Simplify AWS Security
Tired of grappling with the complexities of AWS security and compliance? Make managing AWS security a breeze. Say goodbye to the headache and hello to Uptycs.
Visualize and Prioritize Risk for AWS
Don't just rely on basic security graphs; take your AWS security to the next level. Identify vulnerabilities across your entire cloud infrastructure.
Take Control of Your Cloud Identities
Safeguard your assets from unauthorized access, misuse, and insider threats. Easily spot permission gaps and overly-permissive roles, all while applying the essential principles of least privilege.
Quickly Detect & Respond to Threats
Security incidents don't wait, and neither should you. Rapidly identify and respond to malicious activities in your AWS environment.
Edit BG
Image
AWS Security Made Easy
AWS Partnership: Secure the cloud together
Uptycs, a proud AWS Security Software Competency Partner and Public Sector Partner, offers extensive expertise in delivering comprehensive security solutions for a wide range of AWS services.
- Deep expertise across the breadth and depth of AWS services. From EC2 to EBS to Amazon Workspaces
- Support for Amazon Linux, and AWS Graviton processors for EC2, ECS, EKS, and Fargate
- Proven solutions protecting large-scale AWS deployments
- Effortless integration into your AWS infrastructure, delivering value in minutes
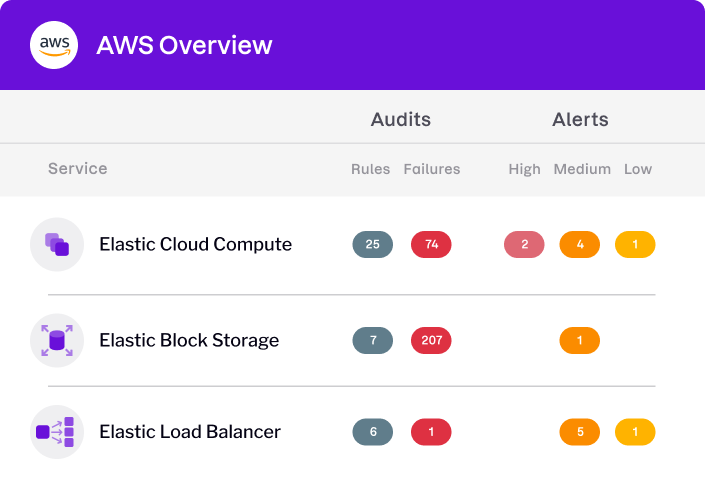
Get a handle on risky configurations
Address policy violations and misconfigurations to free up resources, enabling you to focus on managing a scalable cloud environment.
- Validate configurations against industry standards, including CIS Benchmarks, PCI-DSS, and SOC 2
- Demonstrate compliance more efficiently with detailed evidence and reporting
- Identify risks to AWS resources for unauthorized API activity, lack of user MFA, and user activity logging
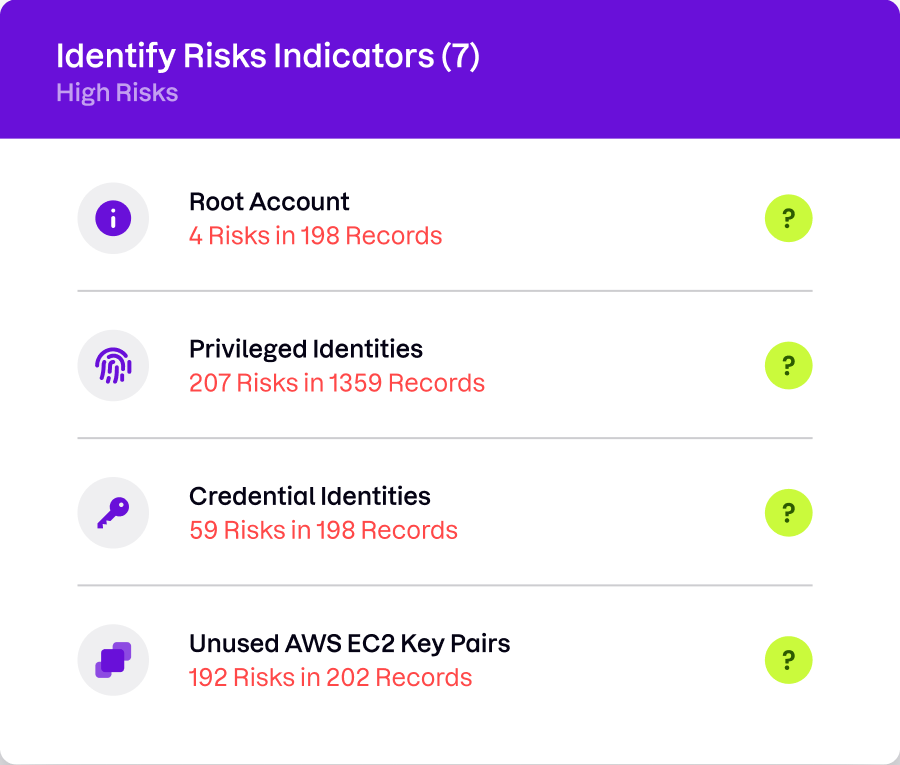
Take control of your cloud access
Comprehensive visibility into your cloud identity risks and governance. Better protect your AWS resources from unauthorized access, misuse, and insider threats.
- Address permission gaps so only authorized personnel can access your cloud resources
- Visualize asset access and permissions to identify who can access specific resources and what actions they can take
- Detailed breakdowns of your cloud identity risk, covering identity types, credentials, activity, and AWS IAM configurations
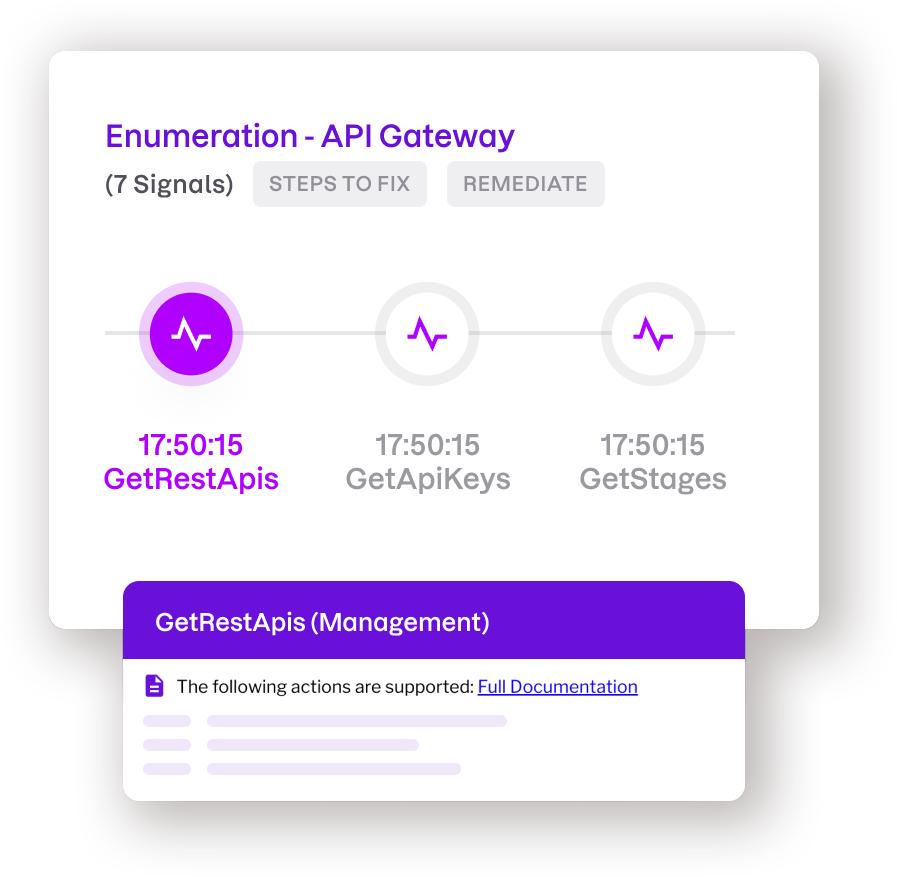
Quickly detect and respond to cloud threats
Rapidly identify malicious use of AWS APIs for discovery, privilege escalation, remote code execution, data exfiltration, and more. Take quick remediation action and then dig in to answer difficult investigation questions.
- Analyze cloud logs to capture the who, what, where, and when of AWS activities
- Make your team smarter with plain-language explanations of cloud security events
- Visualize threat actor behavior within your cloud environment
- Fix issues fast with one-click remediation
Hybrid deployments to fit your needs
Agentless workload scanning enables security teams to scan 100% of their cloud workloads quickly—even unmanaged assets—to detect risk including misconfigurations, policy violations, exposed secrets, vulnerabilities, and malware.
- Fine-tune your security strategy with the ability to deploy agent-based and agentless scanning
- 100% coverage extends workload security to rogue virtual machines or neglected workloads
- Fast, frictionless deployment and unmatched customization options