Secure laptop to cloud with one unified solution
Find and remove critical risks in your modern attack surface—cloud, containers, and endpoints—all from a single UI and data model.
All the security you need.
All in one place.
Attackers don’t work in silos, neither should your security. Uptycs offers a single, unified solution to protect your modern attack surface.
Containers and Kubernetes
Servers and VMs
Endpoints
Cloud Providers
SaaS Providers
Identity Providers
CNAPP
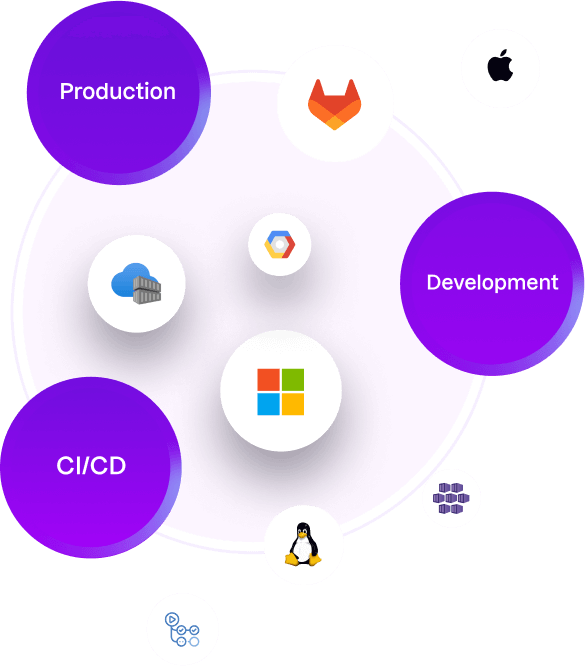
Uptycs supports dev laptops, CI/CD registry scanning, AWS, Azure, Google Cloud, and Kubernetes. Protect the arc of cloud-native app development.
XDR
Uptycs supports macOS, Windows, and Linux. Run YARA rules, carve files to extract malicious payloads, and implement Zero Trust.
Shift up your cybersecurity
Don’t settle for gaps in coverage
Your developer’s laptop is just a hop away from crown-jewel data, services, and source code. Stop relying on siloed solutions to protect cloud, containers, laptops, and servers.
With Uptycs you can tie together threat activity as it traverses on-prem and cloud boundaries.
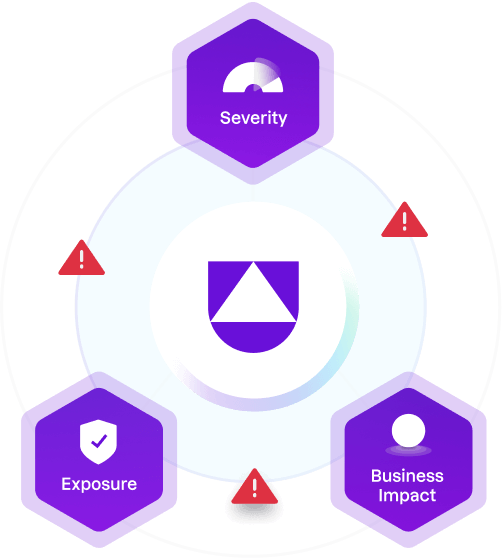
Focus on what matters
Eliminate risk and reduce alert fatigue by prioritizing your responses to threats, vulnerabilities, misconfigurations, and compliance mandates across cloud, containers, and endpoints.
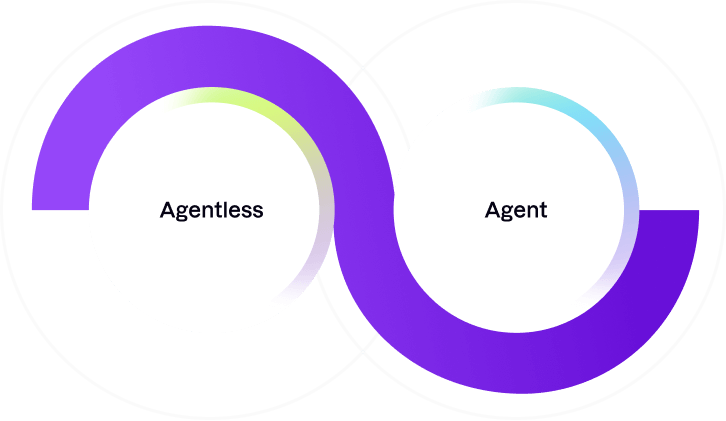
Agent or agentless?
There's no need to choose.
Uptycs gives you the freedom to work the way you want. For cloud and container security, start with instant-on agentless coverage, then add runtime protections with the Uptycs agent.
Uptycs normalizes data close to its collection point, then streams it up into an SQL-powered data lake, for comprehensive security across every point in your attack surface.
Steve Shedlock
Incident Response Team Lead, SEIResources for
the modern defender
Prepare for any challenges that lie ahead by choosing
the right tools today.
Gartner® CNAPP Market Guide
Cloud Native Application Protection Platform (CNAPP)

Quarterly Threat Bulletin #7

See Uptycs
in action
Find and remove critical risks in your modern attack surface - cloud, containers, and endpoints - all from a single UI and data model. Let our team of experts show you how.
