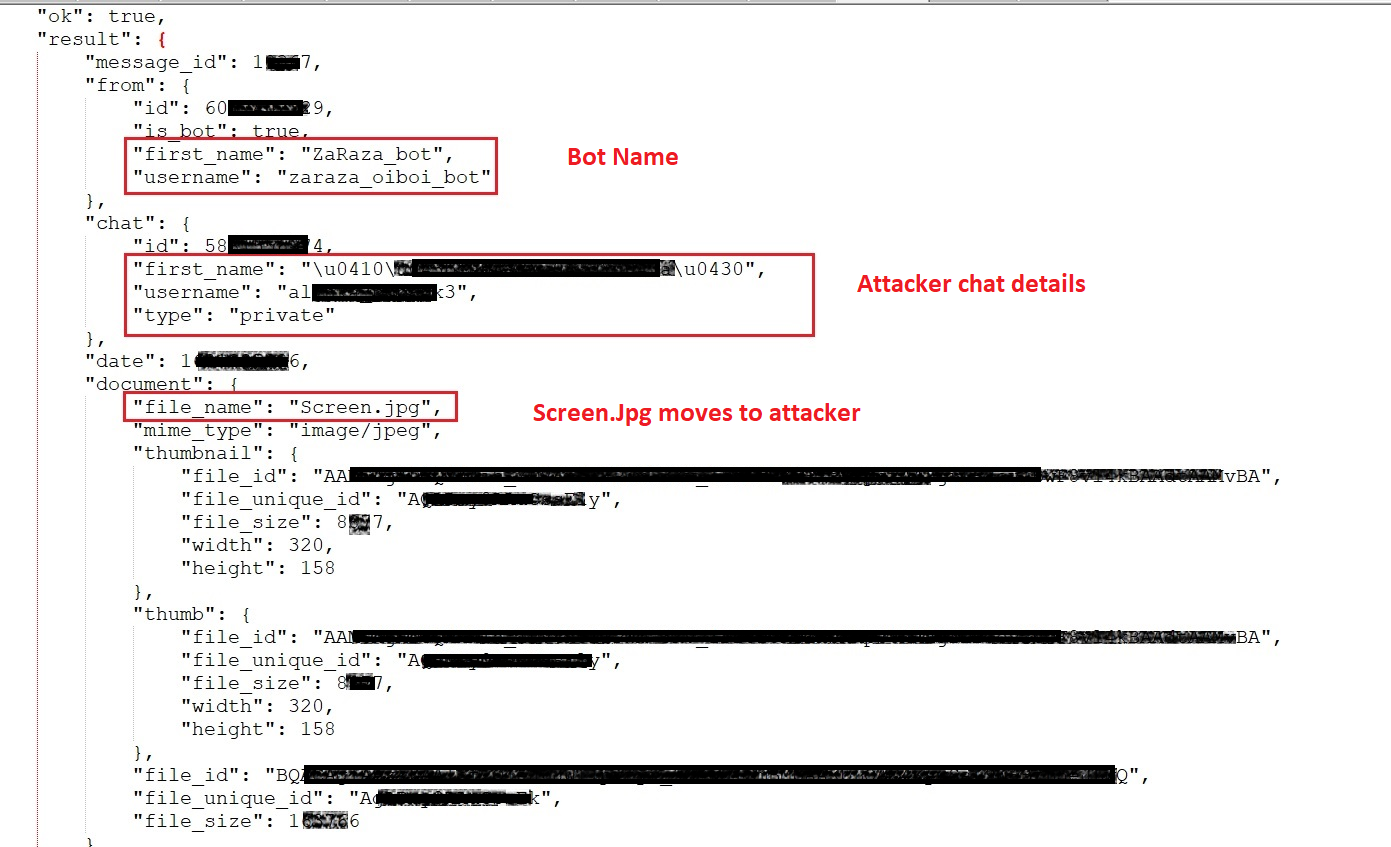
Figure 10 - Network (HTTPS) traffic
How to detect and respond to Zaraza bot using your current XDR solution or Uptycs XDR
Uptycs XDR clients can easily scan for credential stealers like Zaraza bot since our platform is armed with YARA process scanning and advanced detections. Additionally, Uptycs XDR contextual detection provides important details about such identified malware. Users can navigate to the toolkit data section in the detection alert, then click on a name to learn about its behavior (fig. 11).
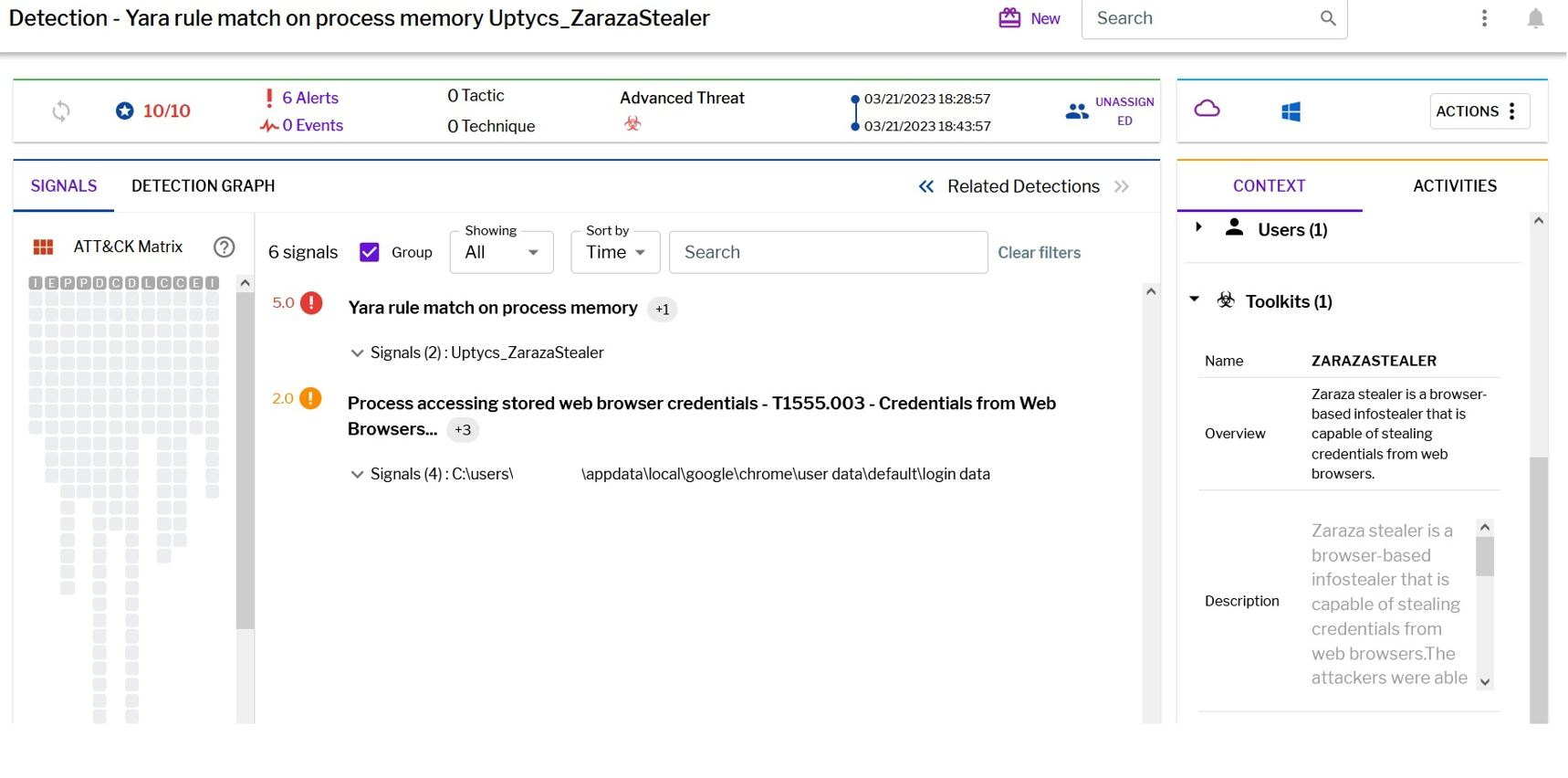
Figure 11 - Uptycs XDR detection
Zaraza bot YARA malware detection rule
Uptycs XDR scans the memory of newly launched processes and detects any presence of suspicious strings by utilizing YARA rules.The YARA rule for detecting this malware has already been made available to our customers.
If you are not an Uptycs XDR customer, you can use either the YARA tool or a third-party tool to scan suspicious processes. We have shared the rule below for your convenience.
rule Uptycs_Zarazabot_v1
{
meta:
malware_name = "Zarazabot"
description = "Zarazabot is a credential stealer that is capable of stealing login credentials from web browsers."
author = "Uptycs Inc"
version = "1"
strings:
$string_1 = "\\Ya Passman Data" ascii wide
$string_2 = "\\Google\\Chrome\\User Data" ascii wide
$string_3 = "Microsoft\\Edge\\User Data" ascii wide
$string_4 = "BraveSoftware\\Brave-Browser\\User Data" ascii wide
$string_5 = "encrypted_key" ascii wide
$string_6 = "FromBase64String" ascii wide
$string_7 = "<UploadToTelegram>" ascii wide
$string_8 = "DownloadString" ascii wide
$string_9 = "CopyFromScreen" ascii wide
$string_10 = "\\output.txt" ascii wide
$string_11 = "Passwords.txt" ascii wide
$string_12 = "\\Screen.jpg" ascii wide
condition:
all of them
}
IOC
|
File name |
Md5 |
|
Zaraza bot binary |
41D5FDA21CF991734793DF190FF078BA |
URL
|
https[:]//t[.]me/zarazaA_bot |
|
149.154.167[.]220 |







