Secure Your Hybrid
Cloud from Dev to Runtime
Uptycs CNAPP extends your security visibility from development to runtime, ensuring consistent protection and compliance across your application infrastructure.





CNAPP
(but without the blind spots)
Other CNAPPs are limited to snapshot or runtime visibility. With Uptycs, you get 13 months of history so you know if, when, and how you were breached. Get the complete picture across your hybrid cloud and Kubernetes environments.

The reviews are in: customers and analysts love Uptycs
Learn why customers and analysts rank Uptycs a leader in cloud and endpoint security
.png?width=2000&height=2000&name=Awards%20(1).png)
Unify Your Cloud Security
Too many security tools? Unify your security across hybrid multicloud environments, Kubernetes, and the DevOps pipeline with a single platform that inventories and safeguards your cloud infrastructure.
Why industry leaders choose Uptycs
“Uptycs was deployed on a large scale as a key component of our security posture.”
Comcast
Vice President IT Security“We transitioned to Uptycs from an industry behemoth. We reduced costs, but more importantly, Uptycs' digs deeper for more impact.”
Computer & Network Security
Large Enterprise“Uptycs has been instrumental for our FedRamp authorization and ISO 27001 certification.”
Grant Kahn
Director, Security Engineering Lookout“Uptycs helps me sleep better at night.”
Sean Todd
CISO Pay Near Me“Uptycs contextualizes threat activity across K8s, cloud services, and laptops. We've dramatically shortened our threat investigation time.”
Anwar Reddick
Director of Information Security Greenlight Financial“Uptycs provides us with a comprehensive view of our environment without the need for log shipping or other data collection methods.”
Cloud Security Engineer
Top 10 Internet Site“I would not want to do security anywhere without this level of visibility.”
Steve Shedlock
Incident Response Team Lead SEI“Everything you want to know is as easy as querying a database. It’s fantastic.”
Security Engineer
E-learning Company“Product works great, is inexpensive, zero Dev complaints about slowing down systems (IYKYK), and they've added every feature I've asked for.”
Security Operations Manager
Business Services Company"Clean interface, very good visibility across assets, and their team is open to feedback."
Manager, Information Security
Finance Industry"A unified view from which we can quickly ask and answer security questions across our environment."
Chris Castaldo
CISO Crossbeam“A major game changer for heavily used hosts (40k requests per second). Running safely within one of the largest cloud environments on the internet. ”
Uptycs Customer
"Uptycs simplifies investigations and saves time—about 30% per investigation.
Sean McElroy
CSO Lumin Digital“If threat actors try to evade detection Uptycs captures those events”
Security Engineer
Large Telecom Company“Blazingly fast. 0.7 seconds from execution to detection, and 1.6 seconds from execution to case management alert.”
Security Engineer
Global Payment ProcessorUptycs provides actionable runtime threat and vulnerability insights and a flexible threat hunting capability.
Uptycs Customer
Director, Information Security Financial“Monitoring containers for Exploit/Mining Activity can be easily traced compared to other apps”
Security Engineer
Telecom Company“For so many issues, our answer is ‘Go to Uptycs.’”
Director of Security Operations
Enterprise Logistics Company“Uptycs enables us to make risk-based decisions.”
Chris Castaldo
CISO, Crossbeam“We transitioned to Uptycs from an industry behemoth. We reduced costs, but more importantly, Uptycs' digs deeper for more impact.”
Computer & Network Security
Large Enterprise“Uptycs was deployed on a large scale as a key component of our security posture.”
Comcast
Vice President IT Security“We transitioned to Uptycs from an industry behemoth. We reduced costs, but more importantly, Uptycs' digs deeper for more impact.”
Computer & Network Security
Large Enterprise“Uptycs has been instrumental for our FedRamp authorization and ISO 27001 certification.”
Grant Kahn
Director, Security Engineering Lookout“Uptycs helps me sleep better at night.”
Sean Todd
CISO Pay Near Me“Uptycs contextualizes threat activity across K8s, cloud services, and laptops. We've dramatically shortened our threat investigation time.”
Anwar Reddick
Director of Information Security Greenlight Financial“Uptycs provides us with a comprehensive view of our environment without the need for log shipping or other data collection methods.”
Cloud Security Engineer
Top 10 Internet Site“I would not want to do security anywhere without this level of visibility.”
Steve Shedlock
Incident Response Team Lead SEI“Everything you want to know is as easy as querying a database. It’s fantastic.”
Security Engineer
E-learning Company“Product works great, is inexpensive, zero Dev complaints about slowing down systems (IYKYK), and they've added every feature I've asked for.”
Security Operations Manager
Business Services Company"Clean interface, very good visibility across assets, and their team is open to feedback."
Manager, Information Security
Finance Industry"A unified view from which we can quickly ask and answer security questions across our environment."
Chris Castaldo
CISO Crossbeam“A major game changer for heavily used hosts (40k requests per second). Running safely within one of the largest cloud environments on the internet. ”
Uptycs Customer
"Uptycs simplifies investigations and saves time—about 30% per investigation.
Sean McElroy
CSO Lumin Digital“If threat actors try to evade detection Uptycs captures those events”
Security Engineer
Large Telecom Company“Blazingly fast. 0.7 seconds from execution to detection, and 1.6 seconds from execution to case management alert.”
Security Engineer
Global Payment ProcessorUptycs provides actionable runtime threat and vulnerability insights and a flexible threat hunting capability.
Uptycs Customer
Director, Information Security Financial“Monitoring containers for Exploit/Mining Activity can be easily traced compared to other apps”
Security Engineer
Telecom Company“For so many issues, our answer is ‘Go to Uptycs.’”
Director of Security Operations
Enterprise Logistics Company“Uptycs enables us to make risk-based decisions.”
Chris Castaldo
CISO, Crossbeam“We transitioned to Uptycs from an industry behemoth. We reduced costs, but more importantly, Uptycs' digs deeper for more impact.”
Computer & Network Security
Large EnterpriseWhy industry leaders
choose Uptycs
“Uptycs was deployed on a large scale as a key component of our security posture.”
Comcast
Vice President IT Security“We transitioned to Uptycs from an industry behemoth. We reduced costs, but more importantly, Uptycs' digs deeper for more impact.”
Computer & Network Security
Large Enterprise“Uptycs has been instrumental for our FedRamp authorization and ISO 27001 certification.”
Grant Kahn
Director, Security Engineering Lookout“Uptycs helps me sleep better at night.”
Sean Todd
CISO Pay Near Me“Uptycs contextualizes threat activity across K8s, cloud services, and laptops. We've dramatically shortened our threat investigation time.”
Anwar Reddick
Director of Information Security Greenlight Financial“Uptycs provides us with a comprehensive view of our environment without the need for log shipping or other data collection methods.”
Cloud Security Engineer
Top 10 Internet Site“I would not want to do security anywhere without this level of visibility.”
Steve Shedlock
Incident Response Team Lead SEI“Everything you want to know is as easy as querying a database. It’s fantastic.”
Security Engineer
E-learning Company“Product works great, is inexpensive, zero Dev complaints about slowing down systems (IYKYK), and they've added every feature I've asked for.”
Security Operations Manager
Business Services Company"Clean interface, very good visibility across assets, and their team is open to feedback."
Manager, Information Security
Finance Industry"A unified view from which we can quickly ask and answer security questions across our environment."
Chris Castaldo
CISO Crossbeam“A major game changer for heavily used hosts (40k requsts per second). Running safely within one of the largest cloud environments on the internet. ”
Uptycs Customer
"Uptycs simplifies investigations and saves time—about 30% per investigation.
Sean McElroy
CSO Lumin Digital“If threat actors try to evade detection Uptycs captures those events”
Security Engineer
Large Telecom Company“Blazingly fast. 0.7 seconds from execution to detection, and 1.6 seconds from execution to case management alert.”
Security Engineer
Global Payment ProcessorUptycs provides actionable runtime threat and vulnerability insights and a flexible threat hunting capability.
Uptycs Customer
Director, Information Security Financial“Monitoring containers for Exploit/Mining Activity can be easily traced compared to other apps”
Security Engineer
Telecom Company“For so many issues, our answer is ‘Go to Uptycs.’”
Director of Security Operations
Enterprise Logistics Company“Uptycs enables us to make risk-based decisions.”
Chris Castaldo
CISO, Crossbeam“We transitioned to Uptycs from an industry behemoth. We reduced costs, but more importantly, Uptycs' digs deeper for more impact.”
Computer & Network Security
Large Enterprise“Uptycs was deployed on a large scale as a key component of our security posture.”
Comcast
Vice President IT Security“We transitioned to Uptycs from an industry behemoth. We reduced costs, but more importantly, Uptycs' digs deeper for more impact.”
Computer & Network Security
Large Enterprise“Uptycs has been instrumental for our FedRamp authorization and ISO 27001 certification.”
Grant Kahn
Director, Security Engineering Lookout“Uptycs helps me sleep better at night.”
Sean Todd
CISO Pay Near Me“Uptycs contextualizes threat activity across K8s, cloud services, and laptops. We've dramatically shortened our threat investigation time.”
Anwar Reddick
Director of Information Security Greenlight Financial“Uptycs provides us with a comprehensive view of our environment without the need for log shipping or other data collection methods.”
Cloud Security Engineer
Top 10 Internet Site“I would not want to do security anywhere without this level of visibility.”
Steve Shedlock
Incident Response Team Lead SEI“Everything you want to know is as easy as querying a database. It’s fantastic.”
Security Engineer
E-learning Company“Product works great, is inexpensive, zero Dev complaints about slowing down systems (IYKYK), and they've added every feature I've asked for.”
Security Operations Manager
Business Services Company"Clean interface, very good visibility across assets, and their team is open to feedback."
Manager, Information Security
Finance Industry"A unified view from which we can quickly ask and answer security questions across our environment."
Chris Castaldo
CISO Crossbeam“A major game changer for heavily used hosts (40k requsts per second). Running safely within one of the largest cloud environments on the internet. ”
Uptycs Customer
"Uptycs simplifies investigations and saves time—about 30% per investigation.
Sean McElroy
CSO Lumin Digital“If threat actors try to evade detection Uptycs captures those events”
Security Engineer
Large Telecom Company“Blazingly fast. 0.7 seconds from execution to detection, and 1.6 seconds from execution to case management alert.”
Security Engineer
Global Payment ProcessorUptycs provides actionable runtime threat and vulnerability insights and a flexible threat hunting capability.
Uptycs Customer
Director, Information Security Financial“Monitoring containers for Exploit/Mining Activity can be easily traced compared to other apps”
Security Engineer
Telecom Company“For so many issues, our answer is ‘Go to Uptycs.’”
Director of Security Operations
Enterprise Logistics Company“Uptycs enables us to make risk-based decisions.”
Chris Castaldo
CISO, Crossbeam“We transitioned to Uptycs from an industry behemoth. We reduced costs, but more importantly, Uptycs' digs deeper for more impact.”
Computer & Network Security
Large EnterpriseProtect Your Software
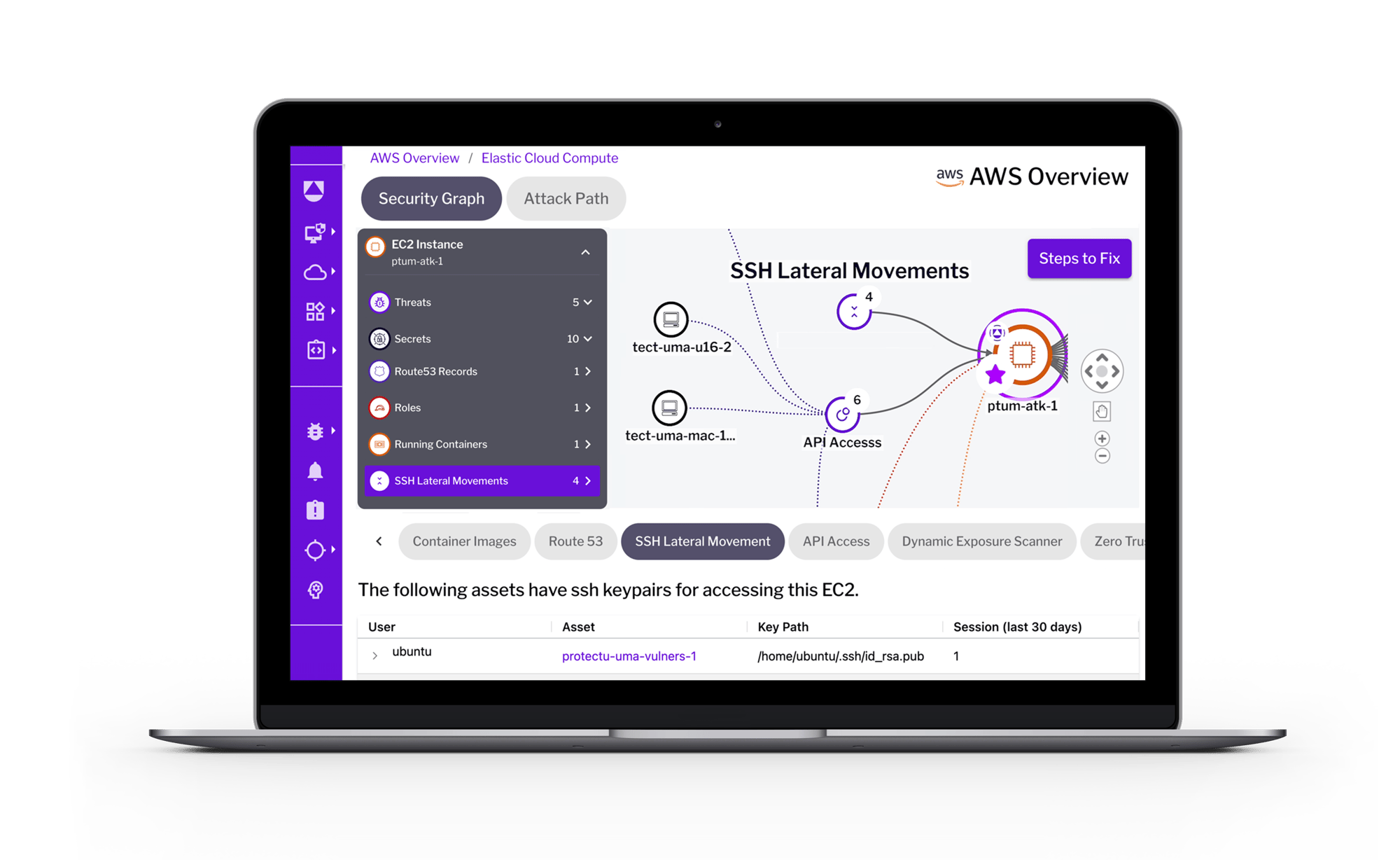
Is your software truly secure? Eliminate vulnerabilities at their source with security guardrails that are developer-friendly.
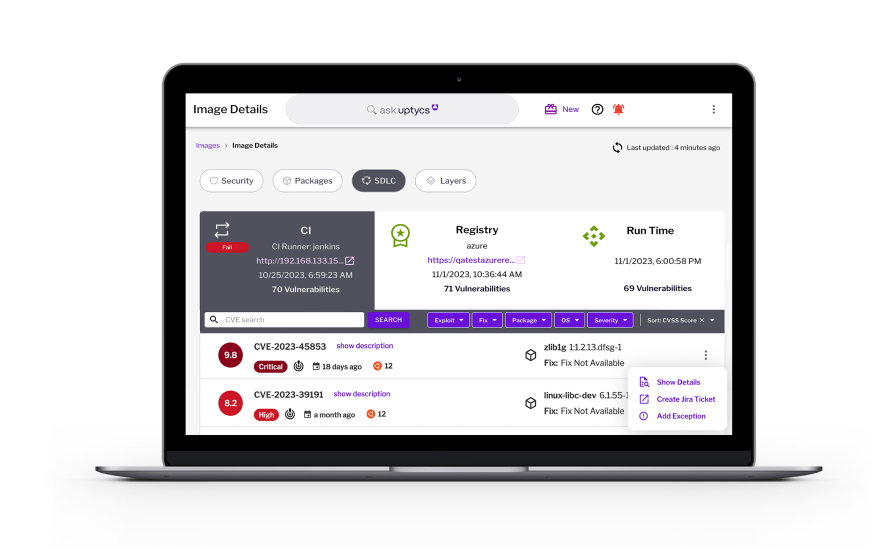

Make Your Audits Effortless
Tired of the audit treadmill? Make audits a breeze with compliance automation, flexible policy templates, and query-based evidence gathering.
Scale Security Seamlessly from
Development to Hybrid Cloud
Get deeper cyber asset inventory, unified security visibility, risk-based prioritization, and faster remediation—all at cloud speed and scale.
Unify Visibility
Take command with a unified security console, robust policy framework, and an expansive data lake that give you visibility at scale.
Protect Dev
Automate build-time and registry scans for vulnerabilities, malware, and secrets detection throughout your entire CI/CD pipeline.
Reduce Dwell Time
Slash MTTR by 50% with real-time ATT&CK-mapped behavioral detections, alerting, and remediation.
Secure Anywhere
Secure Kubernetes and container-based applications, anywhere - on-premises, in the cloud, or serverless.
Prioritize Remediation
Prioritize vulnerabilities and provide image layer insights for faster developer fixes.
Accelerate Investigations
Accelerate your threat hunting and investigations with real-time and historical queries, as well as tools such as YARA file and memory scanning.
Deploy Fast
Start with agentless coverage for fast deployment, and layer on the Uptycs Sensor for runtime security.
Control Runtime
Enforce risk-based policies to ensure only trusted images are deployed.
Streamline Compliance
Automate compliance for NSA Kubernetes hardening checks, CIS Benchmarks, SOC 2, PCI-DSS, HIPAA, and ISO 27001.
The first unified CNAPP
and XDR platform
Attackers don't think in silos and neither should your security.
Master your threat operations, meet compliance mandates, and reduce risk across clouds, containers, and endpoints-all from a single console and data lake.
Attack Surfaces
Cloud Providers
Cloud Providers
The most important way to improve cloud security posture is to ensure resources are configured correctly. It’s a task that can be difficult without visibility across cloud accounts. With Uptycs, IT and security teams can inventory cloud assets and resources, identify non-compliant resources, and access evidence needed for remediation — and more.
Cloud Workload
Container Runtime
Cloud Workload
Container Runtime
As organizations adopt new processes and technologies for building and running applications, they require new types of security observability. Uptycs equips modern defenders with the functionality to protect container-based applications, whether run on-premises, or in the cloud—on a VM or in a serverless deployment.
Kubernetes
Kubernetes
When Kubernetes and container deployments scale up, it becomes difficult to inventory and monitor your fleet. To solve your problems around Kubernetes and container workflows, Uptycs offers Kubernetes security posture management (KSPM) to cover a broad range of security use-cases including hardening, compliance, and threat detection.
Endpoints Host OS
Endpoints Host OS
Developer laptops and other on-premises assets are key targets, containing cloud provider and GitHub credentials. All security tools generate alerts — but only Uptycs Extended Detection and Response (XDR) streamlines telemetry across modern attack surfaces and gives you comprehensive detection and response capabilities, from the laptop to the cloud.
Uptycs Detection Cloud
A powerful analytics engine and data pipeline
Uptycs Solutions
Data summarizations and visualizations that solve for multiple solutions
- Cloud-Native Application Protection Platform (CNAPP)
- Extended Detection and Response
- Governance, Compliance
and Audit Evidence - Cyber Asset Inventory and Insights
- Ask Uptycs
Shift up your cybersecurity
Don’t settle for gaps in coverage
Your developer’s laptop is just a hop away from crown-jewel data, services, and source code. Stop relying on siloed solutions to protect cloud, containers, laptops, and servers.
With Uptycs you can tie together threat activity as it traverses on-prem and cloud boundaries.
Resources for
the modern defender
Prepare for any challenges that lie ahead by choosing
the right tools today.
Gartner Hype Cycle for Application Security, 2022

Gartner Hype Cycle for Application Security, 2022

Gartner Hype Cycle for Application Security, 2022

See Uptycs in action
Start with our free, no-obligation 35-day trial. Get comfortable with Uptycs using synthetic data, then deploy to a live environment.
Resources for
the modern defender
Gartner CNAPP Market Guide
Mastering Kubernetes Security
.png?width=300&height=300&name=Mastering%20Kubernetes%20Security%20e-book%20(2).png)
Lookout Case Study


