On 29 March 2024, the cybersecurity community turned its attention to a newly disclosed vulnerability in XZ Utils, identified as CVE-2024-3094. This backdoor vulnerability has sent ripples across the tech world, primarily due to the widespread use of XZ Utils for lossless data compression in Linux and macOS systems. This blog aims to demystify CVE-2024-3094, outlining its background, impact, and the steps required for mitigation.
XZ Utils backdoor vulnerability: Background
XZ Utils is an essential software package for developers, offering lossless compression of release tarballs, software packages, kernel images, and initramfs images. Given its utility, XZ Utils is almost ubiquitously installed across Linux and macOS systems for convenience. The discovery of a backdoor in versions 5.6.0 and 5.6.1 of XZ Utils presents a significant security concern, especially for systems with publicly accessible SSH ports.
RedHat has issued a warning about this flaw in XZ Utils, a set of XZ format compression tools commonly found in Linux distributions, indicating it could potentially allow a nefarious individual to compromise sshd authentication and obtain remote unauthorized system access. However, Red Hat also mentioned that fortunately, versions 5.6.0 and 5.6.1 have not been extensively adopted by Linux distributions yet, mainly appearing in pre-release forms.
The malicious versions intentionally interfere with authentication performed by SSH, a commonly used protocol for connecting remotely to systems. SSH provides robust encryption to ensure that only authorized parties connect to a remote system. The backdoor is designed to allow a malicious actor to break the authentication and, from there, gain unauthorized access to the entire system. The backdoor works by injecting code during a key phase of the login process.
The backdoor was deliberately concealed by the developer. It gets incorporated into the binary during the RPM or DEB packaging process for x86-64 architecture, using gcc and gnu linker, under the guise of a "test" step. Consequently, the compromised binary is distributed within the RPM or DEB package.
How the XZ Utils backdoor vulnerability operates
It is a sophisticated backdoor that remains dormant until activated under specific conditions. It leverages the glibc library and exploits systems running vulnerable versions of xz or liblzma. Notably, the backdoor can be triggered by remote, unprivileged systems connecting to public SSH ports, leading to performance issues and potential unauthorized access.
XZ Utils Vulnerability criteria
For a system to be vulnerable to CVE-2024-3094, several conditions must be met:
- The system must use glibc, specifically for IFUNC support.
- XZ Utils version 5.6.0 or 5.6.1, or the corresponding versions of liblzma, must be installed.
- Systems utilizing systemd and a patched version of OpenSSH are known to be vulnerable, though the risk may extend to other configurations pending further analysis.
Who is affected by CVE-2024-3094?
|
OS |
Affected |
Comments |
Reference |
|
Debian (testing, unstable and experimental distributions) |
Yes |
Vulnerable Versions are 5.5.1alpha-0.1 to 5.6.1-1 |
https://lists.debian.org/debian-security-announce/2024/msg00057.html |
|
Debian (Stable Version) |
No |
No Debian stable versions are known to be affected. |
https://lists.debian.org/debian-security-announce/2024/msg00057.html |
|
Fedora 41, Fedora Rawhide |
Yes |
Vulnerable versions are xz-5.6.0-* and xz-5.6.1-* |
https://www.redhat.com/en/blog/urgent-security-alert-fedora-41-and-rawhide-users |
|
Fedora 40 |
No |
RedHat recommends that users downgrade to a 5.4 build of XZ as a precaution |
https://www.redhat.com/en/blog/urgent-security-alert-fedora-41-and-rawhide-users |
|
Alpine Edge |
Yes |
Vulnerable versions are 5.6.0 to 5.6.1 |
|
|
Kali Linux |
Yes |
Backdoored version of xz was included in Kali Linux (xz-utils 5.6.0-0.2) between March 26 and March 28 |
|
|
Arch Linux |
Yes |
Vulnerable versions are 5.6.0-1 to 5.6.1-1 |
https://archlinux.org/news/the-xz-package-has-been-backdoored/ |
|
openSUSE Tumbleweed and openSUSE MicroOS |
Yes |
Backdoored version of xz was included in Tumbleweed and MicroOS between March 7 and March 28 |
|
|
SUSE Linux Enterprise and Leap |
No |
Both Enterprise and Leap are isolated from OpenSUSE and are unaffected. |
|
|
RedHat |
No |
No versions of Red Hat Enterprise Linux (RHEL) are affected. |
https://www.redhat.com/en/blog/urgent-security-alert-fedora-41-and-rawhide-users |
|
Ubuntu |
No |
No stable ubuntu versions are affected |
|
|
Amazon Linux |
No |
Amazon Linux customers are not affected by this issue, and no action is required |
https://aws.amazon.com/security/security-bulletins/AWS-2024-002/ |
- CISA warns that they have reports of supply chain compromise - https://www.cisa.gov/news-events/alerts/2024/03/29/reported-supply-chain-compromise-affecting-xz-utils-data-compression-library-cve-2024-3094
Uptycs products are unaffected
Uptcys has confirmed that our products, both the endpoint client software running on customer systems along with our on-premises software and our cloud servers, were not impacted by CVE-2024-3094 and did not present a risk to our customers or their systems.
CVE-2024-3094: Detection with Uptycs CNAPP
Uptycs has proactively pushed a vulnerability threat book to all of our customers and scanned all of the configured assets. The results of the scan are present on our landing page in the Trending Vulnerabilities card. If any assets are impacted they would surface to the top. If there are no assets impacted it is shown at the end of the list as there is no action to take.
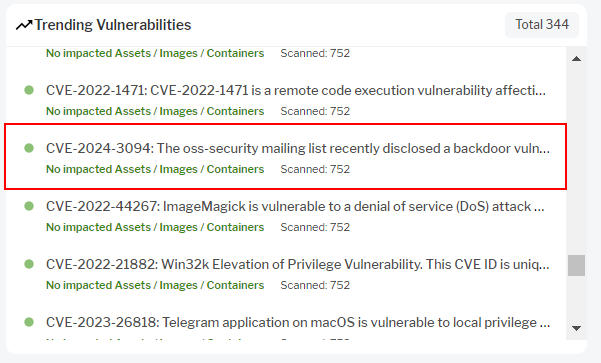
Figure 1 - The vulnerability CVE-2024-3094 in Trending Vulnerabilities Card
Does your system have a vulnerable version of XZ Utils? Uptycs XDR offers robust vulnerability scanning features for timely detection. Uptycs XDR stores vulnerability scan results in a dedicated table, accessible via SQL queries, as shown below:
select cve_list, package_name, package_version, cvss_score, os from vulnerabilities where cve_list = 'CVE-2024-3094'
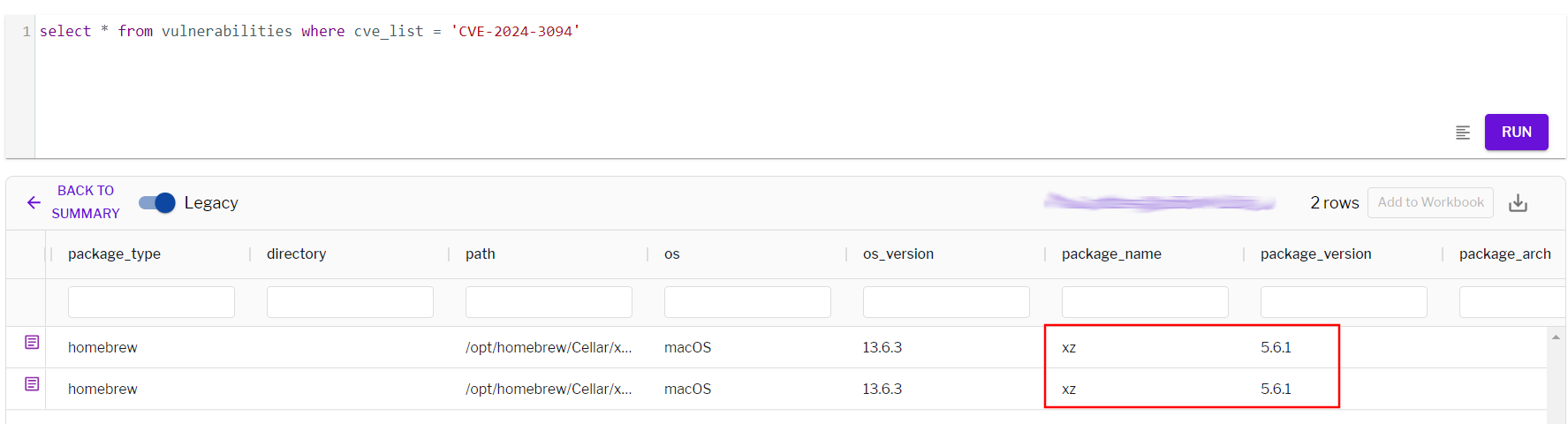
Figure 2 - Detection of CVE-2024-3094 with vulnerability scan
Conclusion
Uptycs continues to monitor latest and trending threats and provide additional steps for mitigating the threat. It is highly recommended for admins to check if the affected xz library versions are present in any of the assets in their fleet and patch immediately.
SHA256 Hashes:
|
15b08cbaa49b6df580f81ef85d5dd4bcca4dac41daa87b47c67177707b697cb7 |
aaaaf9a12d38dac328c74b45a2e6ea43950c85ecb010406d4092594cd904edc3 |
|
257fc477b9684863e0822cbad3606d76c039be8dd51cdc13b73e74e93d7b04cc |
b0f95b124073faaac4415aefa4bb3985f287318efa8db702303f68dd650da349 |
|
319feb5a9cddd81955d915b5632b4a5f8f9080281fb46e2f6d69d53f693c23ae |
b418bfd34aa246b2e7b5cb5d263a640e5d080810f767370c4d2c24662a274963 |
|
5448850cdc3a7ae41ff53b433c2adbd0ff492515012412ee63a40d2685db3049 |
c292bc94bb3a4d631ee458b22d633268e0a74733838f4b8638cd164bf150c9c5 |
|
5d9f751a8311dab1c3fe3ec7ee8639cda5b451c305d58075f80e47ec8663e220 |
cbeef92e67bf41ca9c015557d81f39adaba67ca9fb3574139754999030b83537 |
|
605861f833fc181c7cdcabd5577ddb8989bea332648a8f498b4eef89b8f85ad4 |
d44d0425769fa2e0b6875e5ca25d45b251bbe98870c6b9bef34f7cea9f84c9c3 |
|
6c4a1e1b7a776f9666eccfb0fb397576300c32f72090685c3b9bd61b534c8553 |
f19f29bbde3d6a6777fa7524179f68583a19278494019c289b6b9d59e5be9fd8 |
|
8d2922eab67169c01aca9b7c9813ff5c14b932ce70928ce7beac2945623d53b1 |
f50ee33bab6abc93164577ca80f111d77595659842920d04a4d22e184f675d14 |
|
8fa641c454c3e0f76de73b7cc3446096b9c8b9d33d406d38b8ac76090b0344fd |
fcd4d1ba8a4def4e7178c27513a2897001019722f131efe7c4f6b940f231071b |
Suggested further reading:
https://www.uptycs.com/blog/tag/threats







