Extended Detection and Response (XDR)
Protect the developer laptops that build your applications, to the Linux servers that run them. The Uptycs extended detection and response (XDR) solution gives you powerful visibility and flexibility to secure and query any endpoint in your fleet. Enjoy unified threat detection and response, vulnerability scanning, security hygiene, compliance, remediation, and more.
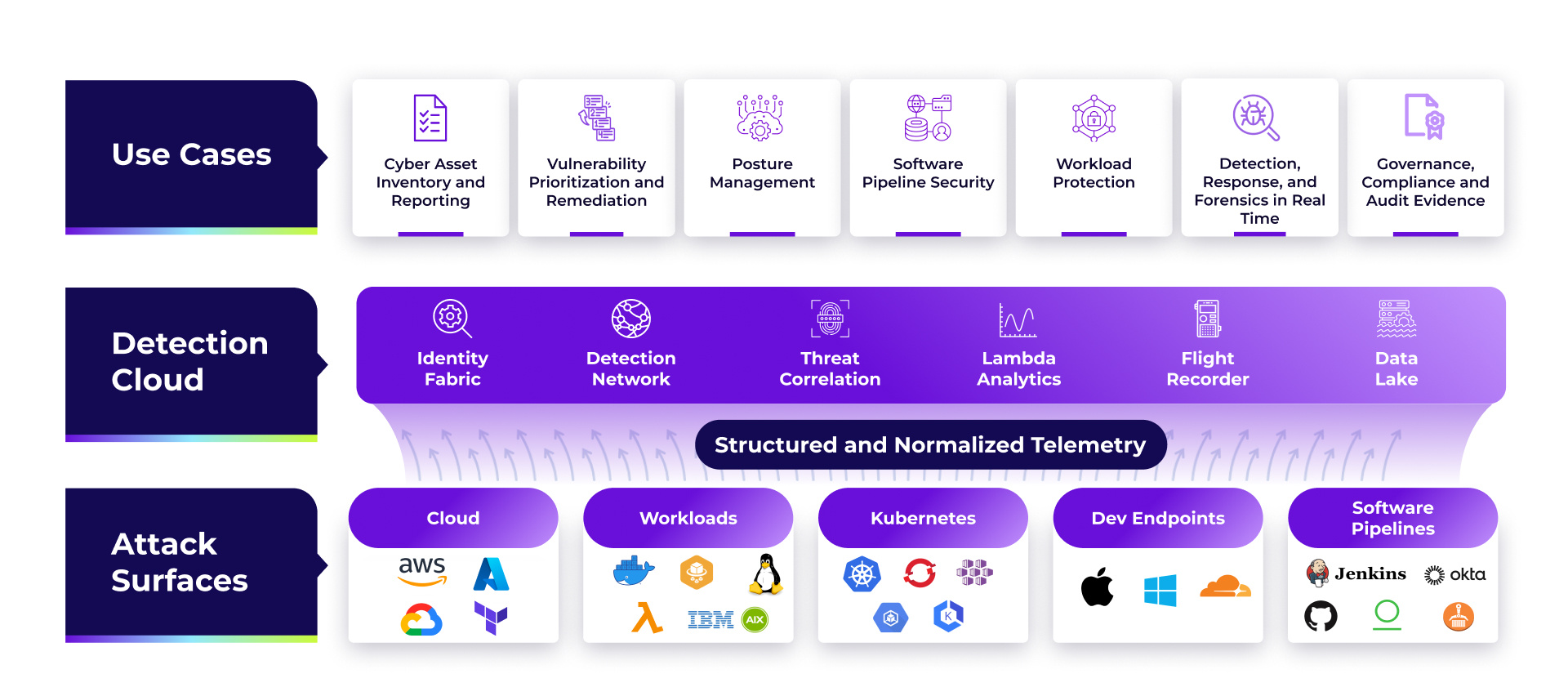
CNAPP Visibility That Reliably Scales
More than just everyday endpoint detection and response (EDR)
Our Customer Experience team is always on-hand to help fine-tune and optimize your strategy to improve efficiency and maximize your investment.
Leverage out-of-the-box behavioral detections, then tailor them to meet your specific security requirements.
Halt malicious binaries and dubious domain requests, or deploy automated remediation scripts with ease. Detect hidden vulnerabilities and establish preventative controls with deep support.
Swiftly determine the scope and root cause of incidents, armed with in-depth context and advanced forensic capabilities.
Best-in-class endpoint security
With employees working from home, securing laptops is more important than ever. Uptycs supports macOS, Windows, and Linux endpoints with advanced endpoint security capabilities including file integrity monitoring, YARA rule support, and more.
Powerful Vulnerability Scanning
Zero-trust scores for endpoints
-
Uptycs calculates device integrity, threat, and vulnerability scores.
-
Determine if a device can be trusted to access any on-prem, cloud, or SaaS services.
Threat intelligence that’s smart
-
The Uptycs threat research team is constantly exploring the latest threats.
-
Uses our global threat intelligence framework including external and internal sources.
-
Results in actionable reports specifically for your environment.
Works with What You Have
You rely on an existing suite of tools, and adding a CNAPP shouldn't complicate your team's work. That's why Uptycs works seamlessly with your existing tech stack.
.jpg)


Success Stories
“We've gotten a significant ROI on our Uptycs investment by playing to its strengths - the single data model and backend analytics.”

“Uptycs was deployed on a large scale as a key component of our security posture.”
“Uptycs helps me sleep better at night.”
“A unified view from which we can quickly ask and answer security questions across our environment.”
“Uptycs simplifies investigations and saves time—about 30% per investigation.”

“I would not want to do security anywhere without this level of visibility.”







