Meet Red Team Curly and Blue Team Linus. Hijinx will ensue.
Ever wondered how everyday, innocuous linux commands and utilities can be leveraged by bad actors? Curious how you can detect if they’re being used maliciously in your ecosystem?
Curly will stop at nothing to infiltrate Hackington and exfiltrate all the data he can find. There’s just one problem. Linus-- always vigilant, alert to anything suspicious, and wise to Curly’s tricks.
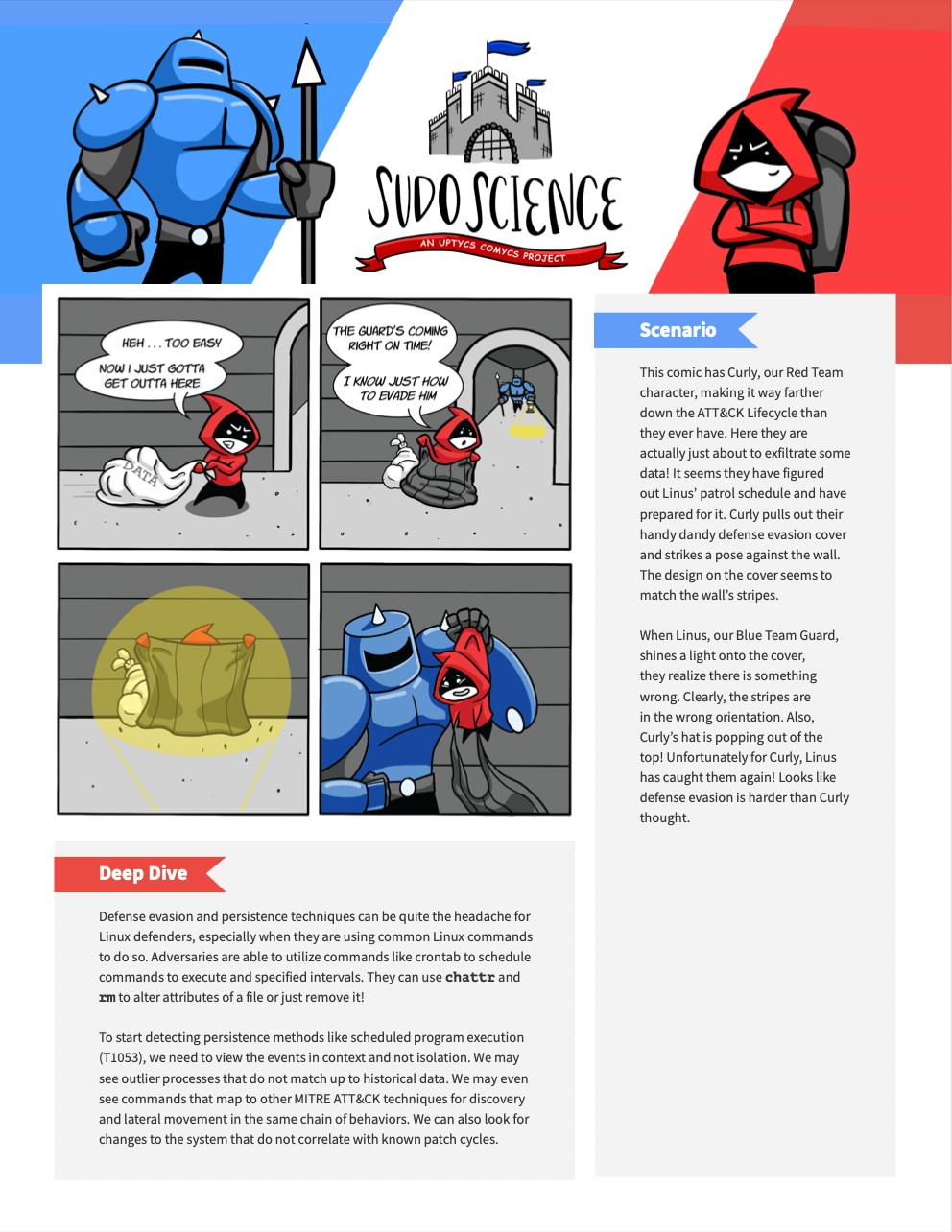
This episode of Sudo Science has Curly, our Red Team character, making it way farther down the ATT&CK Lifecycle than they ever have. Here they are actually just about to exfiltrate some data! It seems they have figured out Linus’ patrol schedule and have prepared for it. Curly pulls out their handy dandy defense evasion cover and strikes a pose against the wall. The design on the cover seems to match the wall’s stripes.
Click here to downloadDeep Dive
Defense evasion and persistence techniques can be quite the headache for Linux defenders, especially when they are using common Linux commands to do so. Adversaries are able to utilize commands like crontab to schedule commands to execute and specified intervals. They can use chattr and rm to alter attributes of a file or just remove it!
To start detecting persistence methods like scheduled program execution (T1053), we need to view the events in context and not isolation. We may see outlier processes that do not match up to historical data. We may even see commands that map to other MITRE ATT&CK techniques for discovery and lateral movement in the same chain of behaviors. We can also look for changes to the system that do not correlate with known patch cycles.
Want to see the full Sudo Science Comyc? Download your copy here.


