Microsoft released multiple security updates on Tuesday, July 14, including one for a remote code execution vulnerability for their DNS server.
Why is this different than any other Patch Tuesday?
What makes this vulnerability different is that, if an exploit finds its way into the wild, it will allow full SYSTEM-level access to any Windows-based DNS server without any sort of authentication.
Exploitation could be as simple as sending a specially crafted DNS request, which can be done at scale. Oh, and in most cases, every domain controller within an Active Directory domain is also a DNS server and is vulnerable.
What can I do?
Patch immediately. This article has all the information needed for your IT staff to get busy. Delaying this update for a maintenance window is highly discouraged.
If you can't patch right away, there's a quick registry fix outlined in the article that can be applied without rebooting, as long as the DNS service is restarted.
How can Uptycs help?
If you are running Uptycs or another osquery-based solution on all your Windows servers, checking the status of this vulnerability across your entire fleet is just a quick query away.
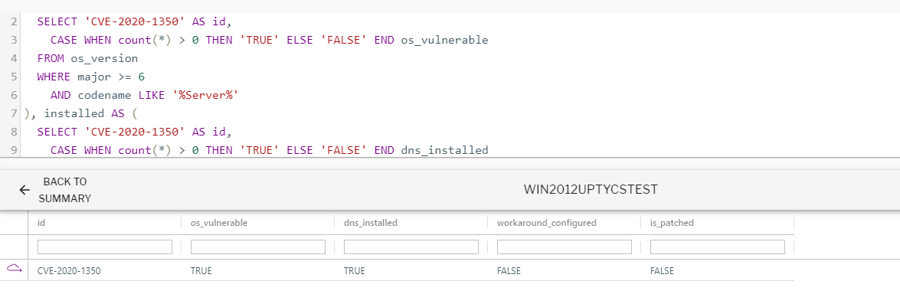
WITH vulnerable AS (
SELECT 'CVE-2020-1350' AS id,
CASE WHEN count(*) > 0 THEN 'TRUE' ELSE 'FALSE' END os_vulnerable
FROM os_version
WHERE major >= 6
AND codename LIKE '%Server%'
), installed AS (
SELECT 'CVE-2020-1350' AS id,
CASE WHEN count(*) > 0 THEN 'TRUE' ELSE 'FALSE' END dns_installed
FROM services
WHERE name = 'DNS'
), workaround AS (
SELECT 'CVE-2020-1350' AS id,
CASE WHEN count(*) > 0 THEN 'TRUE' ELSE 'FALSE' END workaround_configured
FROM registry
WHERE key = 'HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\DNS\Parameters'
AND name = 'TcpReceivePacketSize'
AND CAST(data AS int) <= 65280
), patched AS (
SELECT 'CVE-2020-1350' AS id,
CASE WHEN count(*) > 0 THEN 'TRUE' ELSE 'FALSE' END is_patched
FROM patches
WHERE hotfix_id IN ( 'KB4558998', 'KB4565483', 'KB4565503', 'KB4565511','KB4565524', 'KB4565529', 'KB4565535', 'KB4565536', 'KB4565537', 'KB4565539', 'KB4565540', 'KB4565541' )
)
SELECT * FROM vulnerable JOIN installed USING (id), workaround USING (id), patched USING (id)
This query detects if the operating system is vulnerable and whether or not the DNS service is installed. It will then check the registry to see if the workaround is applied and if the appropriate patch has been installed.
Query output in Uptycs. Click to see larger version.
For those savvy with SQL, the query template outlined above can be used for any high-profile Microsoft vulnerability that you need immediate information about.
Image by Aida KHubaeva from Pixabay


![mastering-kubernetes-container-s[1]](https://www.uptycs.com/hs-fs/hubfs/mastering-kubernetes-container-s%5B1%5D.jpg?width=400&height=209&name=mastering-kubernetes-container-s%5B1%5D.jpg)
![kevin-paige-ciso-cybersecurity-standup-podcast[1]](https://www.uptycs.com/hs-fs/hubfs/kevin-paige-ciso-cybersecurity-standup-podcast%5B1%5D.jpg?width=400&height=209&name=kevin-paige-ciso-cybersecurity-standup-podcast%5B1%5D.jpg)