Recently a heap-based buffer overflow vulnerability was discovered in the sudo utility by Qualys. Sudo is a command-line utility that allows a user to run commands in the context of other users with proper authentication. The vulnerability lets any user escalate the privileges to the root user. Qualys has shared technical details in their blog post, so in this post I’ll focus on how osquery and Uptycs can be used to detect the exploit and unpatched systems.
CVE-2021-3156 exploit detection using Uptycs’ EDR capabilities
It’s most likely that a working exploit will be available in public very soon. A patch is already available and we recommend updating the package to the latest version. We have added a rule in Uptycs’ EDR to detect the exploit. The following query can be used to find the hosts for a possible exploit attempt:
select path,cmdline,login_name,uname,cmdline_size from process_events where cmdline like '%sudoedit%' and (cmdline like '%-s%' or cmdline like '%-i%') and cmdline like '%\%' and cmdline_size > 10
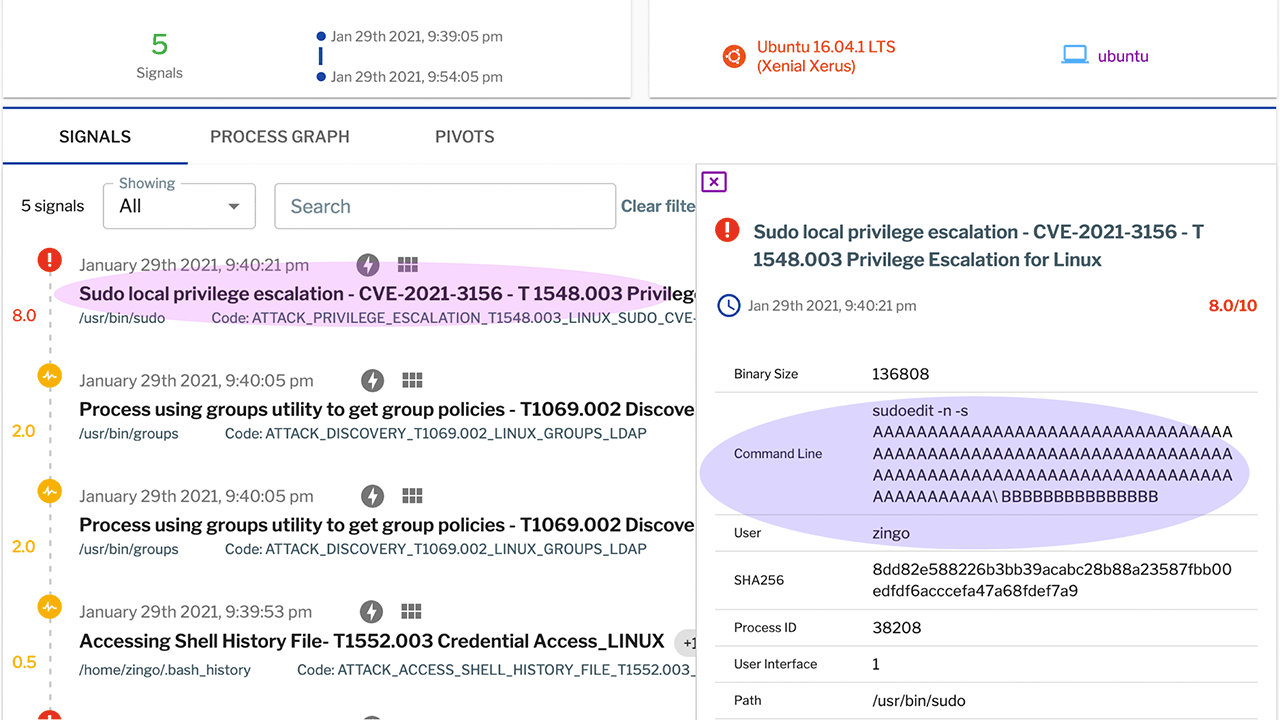
The following shows the Uptycs EDR detection:
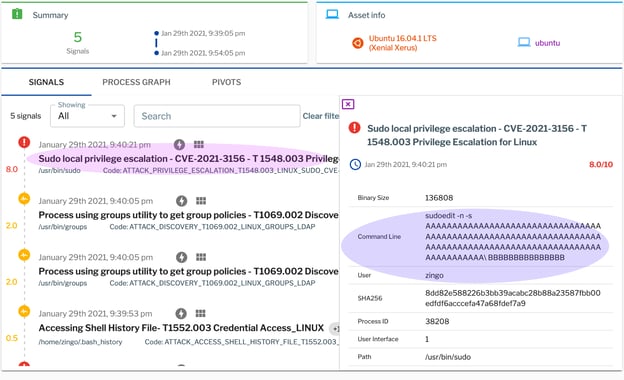
Figure 1. Uptycs EDR detection for CVE-2021-3156.
Identifying vulnerable packages and unpatched systems
Vulnerability details about the package are already available in the Uptycs vulnerability database (upt_threat_indicators table). A quick scan for the vulnerable sudo package on Ubuntu can be done using the following query:
WITH current_deb_packages AS ( SELECT * FROM windowed_deb_packages WHERE LOCALTIMESTAMP BETWEEN upt_add_time AND upt_remove_time), dp AS (SELECT dp.upt_asset_id, dp.NAME, dp.version, dp.arch, Osversion(ov.major, ov.minor) AS os_version FROM current_deb_packages dp JOIN os_version ov ON dp.upt_asset_id = ov.upt_asset_id) SELECT DISTINCT dp.upt_asset_id, lvv.package_name, dp.version AS installed_version, Vercmp(lvv.package_version, dp.version) AS vercmp_result, CASE WHEN Vercmp(lvv.package_version, dp.version) > 0 THEN 'VULNERABILITY DETECTED' END AS version_compare_result, lvv.os_version, lvv.id AS bulletin_id, lvv.cve_list, lvv.cvss_score, lvv.hrefs, lvv.published, lvv.modified FROM upt_threat_indicators lvv JOIN dp ON lvv.package_name = dp.NAME AND lvv.os_version = dp.os_version WHERE lvv.os = 'Ubuntu' AND lvv.operator = 'lt' AND Vercmp(lvv.package_version, dp.version) > 0 and lvv.package_name = 'sudo';
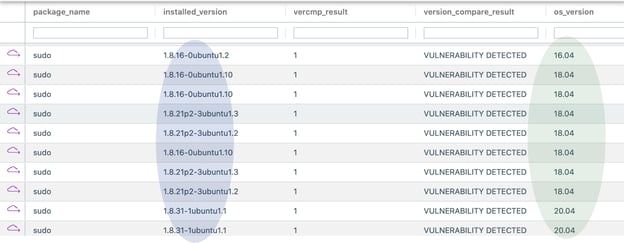
Figure 2. Vulnerable sudo package.
Schedule a demo to learn more about the detection and investigation functionality in Uptycs.